Raspberry Pi Tor Proxy
I'm working on a talk for a conference and an aspect of my talk involves being anonymous. I'd considered several ideas as to that initial step but ended up with a Raspberry Pi Tor Proxy to sit in front of my burner laptop. That's just the beginning, of course, because there will be multiple layers but that's the direction of the talk and not the topic of this post. This post is that initial platform of anonymity.
When I looked around at examples for Pi proxies, I saw some older posts that were no longer valid and some newer posts that didn't exactly cover what I was trying to do. Or perhaps my Googling wasn't good enough. Regardless, I pieced some parts together and I got what I wanted. To make this post complete, I'm starting from near the very beginning. Pet projects aside, I not a frequent user of the Raspberry Pi so this will be as much a tutorial for me as for those who stumble upon this post.
After downloading Raspian, or whichever OS you choose for your Pi, we need to write the img file to the SD card. When we insert the SD card into the system, it will automatically get mounted and we need to unmount it. After the card is unmounted, we can then write the image. You'll need to change the name to match the name of your img file. You'll also need to locate the SD card by its /dev name: mount | grep sd
After you change the name of your output to match your SD card location, the command should look something like:sudo dd bs=4M if=2019-09-26-raspian-buster-list.img of=/dev/sdc conv=fsync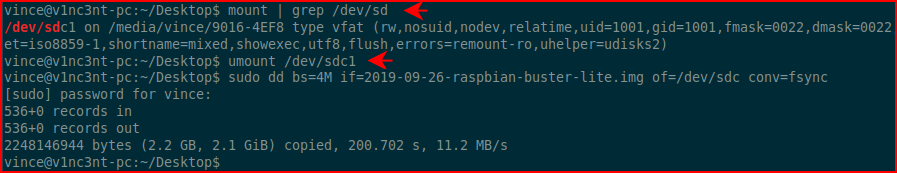
Next, we'll insert the card into the Pi, we'll boot it up and since we don't have SSH open by default, you'll need to be on the console. Username: pi Password: raspberry
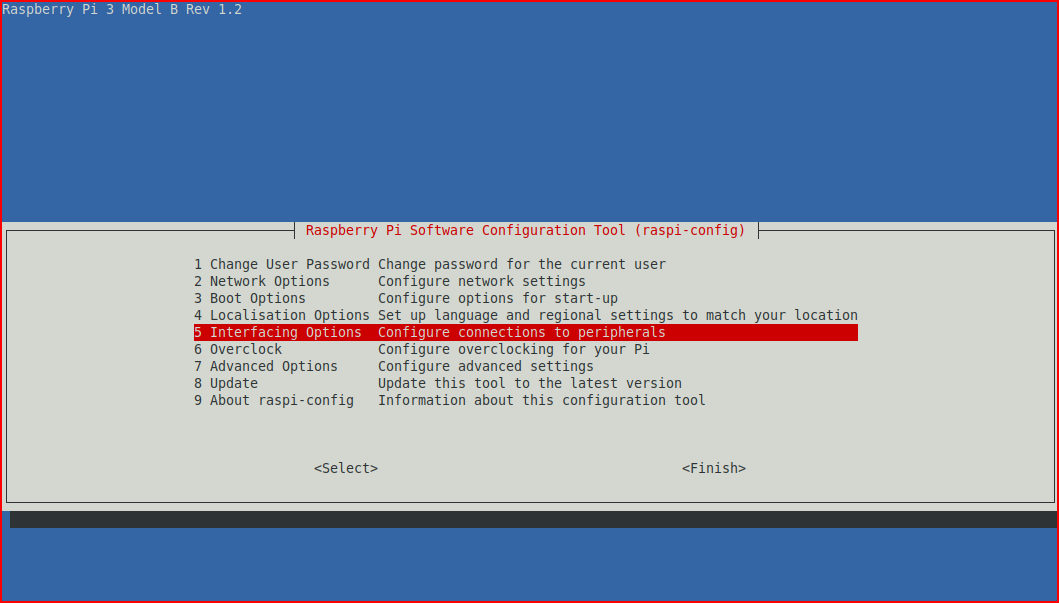
Once you get into the Pi, we're going to configure a few options so we can work on it through SSH. At the command line: sudo raspi-config
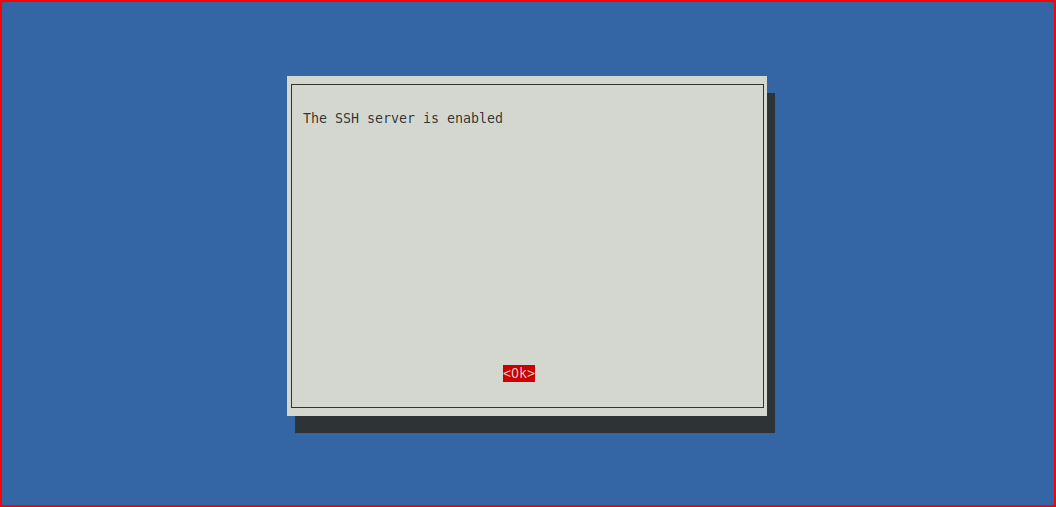
Select: 5 Interfacing Options
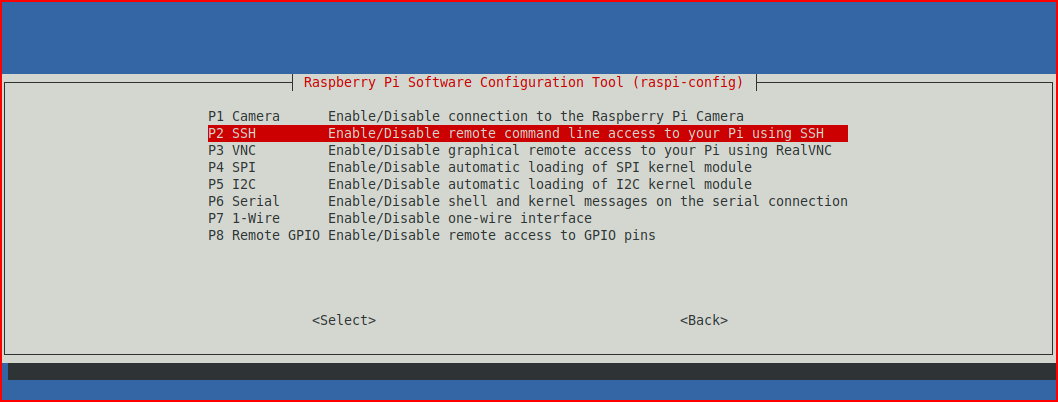
Select: P2 SSH
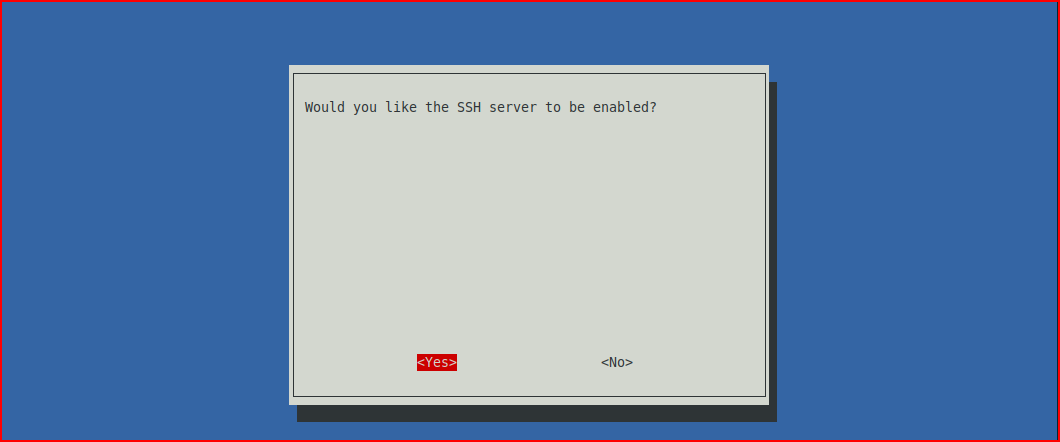
Choose: Yes
Click OK
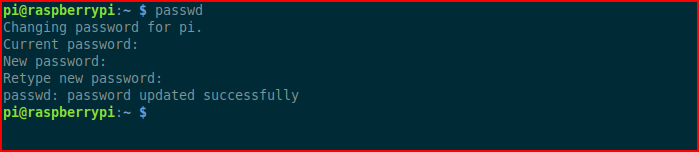
You can do this from within the raspi-config but not being super familiar with this tool, I bounced into the command line and changed the password. Regardless, change the password.
