Pentesting 101: Hash Cracking
- by Vince
-
in Blog
-
Hits: 4045
Penetration testing, red teaming, hacking, being enthusiastic about information security, or whatever else you want to call it -- to some degree, it's an art form. A significant portion of this type of work is non-linear and it requires a creative mind to piece together the puzzle. While the example I'm about to give seems relatively straightforward, there are other aspects of hash cracking that require an artistic imagination and I've seen challenges where I was amazed by the creativity of both the challenger and the participant. Today, we're keeping it simple but this is a real world situation.
While scanning a host, we uncover the following:
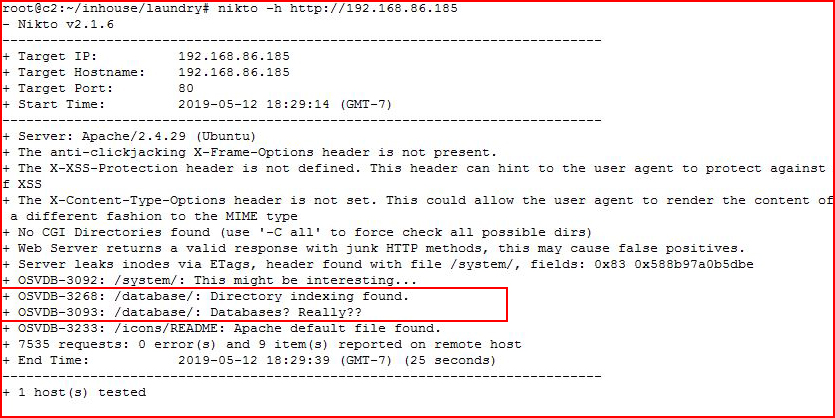
I find it amusing that even Nikto is like -- "Databases? Really??"
Don't laugh though, I was working with a client who used a third party web developer and when the developer packaged up the site, the files and the SQL database were both contained in the package. I loaded the site into the development server on our end and when I scanned the site, I found another copy of the database sitting in a folder in the webroot directory -- like you see above.
Pointing our browser to the /database folder, we find: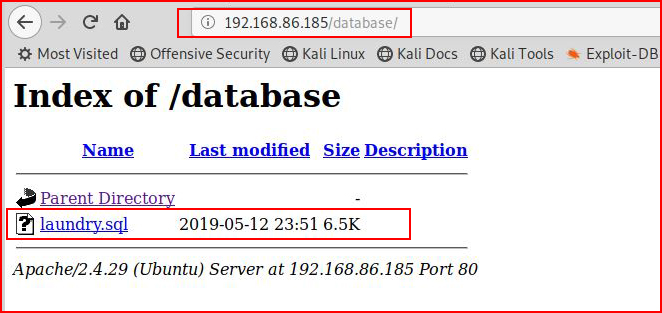
We download the laundry.sql file, open it up and we see:
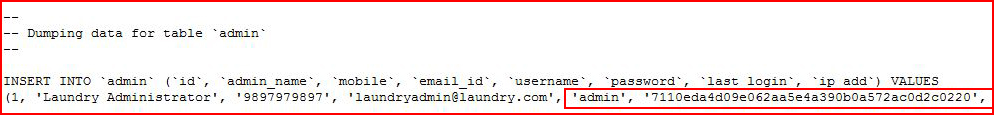
We have a username and a hashed password.
