Windows Exploit Suggester
- by Vince
-
in Blog
-
Hits: 2553
There are a ton of privilege escalation scripts that perform a wide variety of tasks but the reason why this particular tool sticks out is that it doesn't run on the target machine. The description for Windows Exploit Suggester states: "This tool compares a targets patch levels against the Microsoft vulnerability database in order to detect potential missing patches on the target. It also notifies the user if there are public exploits and Metasploit modules available for the missing bulletins."
Basically, we run systeminfo, save the contents into a file on our machine, and we run Windows Exploit Suggester against that file.
When we run systeminfo, we want to redirect the output into a file but that would make for a very boring screenshot: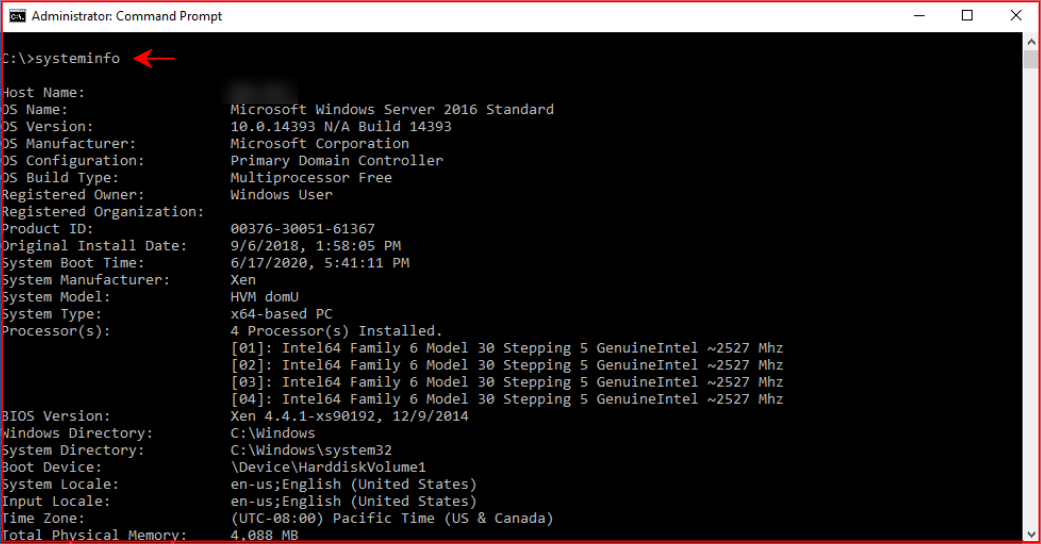
Next, we need to get a copy of the most recent Security Bulletin Data:
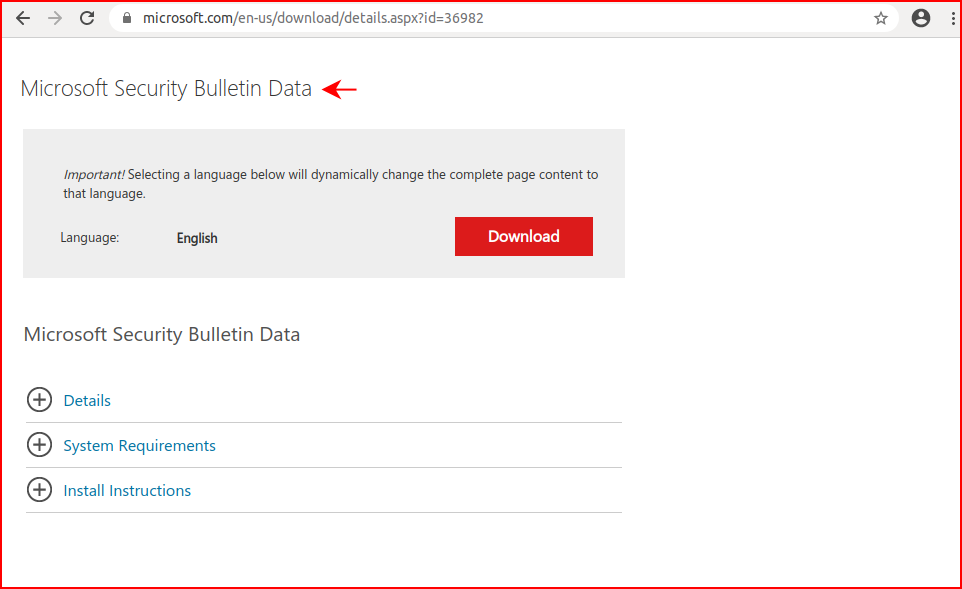
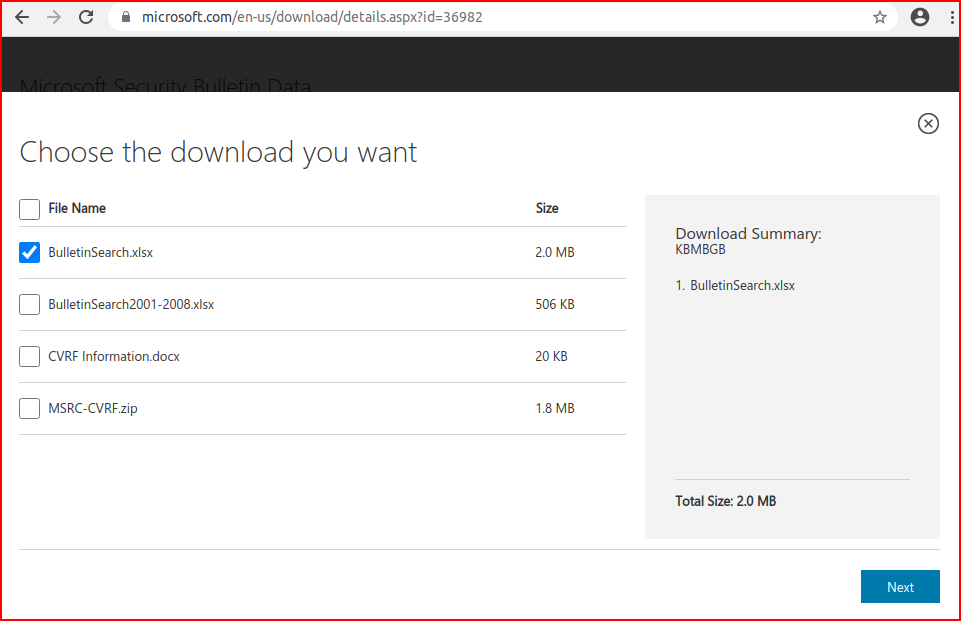
