PDF Password Cracking
- by Vince
-
in Blog
-
Hits: 2194
I sent an email to a vendor asking for a document and when the vendor replied to my email with the document attached, the document was password protected. He said as much and he also said that I could probably crack it. He is correct.
I've probably cracked a PDF once or twice. I've probably also cracked a few ZIP files, RAR files, and various other files with passwords but I think you get the point. Essentially, most of these types of files will all crack the same way -- John the Ripper.
There are a couple of John the Ripper versions but somewhere along the way, I discovered that the Jumbo John package is the one to use for cracking ZIPs and RAR files. I don't know whether PDFs fall under that some umbrella but that's where I went.
To perform this little parlor trick, I went to one of the machines with the Jumbo package. Prior to moving over to a terminal window for my little test case, I created a PDF document, password protected it, and then I moved it over to Kali.
Again, John versions vary so I just wanted to run this to see if I got a full hash. There was a pdf2john.py version that didn't give me what I wanted.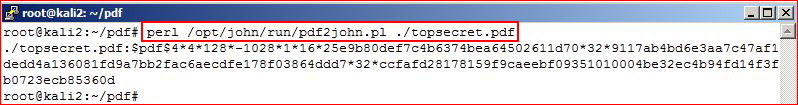
Looks good so now I re-run the command I redirect the output into a file titled: "hash". I then start cracking the hash with a small wordlist:perl /opt/john/run/pdf2john.pl ./topsecret.pdf > hash/opt/john/run/john hash --wordlist=/usr/share/wordlists/top500.txt
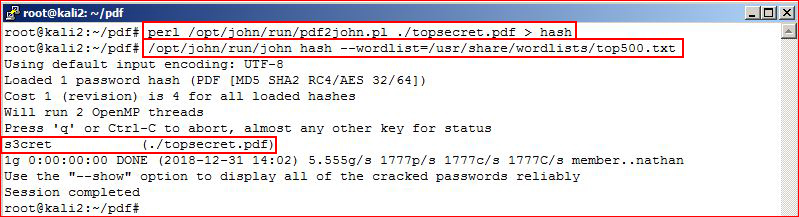
Not that I've created the most secure password, this was more of just proving a point. So now we have the password -- "s3cret", we're going to attempt to open the document with our newly acquired password:

It accepts our password:

And now you can see what I truly think are top secret documents. Btw, this recipe was delicious!
The real point of this exercise is to show you that this false sense of security is just that. A more complex password would have stopped my wordlist brute force but there are other methods for countering that problem as well.