Back in raspi-config, we need to expand the disk. I guess Raspian only uses what it needs and we want to use the full card.
Select: Advanced Options:
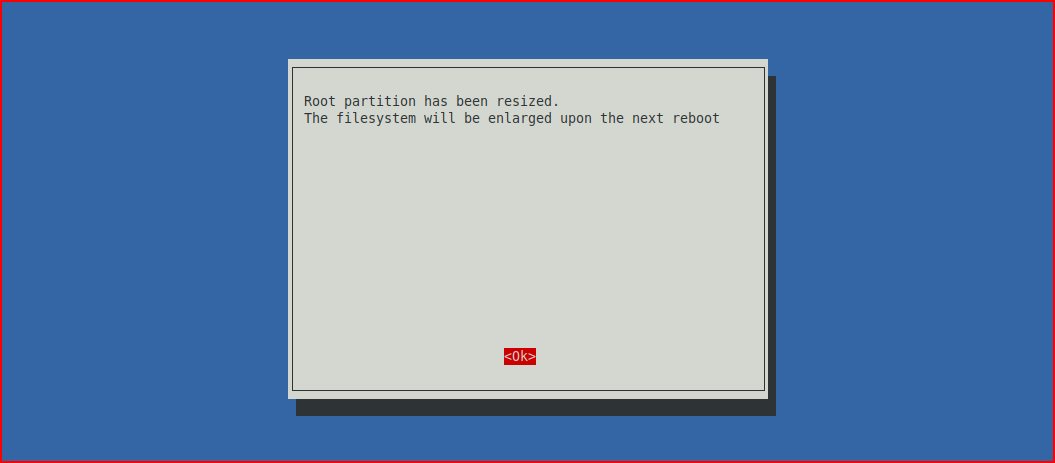
Select: A1 Expand Filesystem
Choose OK:
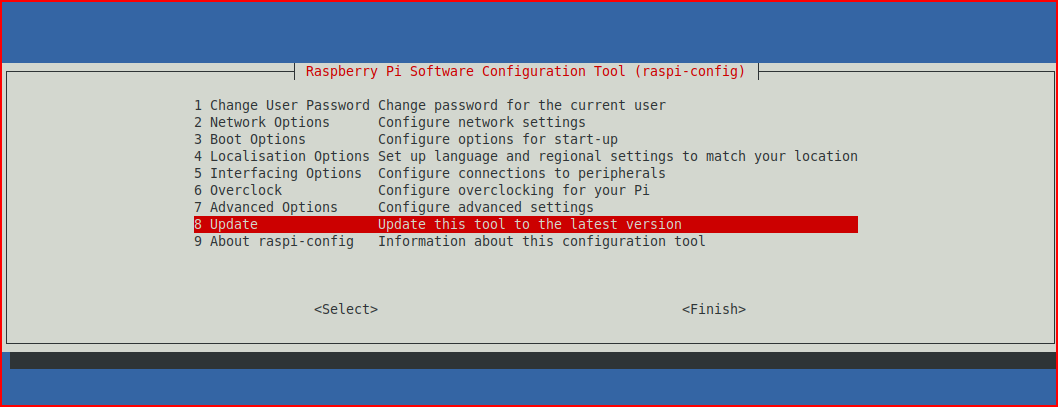
I'm probably doing a few thing out of order but we should probably update the tool.
