Hashcat Mask Attack
Hashcat is one of those tools where I feel like I'm just scratching at the surface with respect to all of its capabilities. Normally, I'm attempting to crack hashes with a wordlist to prove the strength of a password. Or I'm playing some CTF where I need to retrieve a password. In each case, I'm not brute forcing a password, I'm providing a wordlist which makes the process light years faster. That being said, there are times when I've wanted to use a brute force attack but have shied away when confronted with reading the manual. RTFM!
The mask attack for brute forcing is actually not that complicated. Recently, I became curious as to how long it would take to brute force a hash with my Vapor card given some known pieces of the puzzle. In a Windows environment, we have password complexity rules which consist of the following:
Must be at least 8 characters in length.
Must include one upper case letter.
Must include one lower case letter.
Must include one number.
Must include one special character.
Given this set of rules, people are likely to make the first letter an upper case, the number is likely to be on the end, and the special character will likely follow the number.
For example: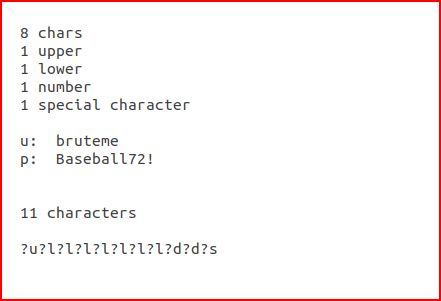
The mask looks complicated, or at least it did to me the first time I saw it, but it's not.
?u = upper case
?l = lower case
?d = number
?s = special character
The password is 11 characters and the ?X's are also 11 characters. In other words, we're brute forcing a password of exactly 11 characters in length. If it's more or less, or anything isn't as we think it is, we're not going to succeed. Seems like the odds are stacked against us but think about all of the password dumps on the Internet. If you find the same person in multiple breaches and there's a common theme -- Baseball70!, Baseball71!, Baseball72!, we're only cracking two digits, a special character but not the 8 alpha characters preceding the last three positions. In that case, we could use a hybrid wordlist and mask attack: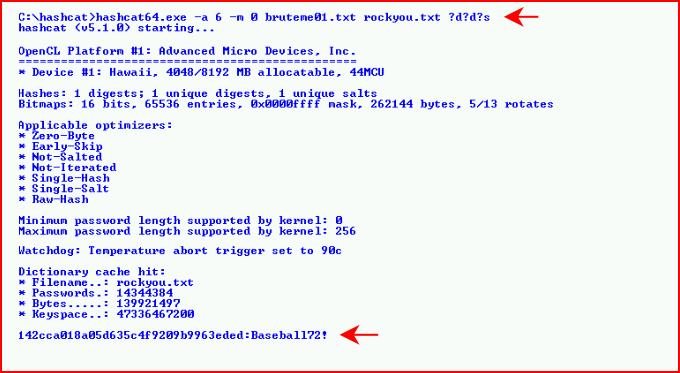
The above took only seconds to crack. But let's say we had less information and we were going to brute force the entire length, our mask attack would look like this:
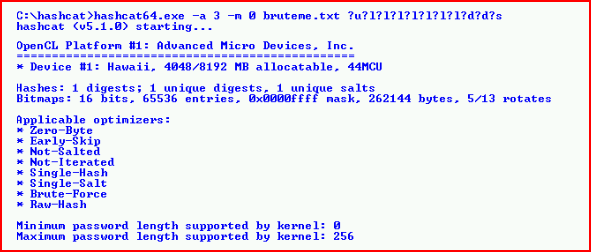
When we call the status, Hashcat assumes we're going to exhaust the entire list which it states will take two days and 17 hours:
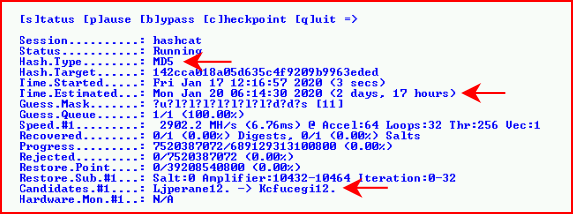
Because we fall somewhere short of almost three days, it "only" took 7+ hours:
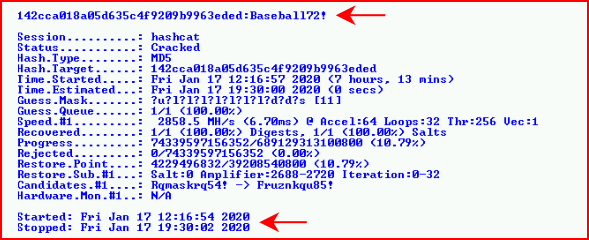
Granted, this is one modestly fast card and not 8 cards like I've seen in some of the large cracking systems. Are 8 cards 8x faster? If so, this is less than an hours worth of work.