JoomlaVS
I stumbled upon this tool while following a link to a website that performs passive scans on various content management systems. Instead of keeping their scanning technique a mystery, they list a bunch of open source tools that they leverage in parallel. In addition to Joomscan which is something I already use, they mentioned JoomlaVS.
The description states: "JoomlaVS is a Ruby application that can help automate assessing how vulnerable a Joomla installation is to exploitation. It supports basic finger printing and can scan for vulnerabilities in components, modules and templates as well as vulnerabilities that exist within Joomla itself."
I decided to give it a whirl. When we fire it up with no arguments, we get the help screen: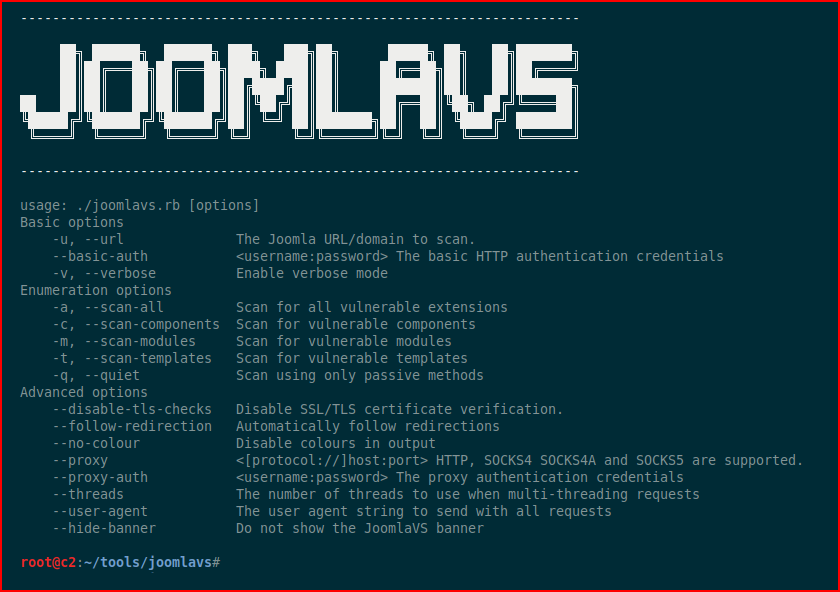