Select: 8 Update
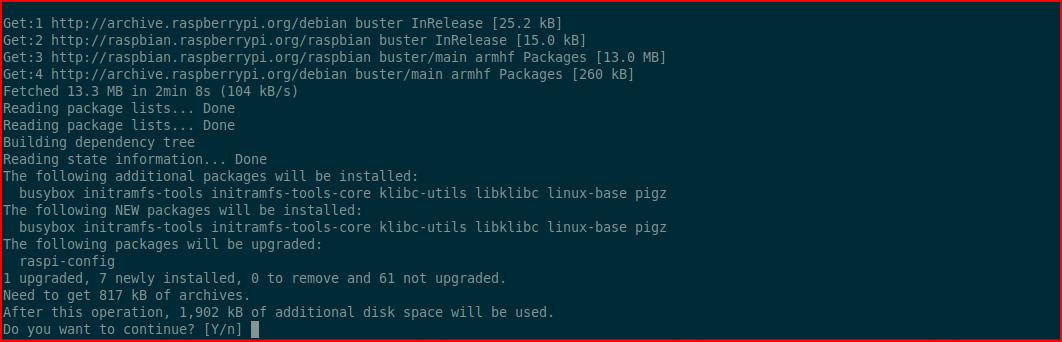
It goes through the updating process after we select Y:
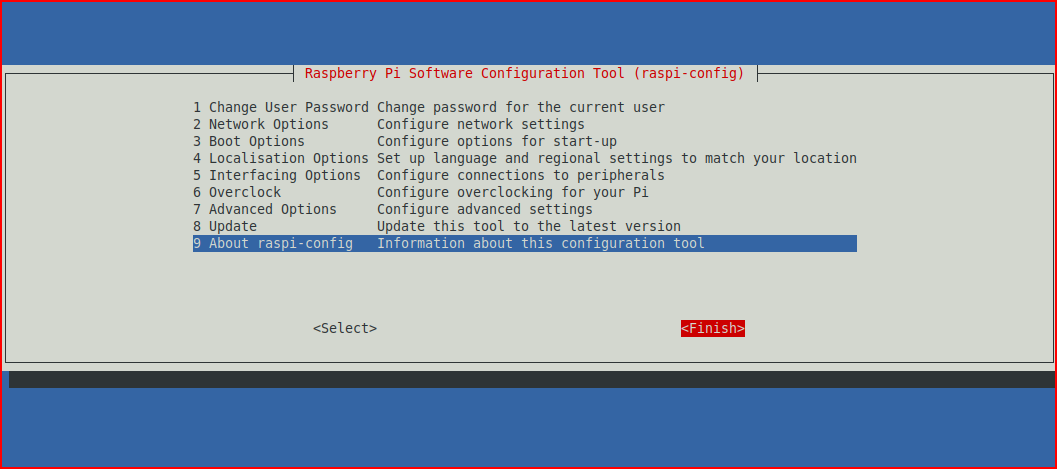
And finally, choose Finish:
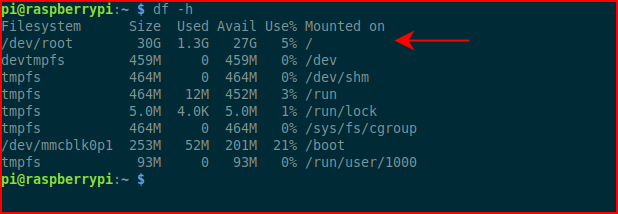
If we look at the disk, we see that we have the full 32GB available to us:
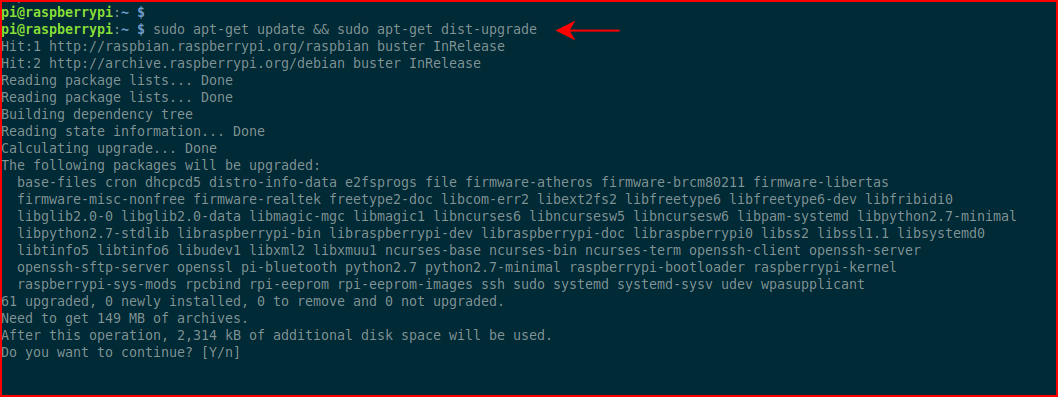
Now let's upgrade the OS:sudo apt-get update && sudo apt-get dist-upgrade
We select Y and we watch it update:
When it's finished, we want to put the Pi's wlan interface on a wifi network. sudo iwlist wlan0 scan | grep ESSID
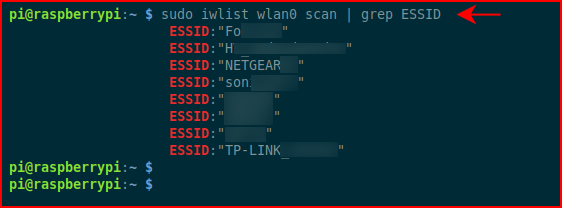
I see my network, next, I'm going to edit: /etc/wpa_supplicant/wpa_supplicant.conf
Add the SSID and psk password:
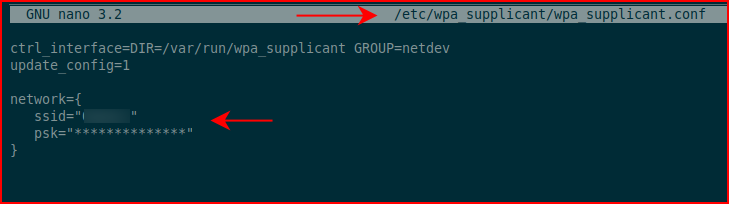
