Sequential Passwords
- by Vince
-
in Blog
-
Hits: 12544
Over the last couple of weeks, I’ve seen a few examples of passwords being rejected for failing to meet the complexity rules. For example, the current password is “secret1234” and the new password attempted is “secret1235”. There are similar variations where people attempt to use the year and month – “password201810” and “password201811”.
My password manager shows that I have 516 accounts and passwords. Trying to remember 516 passwords is impossible which is why you should use a password manager. While a typical user might not have 516 accounts, they have quite a few and without a password manager, they try to create something memorable. I completely understand their need to change one digit and move on -- I disagree but I understand. Here’s the problem – let’s say I get wind of this type of pattern and the initial portion of the password is “testing” and the remaining portion is a four digit number. Technically, it’s an eleven digit, alphanumeric, password. In reality, it’s a four digit, numeric, password.
Basically, I need to create a wordlist with “testing” followed by every possible combination between 0000 and 9999. First we’re going to create our number sequence and pipe the output to a file:
seq -w 0 9999 >>numbers.out
Now that we have our number sequence, we’re going to prepend the word “testing” to each line:
sed -i -e 's/^/testing/' numbers.out
Not that we didn’t know this already but when we do a line count:
wc –l numbers.out
… we see there are 10,000 possibilities.
Cracking a sha512crypt password with only 10,000 possibilities is beyond fast: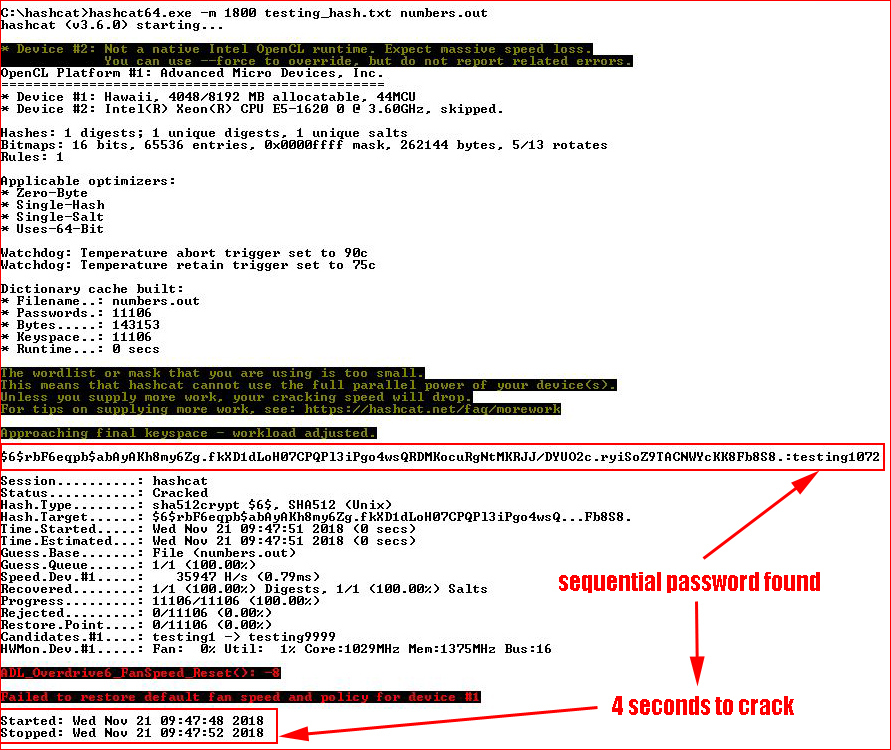
Even if the password happened to be “testing9999” it would be less than a minute to exhaust the entire wordlist.
The assumption is that it’s an eleven character secret but the real assumption should be that somewhere, sometime, one of your passwords has been compromised. If your password was created by a password manager and it looks like this:
xZc%6&}MR!R:!YeMb#wdXibB_if
… odds are pretty good someone will go hunting elsewhere. But if your password is along the lines of what I’ve described above, you can see the flaw in that method.