Network Segmentation
While performing a penetration test recently, I managed to pivot from a workstation to a VoIP server. One of the main reasons this occurred is due to the fact that the network was not segmented. So what is network segmentation? It's breaking up the network into logical parts while isolating some devices from other devices.
I think most WiFi networks these days have a "guest network" which is essentially the same concept. We're isolating the guests from the rest of our network but we're still allowing them access to the Internet. With our network, we're able to do this with several different technologies but it can be done for as little as $20-$30.
In the picture below, I've created a basic network:
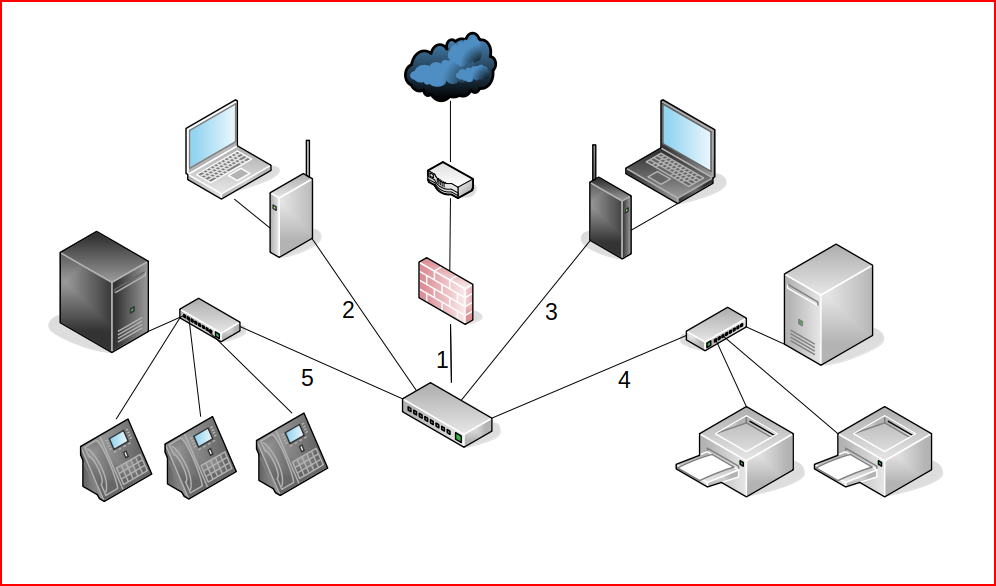
In the picture above, at the top, we have the Internet connecting to a router, a firewall, and a switch with VLAN (virtual local area network) capability. All of that falls into port #1. On ports #2 and #3, we have our internal WiFi network and our Guest WiFi network. On port #4, we have a file and print server. And finally, on port #5, we have a VoIP PBX and phones.
In the settings below, I've setup segmentation:
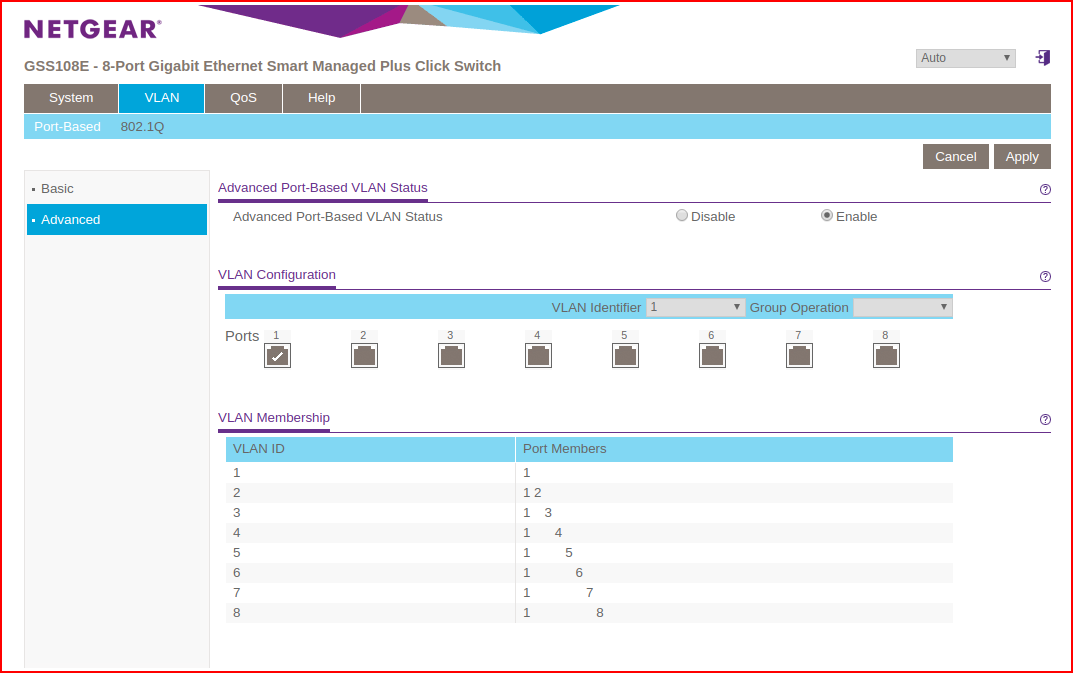
The VLAN ID off to the left corresponds to the switch port with the same ID. Port #1 connects to the Internet. And honestly, it doesn't need to have any port members for this scenario to work. However, for any of the other ports to connect to the Internet, we do need to have at least Port #1 as a member. Because none of the ID's have any other members other than Port #1, they are all isolated from each other but they can get to the Internet. So is this a functional setup? Not really.
The Guest WiFI network segment and the VoIP segment could remain as they currently exist. But the Internal workstations would be connected to the segment with the file and print segment. Now we're opening it up a little but in the case of where I was able to pivot from the workstation to the VoIP server, that could not happen.
Another consideration for segmentation are all those Internet of Things devices. You can either toss them onto the Guest WiFi network or you can add another access point and give them their own segment altogether.
Princeton University developed a tool for spying on the devices spying on you and I briefly ran it until it killed my network. It actually states this is possible due to heavy traffic loads. Though, while I did run it, it was obvious these devices were reporting back even when not in use. Either through coincidence or not, the Nest thermostat seemed to ping back to the mother ship each time I walked past it. No good can come from these devices having direct access to our entire network and limiting their view through segmentation makes absolute sense.
We can take this a step further by defining QoS (Quality of Service) rules which allow us to prioritize traffic. For example, do I want my Guest WiFI segment to hog all of the bandwidth? No. We can use QoS to prohibit this from occurring.
We have other avenues we can take to isolate, or restrict, traffic within our network but that's for another day. This is just a basic look at how segmentation could be done.
One final comment -- I wouldn't use a $20-$30 switch for my office. While probably decent, there are more robust options that are a little more expensive but won't break the bank.