You could do a sudo ifconfig wlan0 down and up but that doesn't always work. Easiest thing to do is reboot which is what I ended up doing at the bottom with the: sudo init 6
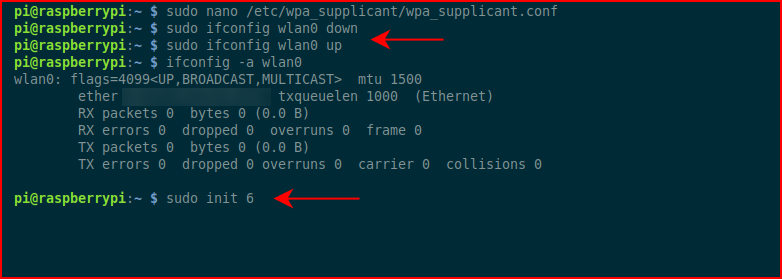
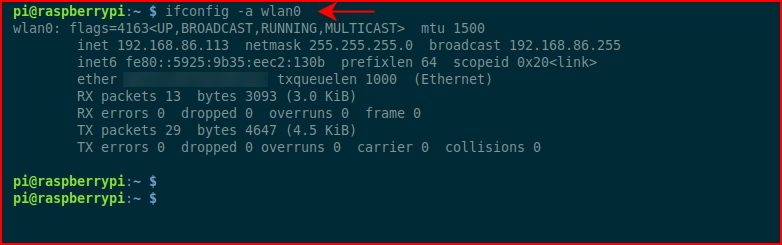
When we ssh back into the system, we run: ifconfig -a wlan0
We see that we've received an IP address from DHCP so we're golden.
Before I jump into this next series of commands, my process takes place in a particular order because at a certain point, I'm going to change lan0 to the proxy interface. At that moment, I will lose my SSH connection. If I were on the console, this wouldn't be a problem but I'm not on the console and the console consists of a 7" display. Yes, I could move it to another display but I'm lazy and the tiny display is sitting next to me.