I went to Vulnhub and grabbed a machine that I knew had Joomla running. We hit it with Nmap:
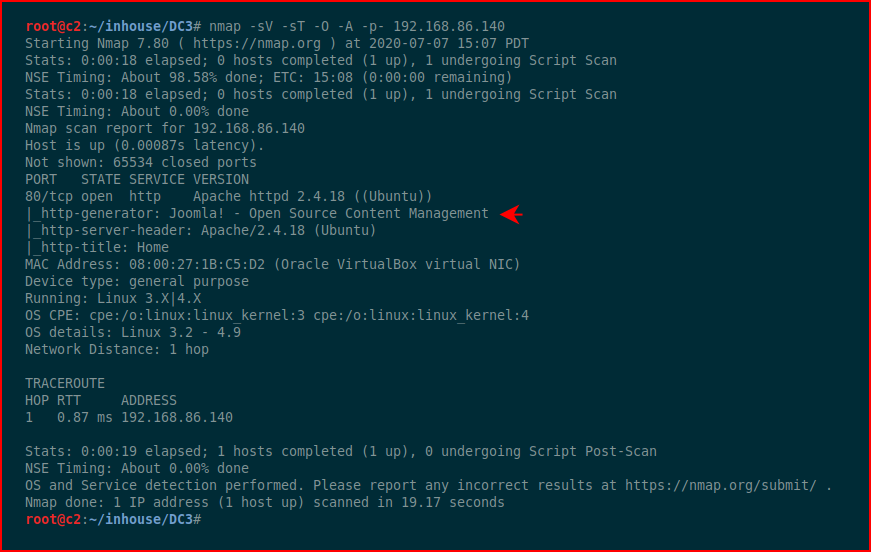
Our Nmap scan shows us that it's running Joomla. When we browse the site:
We fire up JoomlaVS and with the -a option, we're scanning it for all vulnerable extensions:
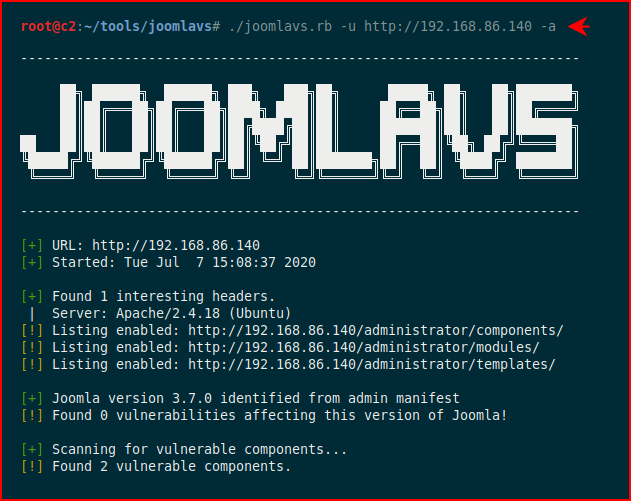
In the second half of the output, we start to see some items in red which indicate some possible avenues for exploitation:
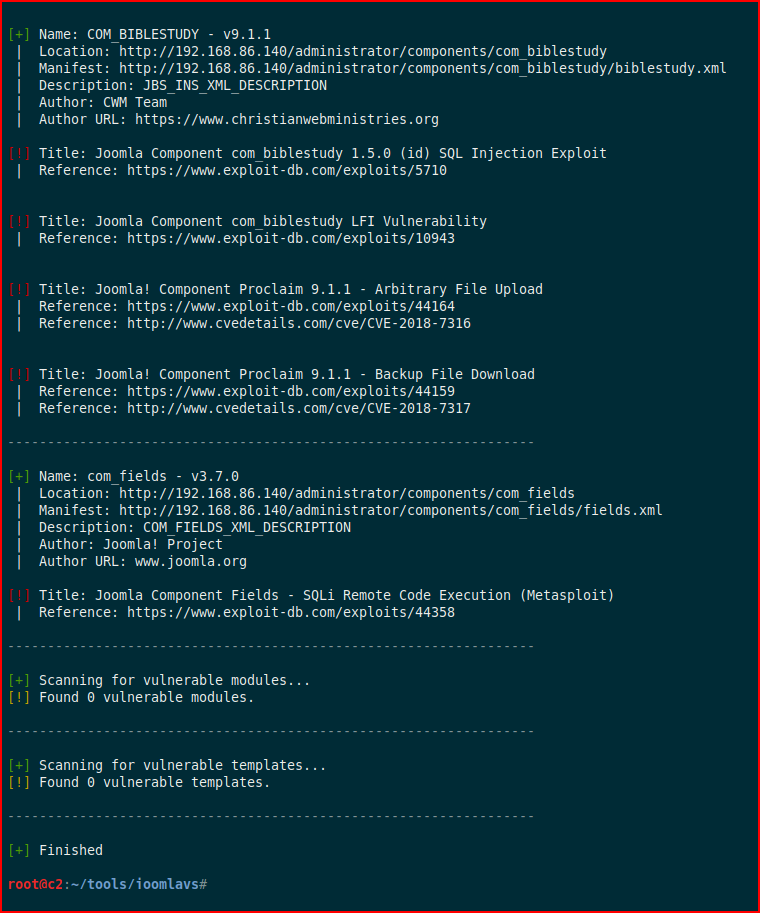
As a comparison, I ran Joomscan across it and it also found the same exact items. I don't know that I'd say one is better than the other but I might run these in parallel to see if one proves to be better than the other over time.