There are a couple of ways to determine the type of hash, the first available to use on Kali is Hash-Identifier:
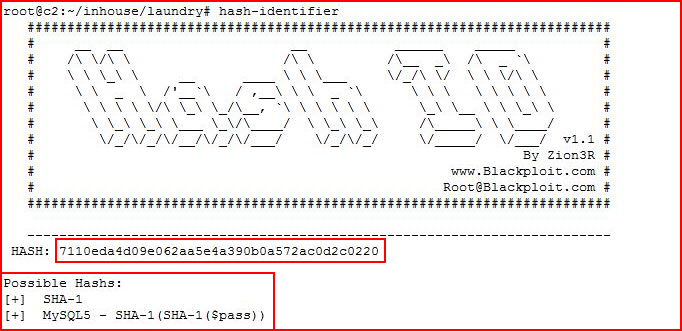
Hash-identifier thinks this is SHA-1. If I don't know the hash mode, or in the event we're not getting an exact match from Hash-Identifier, we can also use the example hashes listing on the Hashcat website:
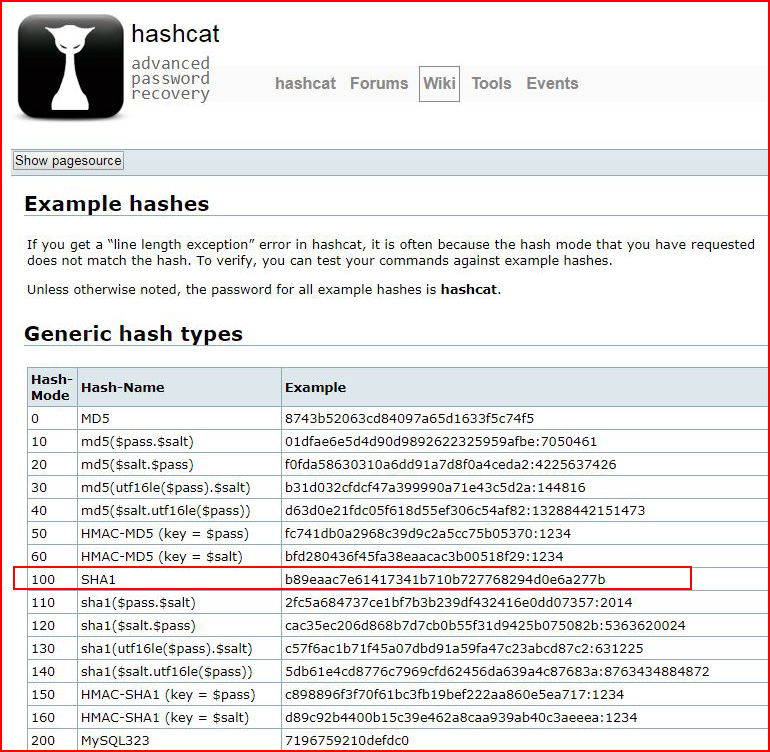
Typically, I'm going to use Hashcat to crack my hashes, there are other tools for other situations though and Hashcat is not the only game in town. In this scenario, I'll save the hashes into a text file to crack with Hashcat. As a sanity check, using the Hashcat example, I might copy the example hash into the same file to see if the length of the hash example matches my hash length.
Once I have an idea as to hash type, I note the hash mode and then I move over to my Windows cracking machine. Couple of things worth pointing out. I run Kali in a VM and hashcat gives all sorts of error regarding the lack of Graphic Processing Unit (GPU). I've never really bothered to invest much time in solving that problem because long ago, I purchased a high-end gaming card to speed up the process of cracking and that's done on a Windows platform.
On less complex hashing algorithms, it's not all that time consuming to crack a hash but when you're using a more difficult hashing algorithm and a large password list, it can take a LONG time. Basically, Hashcat reads a word in the wordlist, encrypts it using the same encryption algorithm