At one point, I screw up the process and I fix the image in Photoshop but the output is missing. Basically, I forgot to save and when I rebooted, I lost my rules. No big deal, if you follow what you see, it will work just fine. Just pointing it out when you don't see the lengthy output in my image. Also, you are most welcome to do this in YOUR order. As I said though, MY order will work. The end result is the same but I just wanted you to understand why i did what I did.
Ok, with that out of the way, we install Tor:
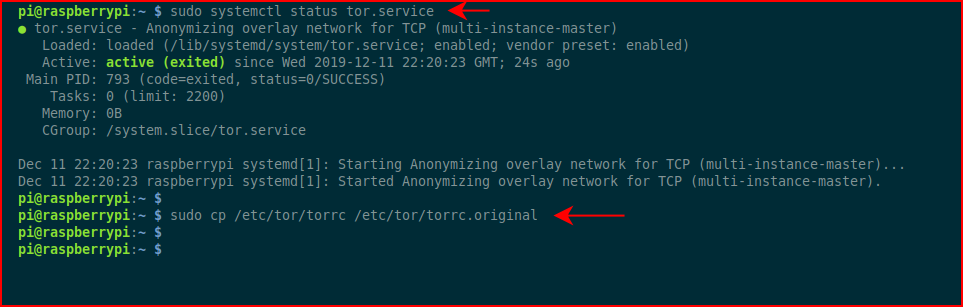
We check the status and we make a backup of the Tor config:
Edit the Tor config file:
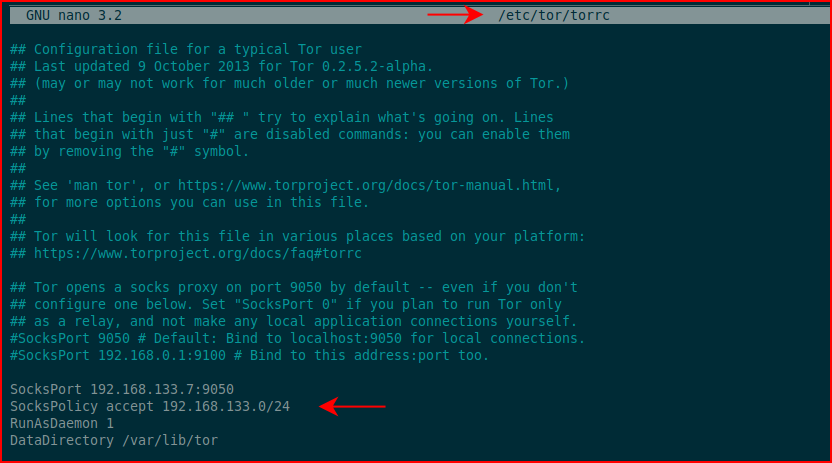
Change the subnet to whatever you like, I thought it would be funny to have 133,7 which is just my inner child having some fun.
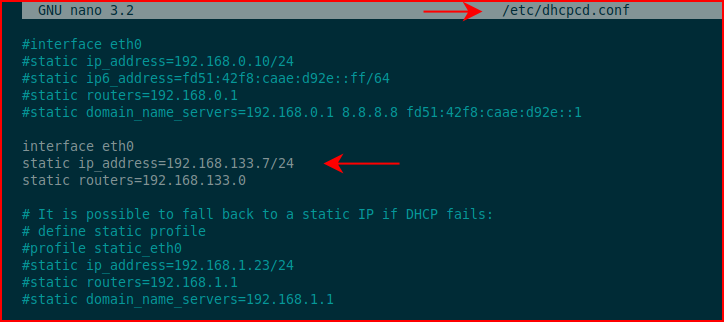
Next thing we need to do is set the static for lan0 to match that of what we chose for our IP in the Tor config file:
