Cracking Active Directory Hashes
- by Vince
-
in Blog
-
Hits: 1959
I attended Cactuscon this past weekend and there was a talk on cracking Active Directory hashes. When I entered the room (late), it was standing room only. For a few minutes, I listened in but eventually ended up leaving because the gist of the talk is something I already practice. Essentially, build a cracking machine, dump the Active Directory hashes, and check for weak passwords.
My cracking machine is a Dell Precision 3600 Series workstation with an NVidia 8GB GPU. Without the GPU, using my 400MB wordlist, it takes approximately 2.5 hours to exhaust the list. With the GPU, it takes 7 minutes. It's a modest cracking machine and its purpose isn't to win any contests. I just want to get through a reasonable wordlist in a reasonable amount of time. This meets that goal.
My current goto wordlist started off as rockyou.txt but I've been adding to it along the way. Again, the goal is not to win any contests but to use a list that includes current thinking in search of weak passwords that still meet the password complexity rules.
For example, if you look at Windows Group Policy Password complexity, it requires the following:
At least one uppercase letter.
At least one lowercase letter.
At least one digit.
At least one non-alphanumeric character.
If you use the stock minimum length, 7 characters.
What I also see frequently is a password age of 90 days -- and a requirement for PCI Compliance.
So these variables factor into how I've shaped my password list. One more variable to add into the mix --
Helpdesks are frequently resetting passwords for users. Taking into consideration that passwords are changing every 90 days and the rules I've stated above, a recent addition to my password list includes the following and a few variations along these lines:
Winter2018!
Spring2018!
Summer2018!
Fall2018!
These passwords are weak but meet the requirements:
Greater than 7 characters.
One uppercase letter.
One lowercase letter.
One non-alphanumeric character.
My list is not the end all be all wordlist but it's good enough to take down the low hanging fruit.
So how do we go about cracking?
Open an elevated Command prompt.
Make a working directory and enter said directory.
Next, we're going to create a Shadow Copy:
vssadmin create shadow /for=C:
Now we're going to copy ntdis.dit to our working directory:
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\ntds\ntds.dit c:\hash
We need to export SYSTEM from the registry (although we could also copy that from our Shadow copy):
reg SAVE HKLM\SYSTEM c:\hash\SYSTEM
And finally, we'll delete our Shadow Copy:
vssdamin delete shadows /shadow={a3df23cd-465c-4102-a218-179d1be99bad}
I'm using Impacket on Kali so I'll move these two files over to the Kali box in order to dump hashes:
/usr/share/doc/python-impacket/examples/secretsdump.py -ntds ./ntds.dit -system ./SYSTEM LOCAL
Depending on the system you dump, you could get multiple hashes, we're just looking for NTLM hashes so you can clean up the dump and limit it to those. It should look like this:
domain.local\user:1103:b4b9b02e6f09a9bd760f388b67351e2b:b4b9b02e6f09a9bd760f388b67351e2b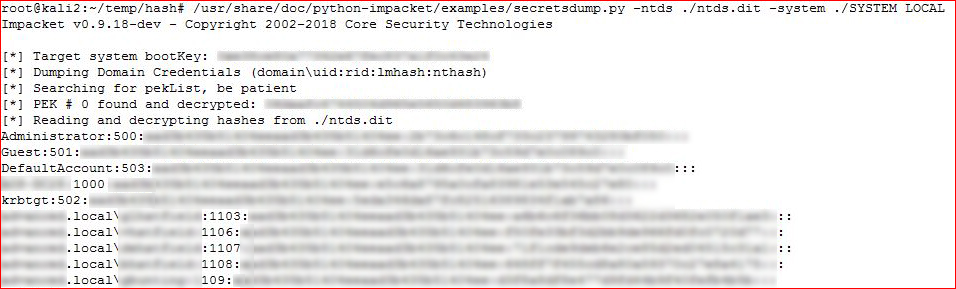
Once we get the hash file cleaned up, we're going to start cracking with hashcat:
hashcat64.exe -m 1000 hashes.txt top50000.txt
As you can see, we scored one password. Does that mean the rest are super strong? No. However, it does mean that they aren't super easy which is what we're trying to uncover.