to generate a hash and then it compares that generated hash to our victim hash. If it's not a match, it moves to the next word. If the hashing algorithm is complex, it takes a while. A graphics adapter with a fast GPU can encrypt faster. hashcat64.exe -m 100 laundry.txt rockyou.txt
-m = mode
100 = hash mode
laundry.txt = our victim hash
rockyou.txt = located on the Kali linux install under: /usr/share/wordlists/rockyou.gz, extract to rockyou.txt
I moved the extracted version over to my cracking machine and when we set Hashcat loose:
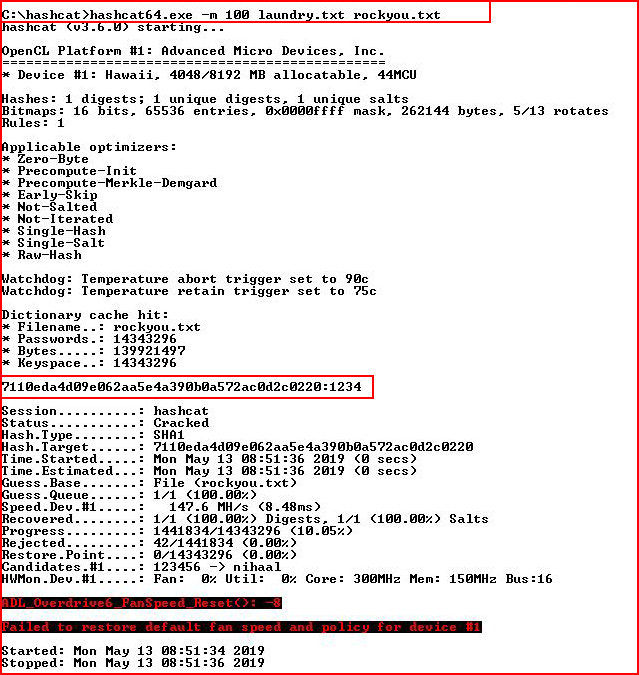
We see that we've cracked the hash in two seconds and the password is: 1234
We already know the username is: admin
Moving over to the login page, we enter:
admin : 1234
And we get logged into the management page: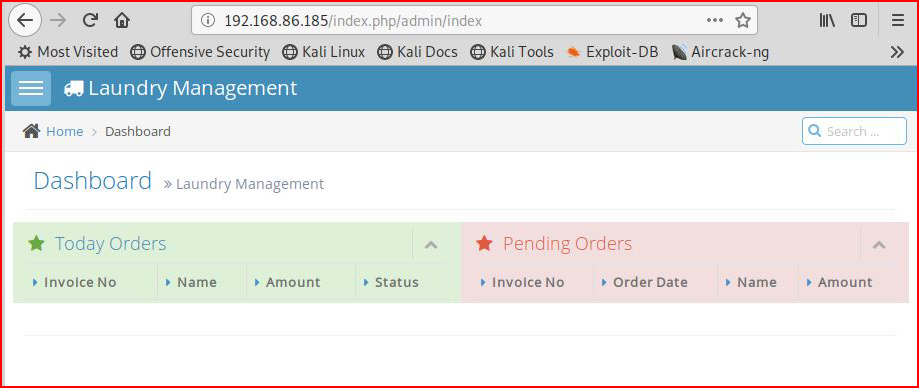
As a final thought, there are some sites that do cracking for free and for pay. Crackstation is one that I've used. Although, I should say that I've had mixed success with hashes it should have cracked. Another that I've heard about but haven't used it hashes.org but I think that could be a pay service.
Using Crackstation, we enter our hash, prove we're not a robot and when hitting submit: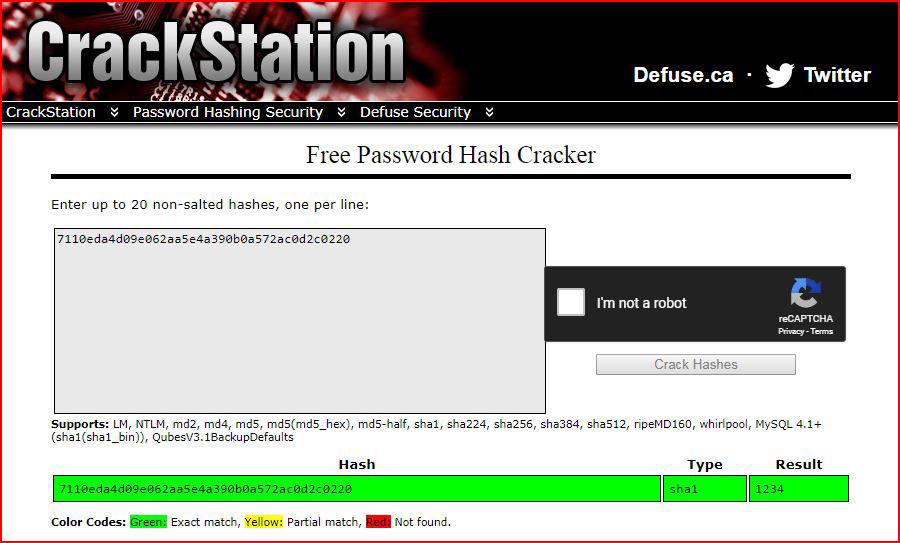
Again, as I mentioned previously, this is just scratching at the surface but the more you play around with simple hashes, the more this makes sense. Collecting other wordlists, consolidating them into bigger or smaller lists, can also help fine tune your cracking.