Next we're going to install dnsmasq which will provide DNS forwarding, DHCP, etc. for the lan0 side:
We'll move the dnsmasq config file:
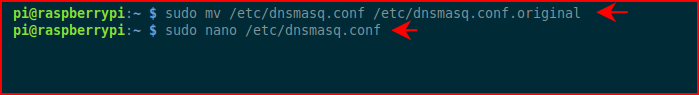
We'll start a brand new version of dnsmasq.conf and give it the following (change to match your config):
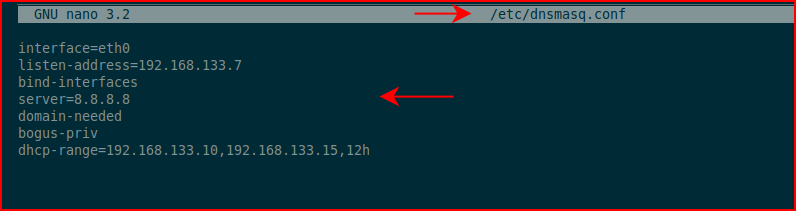
Next, we'll modify sysctl.conf to enable IP forwarding. We're going to find the line: #net.ipv4.ip_forward=1
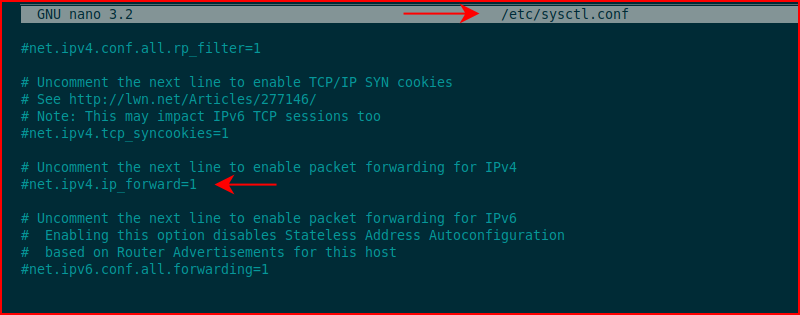
And we're going to remove the comment:
Now this is really where things get out of order. Normally, I'd setup the rules first before running the install but for reasons I've already stated, I'm going to run this first:sudo apt install iptables-persistent
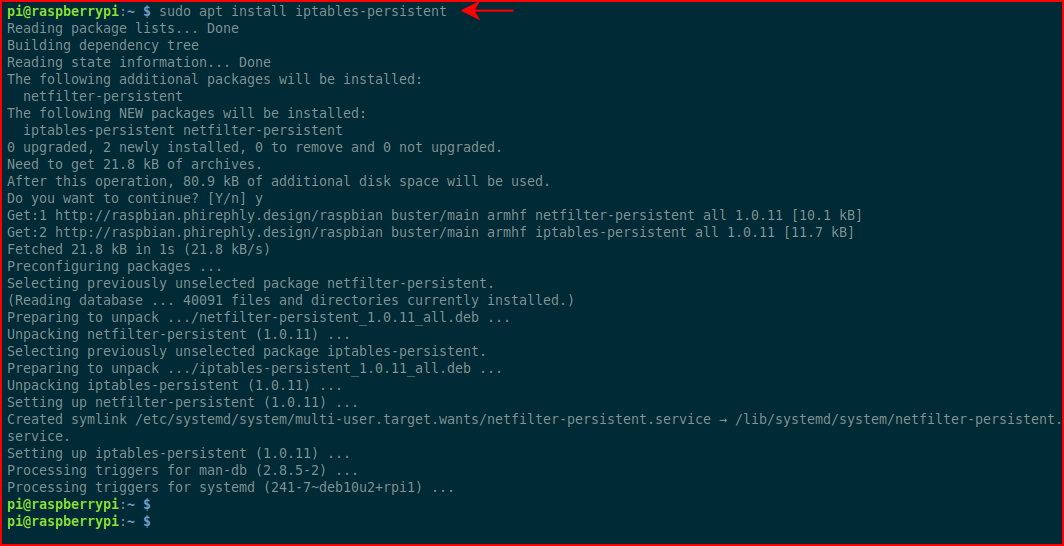
We're almost done. We need to setup the routing for the lan0 and wlan0 interface, we need to save the rules, and we're going to reboot which is the moment I lose my SSH connection:sudo iptables -t nat -A POSTROUTING -o wlan0 -j MASQUERADE sudo iptables -A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT sudo iptables -A FORWARD -i eth0 -o wlan0 -j ACCEPT sudo iptables-save
