Evil-SSDP
- by Vince
-
in Blog
-
Hits: 2047
"Spoof SSDP replies to phish for credentials and NetNTLM challenge/response. Creates a fake UPNP device, tricking users into visiting a malicious phishing page. Also detects and exploits XXE 0-day vulnerabilities in XML parsers for UPNP-enabled apps."
So what is SSDP? "The Simple Service Discovery Protocol is a network protocol based on the Internet protocol suite for advertisement and discovery of network services and presence information."
And if that's unclear to you, it will all make sense in a moment when you see what appears in the Network view.
This tool has a wide variety of uses and it's one that requires a bit of imagination if at first glance you don't find a use for it. Let's get to it and then I'll add some additional thoughts in a bit.
At a minimum, we need to give it a network interface but I like this template (-t) for scanner:
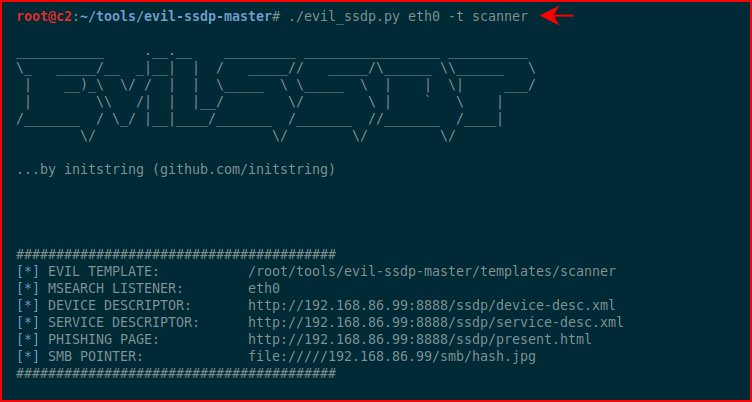
Once it's running, when we view the network, we see the following:
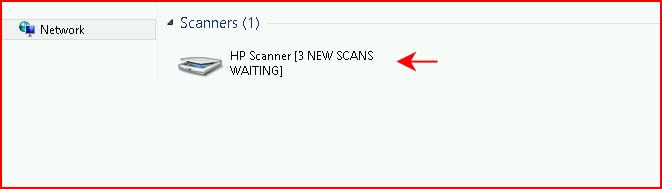
At this point, I can't tell whether I want to use this as an attack tool or a defense tool because I already have some ideas. I'm getting ahead of myself though. When we click Scanner, we are presented with this login prompt which we could clean up and change to look like that of our corporate environment:
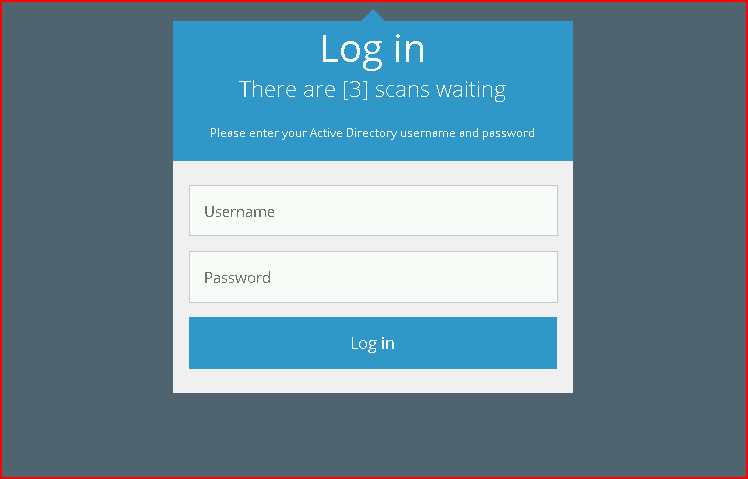
In the root of the evil-ssdp application, we have a templates folder which contains the files we can edit to make changes. I made a small change to the above already from the original just because I think it's a little more believable with three scans waiting versus the three scans waiting for you. I envision the administrator seeing this but not believing there are three scans waiting for her. But three random scans that might not have been seen is something that someone would want to dig into.