Choosing the more recent of the two options since we're running this against a modern machine:
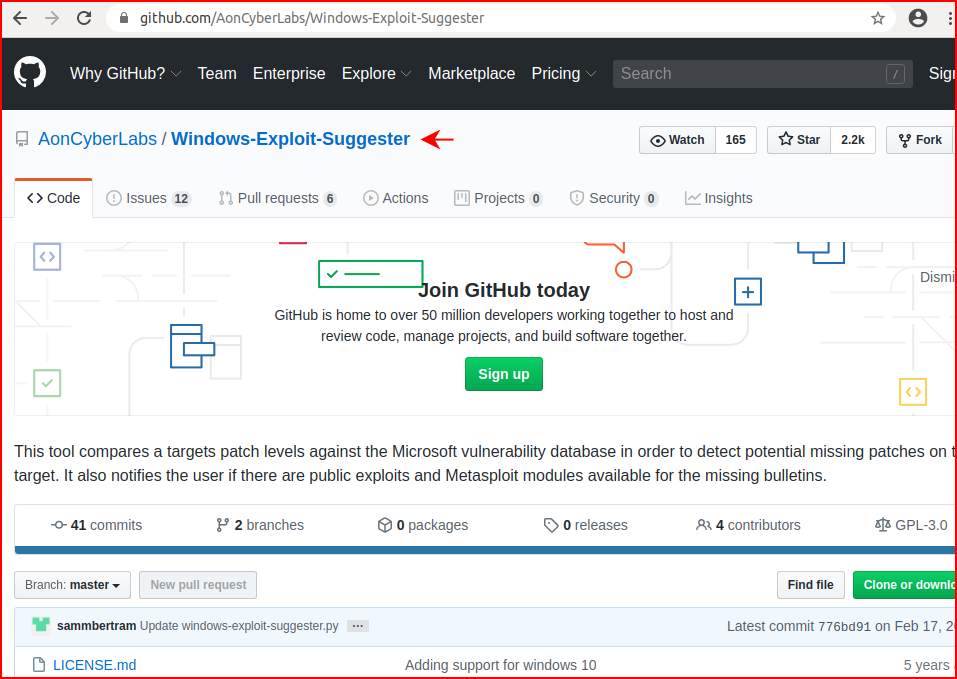
Grabbing a copy of the script:
Here's where we put everything together:
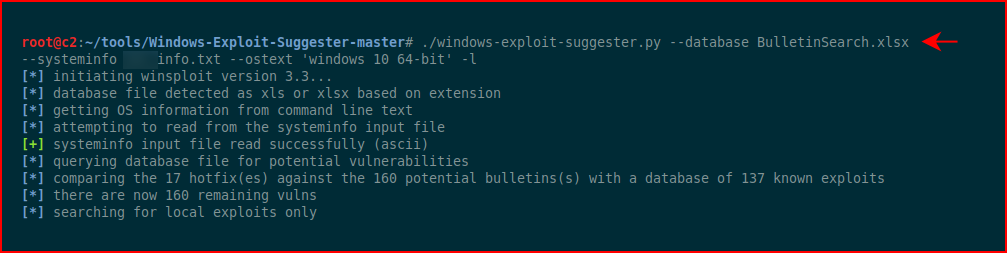
And after a few minutes:
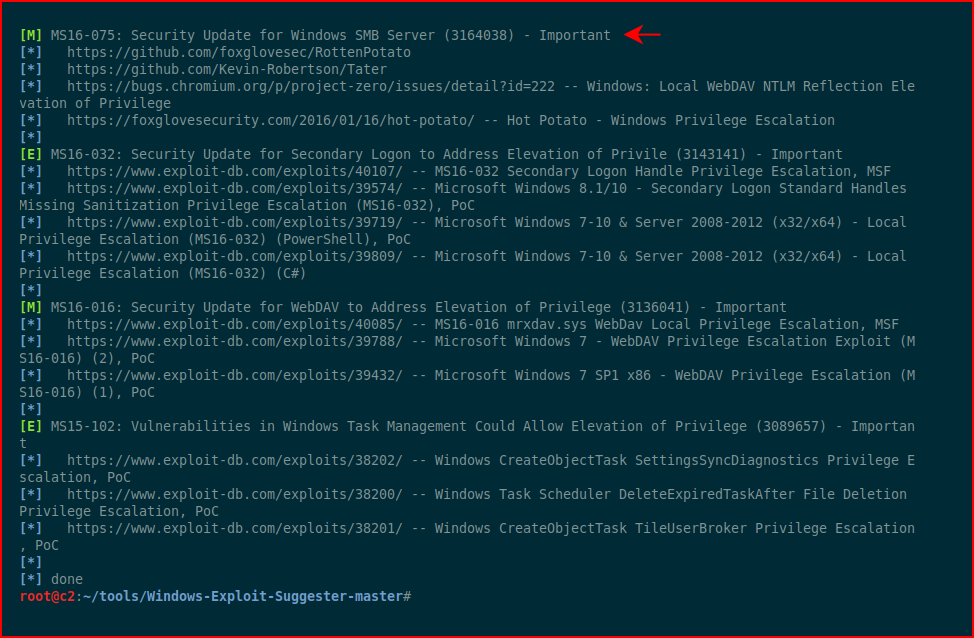
We get a list of options to escalate our privileges.
Again, the big selling point for me is not moving random files to the server. We're just running the native command to get what we need and then everything else is done off the box.