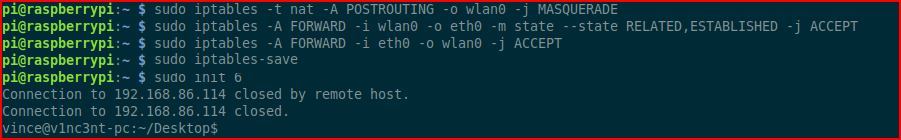
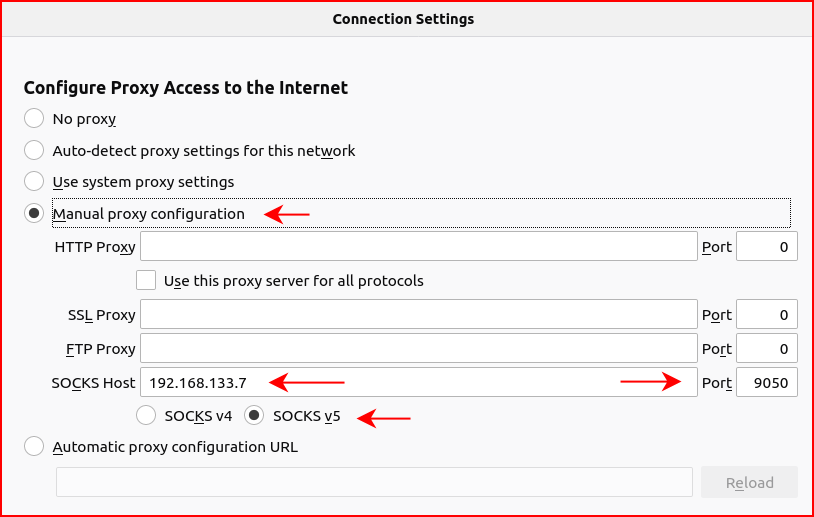
At this point, I connected my laptop to lan0 and it receives an IP on the 192.168.133.X subnet. I want to configure Firefox for the socks5 proxy:
Now I want to open a tab and see if I'm connected to Tor:
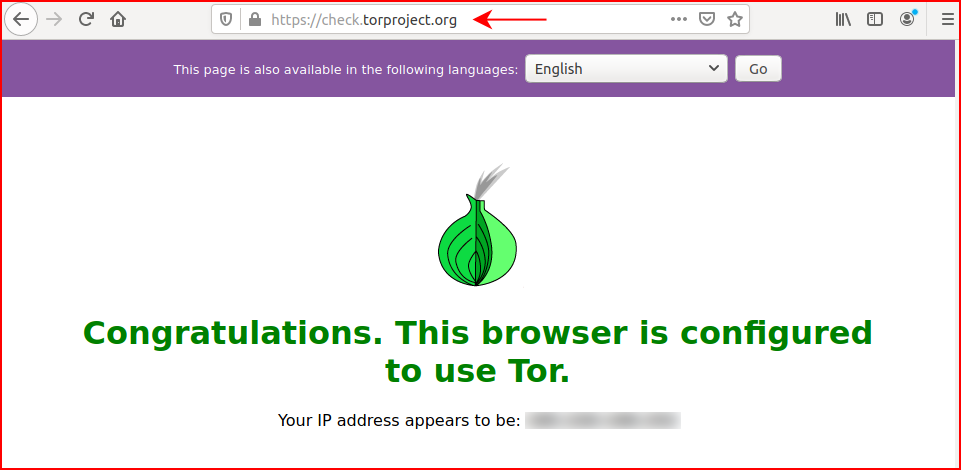
Sweet!
In my talk, I'm not just using the browser, I'm going to use other tools. In order to help with that, I'm going to install proxychains:
We need to edit the proxychains.conf file:
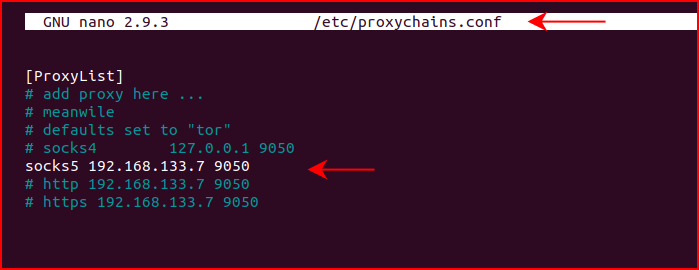
We add the line for the socks5 proxy and we're set. From here, we can run commands like: proxychains ssh root@someIP
If you run this command with and without proxychains, you can look in auth.log and see the two different IP addresses. With proxychains, Tor IP, without, your IP (no bueno).