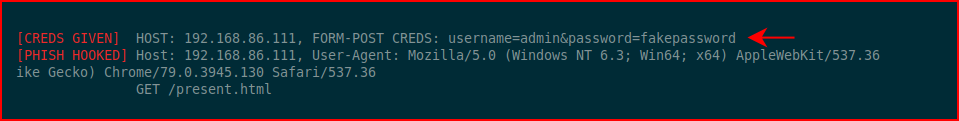
Anyway, back on the attacking machine side, we see the following when we enter credentials:
Another option is password vault:

When we click on it, we're brought to this page. I'm immediately thinking of making this look more legit and directing the victim to an OpenCanary SSH port.
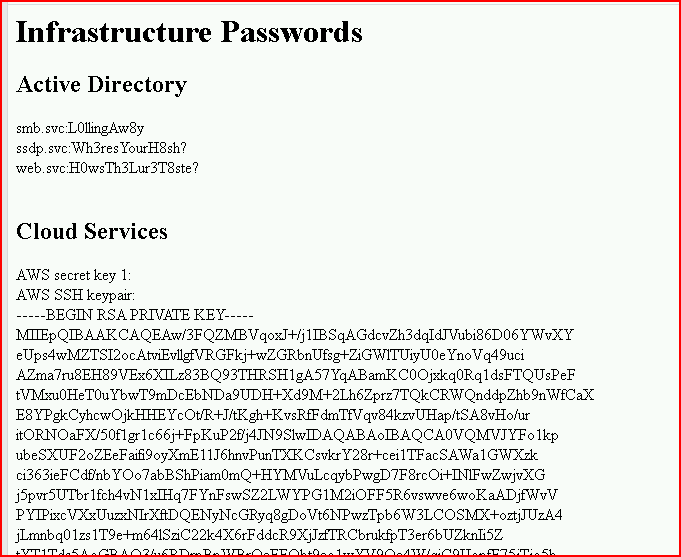
Yet another option:
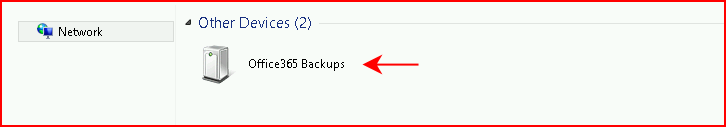
Which gets directed to this page:
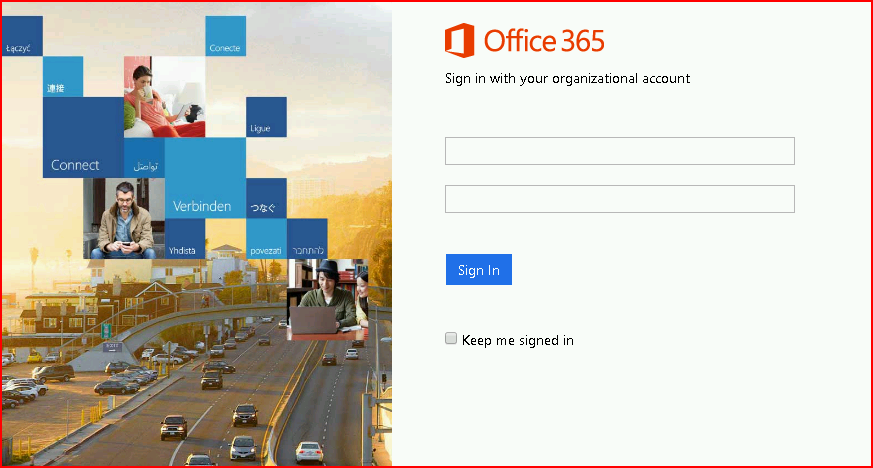
Again, I have lots of ideas floating around in my head and the templates are really easy to setup. This could be used for both offense and defense. Very cool.